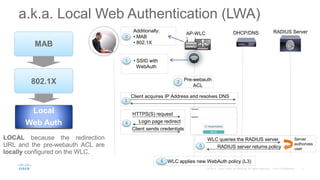
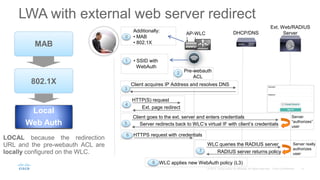
The document provides an overview and comparison of different solutions for wireless guest access management, including WLC native guest, CMX Connect, EMSP, and ISE Guest Portal. It discusses features, use cases, limitations, and configuration examples for each solution. Key information covered includes supported authentication methods, customization options, scalability limits, and integration with external servers.