Common Cybersecurity Mistakes
•
0 likes•370 views
This document outlines 4 common cybersecurity mistakes that small and medium-sized businesses make that leave them vulnerable to attacks. These include not properly training employees, allowing employees to use personal devices for work without a BYOD policy, relying on a single in-house IT person instead of an managed service provider, and failing to have a disaster recovery plan in place. The document provides examples of the risks associated with each mistake and promotes partnering with an MSP for comprehensive security assistance.
Report
Share
Report
Share
Download to read offline
Recommended
Stop occupational fraud - Three simple steps to help stop fraud

Internal fraud and threat is on the rise. The leading cause of insider threat is staff members taking advantage of their systems’ access privileges and using their organizations’ corporate LAN systems as attack vectors. The consequences of internal fraud are significant to organizations, brands and Boards of Directors.
Talking To The Board: How To Improve Your Board's Cyber Security Literacy – U...

Boards of Directors have an inescapable legal responsibility to protect their organisation’s assets and shareholder value against risks. Where does cybersecurity fit in the agenda? Many boards lack the knowledge, awareness and confidence to connect security to the business.
In this webcast, moderator Paul Edon, Director of Customer Services at Tripwire, will provide a variety of perspectives from experienced professionals in the industry — including Amar Singh UK CISO for Elsevier, Ray Stanton EVP Professional Services at BT and Advisory Board Member of ISF, and Gary Cheetham, CISO at NFU Mutual.
Business Safety

Business safety advice from Business Network Long Distance. Small or large business, we have you covered. Business Network Long Distance is your source for all your long distance needs!
Nonprofit Cybersecurity Readiness - Community IT Innovators Webinar

Join CTO and resident security expert, Matt Eshleman, for this webinar which will cover the basics a security plan should include, giving updates and a synthesis of our recent security webinars on understanding risks, considering cyber insurance, security incidence response best practices, and creating a multi-layered security plan that actively includes your staff and executives.
Recommended
Stop occupational fraud - Three simple steps to help stop fraud

Internal fraud and threat is on the rise. The leading cause of insider threat is staff members taking advantage of their systems’ access privileges and using their organizations’ corporate LAN systems as attack vectors. The consequences of internal fraud are significant to organizations, brands and Boards of Directors.
Talking To The Board: How To Improve Your Board's Cyber Security Literacy – U...

Boards of Directors have an inescapable legal responsibility to protect their organisation’s assets and shareholder value against risks. Where does cybersecurity fit in the agenda? Many boards lack the knowledge, awareness and confidence to connect security to the business.
In this webcast, moderator Paul Edon, Director of Customer Services at Tripwire, will provide a variety of perspectives from experienced professionals in the industry — including Amar Singh UK CISO for Elsevier, Ray Stanton EVP Professional Services at BT and Advisory Board Member of ISF, and Gary Cheetham, CISO at NFU Mutual.
Business Safety

Business safety advice from Business Network Long Distance. Small or large business, we have you covered. Business Network Long Distance is your source for all your long distance needs!
Nonprofit Cybersecurity Readiness - Community IT Innovators Webinar

Join CTO and resident security expert, Matt Eshleman, for this webinar which will cover the basics a security plan should include, giving updates and a synthesis of our recent security webinars on understanding risks, considering cyber insurance, security incidence response best practices, and creating a multi-layered security plan that actively includes your staff and executives.
Cybersecurity Toolkit

Cybersecurity is a fast-expanding field spanning network infrastructure, remote services, device diversity, even the nuances of human interaction and behaviour within the enterprise. Today’s IT expert is part technician, part detective, and part sociologist.
This SlideShare presentation is a blow-by-blow account of the issues that matter in today’s hyperlinked, cross-connected, time-shifted organisation—with each threat backed up by some key statistics.
Containing the outbreak: The healthcare security pandemic

James Maude, Senior Security Engineer at Avecto examines the security state of play in the healthcare industry and why it’s now a prime target for hackers.
Checklist for Preventing Ransomware

Chances are you know someone in healthcare whose organization has suffered a ransomware attack – if you are not careful, you could be next. If you haven’t been hit by ransomware personally, you’re either very lucky, or you’ve taken some proactive steps to protect your computers and files. If you do get infected with ransomware, unless you’ve got back-ups, or the crooks made some kind of cryptographic mistake, you’re left with either paying or losing your locked up files forever.
What Does a Data Breach Cost?

Assessing the risk of a data breach is the first step toward preparing your defensive strategy. Learn what factors affect the cost of a data breach and what you can do to mitigate the damage. IT teams can make a significant impact in lowering the cost of security breaches by improving their ability to prevent, detect, and respond. Learn more about information security with CBT Nuggets. http://bit.ly/2a6cNwm
A Hacker's perspective on ransomware

Microsoft MVP and pen tester, Paula Januszkiewicz takes a deep dive into ransomware, how it works and how it can be prevented.
How secure is your company's information?

Do your employees know their responsibilities when it comes to your company's information security? Education is key when helping employees understand the risks that we all too often ignore. Take a look and find out how you can improve your security to keep your information from being at risk.
7 cyber security questions for boards

The cyber security job is everyone's business including the Board of Directors, even without a cyber security degree. Recent cyber security news proves that. According to several studies, Boards are getting it wrong and are leaving cyber awareness and risk management in the hands of the CEO, CISO, CTOs and cyber security companies. In a sense they are abdicating their responsibility to the shareholders. This slideshare proposes 7 questions every board should be asking their company executives abour IT security. They're not necessarily all encompassing and don't take the place of real cybersecurity training, but will drive the discussion to better and more complete understanding of strategic risk. Questions cover the basics of cyber security training, cyber policies, who briefs and when at board meetings. Thanks.
2015 Microsoft Vulnerabilities Report 

Avecto's annual report into Microsoft vulnerabilities uncovers how you can mitigate risk by removing admin rights.
Security Operations Strategies 

SOC managers should work with their teams to define and document processes, codifying them into playbooks. From there, security orchestration and automation can be applied to unify and automate your technologies and processes.
For more on how your security operations team can get started using security automation, check out our webinar on security automation quick wins.
Visit - https://www.siemplify.co/blog/security-operations-strategies-for-winning-the-cyberwar
The New Economics of Cloud Security

Welcome to everything the cloud has to offer. Now, you need to keep your apps and workloads secure, without compromising the speed and flexibility of the cloud. This is the new economics of cloud security.
Learn more: https://www.alertlogic.com/neweconomics
Understanding the 8 Keys to Security Success

CISOS work hard to manage risk and ensure the security of the organization. But, they must also create an environment where business can be transacted seamlessly, conveniently and securely. With over a decade of supporting organizations in this mission, Security On-Demand has compiled the eight keys to security success which will help you achieve your goals of delivering security and business agility.
Ernst & Young visuals security survey 2012

Risk and Security not always aligned. Not enough non IT focus on security. Hardly surprising that organisational Information Security needs are not being met in enough organisations.
What is CryptoLocker and How Can I Protect My Business From It?

If your business operates on Windows computers, be on the lookout. Cybercriminals created malicious computer software, called CryptoLocker, which can invade your computer, encrypt your data, and then demand you pay a ransom. Afterwards, you have roughly 72 hours to pay the ransom of at least $200 in bitcoins. If you don’t pay the ransom on time, the price can go up to $2,000. Or don’t pay and lose your data forever, which likely won’t be an option if CryptoLocker encrypted files critical to operating your business, such as legal documents, payroll forms, and customer information.
Video surveillance: Why should my business use it?

We offered advice for monitoring employee computer use. However, you should not forget about the risks to your business inside your office walls. The threats can come from thieves, attackers, competitors, and even your own employees. According to a 2007 American Management Association survey, 48% of companies use video monitoring to prevent theft, violence, and sabotage. Also, the US Department of Commerce notes that employee theft contributes to 30% of business failures. Consider protecting your business with video surveillance. Learn more here: http://bit.ly/1oANVvm
Bridging the Cybersecurity Gap

While board of directors may understand the importance of cybersecurity, many lack crucial knowledge and visibility into issues and risks, which breeds a lack of trust between the board and IT security professionals. On this site, you’ll find a variety of resources to help bridge those gaps and bring the two groups together so organizations can better defend against advanced threats.
Protecting Your Business from a Cyber Attack

Presentation from Armstrong's Insurance Brokers and Eaglecrest Technologies for CPA Australia and Launceston Chamber of Commerce on how to protect your business from a cyber attack.
6 lessons to better business security

Understand the 6 requirements around better business security.
Before you implement them, find out what you need to do.
Take the test and get your report
INFOGRAPHIC▶ Spear Phishing Scammers Sharpen Their Attacks

Attackers win your confidence with personalized, targeted emails.
4 Precautions to Keep Your Supply Chain Data Safe

Supply Chain companies should take a step in developing high-quality risk management strategies and train their employees to identify potential threats and avoid these types of situations.
More Related Content
What's hot
Cybersecurity Toolkit

Cybersecurity is a fast-expanding field spanning network infrastructure, remote services, device diversity, even the nuances of human interaction and behaviour within the enterprise. Today’s IT expert is part technician, part detective, and part sociologist.
This SlideShare presentation is a blow-by-blow account of the issues that matter in today’s hyperlinked, cross-connected, time-shifted organisation—with each threat backed up by some key statistics.
Containing the outbreak: The healthcare security pandemic

James Maude, Senior Security Engineer at Avecto examines the security state of play in the healthcare industry and why it’s now a prime target for hackers.
Checklist for Preventing Ransomware

Chances are you know someone in healthcare whose organization has suffered a ransomware attack – if you are not careful, you could be next. If you haven’t been hit by ransomware personally, you’re either very lucky, or you’ve taken some proactive steps to protect your computers and files. If you do get infected with ransomware, unless you’ve got back-ups, or the crooks made some kind of cryptographic mistake, you’re left with either paying or losing your locked up files forever.
What Does a Data Breach Cost?

Assessing the risk of a data breach is the first step toward preparing your defensive strategy. Learn what factors affect the cost of a data breach and what you can do to mitigate the damage. IT teams can make a significant impact in lowering the cost of security breaches by improving their ability to prevent, detect, and respond. Learn more about information security with CBT Nuggets. http://bit.ly/2a6cNwm
A Hacker's perspective on ransomware

Microsoft MVP and pen tester, Paula Januszkiewicz takes a deep dive into ransomware, how it works and how it can be prevented.
How secure is your company's information?

Do your employees know their responsibilities when it comes to your company's information security? Education is key when helping employees understand the risks that we all too often ignore. Take a look and find out how you can improve your security to keep your information from being at risk.
7 cyber security questions for boards

The cyber security job is everyone's business including the Board of Directors, even without a cyber security degree. Recent cyber security news proves that. According to several studies, Boards are getting it wrong and are leaving cyber awareness and risk management in the hands of the CEO, CISO, CTOs and cyber security companies. In a sense they are abdicating their responsibility to the shareholders. This slideshare proposes 7 questions every board should be asking their company executives abour IT security. They're not necessarily all encompassing and don't take the place of real cybersecurity training, but will drive the discussion to better and more complete understanding of strategic risk. Questions cover the basics of cyber security training, cyber policies, who briefs and when at board meetings. Thanks.
2015 Microsoft Vulnerabilities Report 

Avecto's annual report into Microsoft vulnerabilities uncovers how you can mitigate risk by removing admin rights.
Security Operations Strategies 

SOC managers should work with their teams to define and document processes, codifying them into playbooks. From there, security orchestration and automation can be applied to unify and automate your technologies and processes.
For more on how your security operations team can get started using security automation, check out our webinar on security automation quick wins.
Visit - https://www.siemplify.co/blog/security-operations-strategies-for-winning-the-cyberwar
The New Economics of Cloud Security

Welcome to everything the cloud has to offer. Now, you need to keep your apps and workloads secure, without compromising the speed and flexibility of the cloud. This is the new economics of cloud security.
Learn more: https://www.alertlogic.com/neweconomics
Understanding the 8 Keys to Security Success

CISOS work hard to manage risk and ensure the security of the organization. But, they must also create an environment where business can be transacted seamlessly, conveniently and securely. With over a decade of supporting organizations in this mission, Security On-Demand has compiled the eight keys to security success which will help you achieve your goals of delivering security and business agility.
Ernst & Young visuals security survey 2012

Risk and Security not always aligned. Not enough non IT focus on security. Hardly surprising that organisational Information Security needs are not being met in enough organisations.
What is CryptoLocker and How Can I Protect My Business From It?

If your business operates on Windows computers, be on the lookout. Cybercriminals created malicious computer software, called CryptoLocker, which can invade your computer, encrypt your data, and then demand you pay a ransom. Afterwards, you have roughly 72 hours to pay the ransom of at least $200 in bitcoins. If you don’t pay the ransom on time, the price can go up to $2,000. Or don’t pay and lose your data forever, which likely won’t be an option if CryptoLocker encrypted files critical to operating your business, such as legal documents, payroll forms, and customer information.
Video surveillance: Why should my business use it?

We offered advice for monitoring employee computer use. However, you should not forget about the risks to your business inside your office walls. The threats can come from thieves, attackers, competitors, and even your own employees. According to a 2007 American Management Association survey, 48% of companies use video monitoring to prevent theft, violence, and sabotage. Also, the US Department of Commerce notes that employee theft contributes to 30% of business failures. Consider protecting your business with video surveillance. Learn more here: http://bit.ly/1oANVvm
Bridging the Cybersecurity Gap

While board of directors may understand the importance of cybersecurity, many lack crucial knowledge and visibility into issues and risks, which breeds a lack of trust between the board and IT security professionals. On this site, you’ll find a variety of resources to help bridge those gaps and bring the two groups together so organizations can better defend against advanced threats.
Protecting Your Business from a Cyber Attack

Presentation from Armstrong's Insurance Brokers and Eaglecrest Technologies for CPA Australia and Launceston Chamber of Commerce on how to protect your business from a cyber attack.
6 lessons to better business security

Understand the 6 requirements around better business security.
Before you implement them, find out what you need to do.
Take the test and get your report
INFOGRAPHIC▶ Spear Phishing Scammers Sharpen Their Attacks

Attackers win your confidence with personalized, targeted emails.
What's hot (19)
Containing the outbreak: The healthcare security pandemic

Containing the outbreak: The healthcare security pandemic
What is CryptoLocker and How Can I Protect My Business From It?

What is CryptoLocker and How Can I Protect My Business From It?
Video surveillance: Why should my business use it?

Video surveillance: Why should my business use it?
INFOGRAPHIC▶ Spear Phishing Scammers Sharpen Their Attacks

INFOGRAPHIC▶ Spear Phishing Scammers Sharpen Their Attacks
Similar to Common Cybersecurity Mistakes
4 Precautions to Keep Your Supply Chain Data Safe

Supply Chain companies should take a step in developing high-quality risk management strategies and train their employees to identify potential threats and avoid these types of situations.
Cyber Risks & Liabilities - Cyber Security for Small Businesses

High-profile cyber attacks on companies such as Target and Sears have raised awareness of the growing threat of cybercrime. Recent surveys conducted by the Small Business Authority, Symantec, Kaspersky Lab and the National Cybersecurity Alliance suggest that many small business owners are still operating under a false sense of cyber security.
The statistics of these studies are grim; the vast majority of U.S. small businesses lack a formal Internet security policy for employees, and only about half have even rudimentary cybersecurity measures in place. Furthermore, only about a quarter of small business owners have had an outside party test their computer systems to ensure they are hacker proof, and nearly 40 percent do not have their data backed up in more than one location.
How to assess your Cybersecurity Vulnerability_.pdf

The new age of cyber threats is not limited to data breaches and ransomware attacks. They have become much more advanced with AI-based security analysis, crypto-jacking, facial recognition, and voice cloning via deep fake, IoT compromise, and cloud-based DDoS attacks.
How to assess your Cybersecurity Vulnerability_.pptx

Surprisingly, Deepfake Technology, which was once used for fun, has now enabled phishing attacks. Rick McRoy detected a deep fake-based voice call that caused a CEO to transfer a sum amount of $35 Million.
Further, AI-powered cyberattacks also pose a serious security risk. Existing cybersecurity tools are not enough to counter this cyber weaponry.
In the wake of such incidents, the need for advanced cybersecurity tools is growing important.
The Small Business Cyber Security Best Practice Guide

Cyber security is a big problem for small business.
Small business is the target of 43% of all
cybercrimes.
• 60% of small businesses who experience a
significant cyber breach go out of business within the
following
6 months.
• 22% of small businesses that were breached by the
2017 Ransomware attacks were so affected they could
not continue operating.
• 33% of businesses with fewer than 100 employees
don’t take proactive measures against cyber security
breaches.
• 87% of small businesses believe their business is
safe from cyberattacks because they use antivirus
software alone.
• Cybercrime costs the Australian economy more than
$1bn annually.
BIZGrowth Strategies — Cybersecurity Special Edition 2023

As cybercriminals continue to advance and evolve, a stagnant cyber risk management approach is simply not an option. Further, the prevalence of cyber breaches means cybersecurity is not solely an IT concern. It takes a robust set of processes and people from across your organization, working together toward a common goal. We offer fresh insights to help protect your organization from cyberthreats in multiple operational areas. Articles include:
- How Cybercriminals Are Weaponizing Artificial Intelligence
- Employee Benefits Cyber Risk Exposure Scorecard
- Closing the Security Gap: Managing Vendor Cyber Risk
- Retirement Plan Sponsor Cybersecurity Checklist
- Protect Your Digital Frontline With Employee Training
Human Error in Cyber Security Breaches | Cyberroot Risk Advisory

When it comes to cybersecurity, human error is to blame for either inadvertent or inaction-related data breaches.
Netwealth educational webinar: Peace of mind in a digital world

According to the latest research from cyber security firm, Kamino, 45% of financial advisers had experienced a cyber incident last year.
Julian Plummer, founder of Kamino, delves into why cyber security is a very real issue for financial advisers and their clients, and the types of cyber incidents that are impacting the financial planning industry. He also provides easy to implement measures to help you improve the cyber security of your practice.
Measures to Avoid Cyber-attacks

We are a new generation IT Software Company, helping our customers to optimize their IT investments, while preparing them for the best-in-class operating model, for delivering that “competitive edge” in their marketplace.
Measure To Avoid Cyber Attacks

cyberattacks on the rise, cybersecurity is crucial for businesses of all sizes. Companies should invest in effective attack and defensive strategies.
Why Should A Business Worry about Cyber Attacks?

In May 2017, Cybersecurity Malaysia confirm the "WannaCry" ransom ware attack spread across Malaysia.
The attack, which locks computers and holds users' files for ransom reported to hit 200,000 victims in 150
countries. The National Health Service reported the massive ransom ware attack shut down work at 16
hospitals across the United Kingdom. Hackers threaten to delete patient records and other critical files if
hospitals don’t pay them.
Фишинг — проклятие или возможность для ИБ? 

Можно ли научить людей тому, чему они не желают учиться? Можно ли превратить слабое звено в союзника службы ИБ и какими инструментами для этого пользоваться? Опыт «Лаборатории Касперского».
5 Reasons Cyber Attackers Target Small and Medium Businesses 

High-profile data breaches of corporate giants make the headlines. But 77% of cyber crime actually targets small and midsize enterprises (SMEs). Here's why SMEs are targets, and what you can do about it.
Mark Villinski - Top 10 Tips for Educating Employees about Cybersecurity

Corporate cybercrime is usually blamed on outsiders, but sometimes, your employees can represent the biggest threat to your organization’s IT security. In this presentation, Kaspersky Lab’s Mark Villinski, will provide practical advice for educating your employees about cybersecurity. Attend to learn:
• How to create efficient and effective security policies
• Overview and statistics of the current threat landscape
• The importance of keeping your employees updated about the latest threats and scams
• Security solutions that can help keep your systems updated and protected
How to Protect Your Business from Cyber Threats | The Entrepreneur Review

Common Cyber Threats and How to Protect Your Business 1. Phishing Attacks 2. Malware and Ransomware 3. Weak Passwords 4. Unsecured Wi-Fi Networks 5. Lack of Employee Awareness 6. Outdated Software 7. Third-party Risks
Cyber liability and cyber security

An overview of Cyber Liability insurance and cyber security tips for small businesses.
Cyber security do your part be the resistance

"Cybercriminals are more aggressive and technically proficient - they are professional, industrialized with well-defined organizational structures" "It’s now more than ever IT security professionals, businesses, agencies, and authorities need to collaborate and function as a unified force, exchanging resources, information, and intelligence to reduce the threat of Cybercriminal activities."
10 Most Important Strategies for Cybersecurity Risk Mitigation.pdf

Businesses and organisations of all sizes are growing more and more concerned about cyber security. The potential for cyber dangers increases dramatically as technology becomes more pervasive in our daily lives. A successful cyber-attack can have disastrous repercussions, including but not limited to financial loss, negative reputation, and even legal repercussions.
Similar to Common Cybersecurity Mistakes (20)
Cyber Risks & Liabilities - Cyber Security for Small Businesses

Cyber Risks & Liabilities - Cyber Security for Small Businesses
How to assess your Cybersecurity Vulnerability_.pdf

How to assess your Cybersecurity Vulnerability_.pdf
How to assess your Cybersecurity Vulnerability_.pptx

How to assess your Cybersecurity Vulnerability_.pptx
The Small Business Cyber Security Best Practice Guide

The Small Business Cyber Security Best Practice Guide
BIZGrowth Strategies — Cybersecurity Special Edition 2023

BIZGrowth Strategies — Cybersecurity Special Edition 2023
Human Error in Cyber Security Breaches | Cyberroot Risk Advisory

Human Error in Cyber Security Breaches | Cyberroot Risk Advisory
Netwealth educational webinar: Peace of mind in a digital world

Netwealth educational webinar: Peace of mind in a digital world
5 Reasons Cyber Attackers Target Small and Medium Businesses 

5 Reasons Cyber Attackers Target Small and Medium Businesses
Mark Villinski - Top 10 Tips for Educating Employees about Cybersecurity

Mark Villinski - Top 10 Tips for Educating Employees about Cybersecurity
How to Protect Your Business from Cyber Threats | The Entrepreneur Review

How to Protect Your Business from Cyber Threats | The Entrepreneur Review
10 Most Important Strategies for Cybersecurity Risk Mitigation.pdf

10 Most Important Strategies for Cybersecurity Risk Mitigation.pdf
Recently uploaded
Cracking the Workplace Discipline Code Main.pptx

Cultivating and maintaining discipline within teams is a critical differentiator for successful organisations.
Forward-thinking leaders and business managers understand the impact that discipline has on organisational success. A disciplined workforce operates with clarity, focus, and a shared understanding of expectations, ultimately driving better results, optimising productivity, and facilitating seamless collaboration.
Although discipline is not a one-size-fits-all approach, it can help create a work environment that encourages personal growth and accountability rather than solely relying on punitive measures.
In this deck, you will learn the significance of workplace discipline for organisational success. You’ll also learn
• Four (4) workplace discipline methods you should consider
• The best and most practical approach to implementing workplace discipline.
• Three (3) key tips to maintain a disciplined workplace.
The effects of customers service quality and online reviews on customer loyal...

The effects of customers service quality and online reviews on customer loyal...balatucanapplelovely
Research ModelingMarketingStrategiesMKS.CollumbiaUniversitypdf

Implicitly or explicitly all competing businesses employ a strategy to select a mix
of marketing resources. Formulating such competitive strategies fundamentally
involves recognizing relationships between elements of the marketing mix (e.g.,
price and product quality), as well as assessing competitive and market conditions
(i.e., industry structure in the language of economics).
An introduction to the cryptocurrency investment platform Binance Savings.

Learn how to use Binance Savings to expand your bitcoin holdings. Discover how to maximize your earnings on one of the most reliable cryptocurrency exchange platforms, as well as how to earn interest on your cryptocurrency holdings and the various savings choices available.
Meas_Dylan_DMBS_PB1_2024-05XX_Revised.pdf

Personal Brand Statement:
As an Army veteran dedicated to lifelong learning, I bring a disciplined, strategic mindset to my pursuits. I am constantly expanding my knowledge to innovate and lead effectively. My journey is driven by a commitment to excellence, and to make a meaningful impact in the world.
Recruiting in the Digital Age: A Social Media Masterclass

In this masterclass, presented at the Global HR Summit on 5th June 2024, Luan Wise explored the essential features of social media platforms that support talent acquisition, including LinkedIn, Facebook, Instagram, X (formerly Twitter) and TikTok.
VAT Registration Outlined In UAE: Benefits and Requirements

Vat Registration is a legal obligation for businesses meeting the threshold requirement, helping companies avoid fines and ramifications. Contact now!
https://viralsocialtrends.com/vat-registration-outlined-in-uae/
Putting the SPARK into Virtual Training.pptx

This 60-minute webinar, sponsored by Adobe, was delivered for the Training Mag Network. It explored the five elements of SPARK: Storytelling, Purpose, Action, Relationships, and Kudos. Knowing how to tell a well-structured story is key to building long-term memory. Stating a clear purpose that doesn't take away from the discovery learning process is critical. Ensuring that people move from theory to practical application is imperative. Creating strong social learning is the key to commitment and engagement. Validating and affirming participants' comments is the way to create a positive learning environment.
Agency Managed Advisory Board As a Solution To Career Path Defining Business ...

Agency Managed Advisory Board
3.0 Project 2_ Developing My Brand Identity Kit.pptx

A personal brand exploration presentation summarizes an individual's unique qualities and goals, covering strengths, values, passions, and target audience. It helps individuals understand what makes them stand out, their desired image, and how they aim to achieve it.
Exploring Patterns of Connection with Social Dreaming

Exploring Patterns of Connection -Introduction to Social Dreaming
#Systems Psychodynamics
#Innovation
#Creativity
#Consultancy
#Coaching
Discover the innovative and creative projects that highlight my journey throu...

Discover the innovative and creative projects that highlight my journey through Full Sail University. Below, you’ll find a collection of my work showcasing my skills and expertise in digital marketing, event planning, and media production.
Company Valuation webinar series - Tuesday, 4 June 2024

This session provided an update as to the latest valuation data in the UK and then delved into a discussion on the upcoming election and the impacts on valuation. We finished, as always with a Q&A
Recently uploaded (20)
The effects of customers service quality and online reviews on customer loyal...

The effects of customers service quality and online reviews on customer loyal...
ModelingMarketingStrategiesMKS.CollumbiaUniversitypdf

ModelingMarketingStrategiesMKS.CollumbiaUniversitypdf
An introduction to the cryptocurrency investment platform Binance Savings.

An introduction to the cryptocurrency investment platform Binance Savings.
Recruiting in the Digital Age: A Social Media Masterclass

Recruiting in the Digital Age: A Social Media Masterclass
VAT Registration Outlined In UAE: Benefits and Requirements

VAT Registration Outlined In UAE: Benefits and Requirements
The Influence of Marketing Strategy and Market Competition on Business Perfor...

The Influence of Marketing Strategy and Market Competition on Business Perfor...
Bài tập - Tiếng anh 11 Global Success UNIT 1 - Bản HS.doc.pdf

Bài tập - Tiếng anh 11 Global Success UNIT 1 - Bản HS.doc.pdf
Agency Managed Advisory Board As a Solution To Career Path Defining Business ...

Agency Managed Advisory Board As a Solution To Career Path Defining Business ...
3.0 Project 2_ Developing My Brand Identity Kit.pptx

3.0 Project 2_ Developing My Brand Identity Kit.pptx
Exploring Patterns of Connection with Social Dreaming

Exploring Patterns of Connection with Social Dreaming
Set off and carry forward of losses and assessment of individuals.pptx

Set off and carry forward of losses and assessment of individuals.pptx
Discover the innovative and creative projects that highlight my journey throu...

Discover the innovative and creative projects that highlight my journey throu...
Company Valuation webinar series - Tuesday, 4 June 2024

Company Valuation webinar series - Tuesday, 4 June 2024
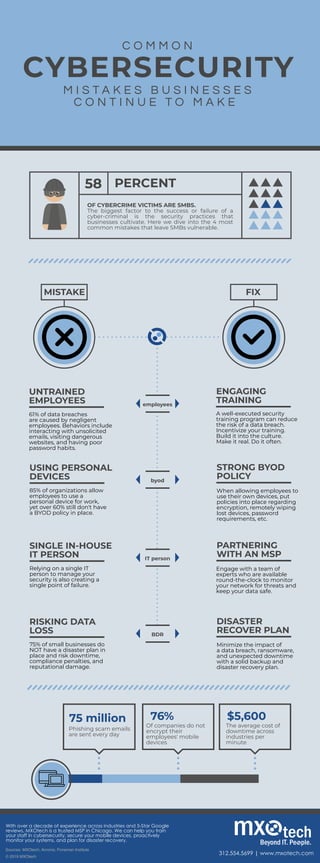
Common Cybersecurity Mistakes
- 1. C O M M O N CYBERSECURITY M I S T A K E S B U S I N E S S E S C O N T I N U E T O M A K E MISTAKE FIX food ENGAGING TRAINING A well-executed security training program can reduce the risk of a data breach. Incentivize your training. Build it into the culture. Make it real. Do it often. UNTRAINED EMPLOYEES 61% of data breaches are caused by negligent employees. Behaviors include interacting with unsolicited emails, visiting dangerous websites, and having poor password habits. 58 PERCENT OF CYBERCRIME VICTIMS ARE SMBS. The biggest factor to the success or failure of a cyber-criminal is the security practices that businesses cultivate. Here we dive into the 4 most common mistakes that leave SMBs vulnerable. employees STRONG BYOD POLICY When allowing employees to use their own devices, put policies into place regarding encryption, remotely wiping lost devices, password requirements, etc. USING PERSONAL DEVICES 85% of organizations allow employees to use a personal device for work, yet over 60% still don't have a BYOD policy in place. byod PARTNERING WITH AN MSP Engage with a team of experts who are available round-the-clock to monitor your network for threats and keep your data safe. SINGLE IN-HOUSE IT PERSON Relying on a single IT person to manage your security is also creating a single point of failure. IT person DISASTER RECOVER PLAN Minimize the impact of a data breach, ransomware, and unexpected downtime with a solid backup and disaster recovery plan. RISKING DATA LOSS 75% of small businesses do NOT have a disaster plan in place and risk downtime, compliance penalties, and reputational damage. BDR Phishing scam emails are sent every day 75 million Of companies do not encrypt their employees' mobile devices 76% The average cost of downtime across industries per minute $5,600 Sources: MXOtech; Acronis; Poneman Institute 312.554.5699 | www.mxotech.com With over a decade of experience across industries and 5-Star Google reviews, MXOtech is a trusted MSP in Chicago. We can help you train your staff in cybersecurity, secure your mobile devices, proactively monitor your systems, and plan for disaster recovery. © 2019 MXOtech