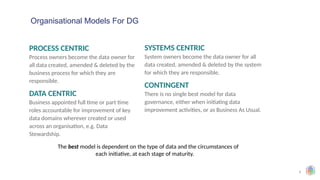
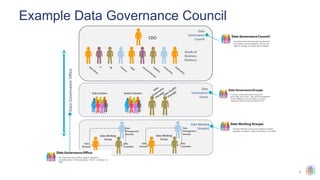
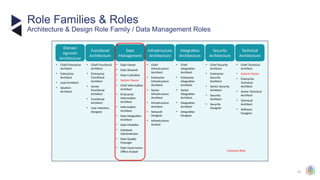
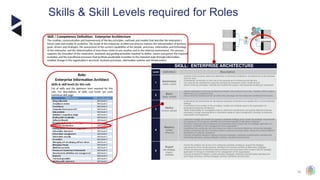
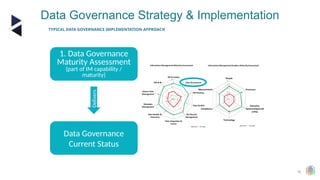
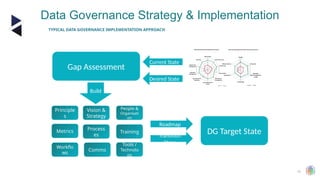
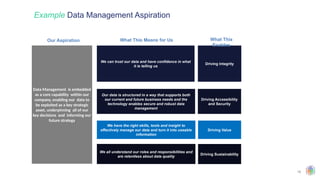
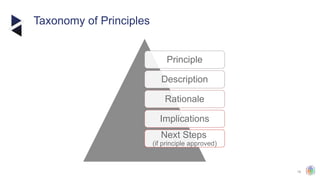
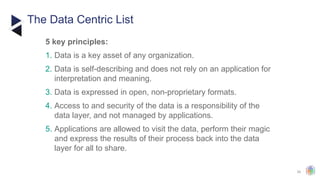
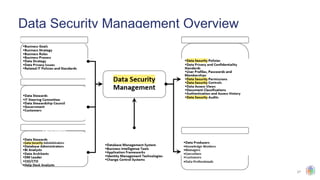
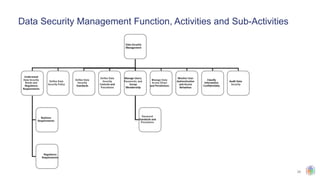
The document outlines the principles and structures of data governance, emphasizing the roles and responsibilities of various stakeholders including data owners, stewards, and custodians. It discusses the implementation of data governance frameworks, security measures, and compliance with regulations such as GDPR and HIPAA. The document also highlights the importance of establishing a data governance council and the need for effective data management practices across organizations.