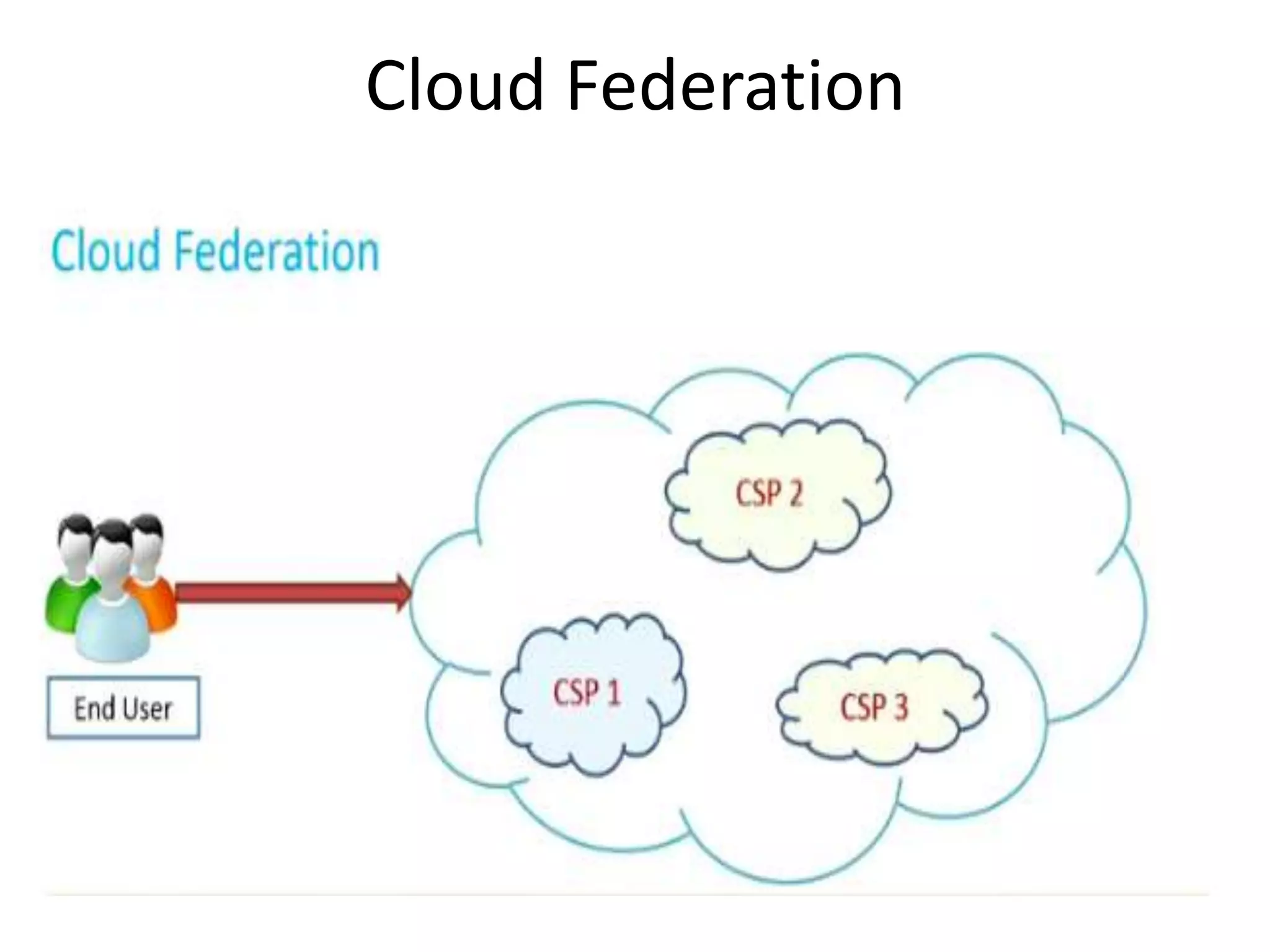
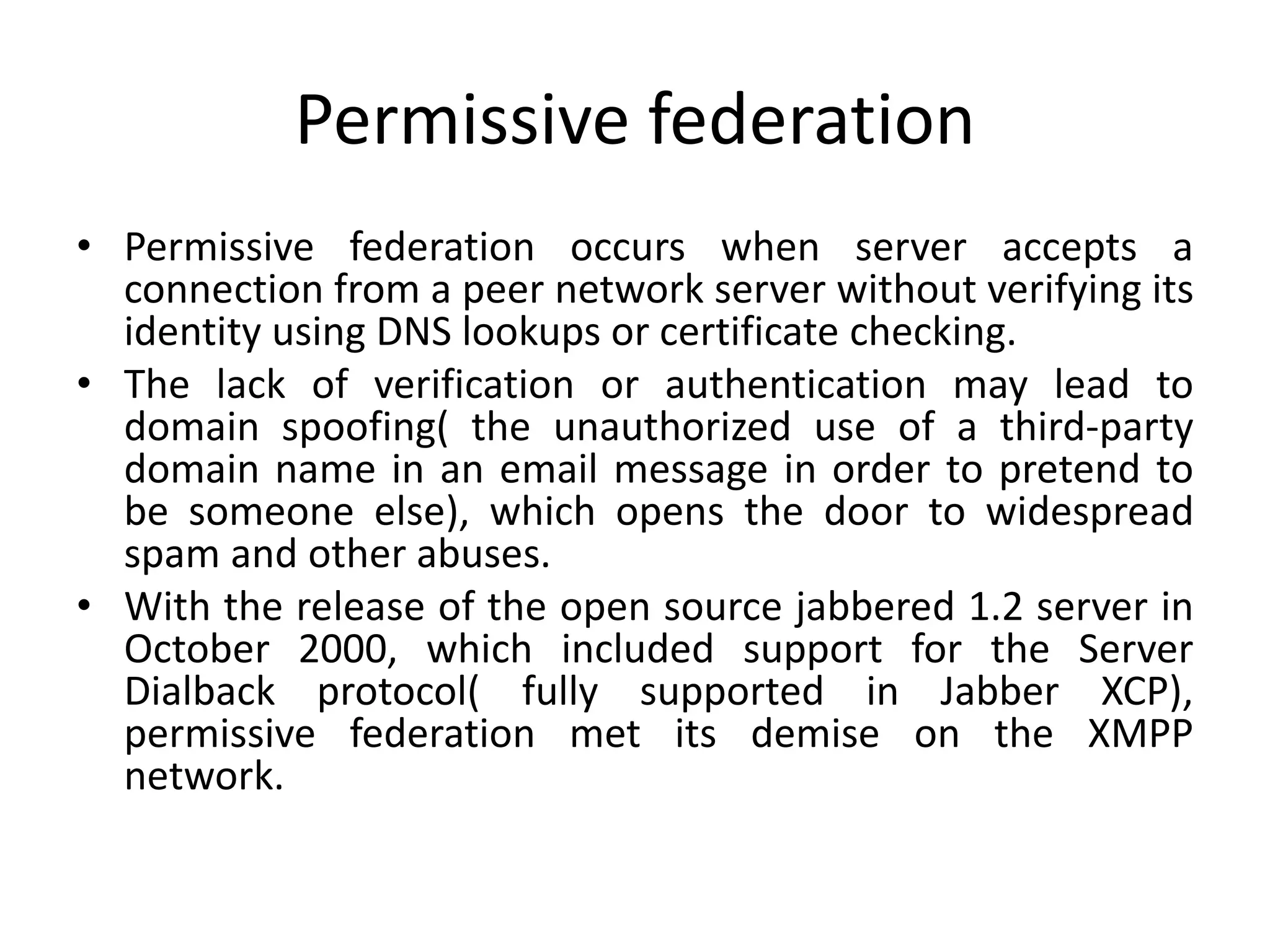
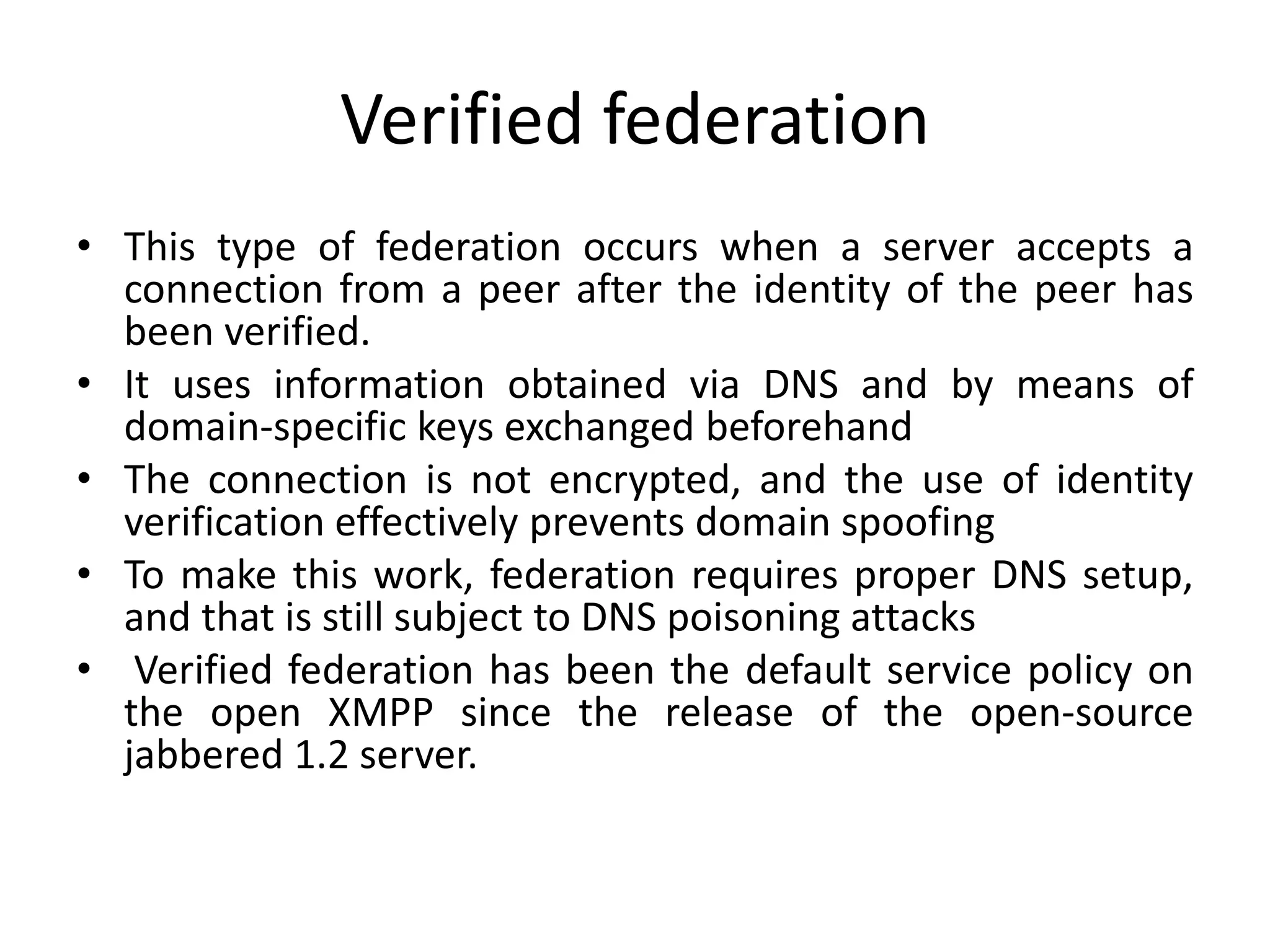
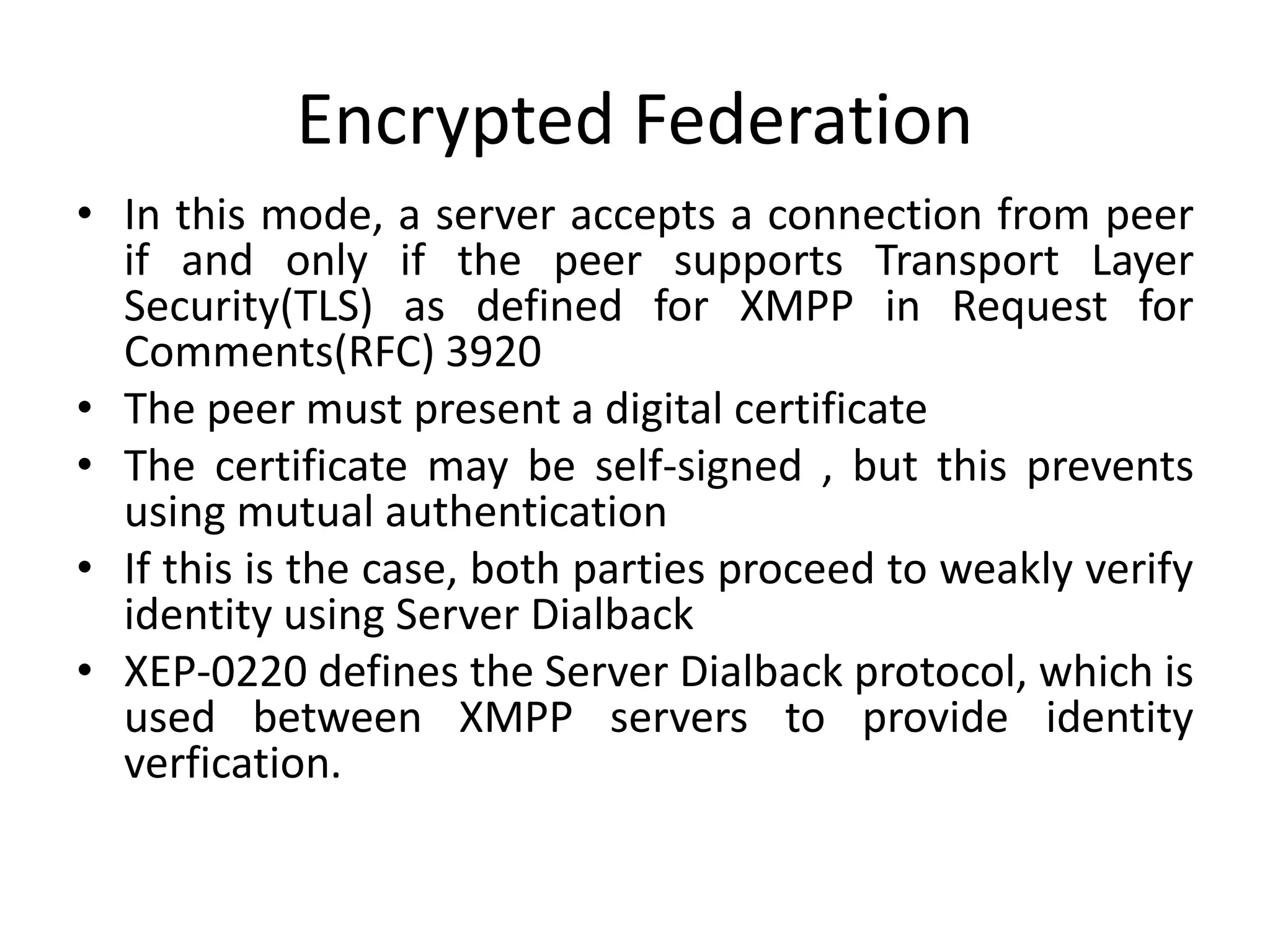
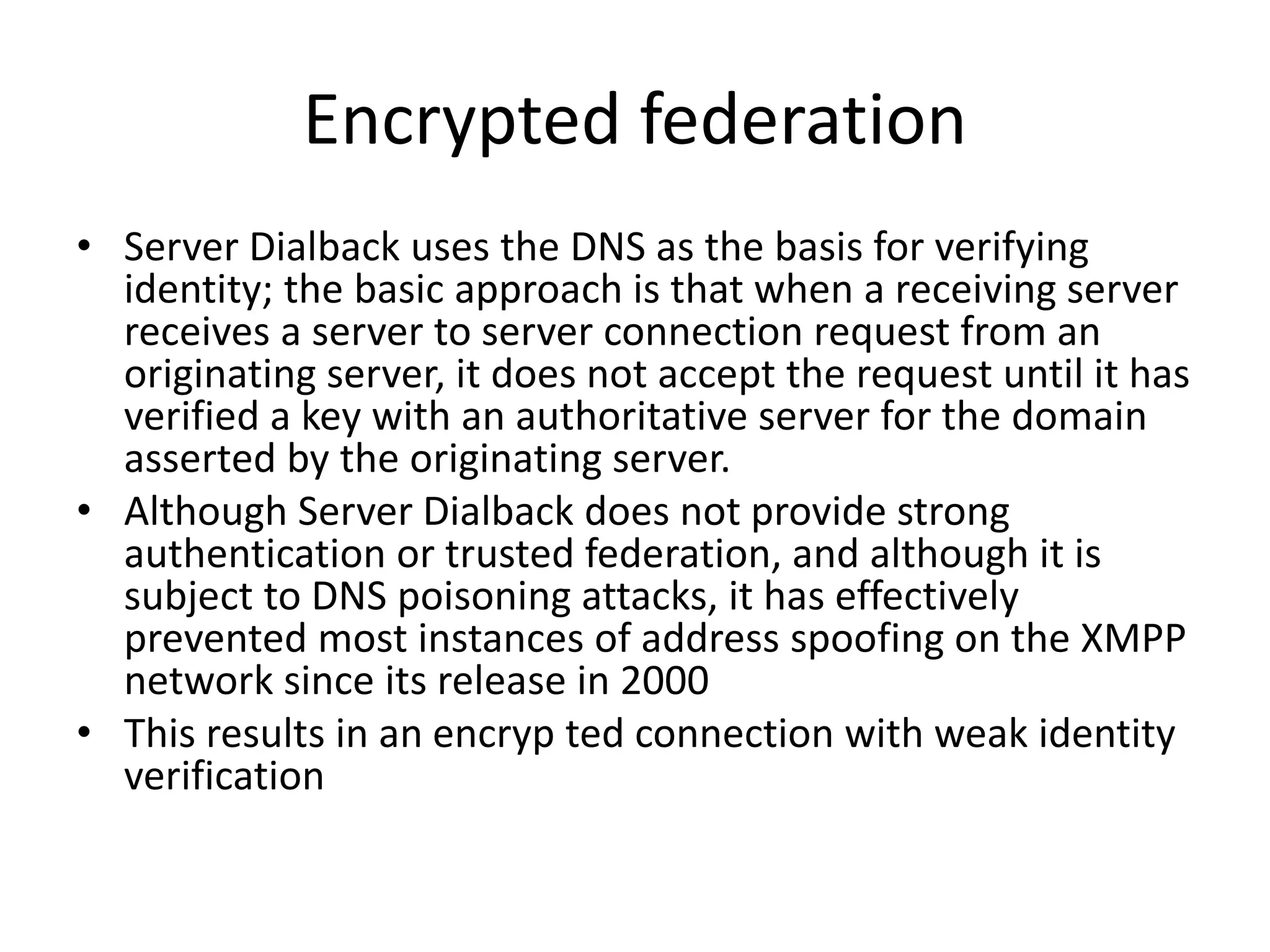
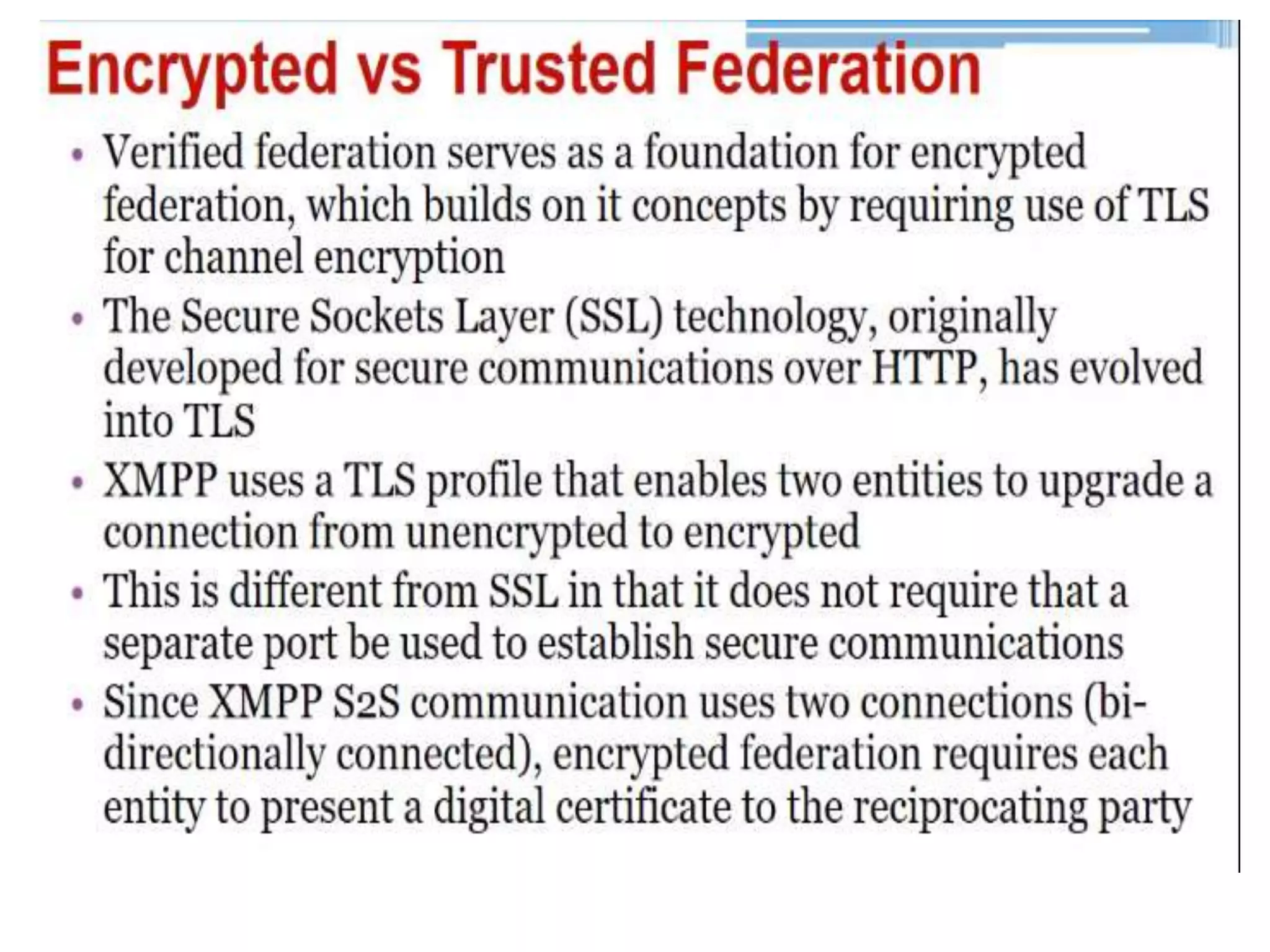
This document discusses cloud federation, which allows independent cloud providers to share resources and balance loads. There are four levels of federation: permissive (no verification), verified (identity verified via DNS), encrypted (TLS-encrypted connection with weak identity verification), and trusted (TLS-encrypted with strong authentication using trusted certificates). Cloud federation provides benefits like efficient resource use, load balancing, failure prevention, and avoiding vendor lock-in.