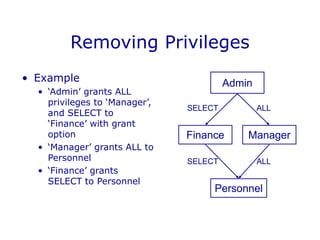
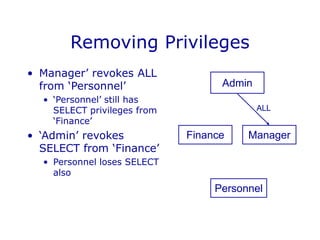
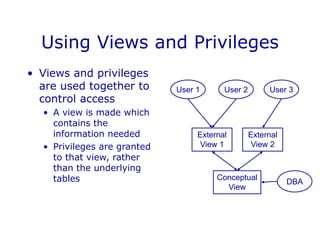
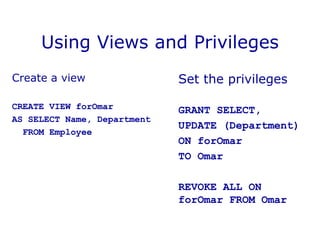
DBMS security involves controlling access to databases through user accounts, passwords, and privileges. Privileges specify access rights and are granted to users at the table or view level. Views provide restricted access to tables by showing only selected columns or rows. Views can be updated if they meet certain conditions, such as containing a single table in the FROM clause. Views and privileges are used together to restrict access - views define the accessible data, and privileges control access rights to those views. This allows fine-grained access control over database information on a per-user basis.





![Privileges in SQL
GRANT <privileges>
ON <object>
TO <users>
[WITH GRANT OPTION]
• <privileges> is a list of
SELECT <columns>,
INSERT <columns>,
DELETE, and
UPDATE <columns>, or
simply ALL
• <users> is a list of user
names or PUBLIC
• <object> is the name of
a table or view (later)
• WITH GRANT OPTION
means that the users can
pass their privileges on
to others](https://image.slidesharecdn.com/dbmssecurity-221105195808-ab973317/85/DBMS-Security-ppt-6-320.jpg)