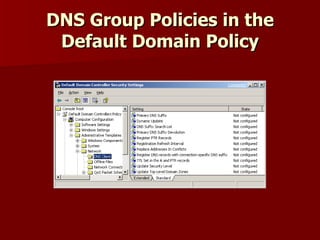
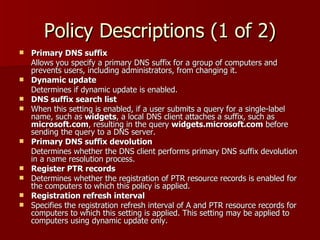
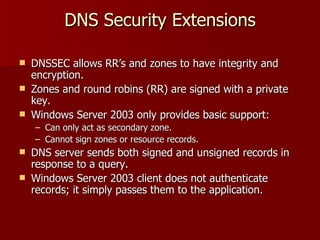
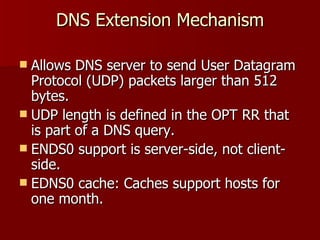
Windows Server 2003 introduced several changes to DNS including:
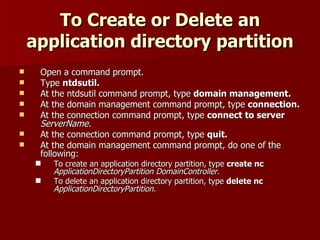
1) Application directory partitions allow DNS zone data to be stored separately from global catalog reducing replication load.
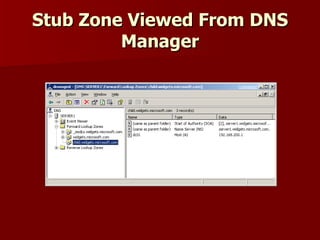
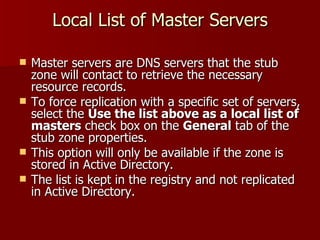
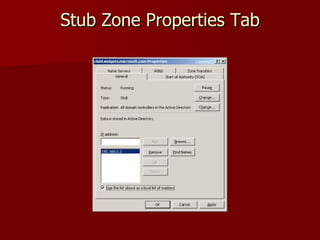
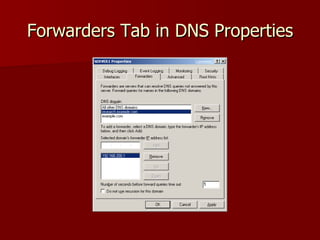
2) Stub zones and conditional forwarders improve name resolution between domains.
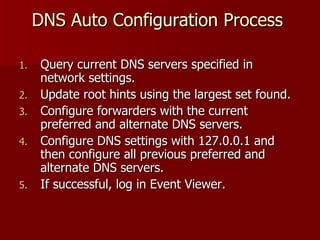
3) DNS client settings can now be centrally managed through group policy for things like suffix search lists.
4) Additional security features were added like DNSSEC and logging enhancements but full support requires future Windows versions.