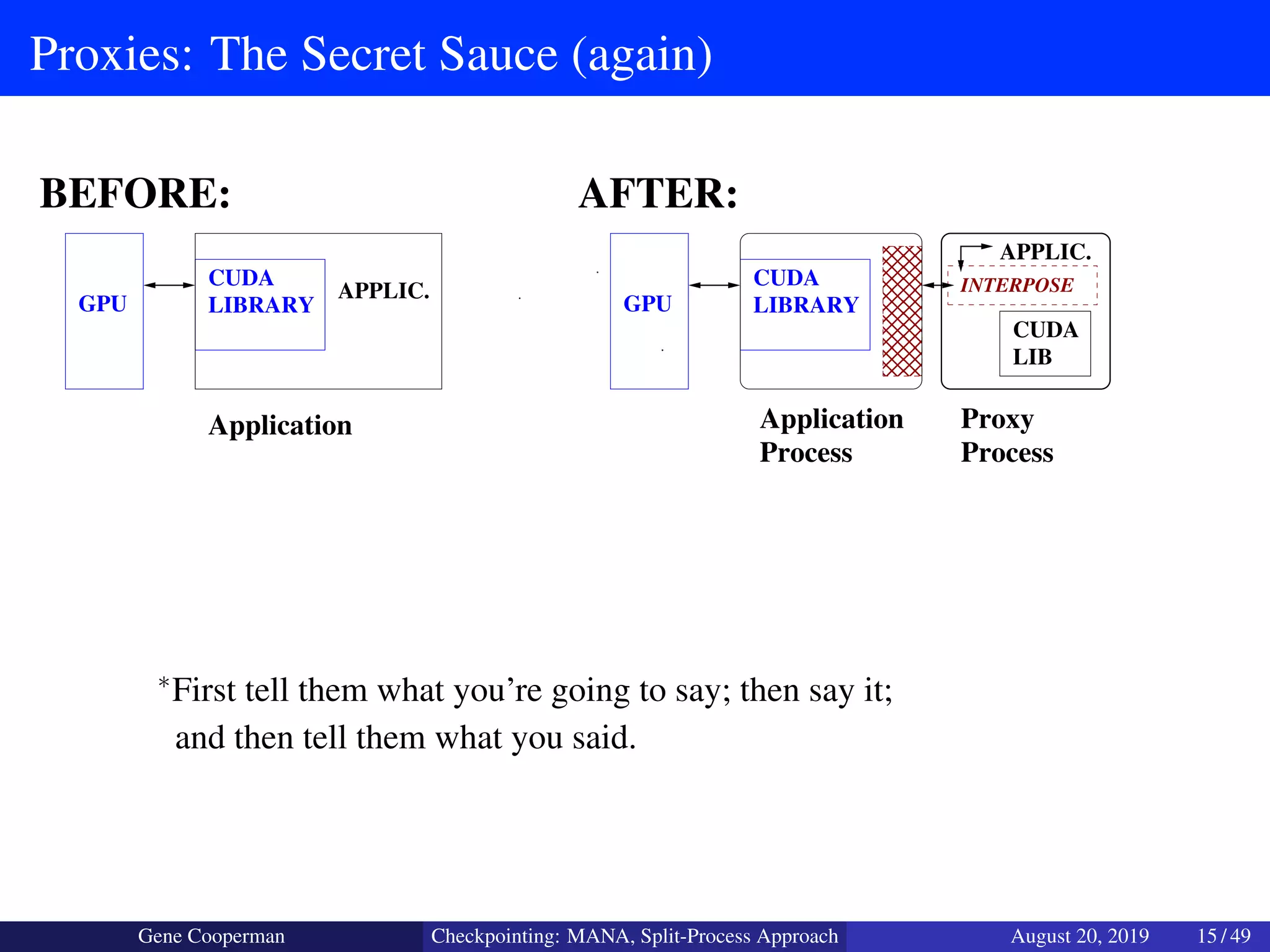
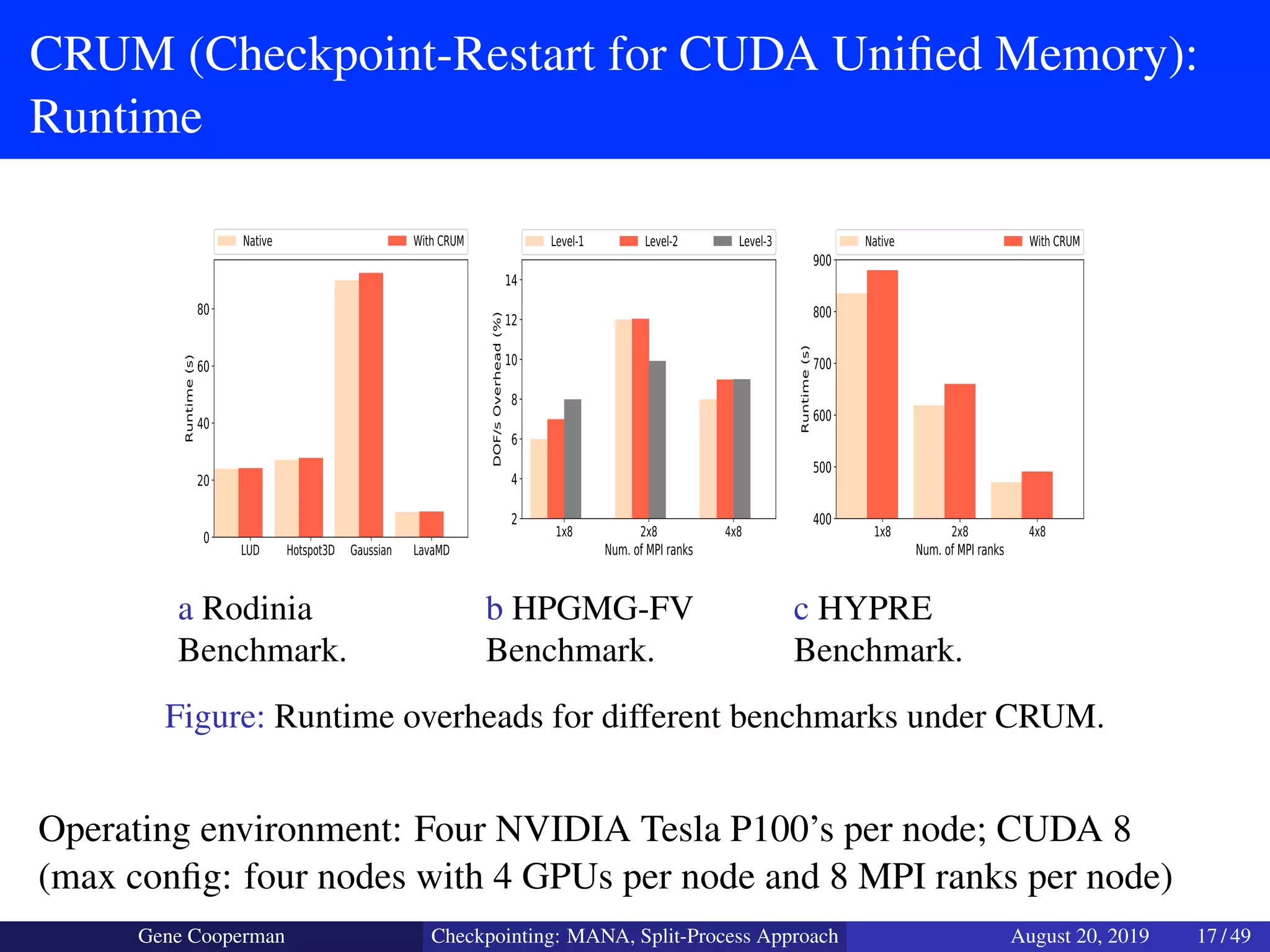
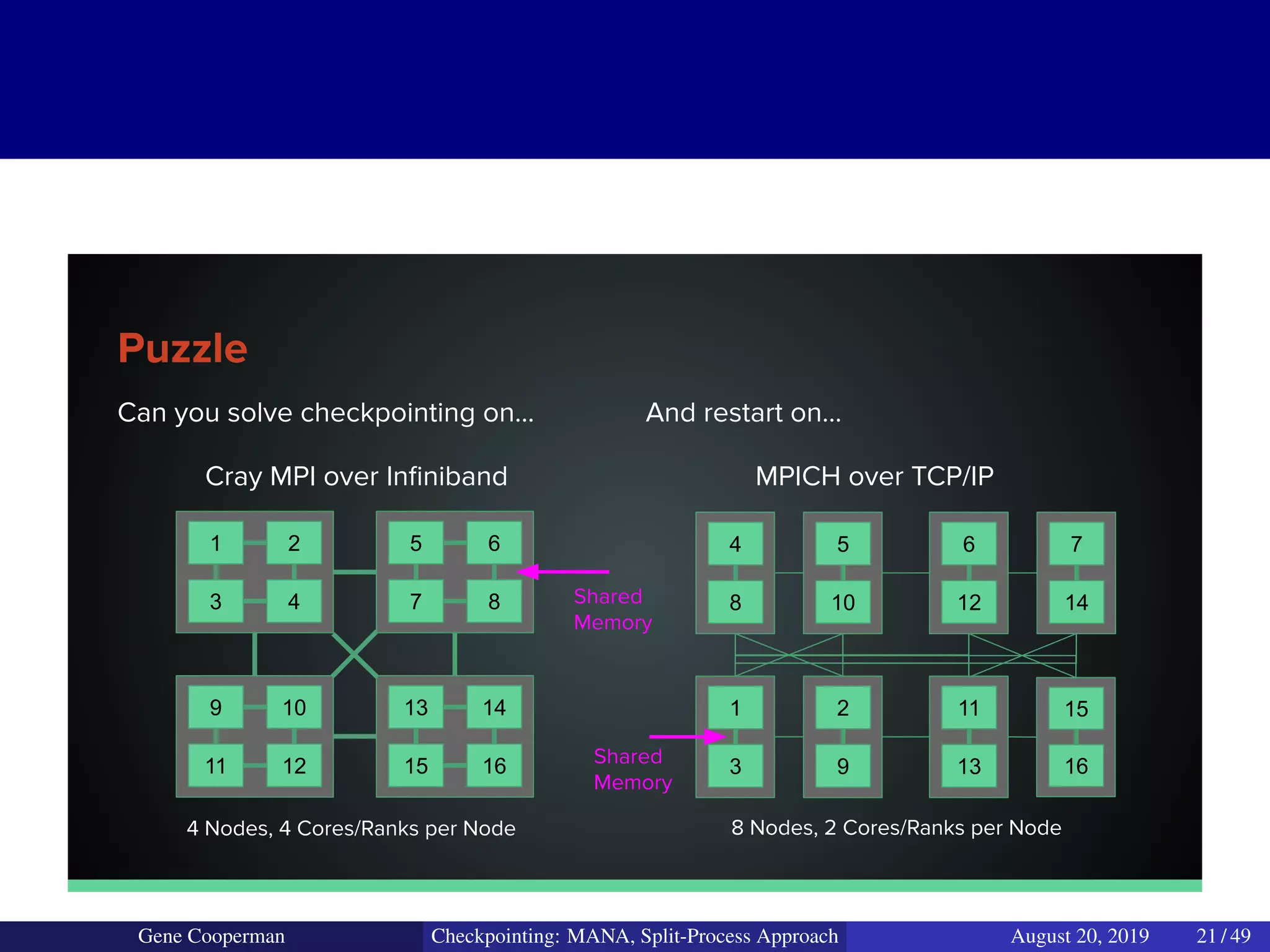
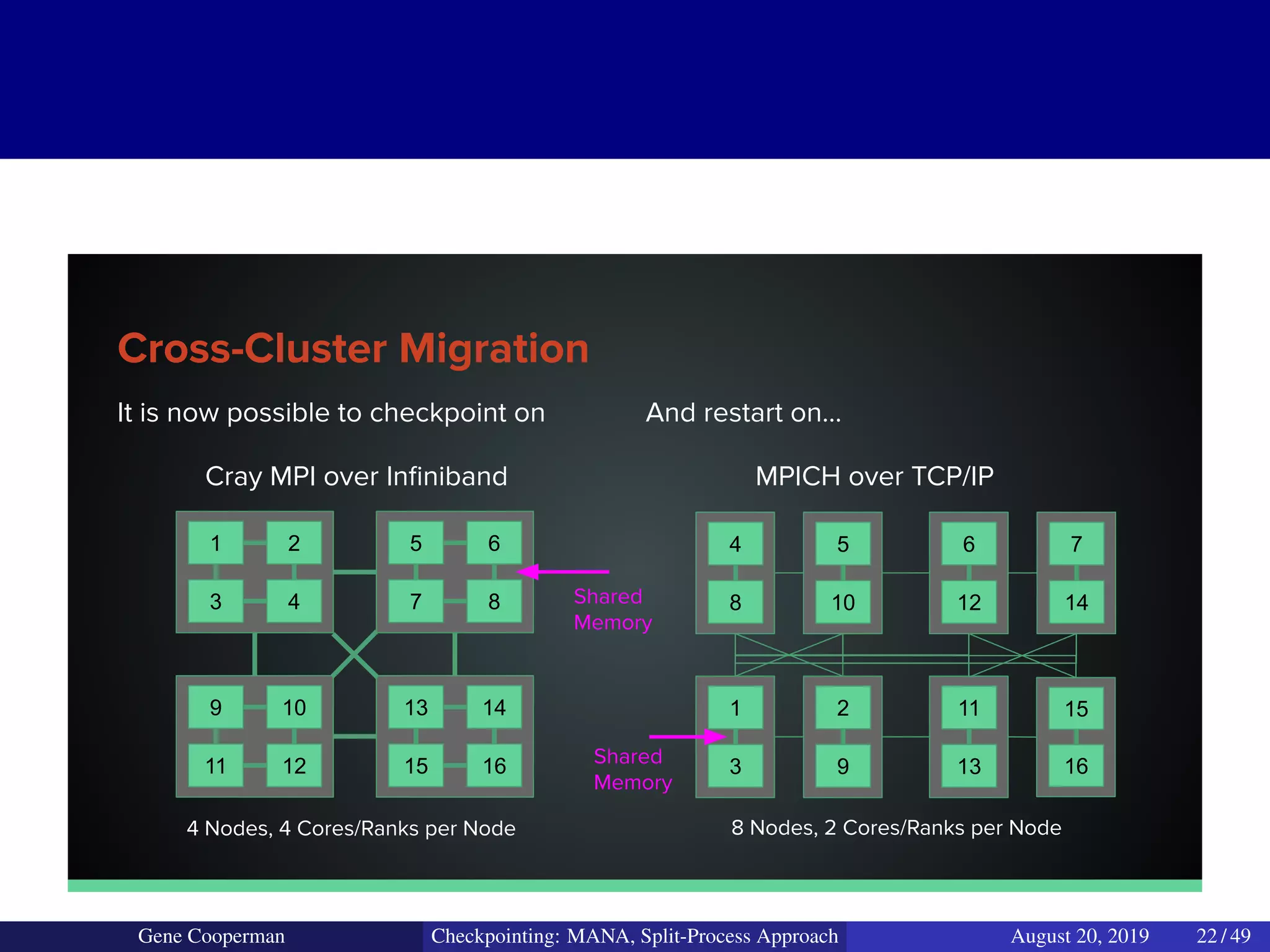
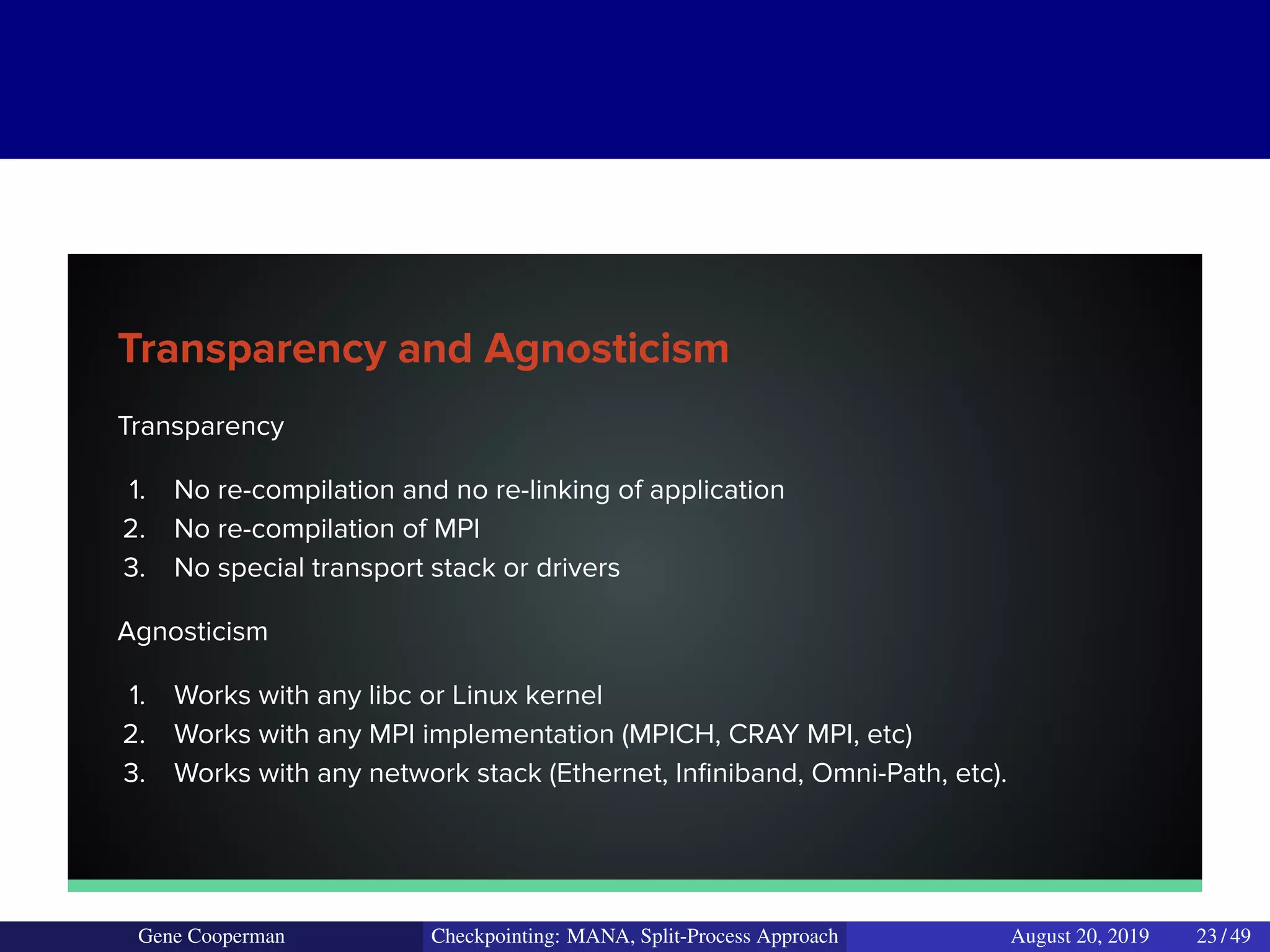
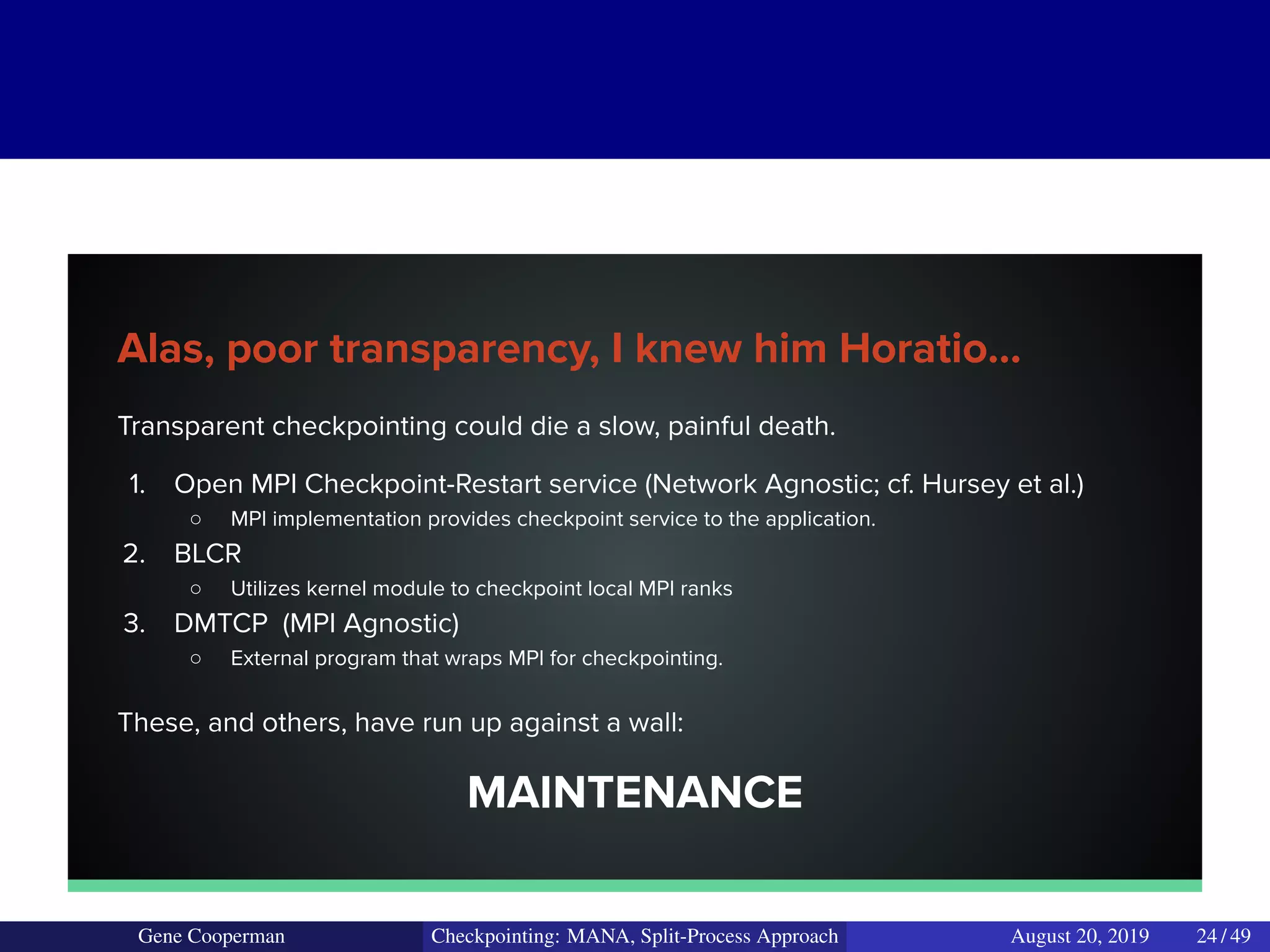
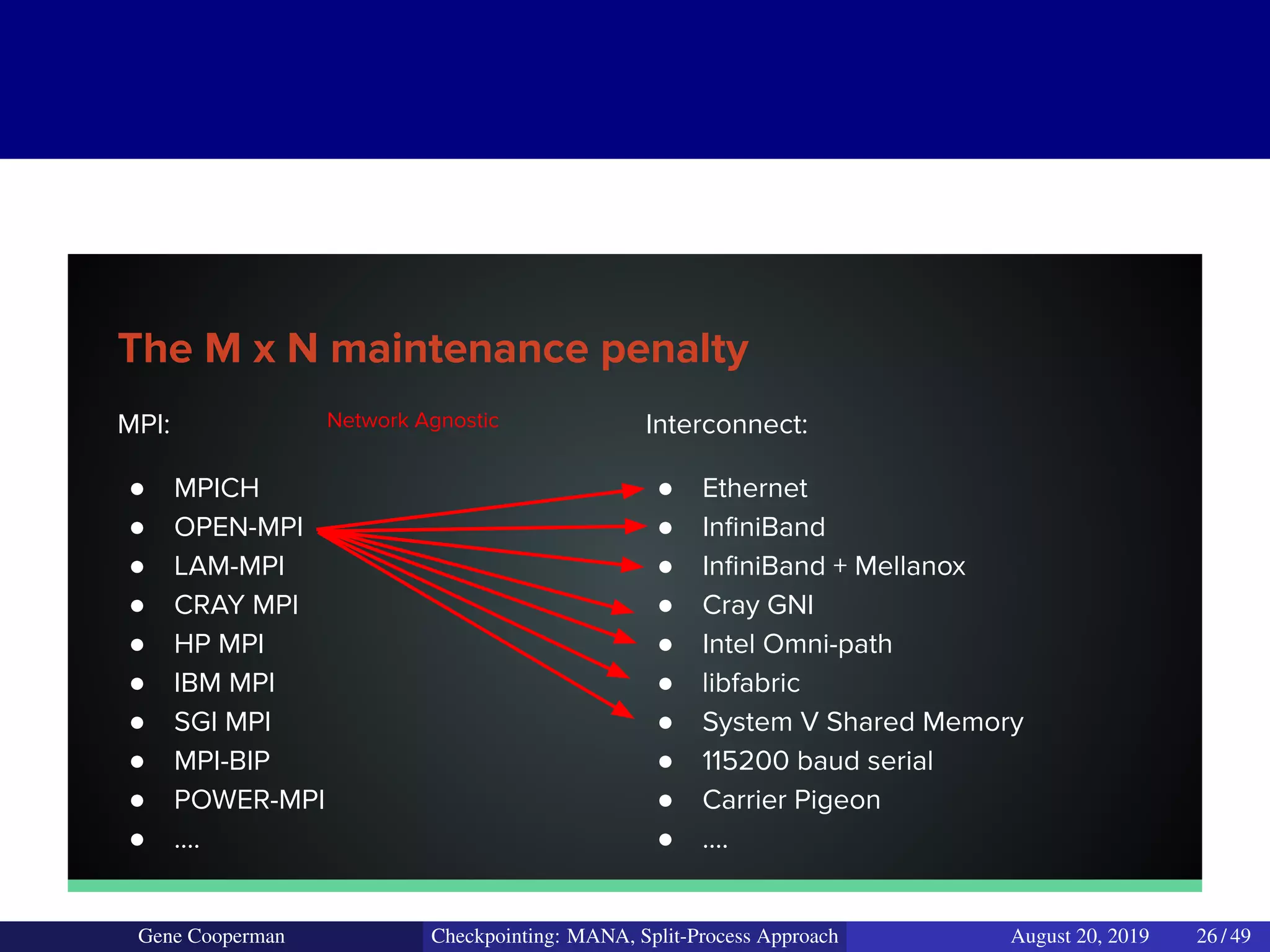
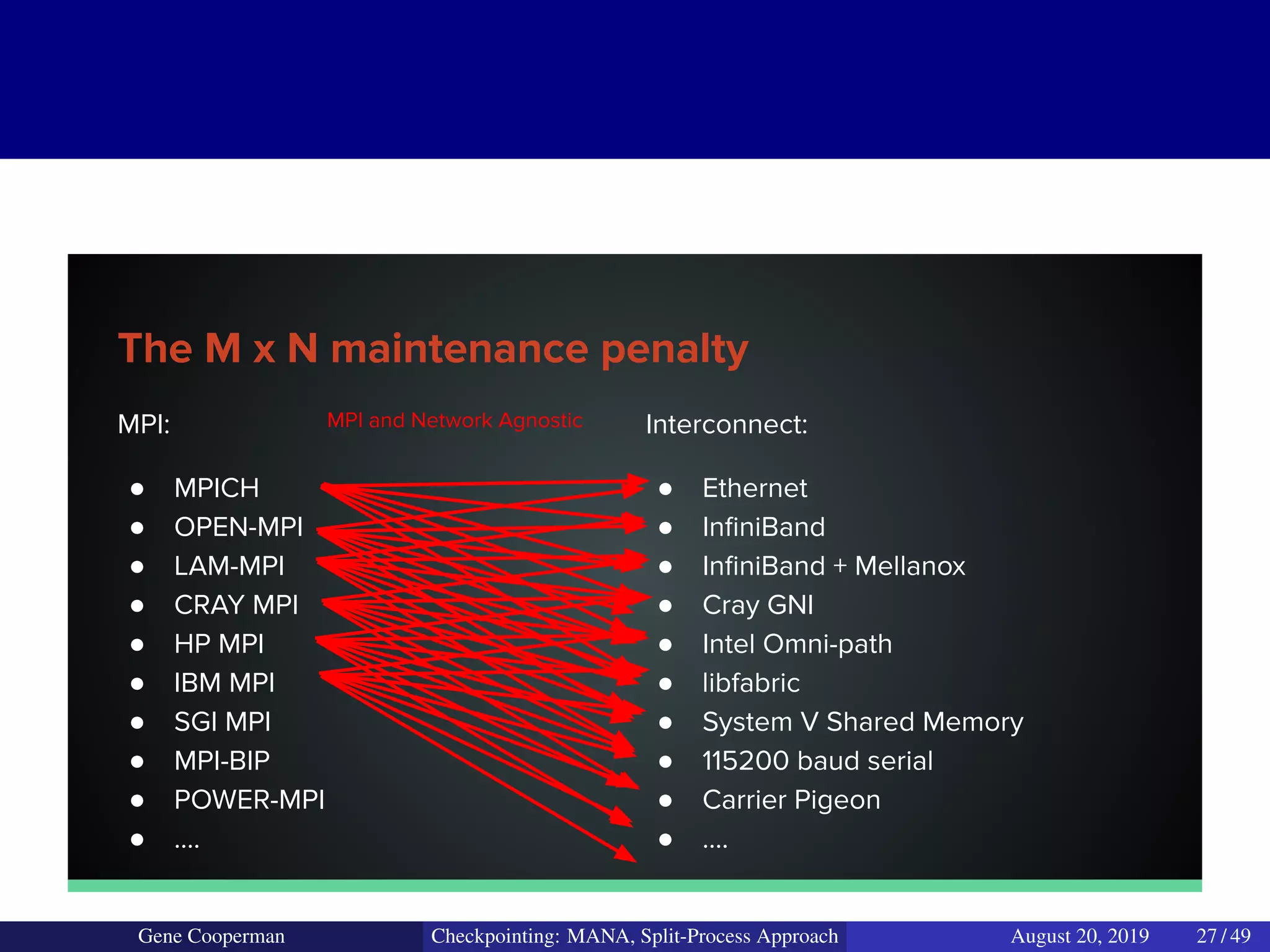
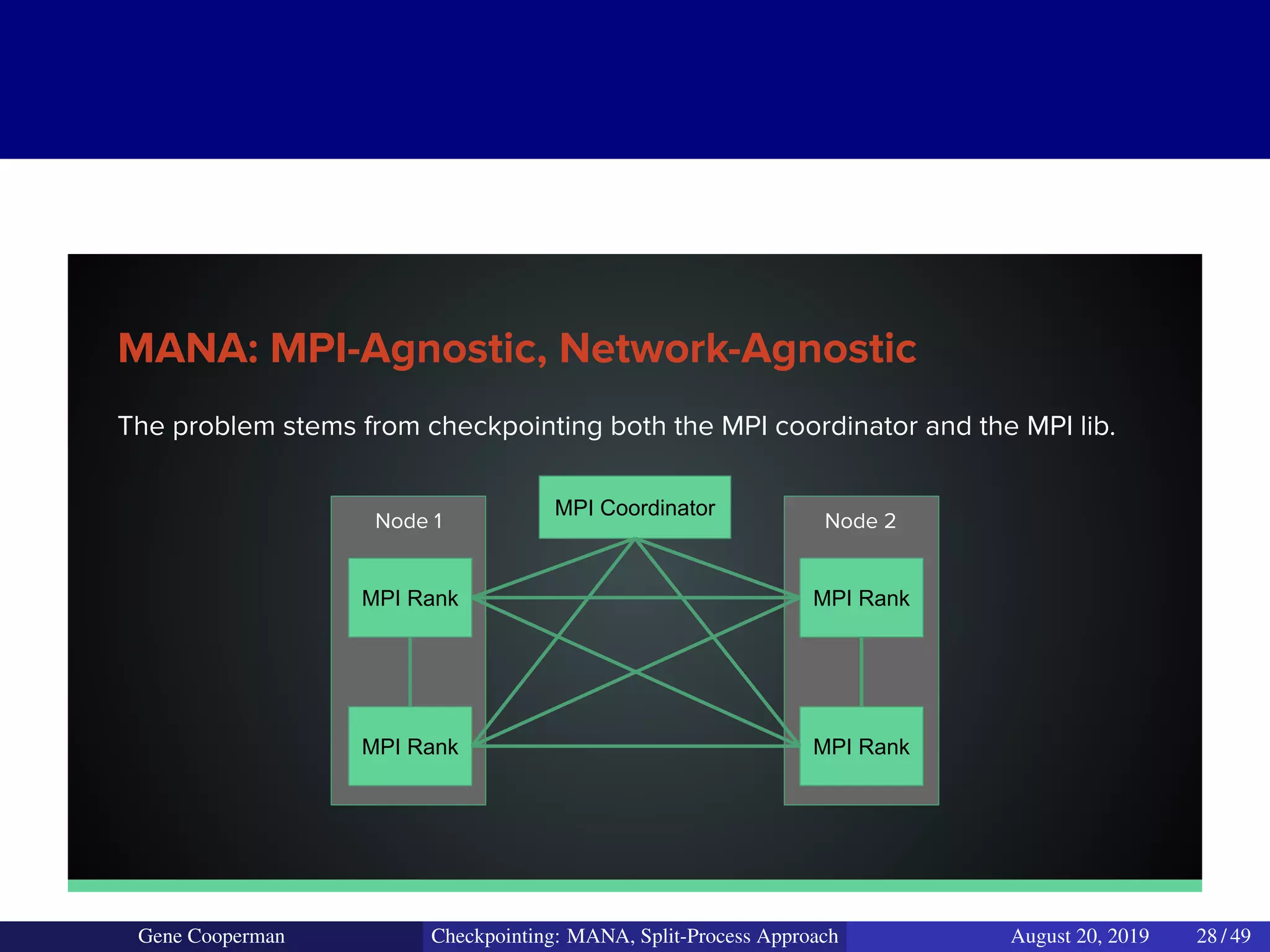
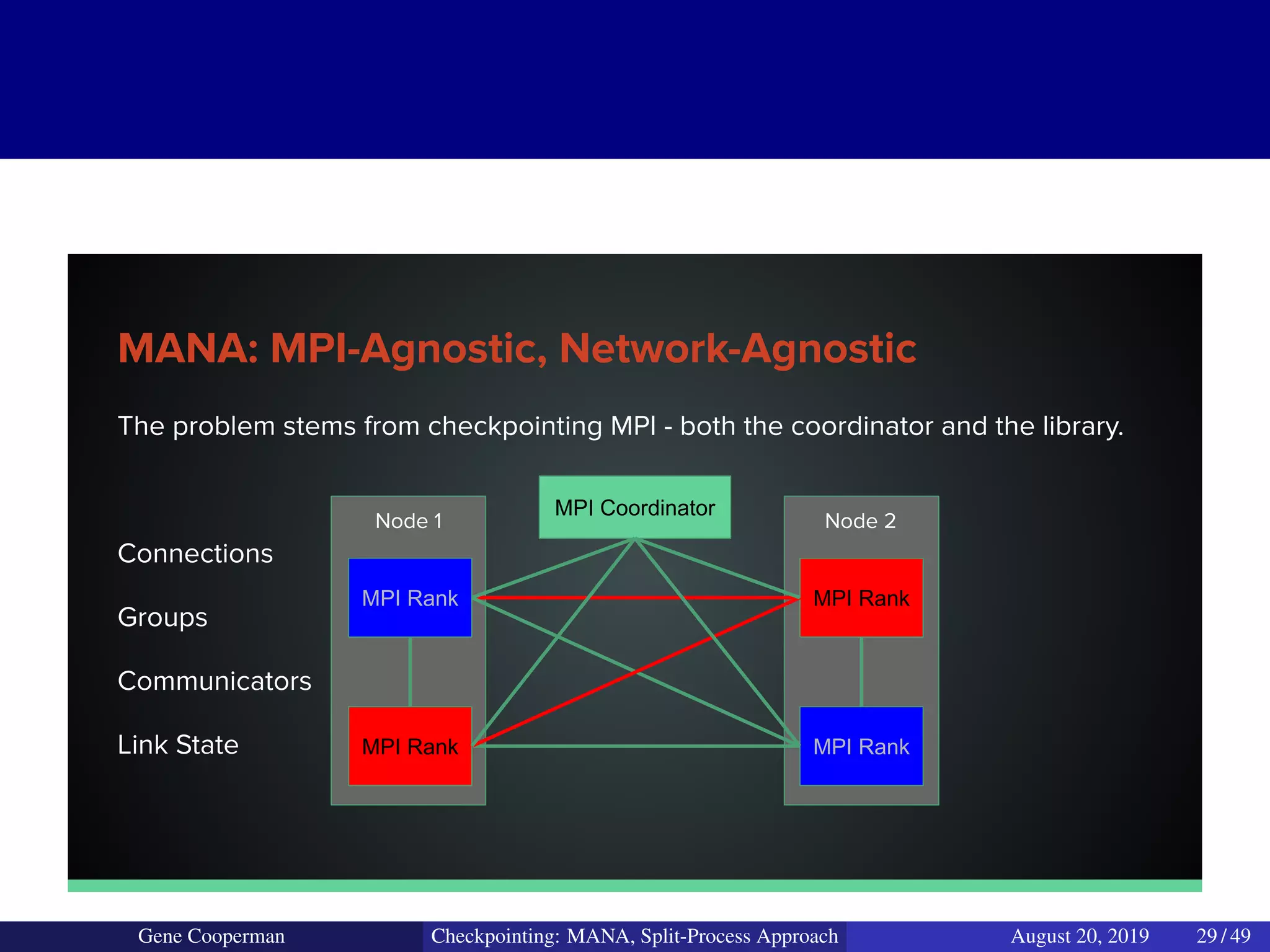
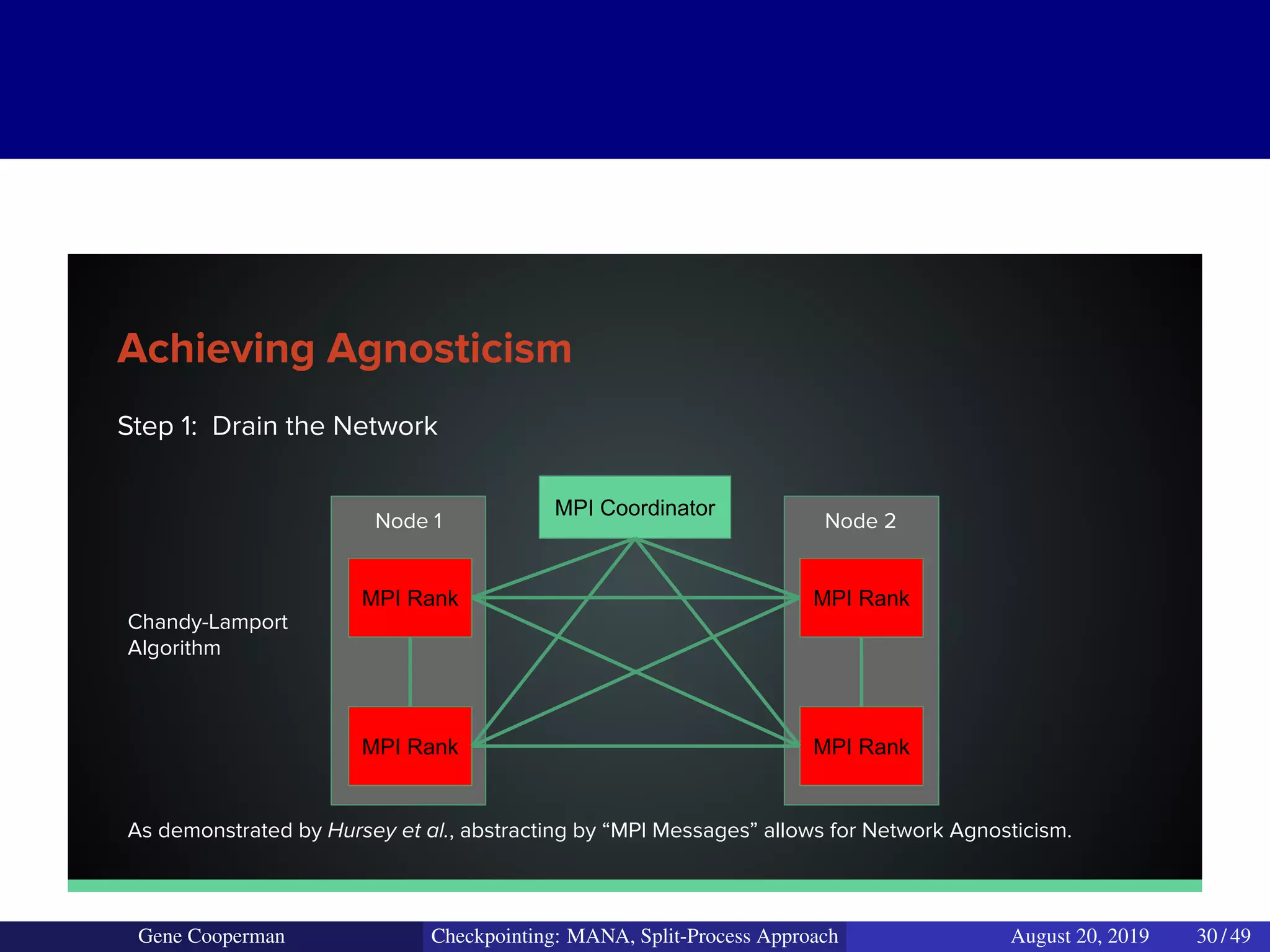
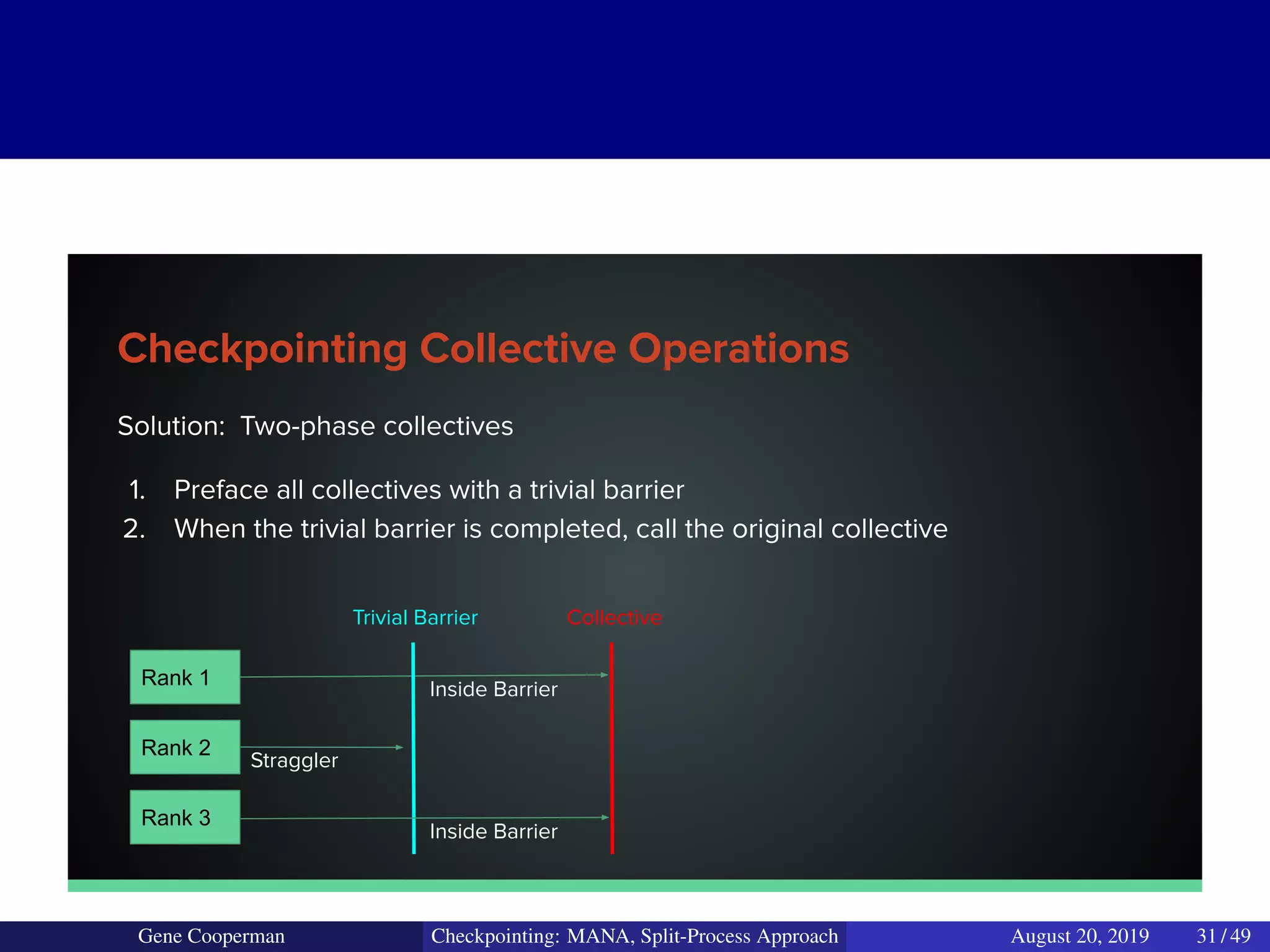
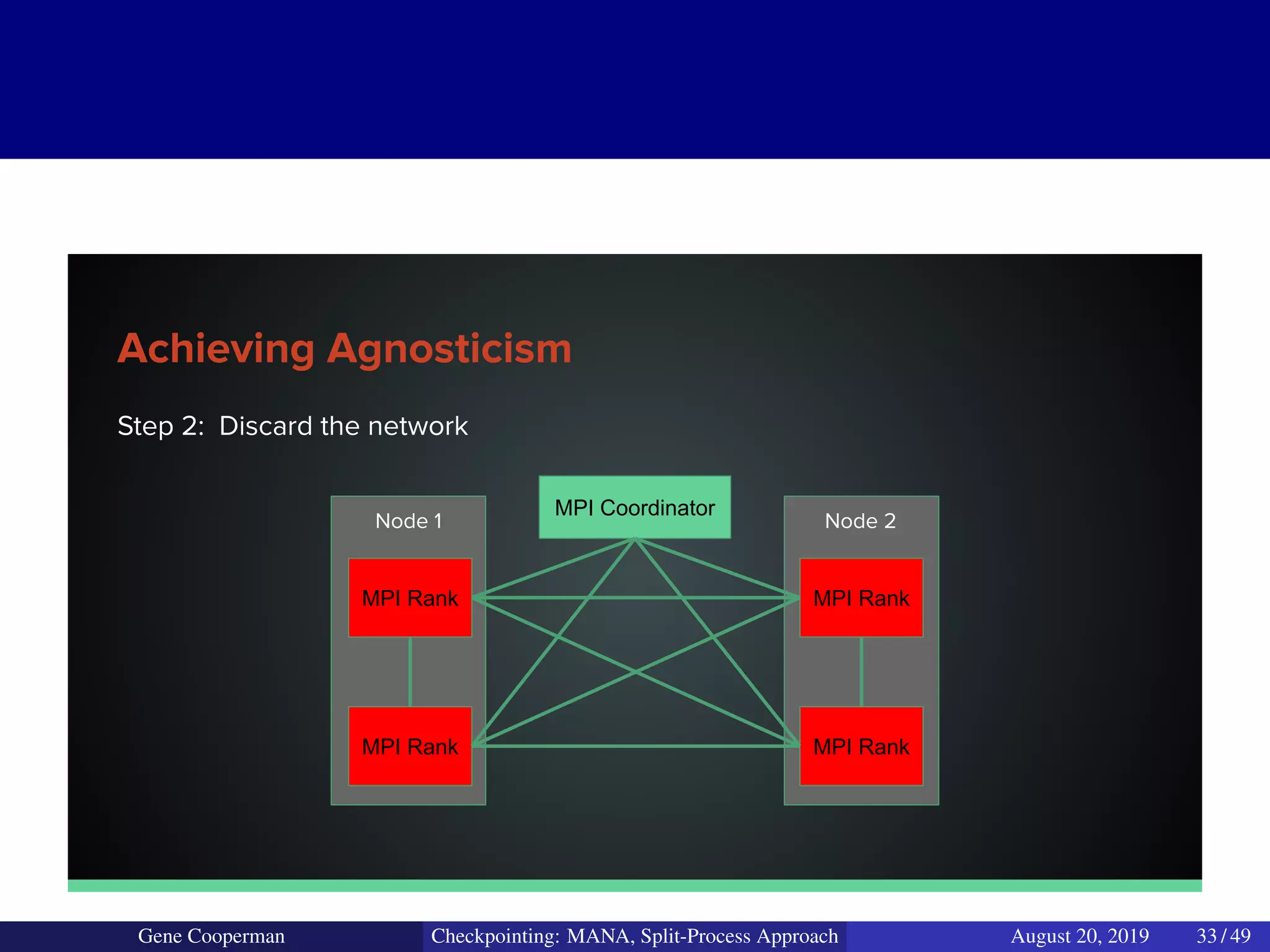
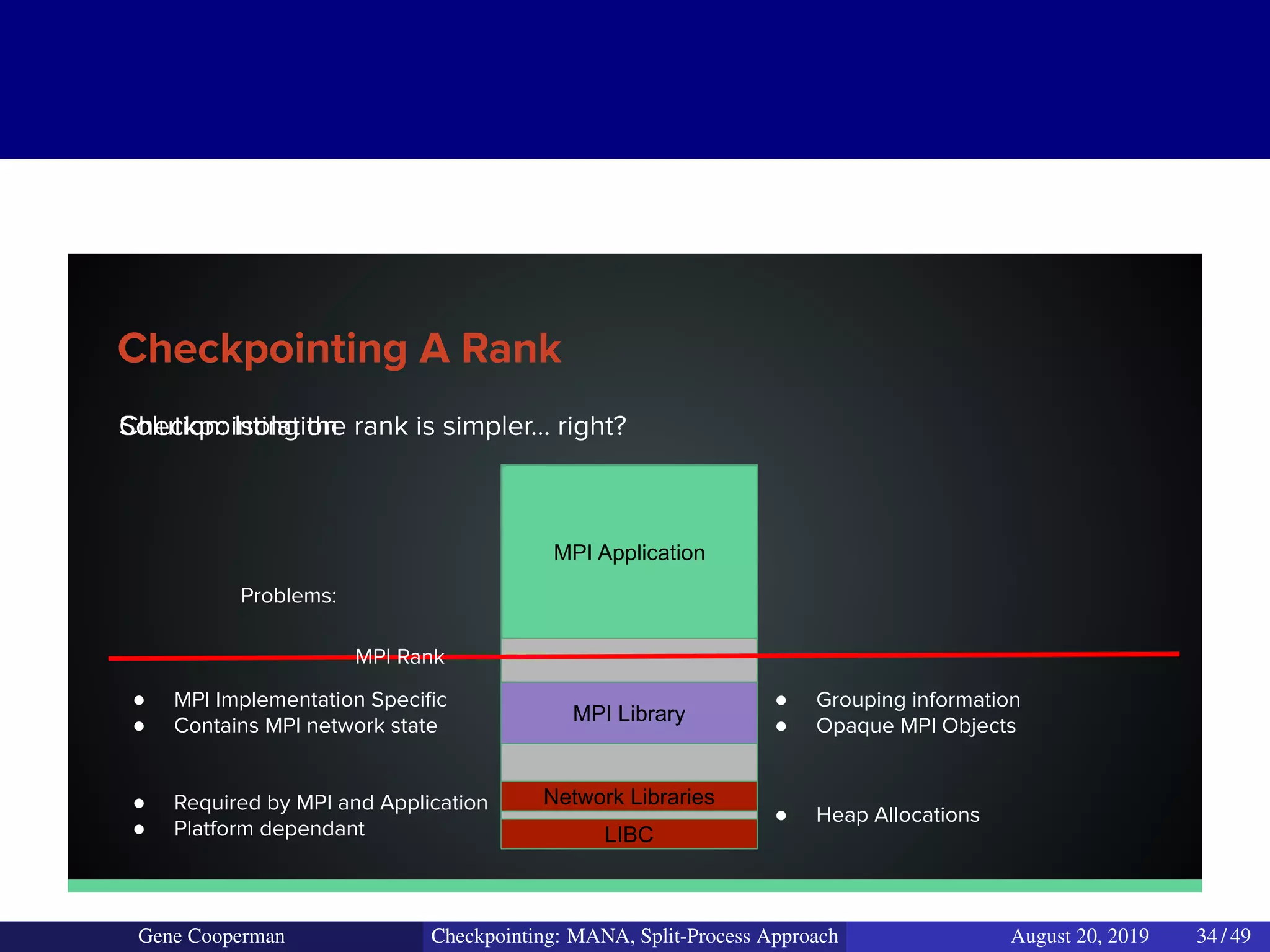
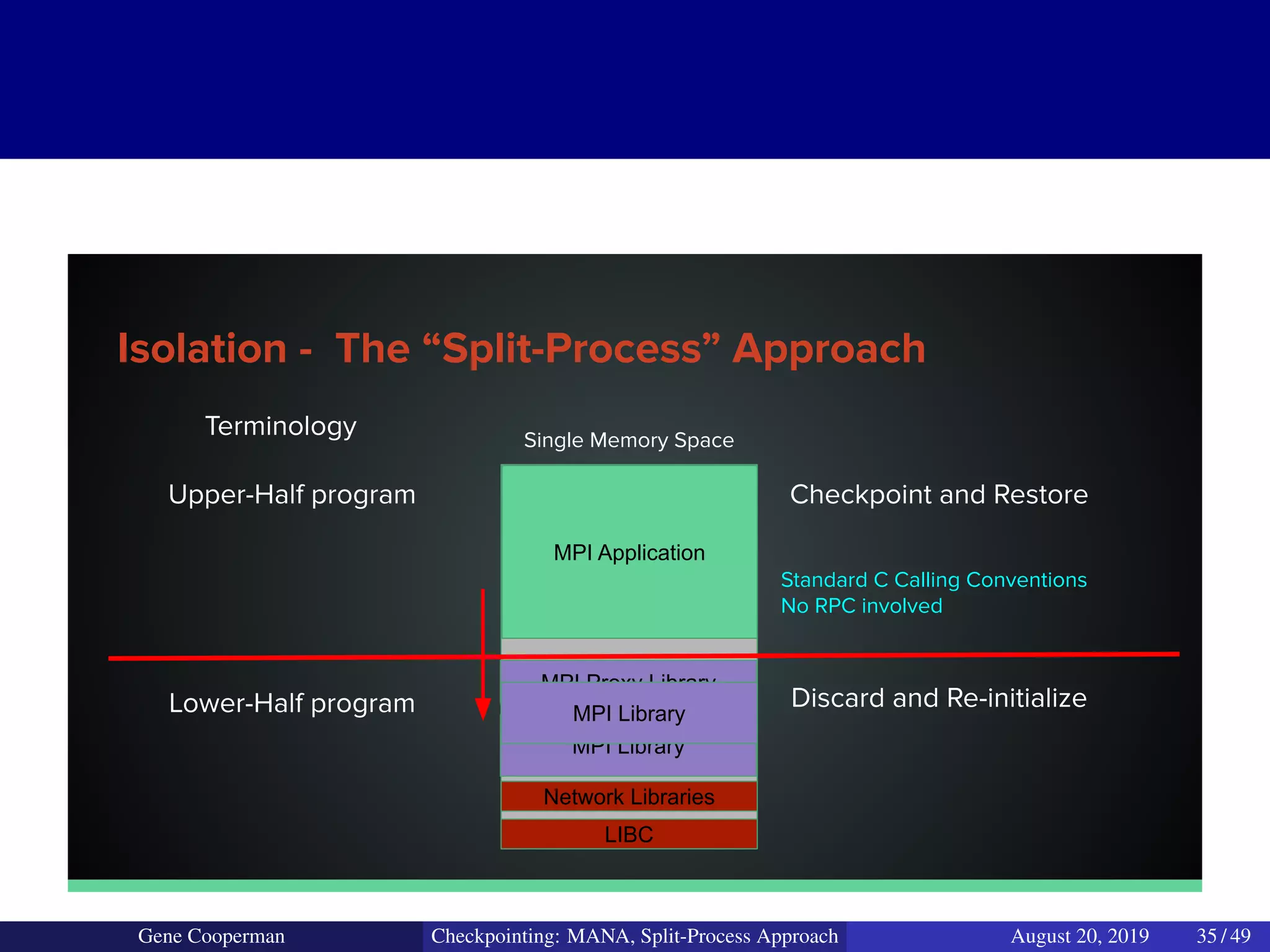
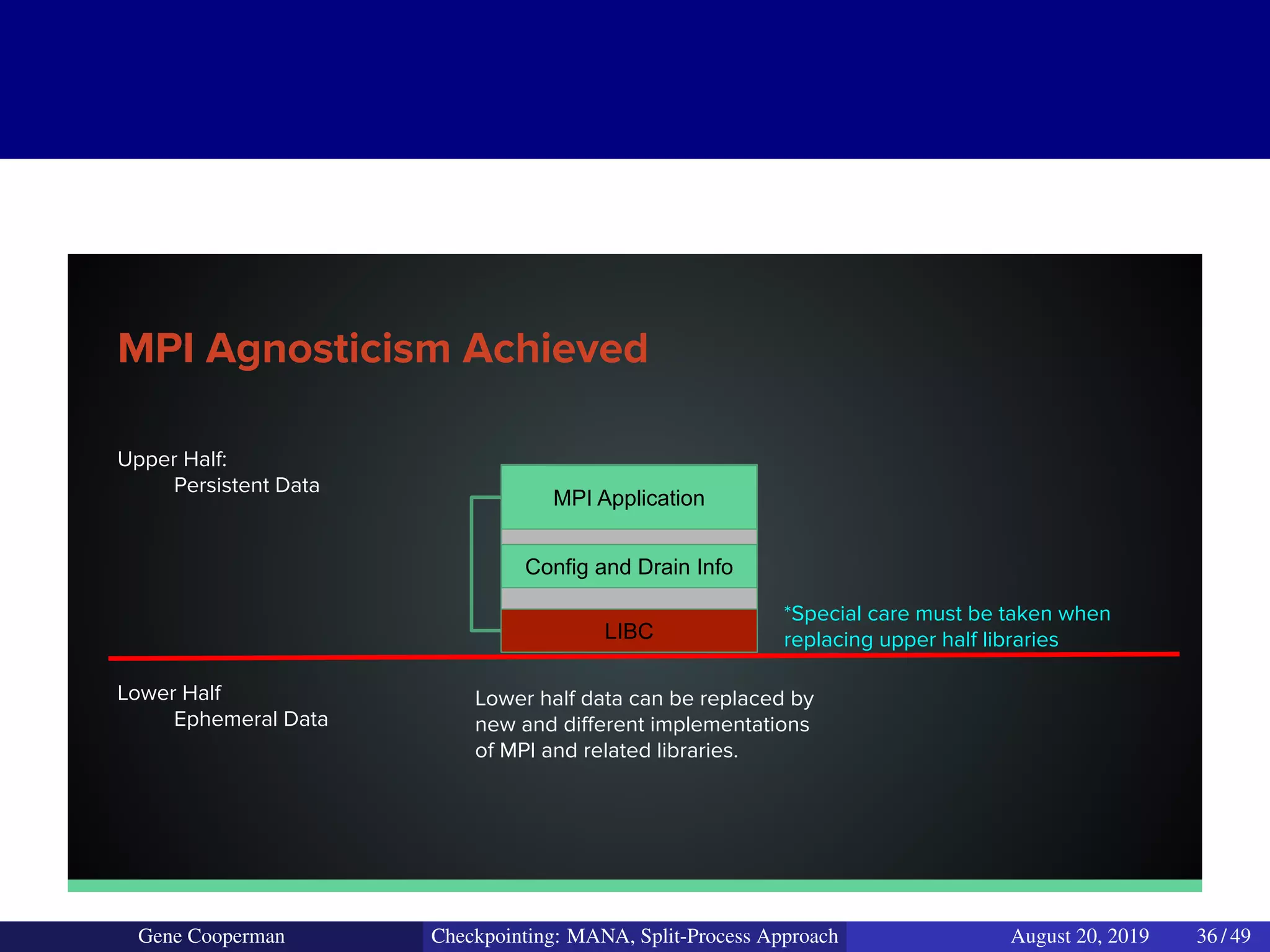
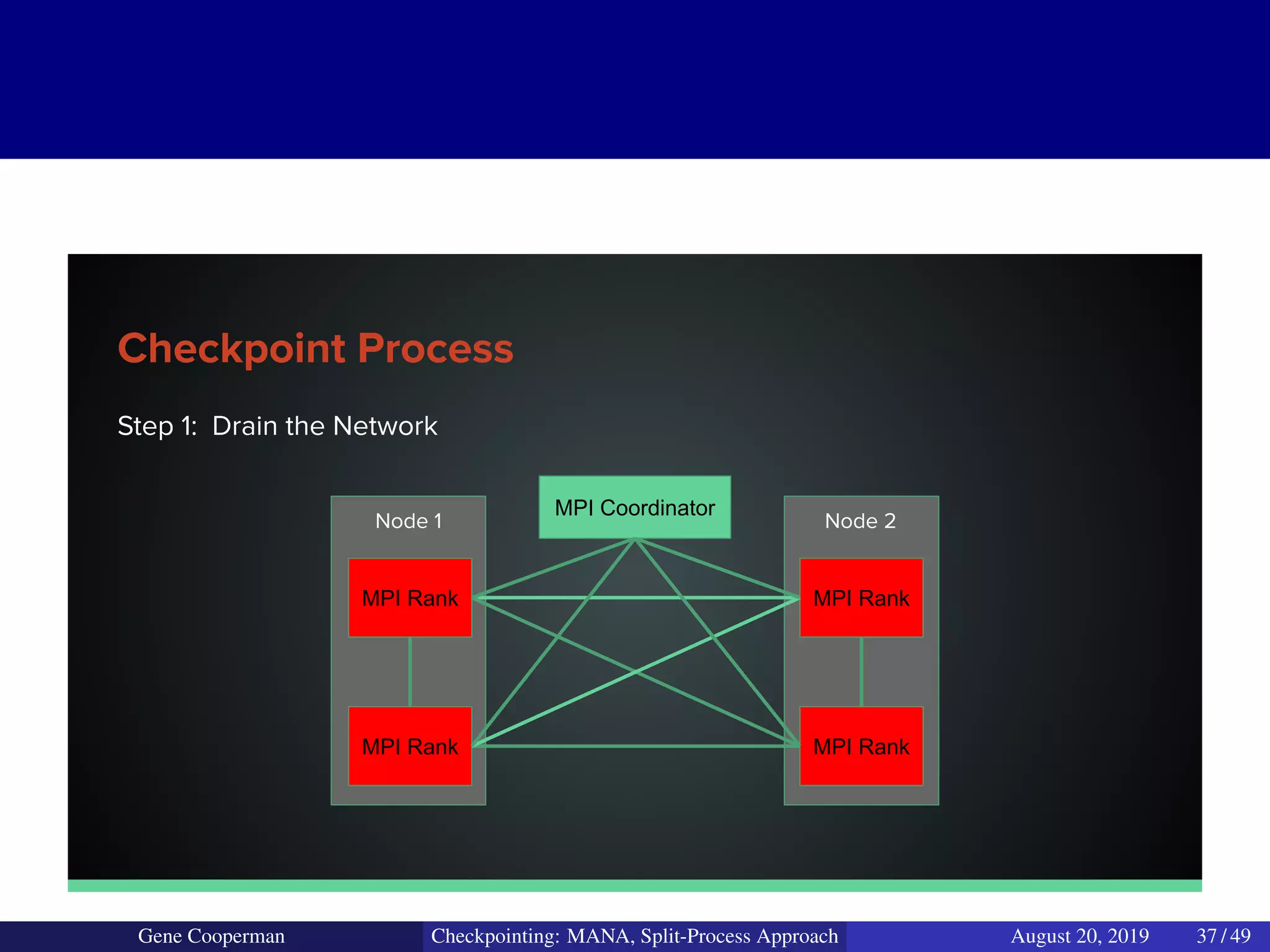
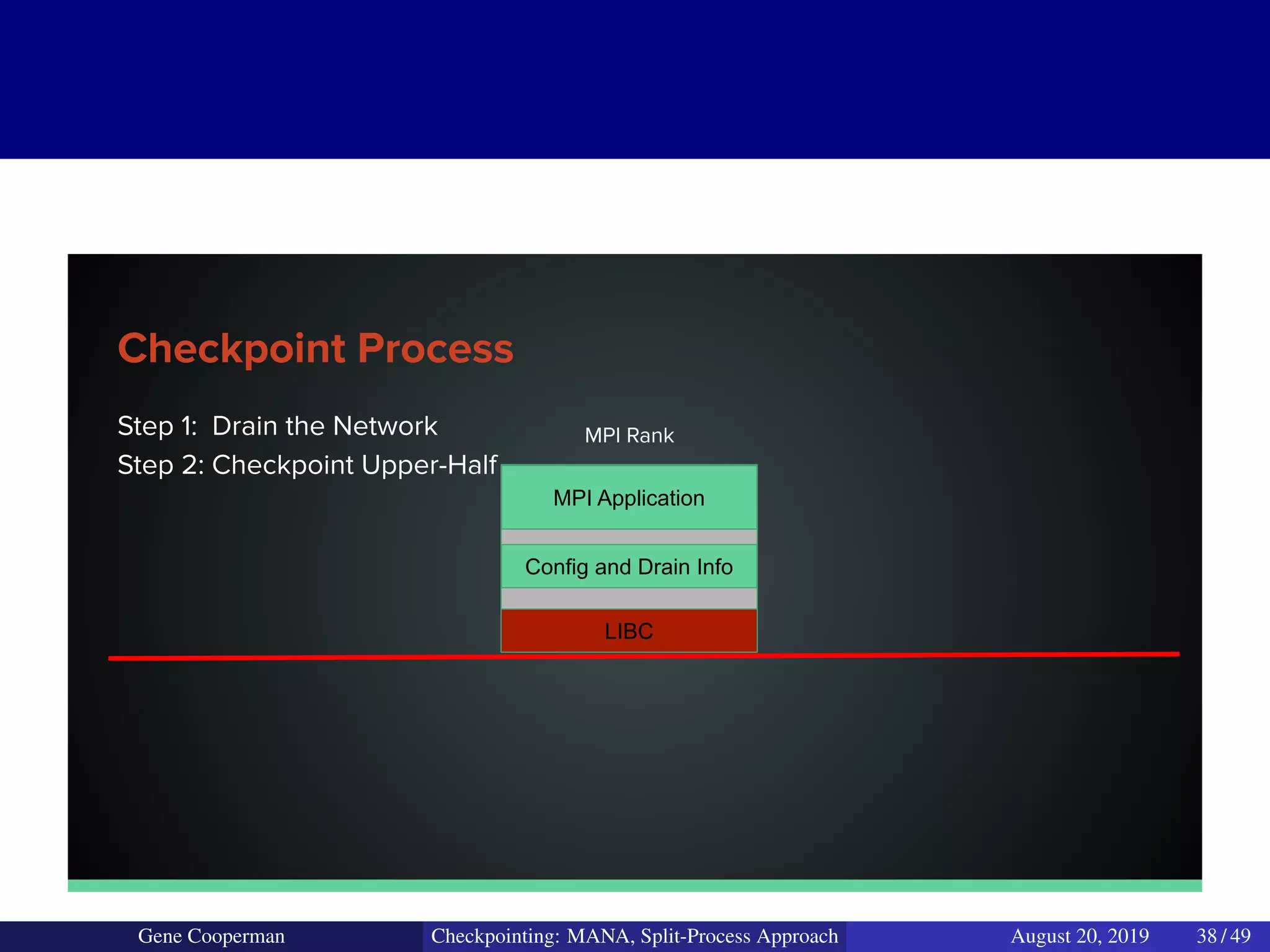
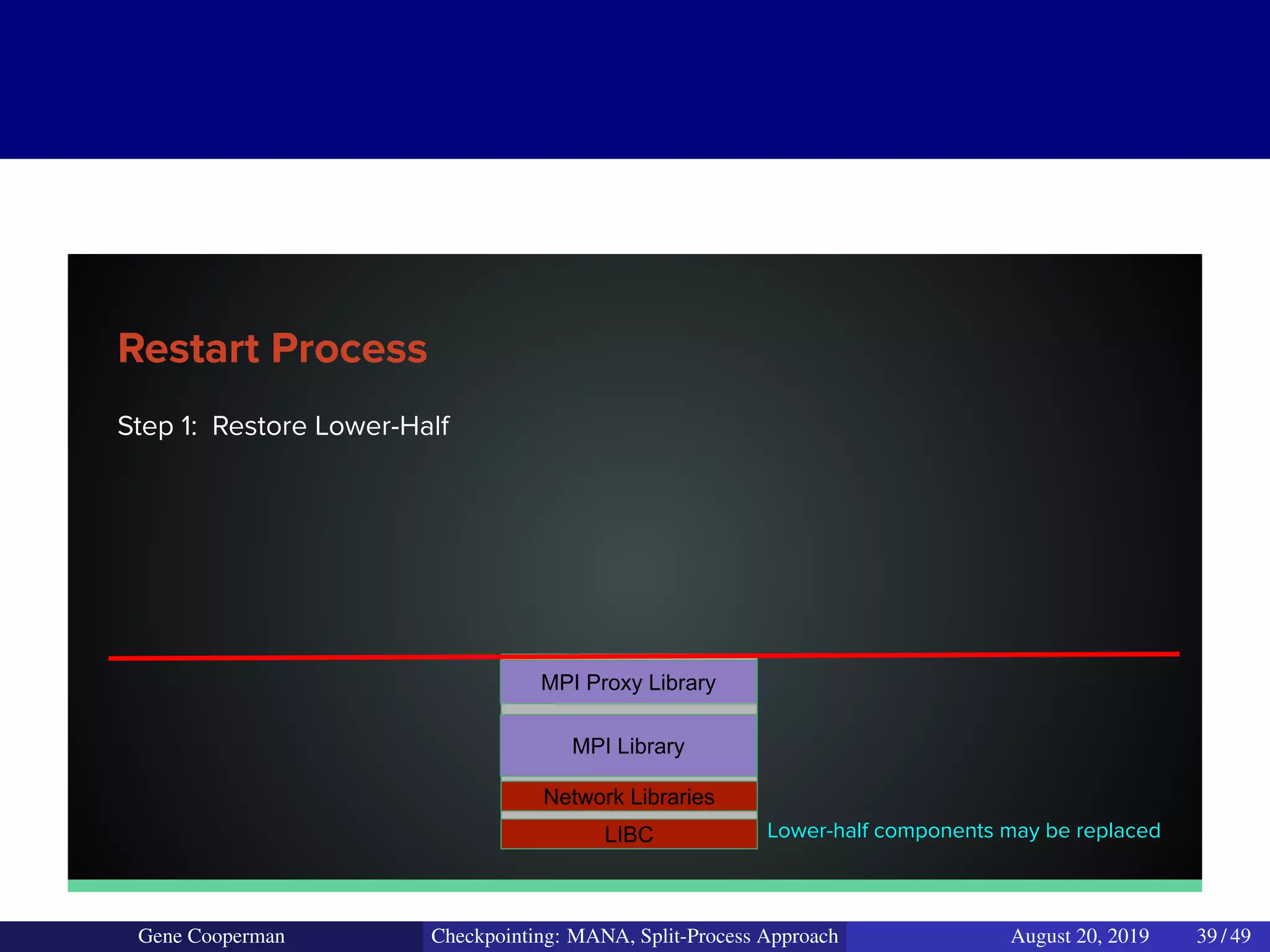
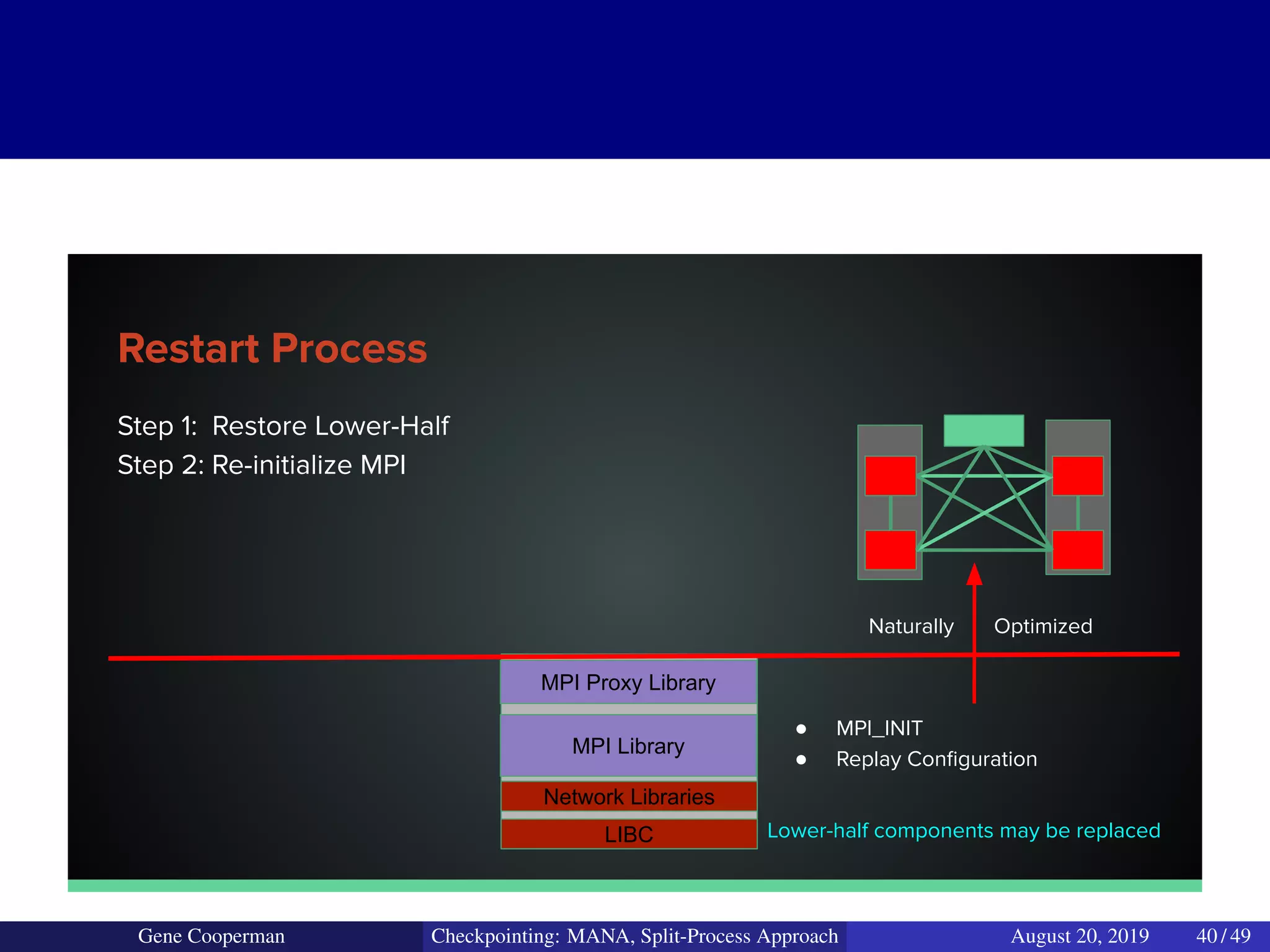
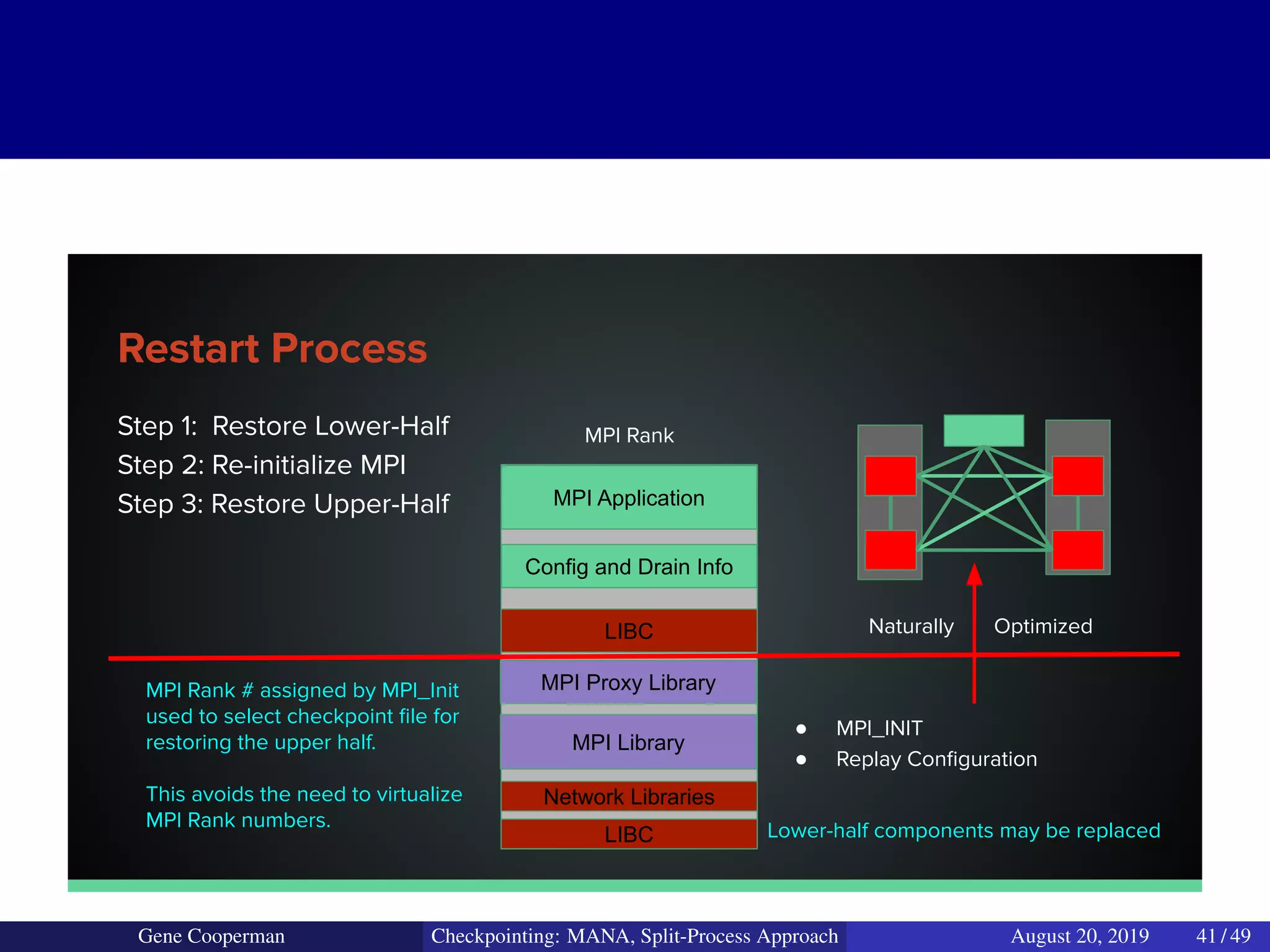
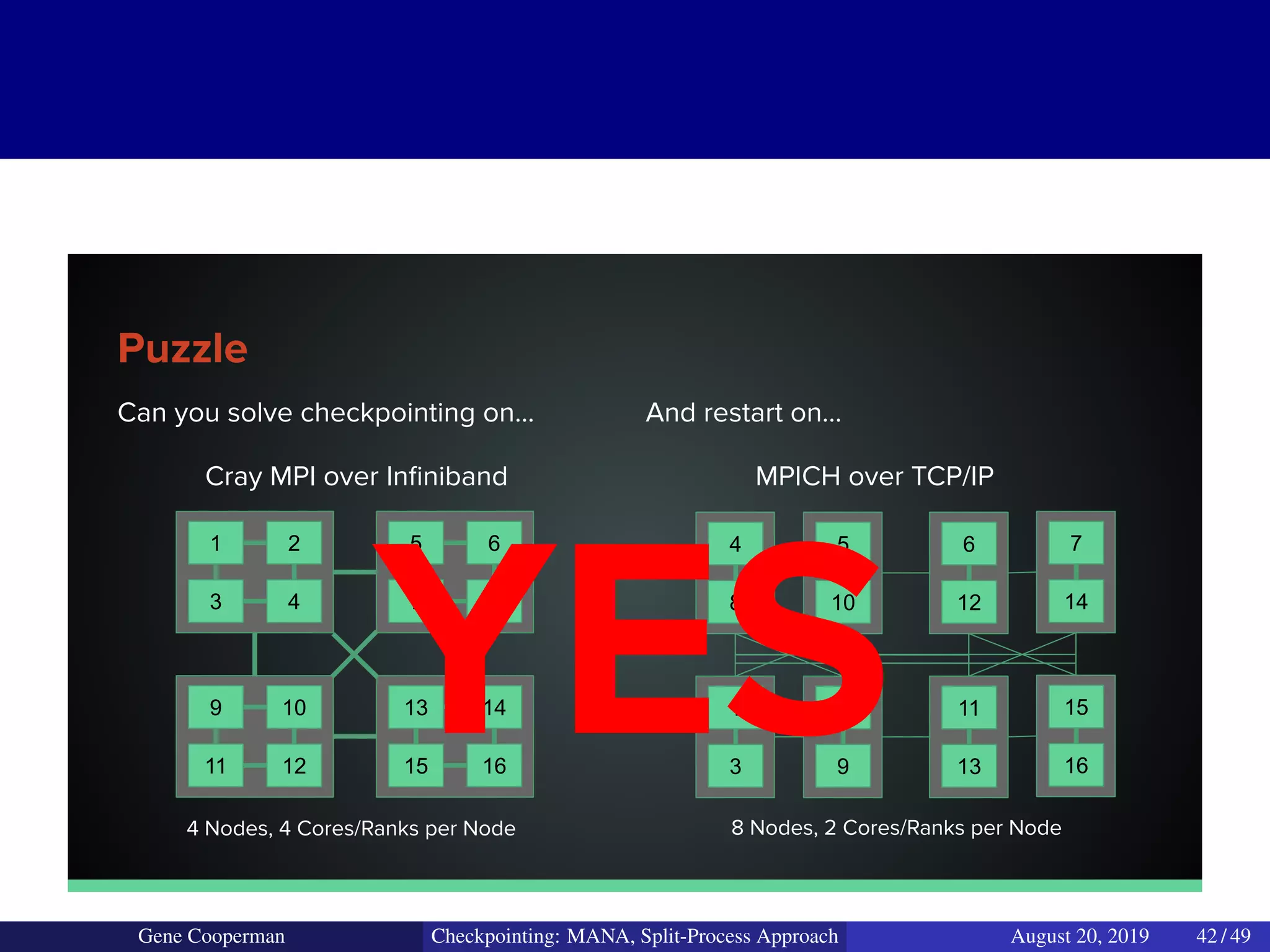
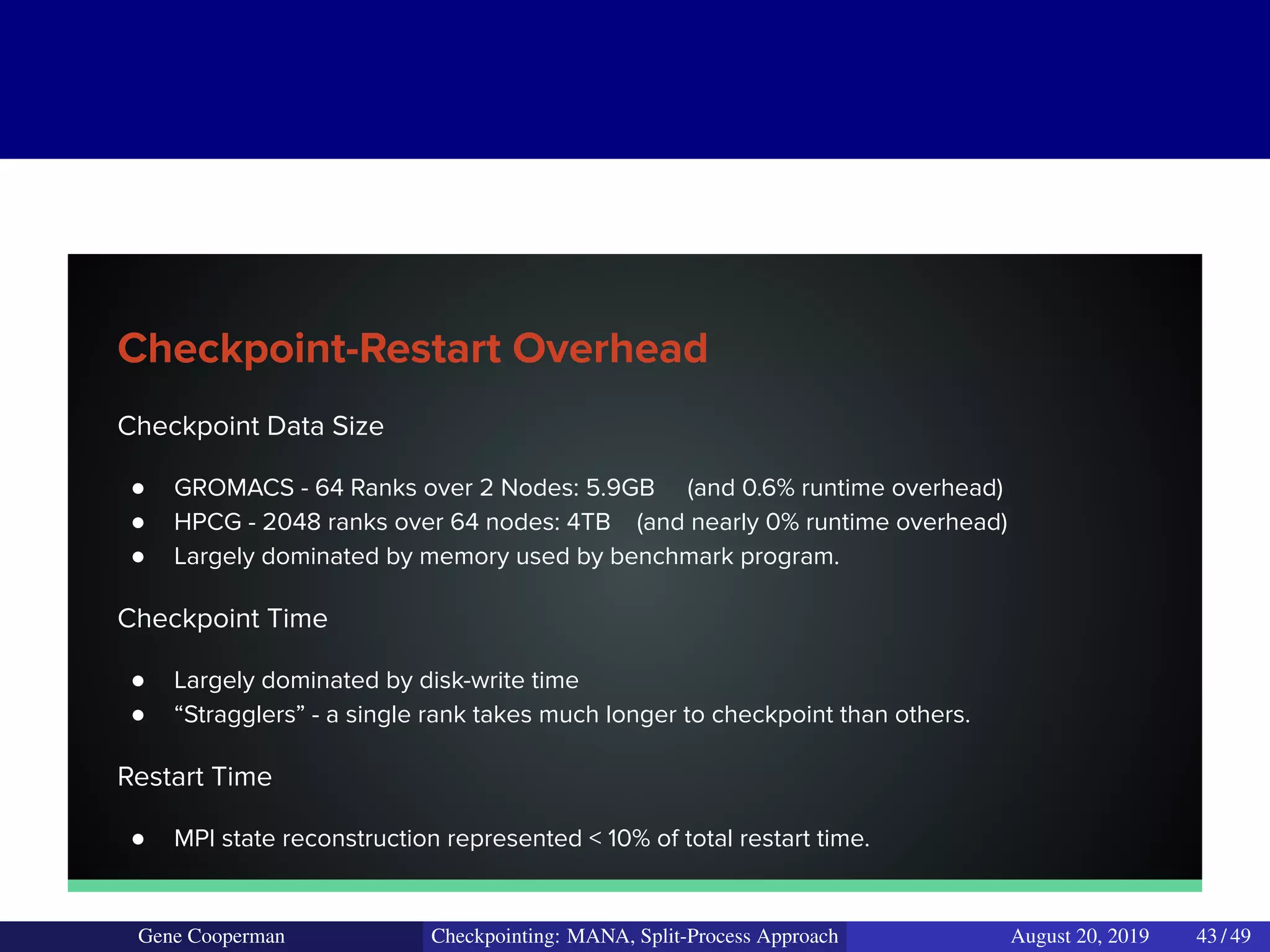
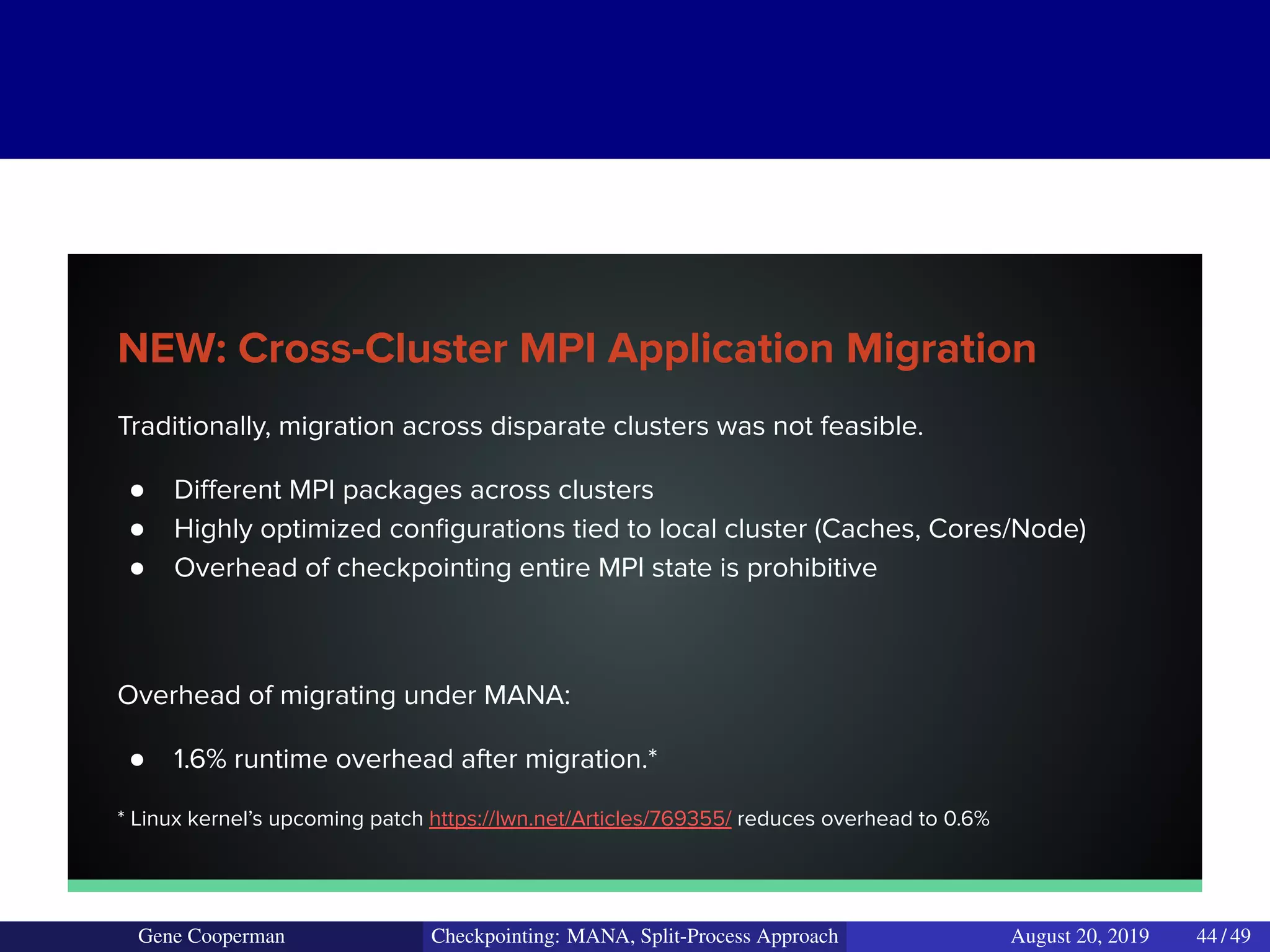
The document discusses the DMTCP (Distributed MultiThreaded CheckPointing) project and its advancements in checkpointing high-performance computing applications while addressing challenges like process virtualization and collective communication. It introduces the concept of a split-process approach, called Mana, which allows for MPI (Message Passing Interface) checkpointing without dependency on specific networks or MPI implementations. The focus is on enhancing transparency and flexibility in checkpointing systems, enabling capabilities such as cross-cluster migration and the use of plugins to handle external subsystems.