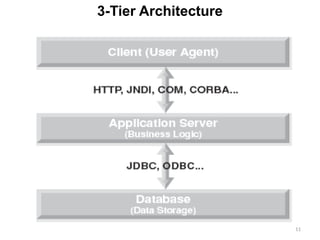
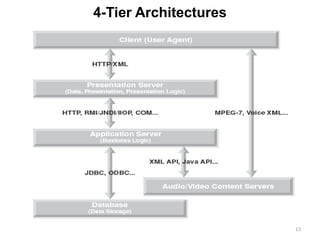
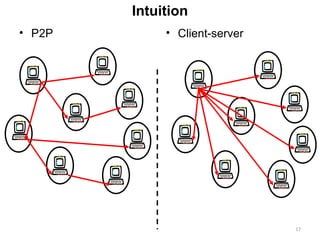
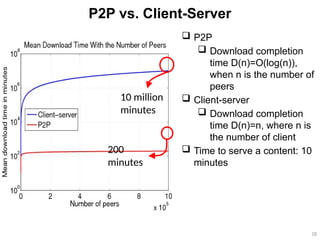
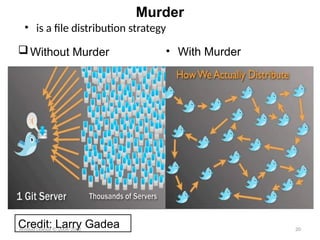
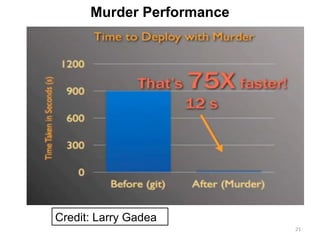
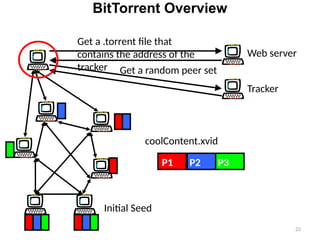
The document discusses various architectures for mobile application development, including centralized, client-server, 3-tier, n-tier, peer-to-peer (P2P), and mobile agent architectures. Each architecture has its advantages and disadvantages, considering factors like reliability, scalability, and the nature of the user interface. It also highlights the challenges faced by the mobile web, including interoperability and usability issues due to device fragmentation and small form factors.