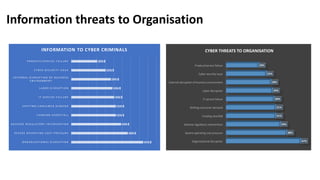
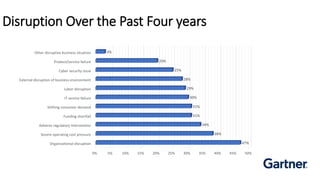
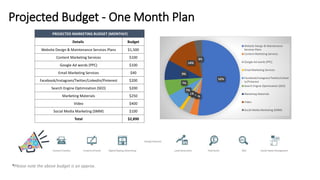
The document outlines a cybersecurity digital marketing plan that emphasizes the importance of security compliance, vendor compatibility, and effective data monitoring in light of escalating cyber threats. It highlights marketing challenges faced by cybersecurity firms and recommends strategies such as lead generation, content marketing, and digital initiatives to increase brand awareness. Additionally, it provides a proposed budget for a one-month marketing plan totaling approximately $2,890.