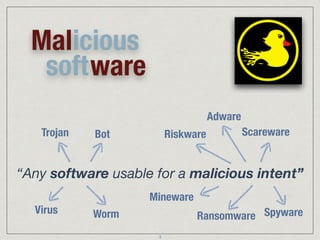
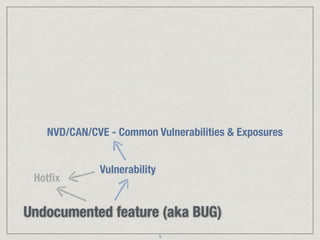
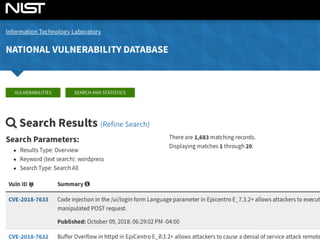
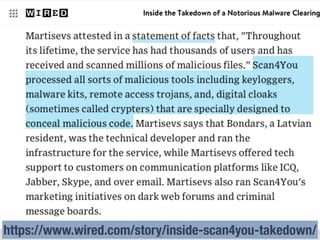
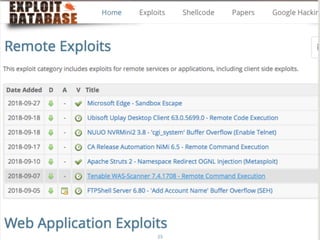
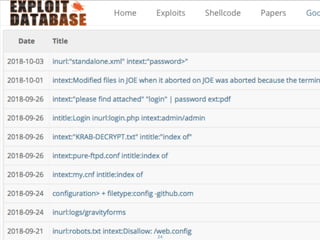
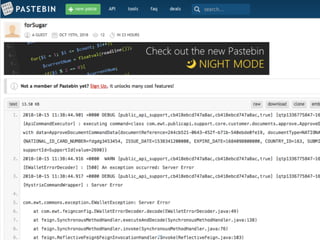
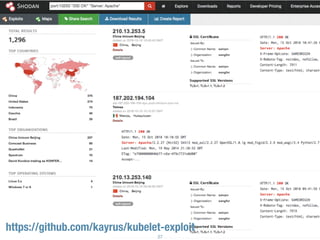
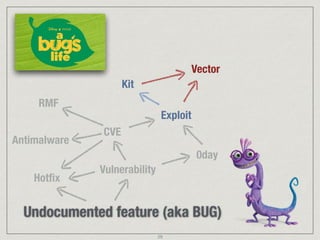
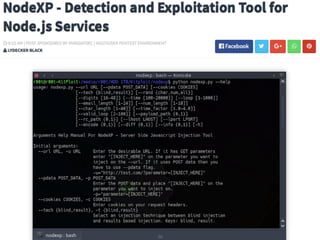
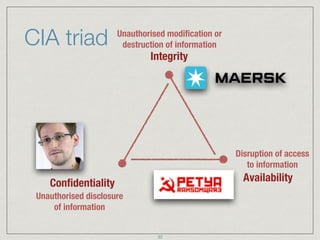
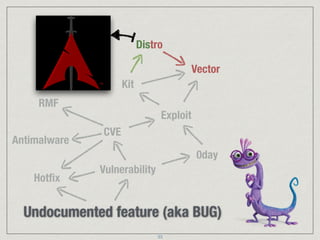
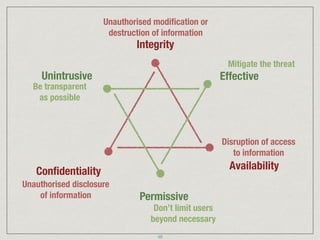
The document provides an extensive overview of cybersecurity concepts, including various types of malware and the importance of vulnerability management. It references numerous standards and frameworks such as NIST's SP-800 series, GDPR, and PCI DSS, emphasizing the need for strong risk management practices. Additionally, it highlights the CIA triad (confidentiality, integrity, availability) and discusses tools and methodologies for effective cybersecurity assessments.