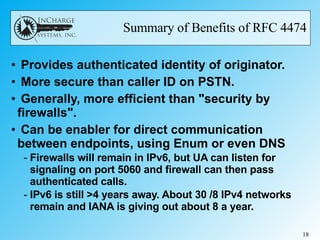
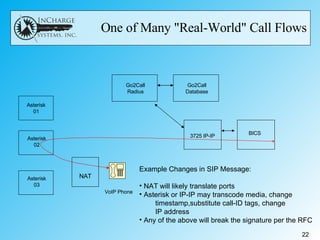
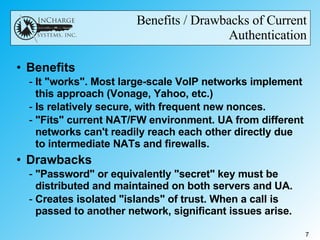
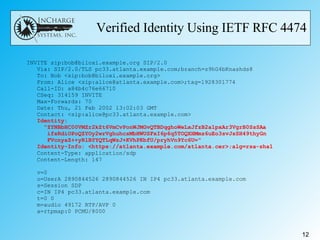
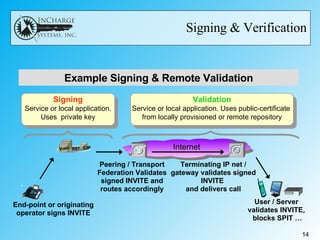
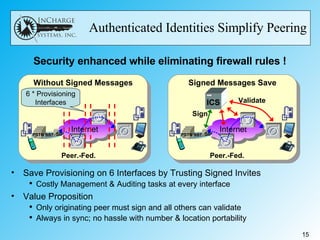
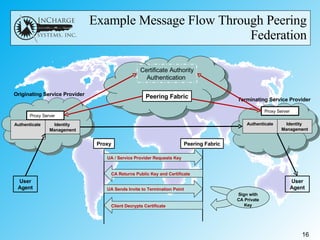
- IETF RFC 4474 proposes using public key infrastructure and certificate signing to authenticate the identity of the originator of SIP messages like INVITE requests. This allows receivers to verify identities and eliminates the need for complex firewall rules between peering networks.
- While it offers security and efficiency benefits, challenges include getting widespread adoption given the "chicken and egg" problem, managing certificates, and handling alterations to SIP messages by network elements that could invalidate signatures.
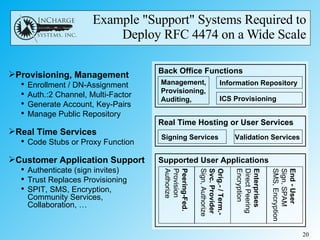
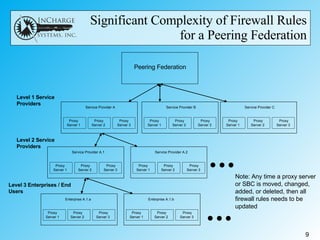
- A reference system is needed to test interoperability, address real-world issues, and potentially revise the RFC based on lessons learned.


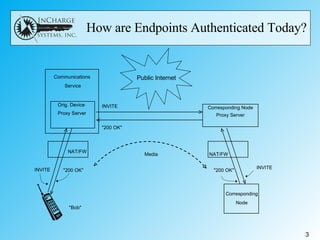







![A "Holy Grail" of VoIP - Direct Communication, Likely Requiring IPv6 CN Firewall Corresponding Node IP Address Public Internet MN FW First Media Stream Second Media Stream RTCP Stream 1 RTCP Stream 2 Mobile Network [2008:0db8::1455:57cd]:12345 2008:0db8::1455:57cd [2008:0db8::1455:57cd]:12345 [2008:0db8::1455:57cd]:12346 [2008:0db8::1455:57cd]:12346 [2008:0db8::1455:57cd]:12345 [1ab2:034f::ccdd:4e8b]:22334 [1ab2:034f::ccdd:4e8b]:22334 1ab2:034f::ccdd:4e8b [2008:0db8::1455:57cd]:12346 [1ab2:034f::ccdd:4e8b]:22335 [1ab2:034f::ccdd:4e8b]:22335 [2008:0db8::1455:57cd]:12346 [1ab2:034f::ccdd:4e8b]:22335 [1ab2:034f::ccdd:4e8b]:22335 [1ab2:034f::ccdd:4e8b]:22334 [2008:0db8::1455:57cd]:12345 [1ab2:034f::ccdd:4e8b]:22334 Signaling (via DNS/Enum) [2008:0db8::1455:57cd]:5060 [2008:0db8::1455:57cd]:5060 [1ab2:034f::ccdd:4e8b]:5060 [1ab2:034f::ccdd:4e8b]:5060](https://image.slidesharecdn.com/presentationtovoiproundtablev2-123980189472-phpapp02/85/Authenticated-Identites-in-VoIP-Call-Control-17-320.jpg)