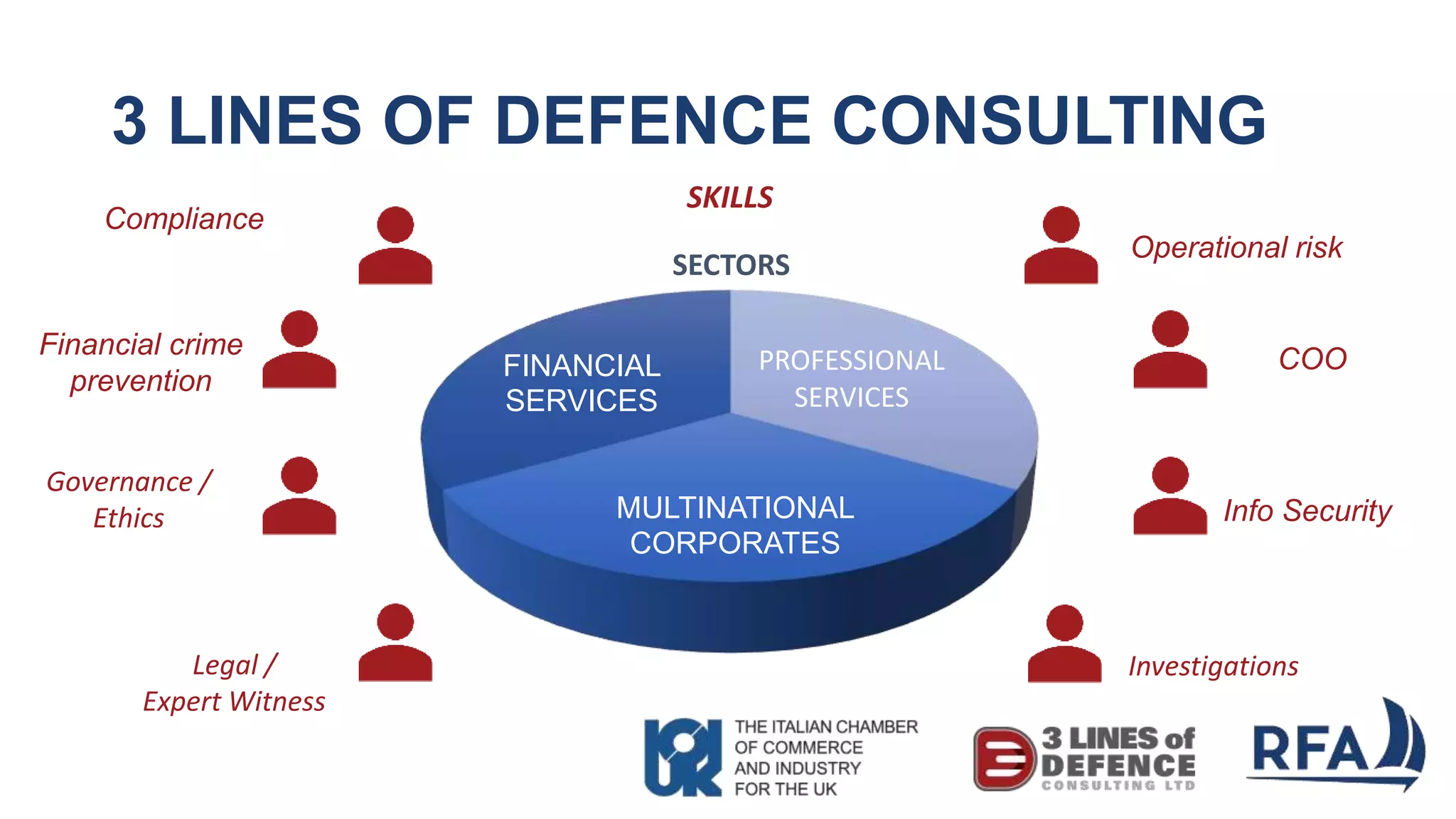
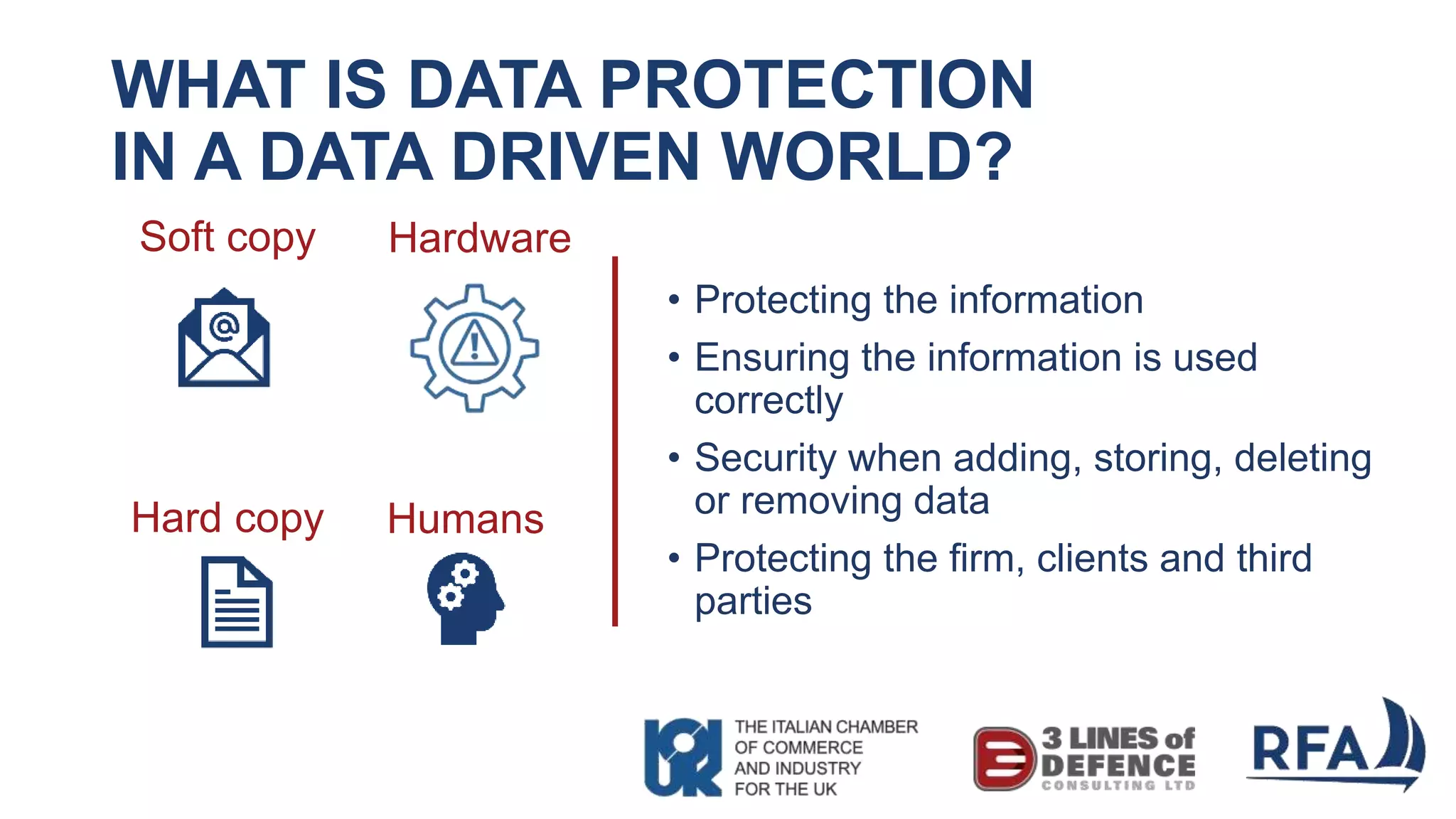
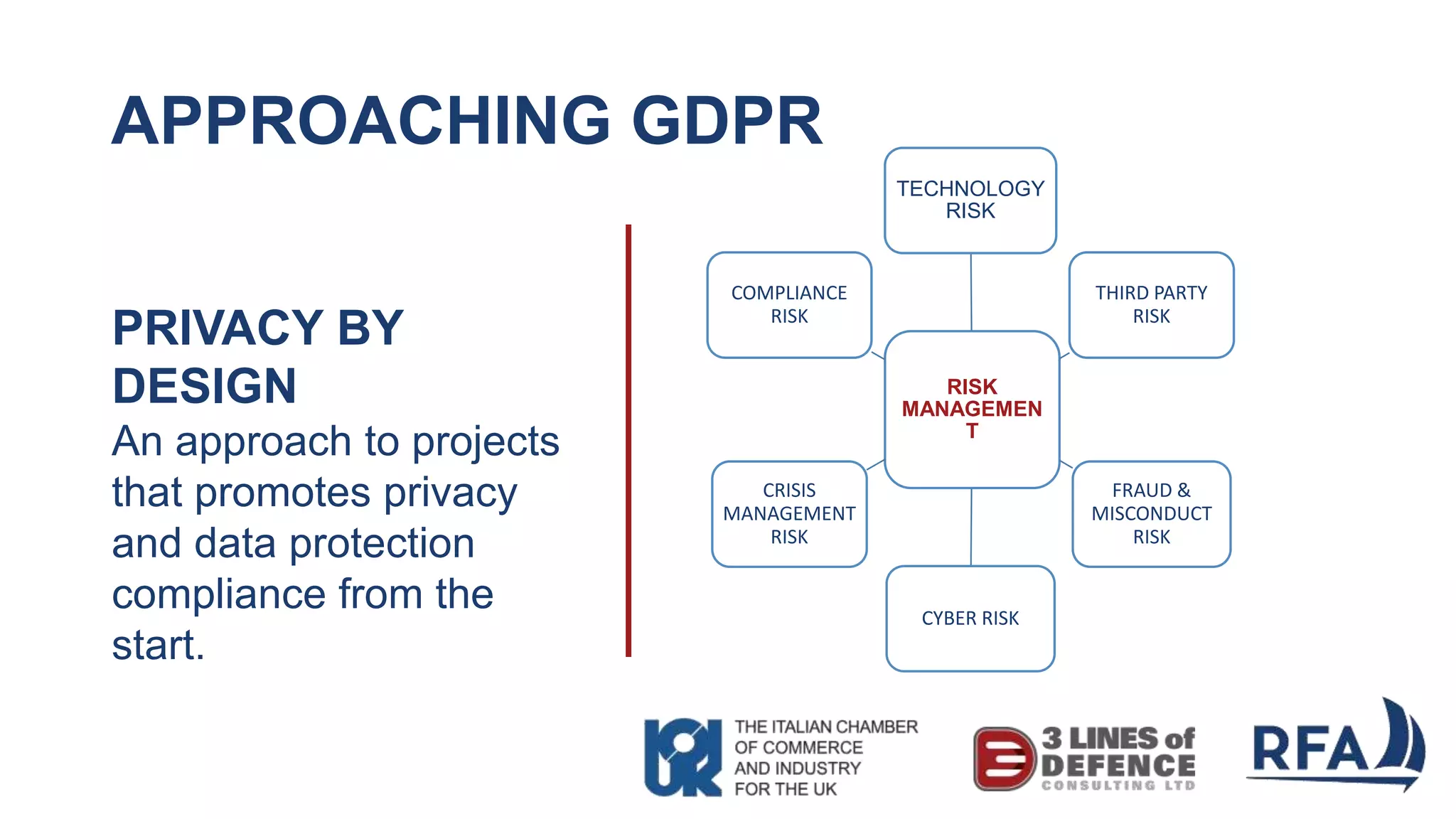
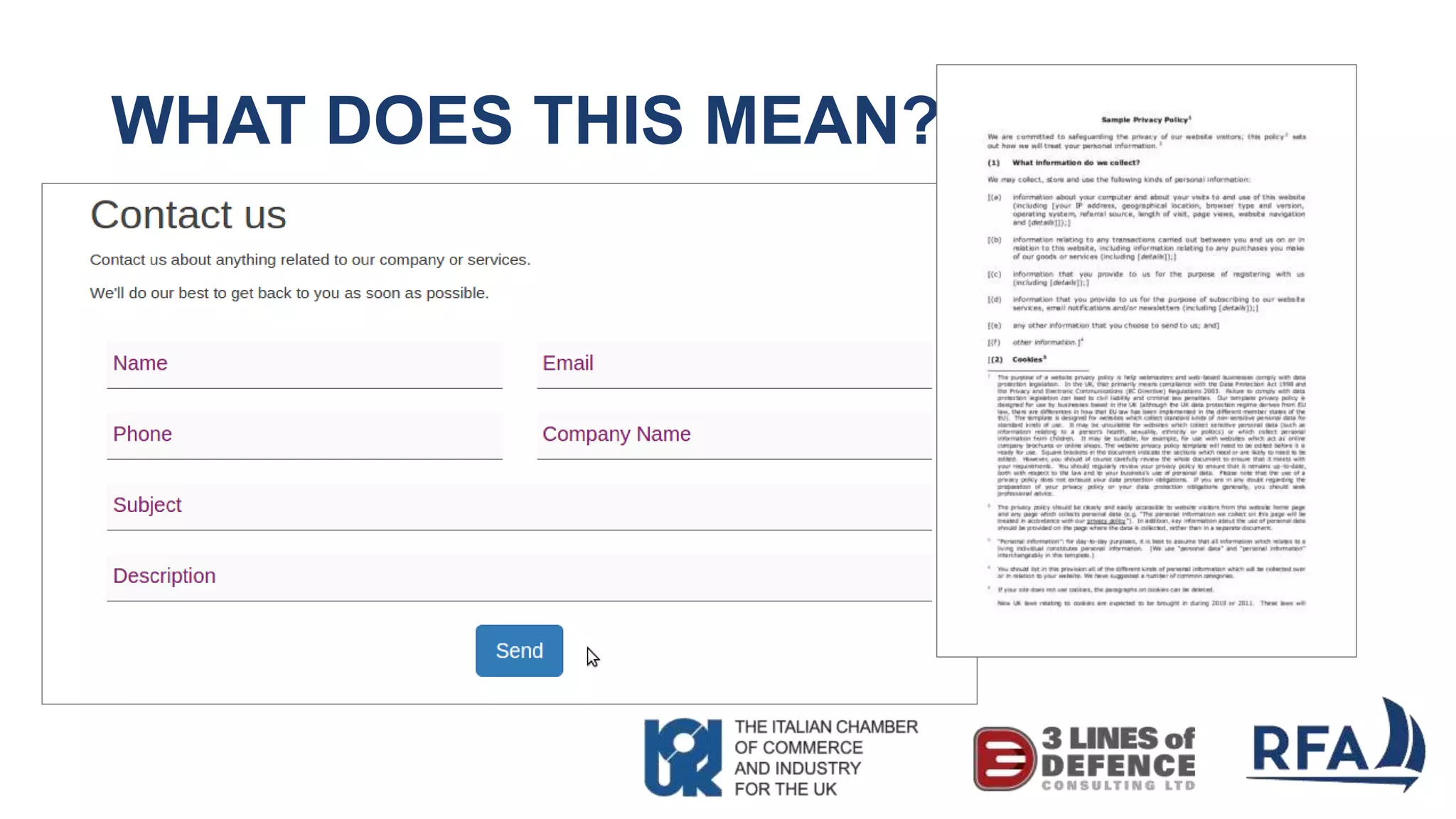
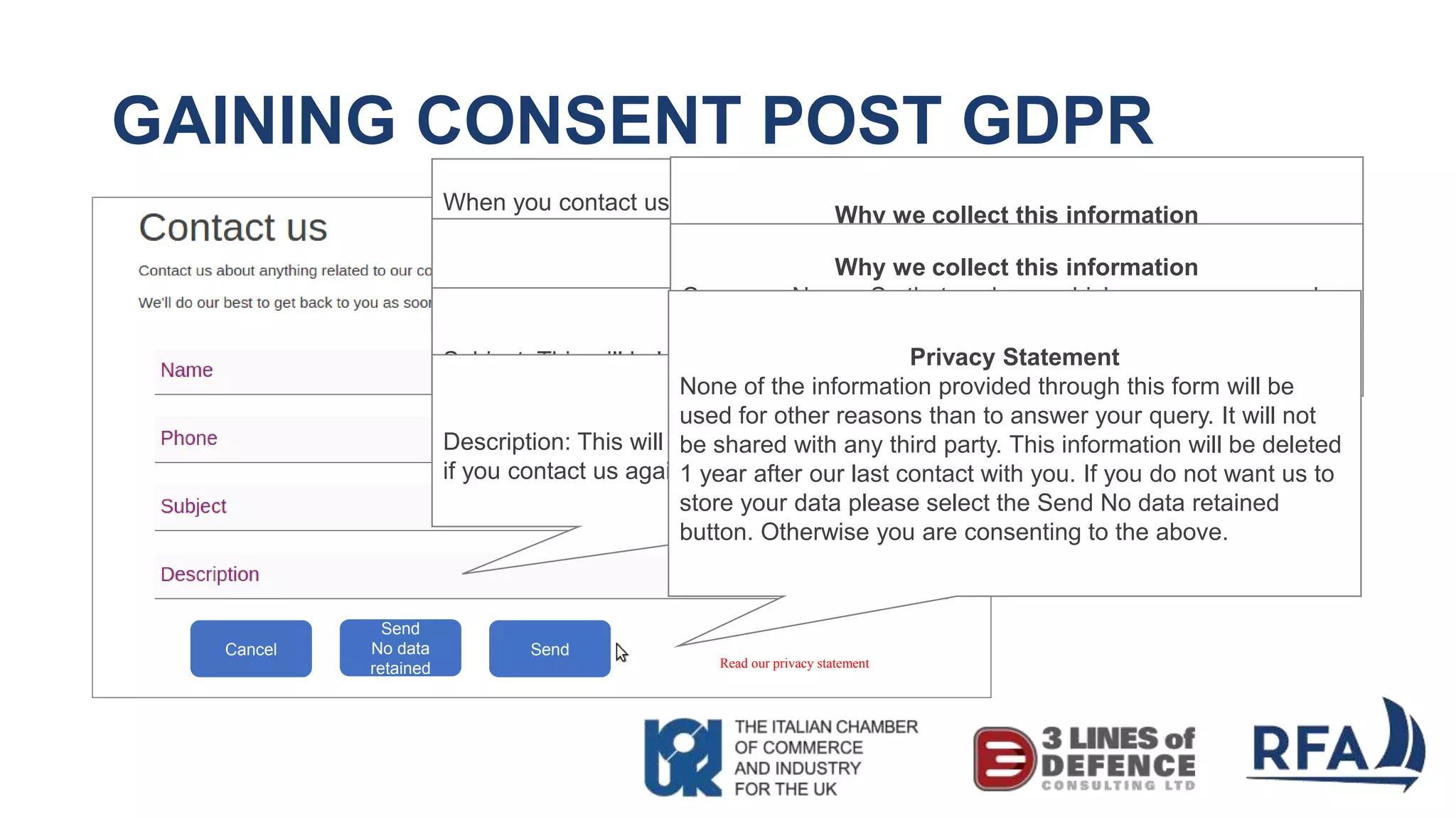
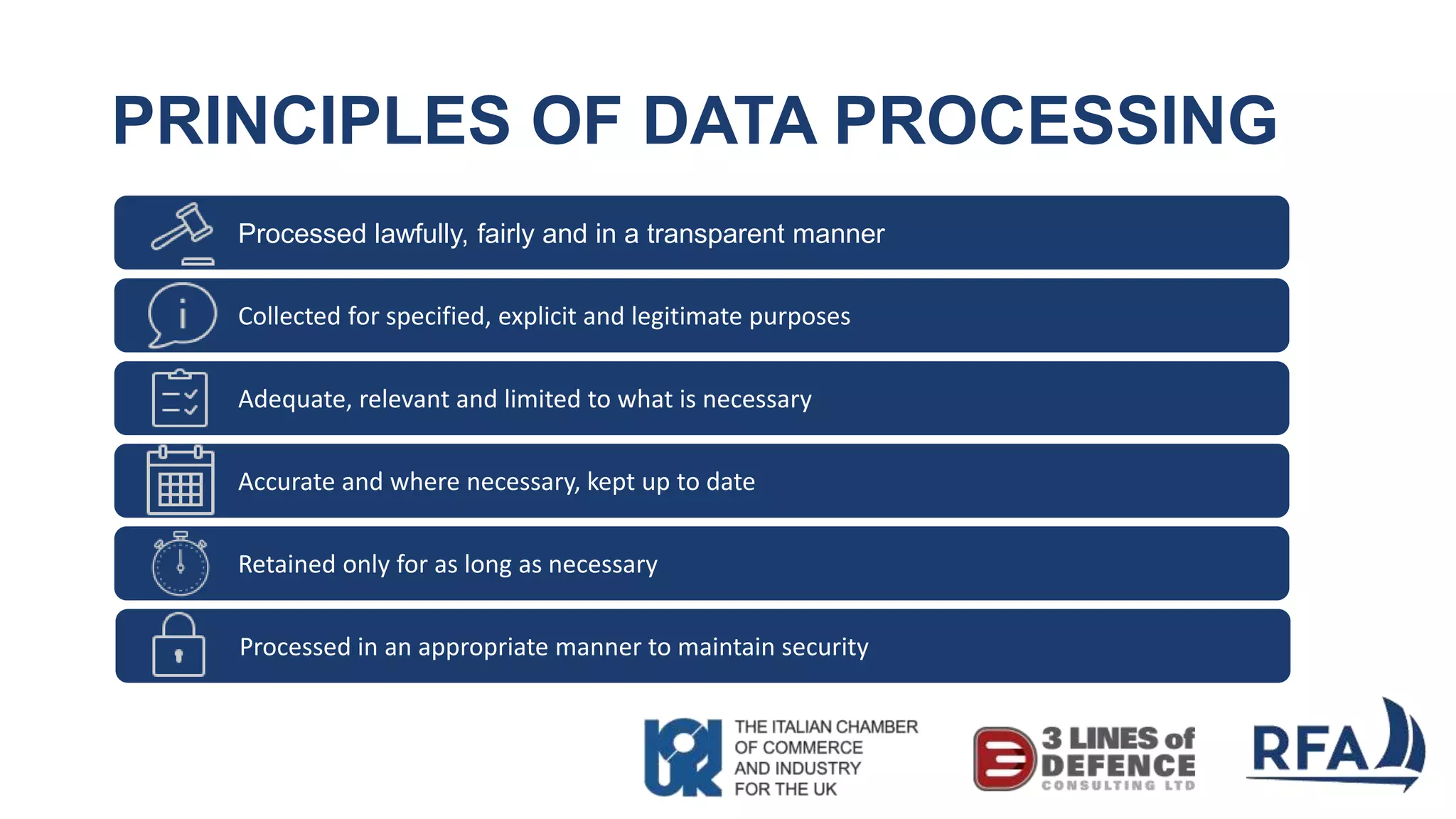
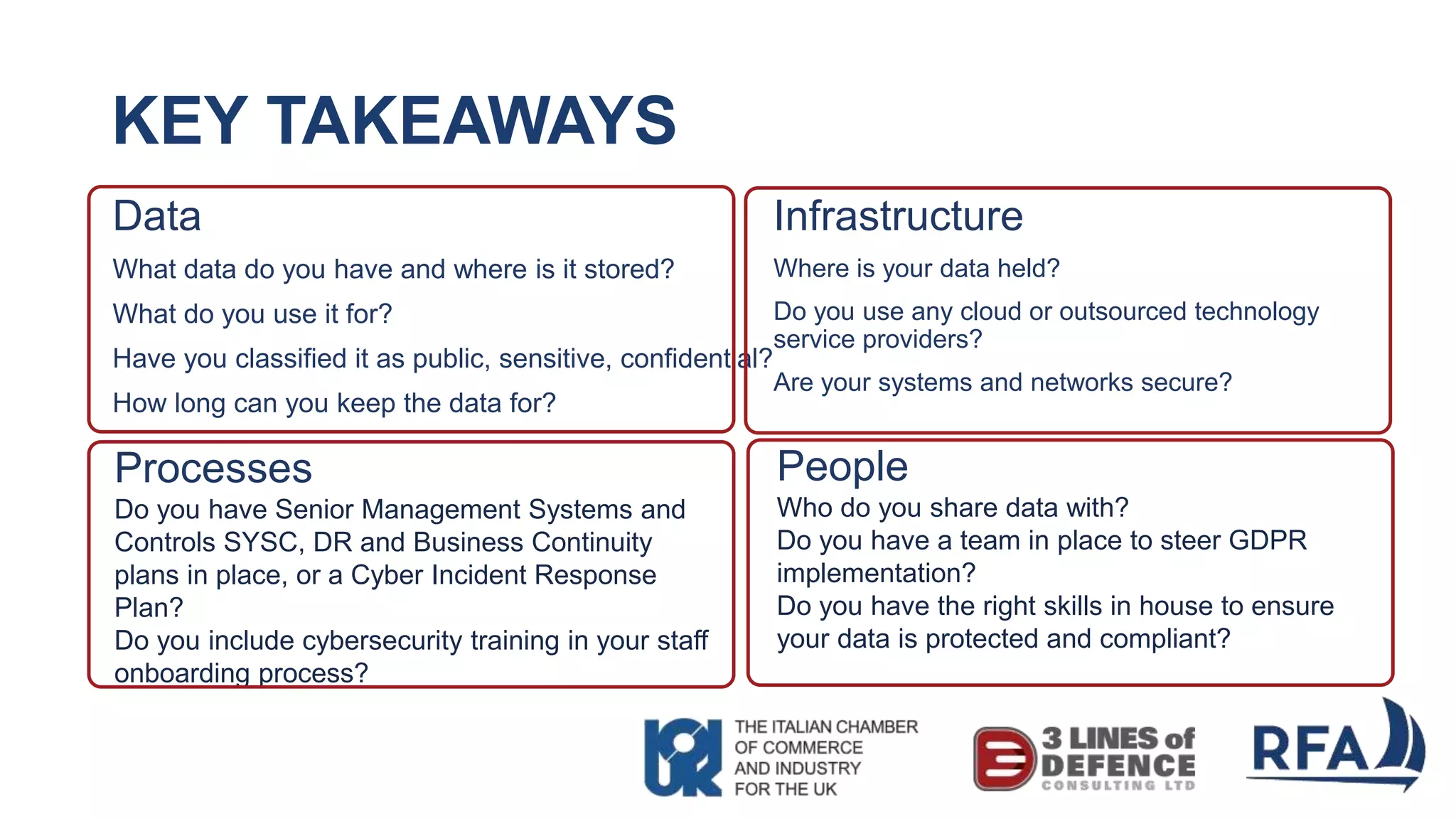
The document discusses the importance of cybersecurity and data protection in a data-driven world, highlighting the services offered by RFA, a global technology consultancy, including managed cloud services and compliance consulting. It emphasizes the legal and regulatory aspects of data protection, particularly the General Data Protection Regulation (GDPR), and outlines a five-step action plan for effective data management. Key takeaways include understanding data assets, ensuring cybersecurity measures, and having a robust strategy for compliance and risk management.