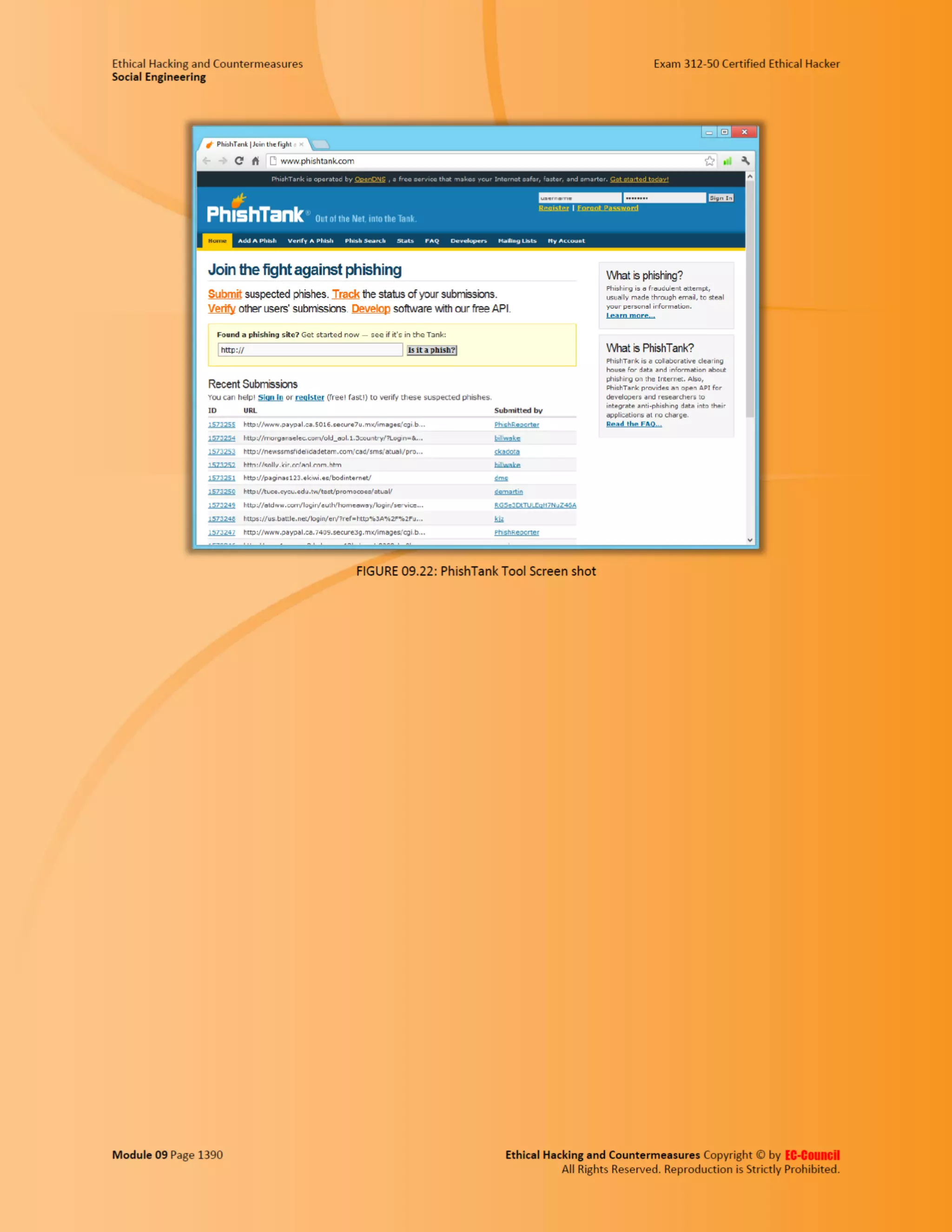
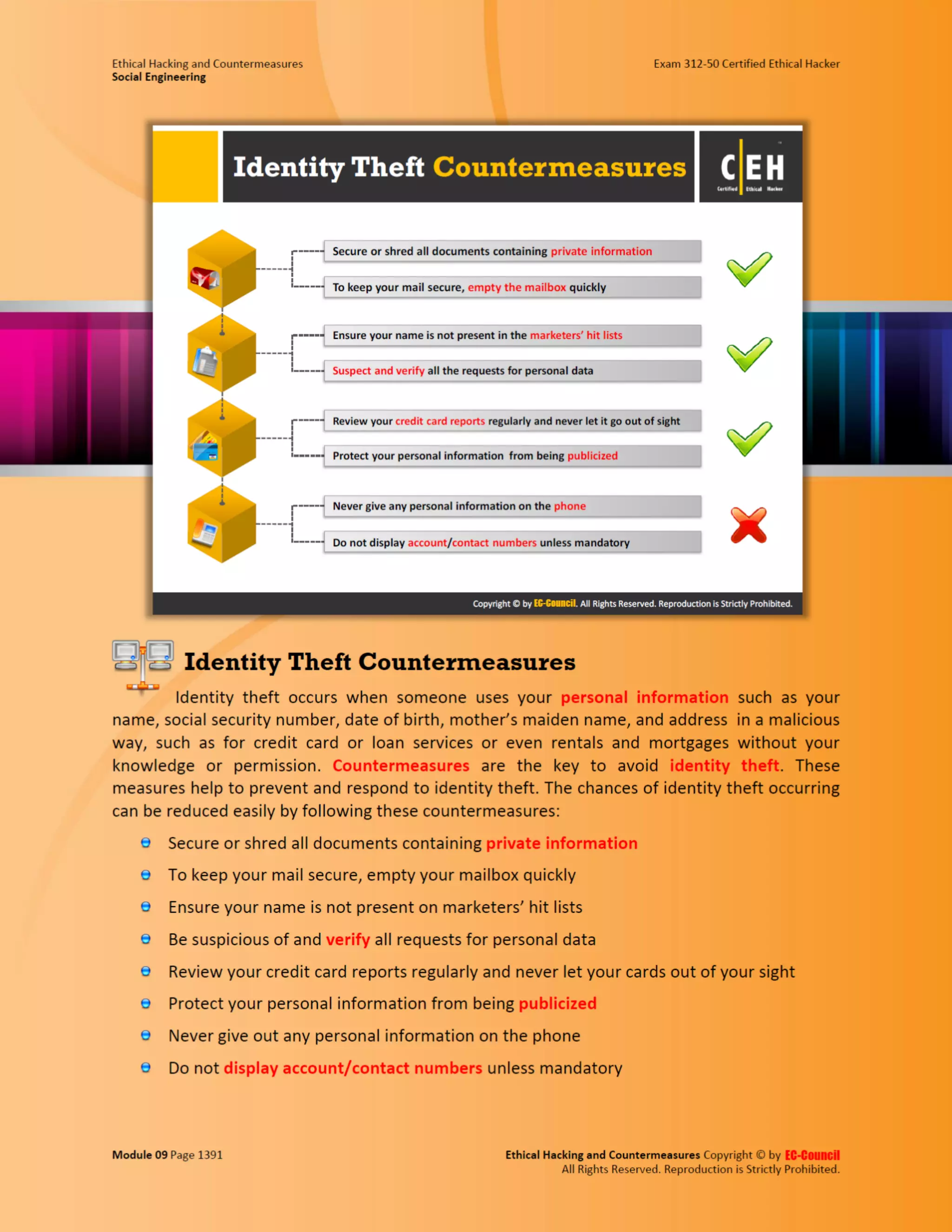
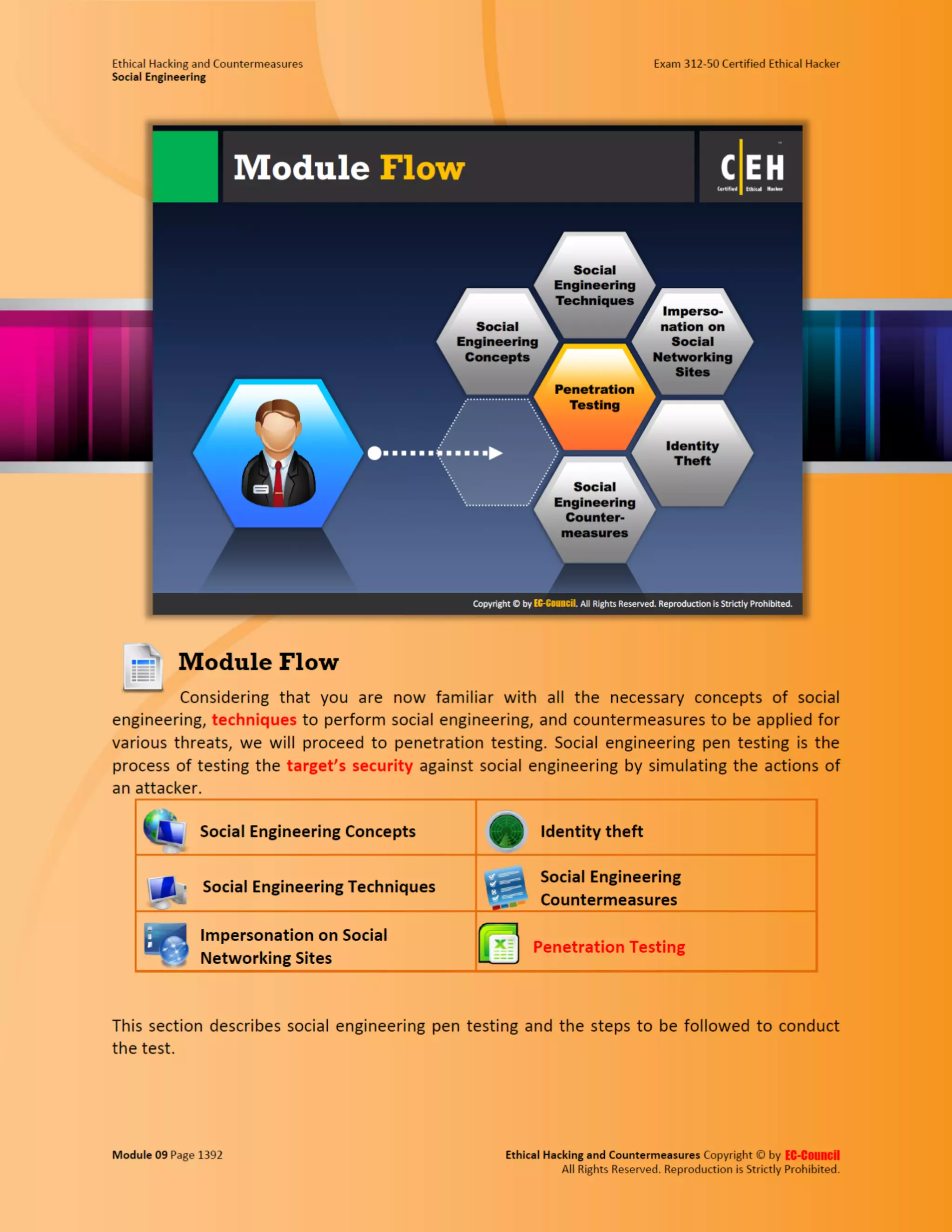
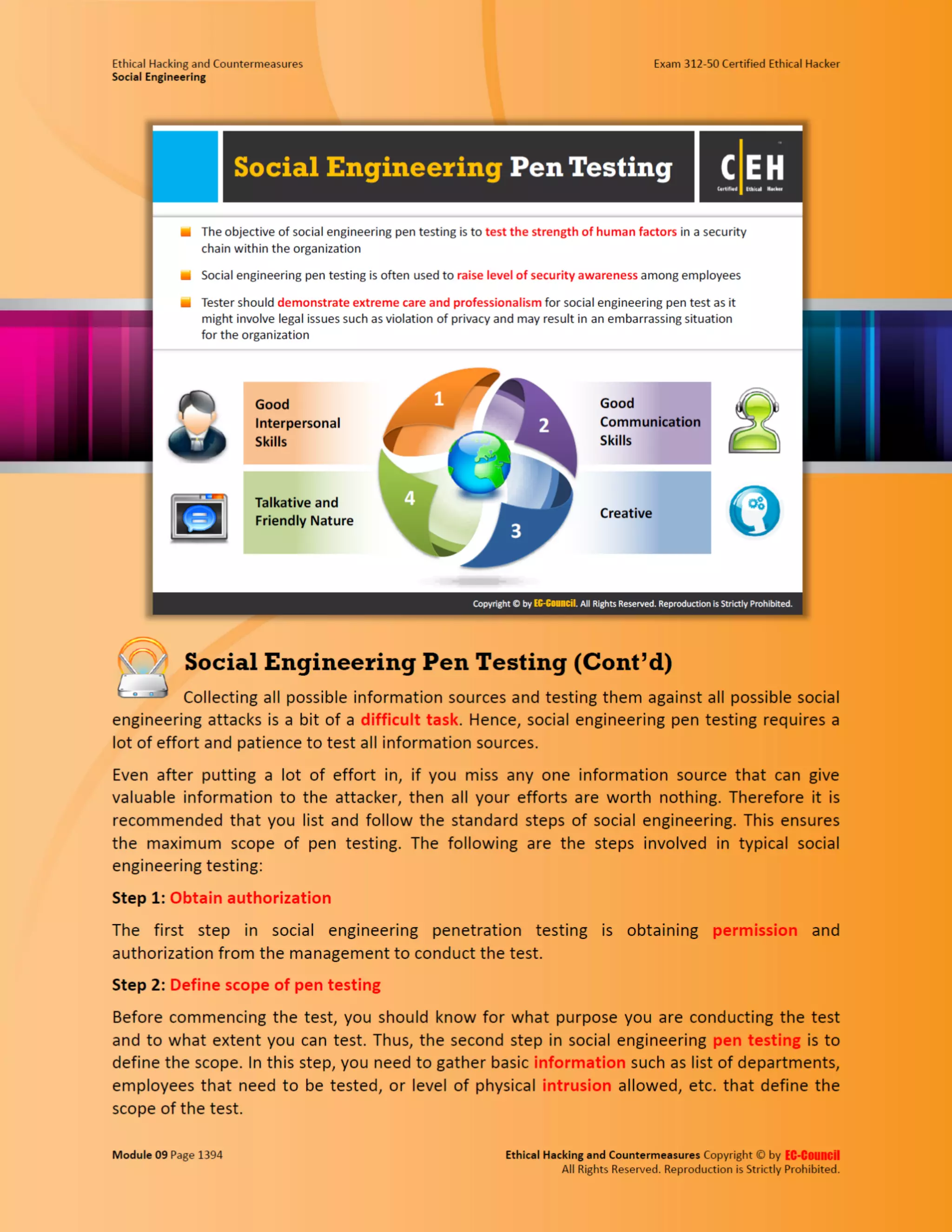
Embed presentation








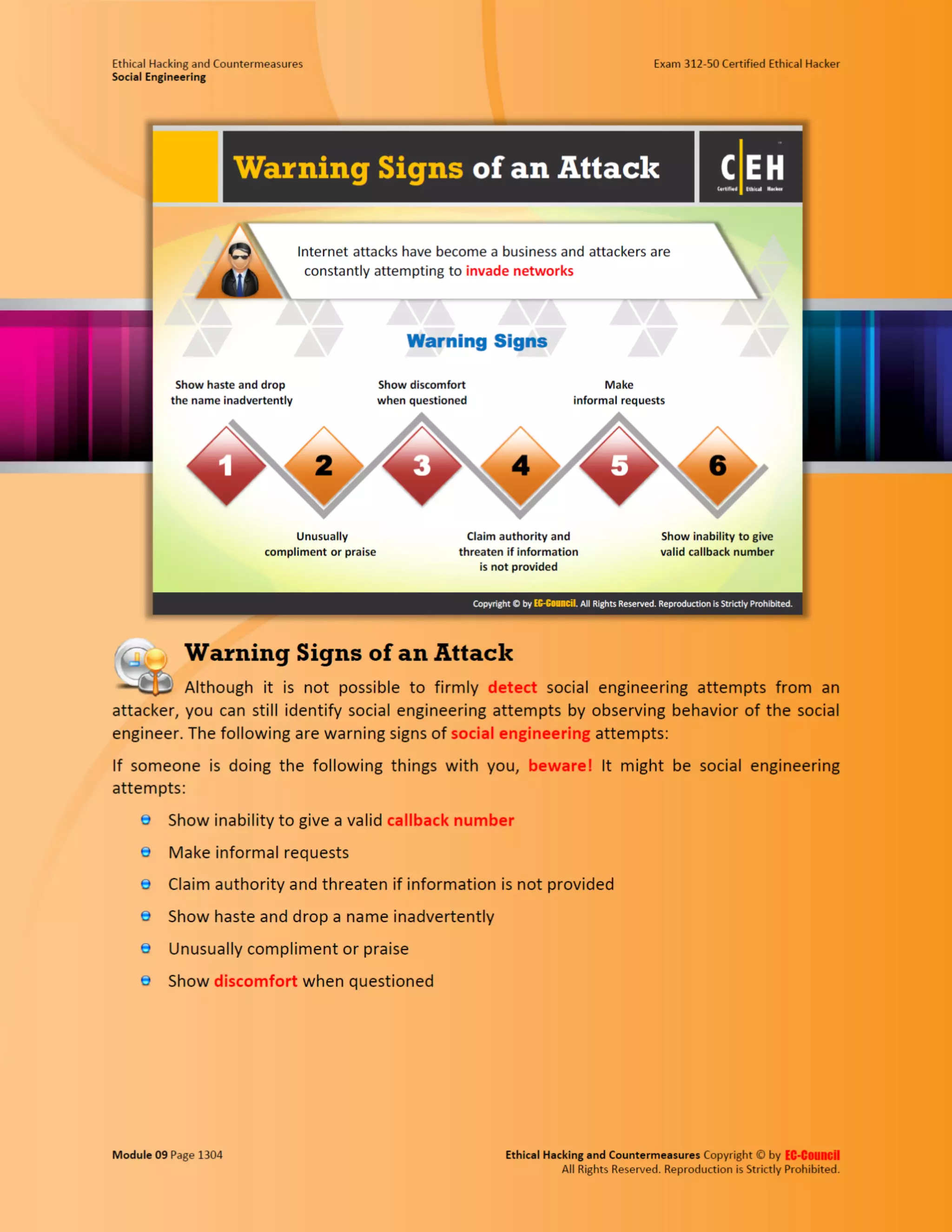




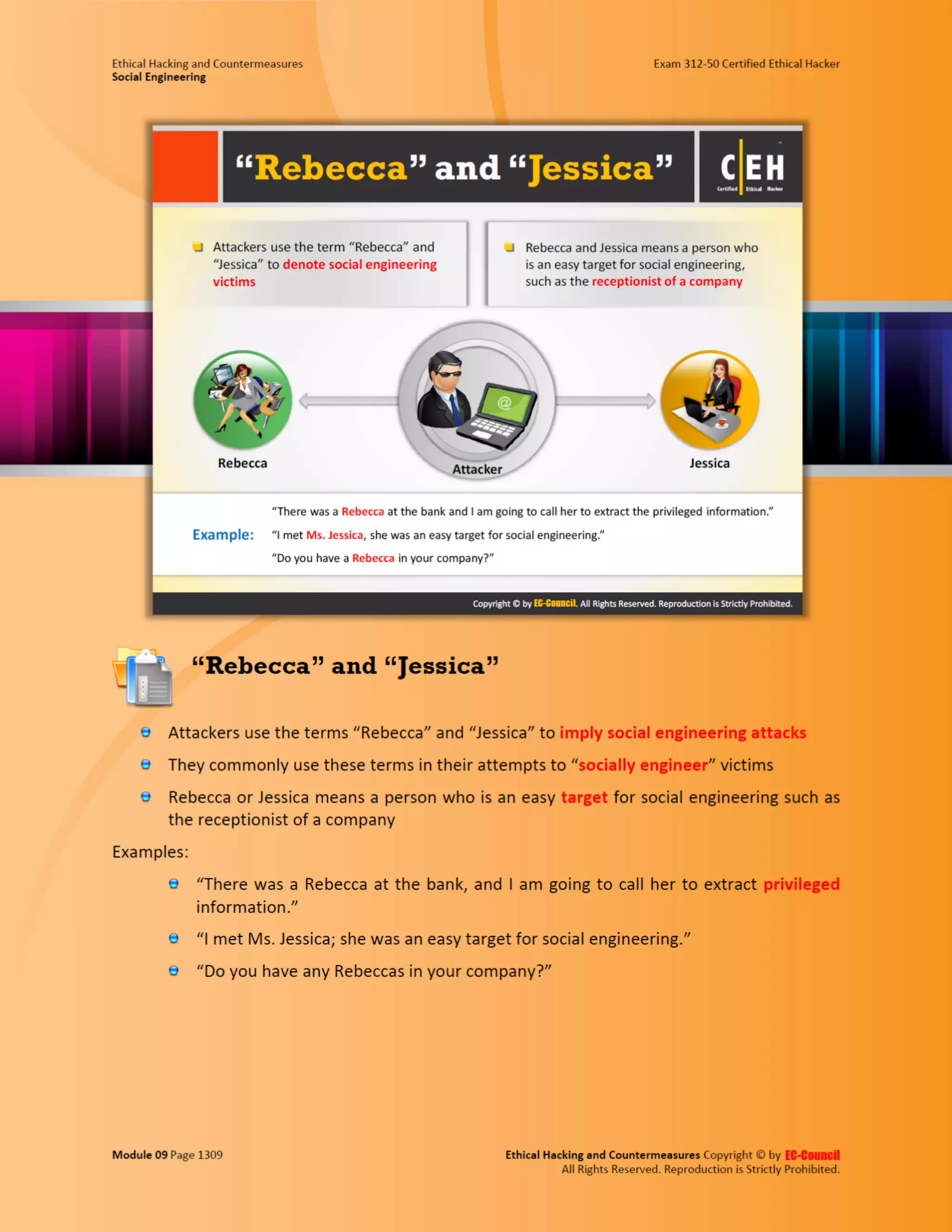

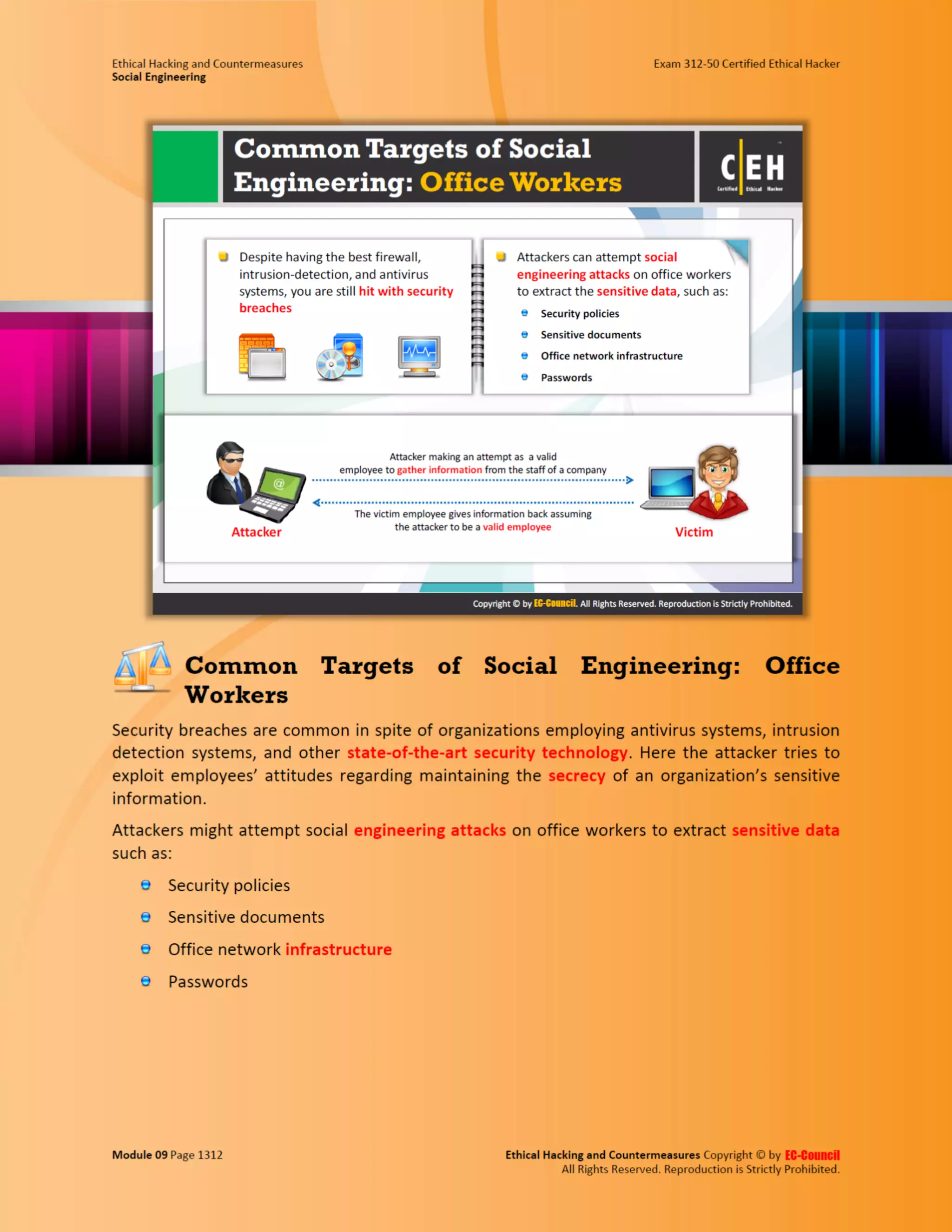

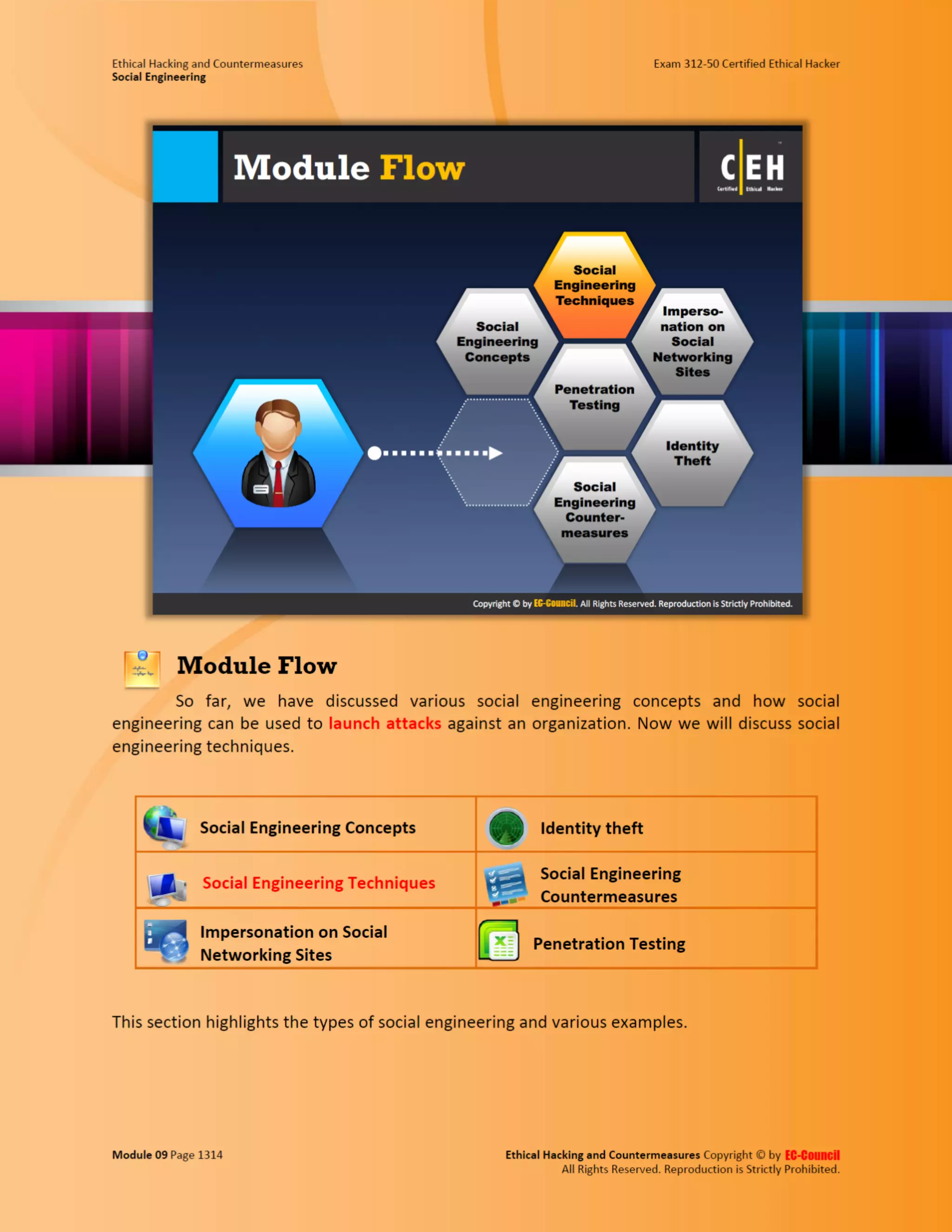
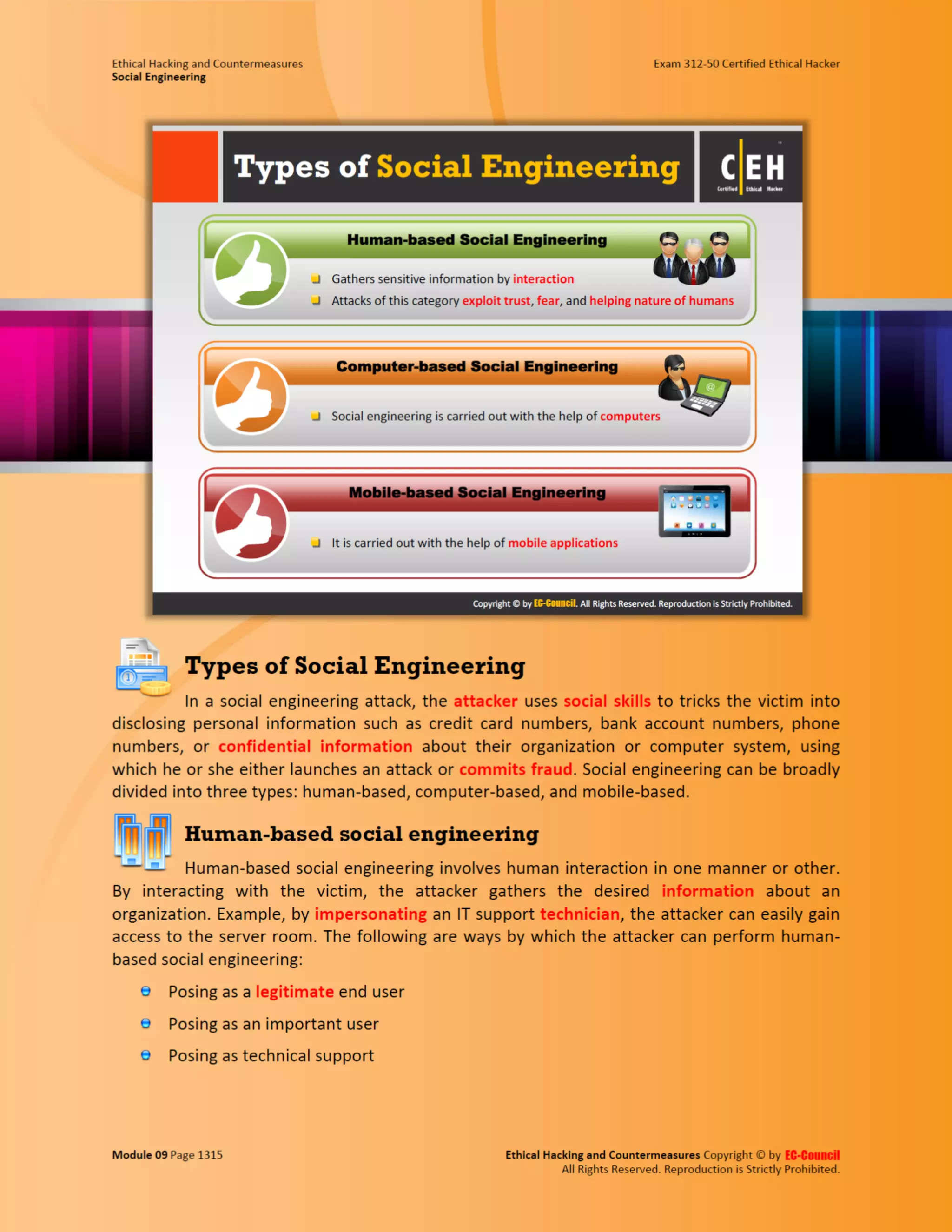




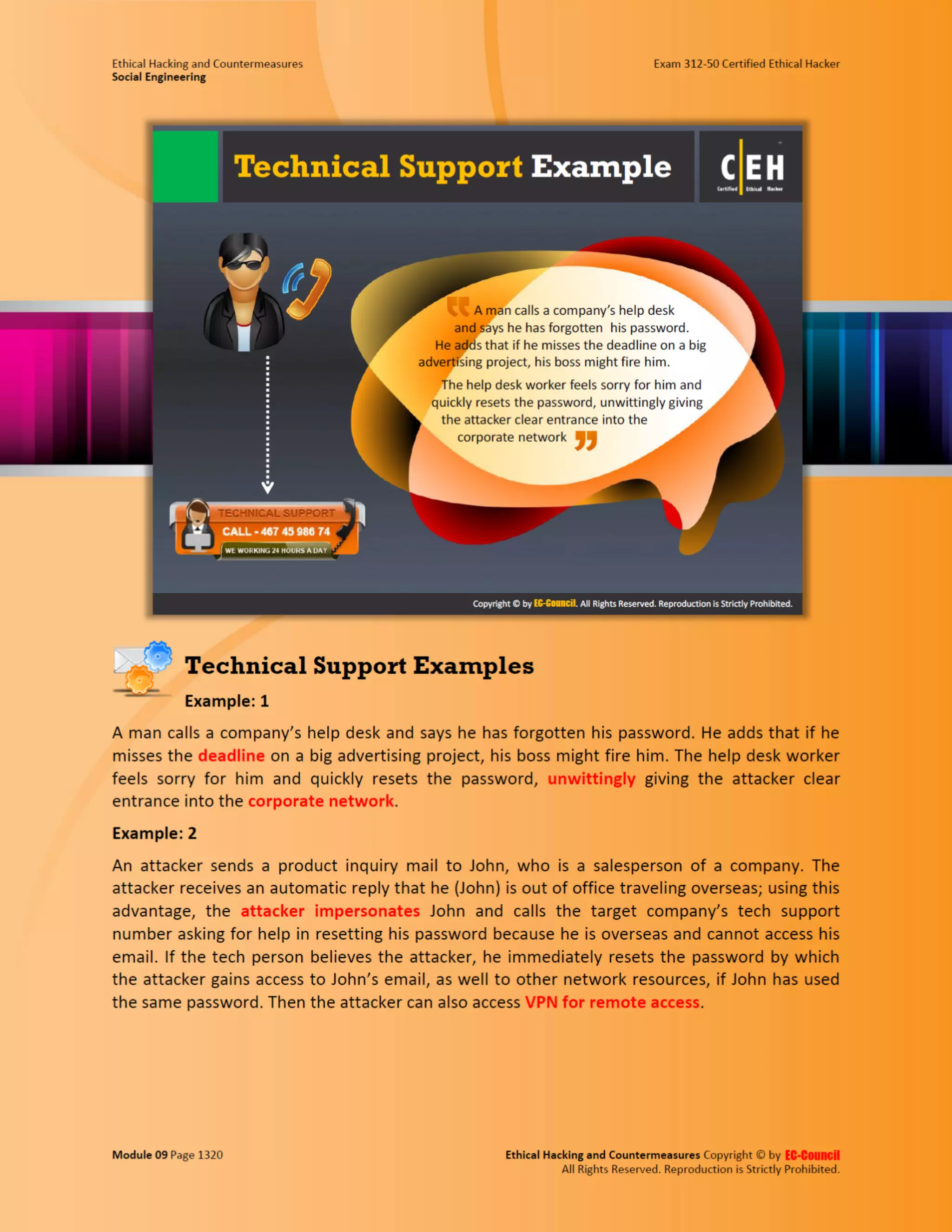









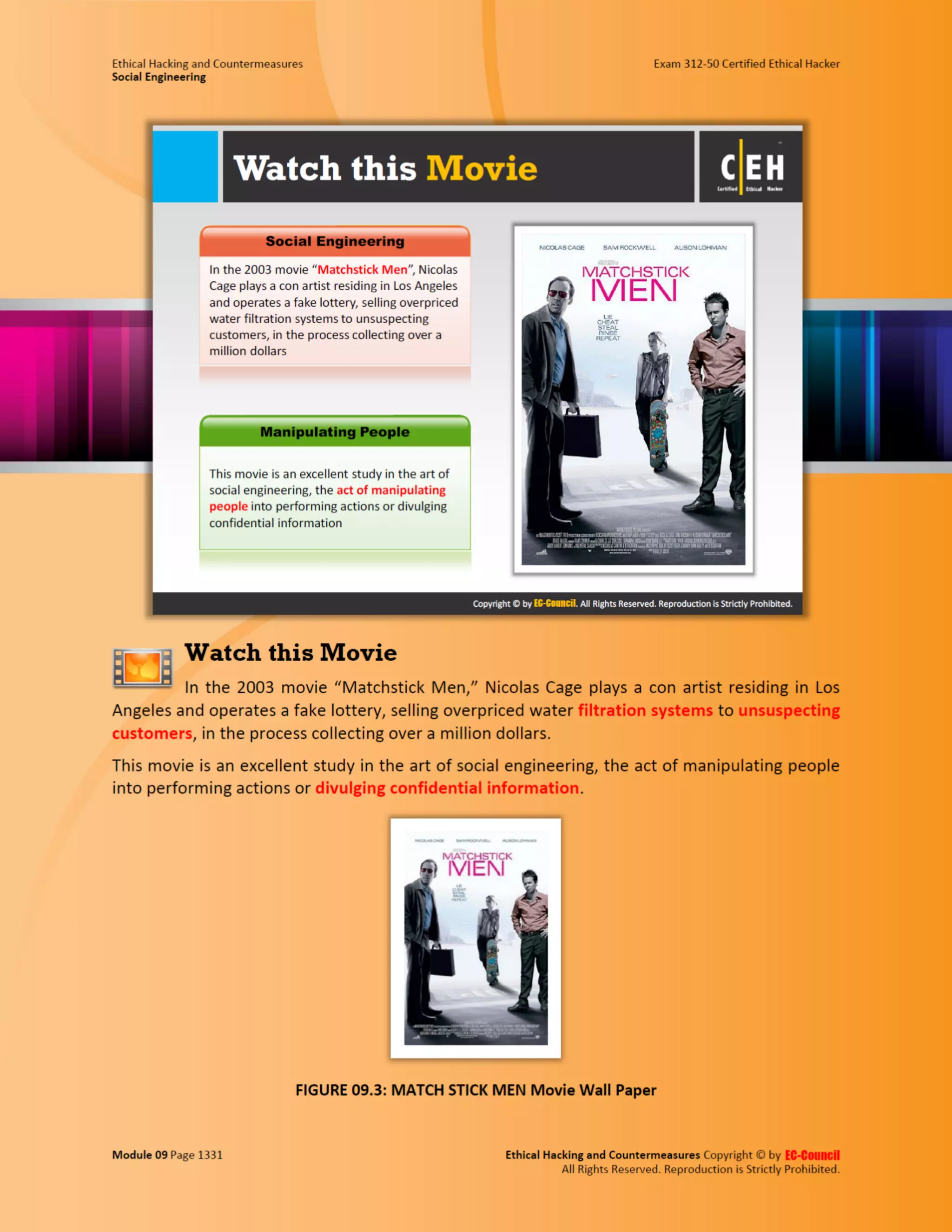


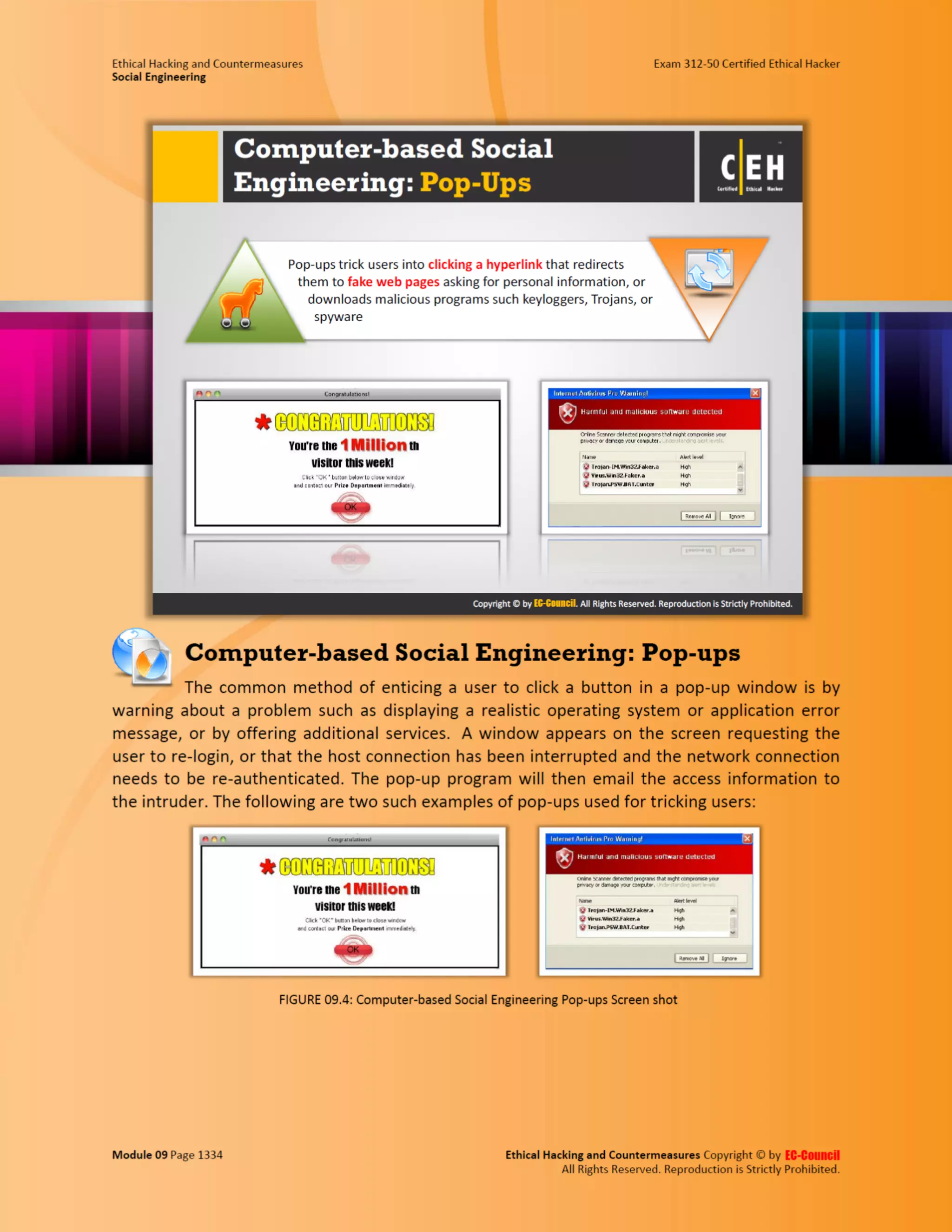
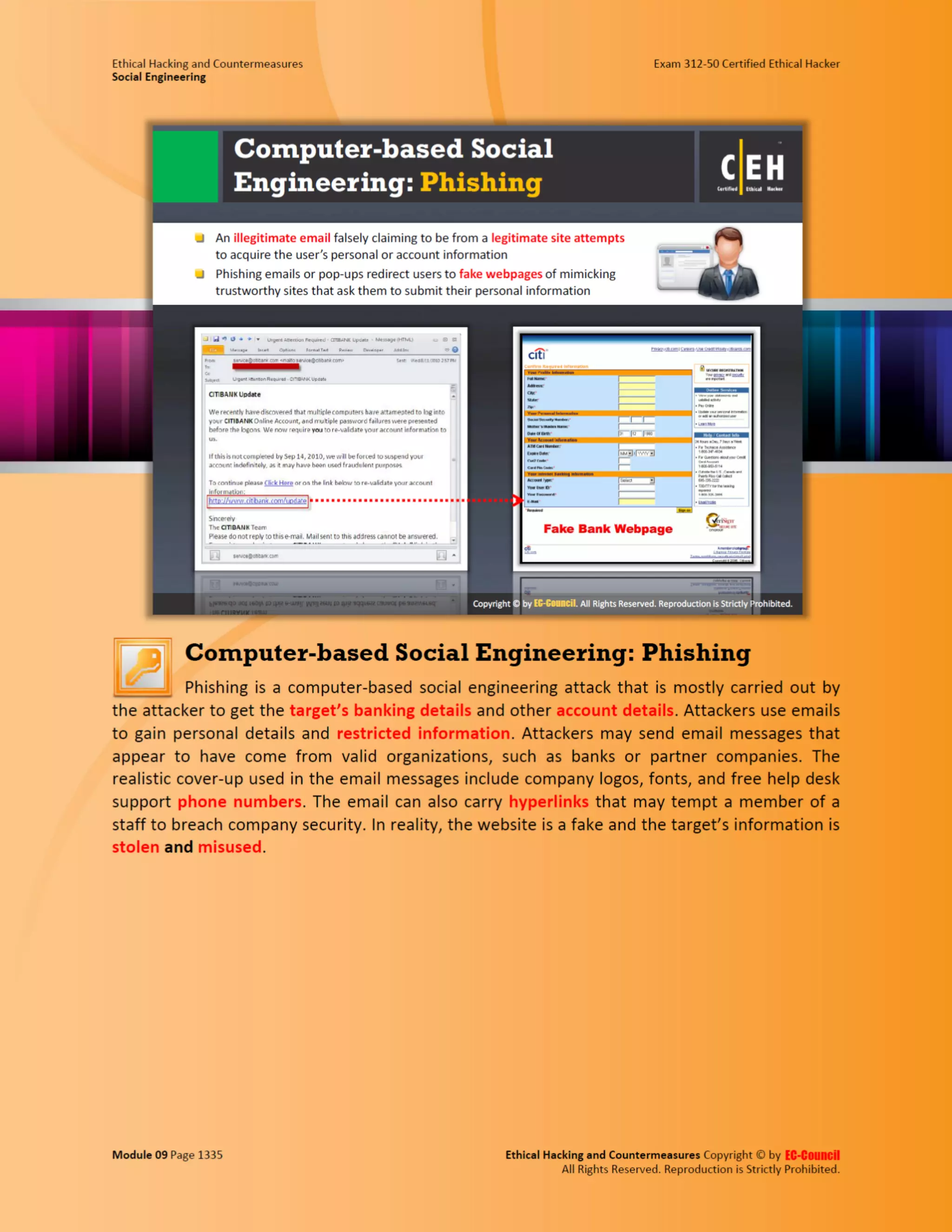
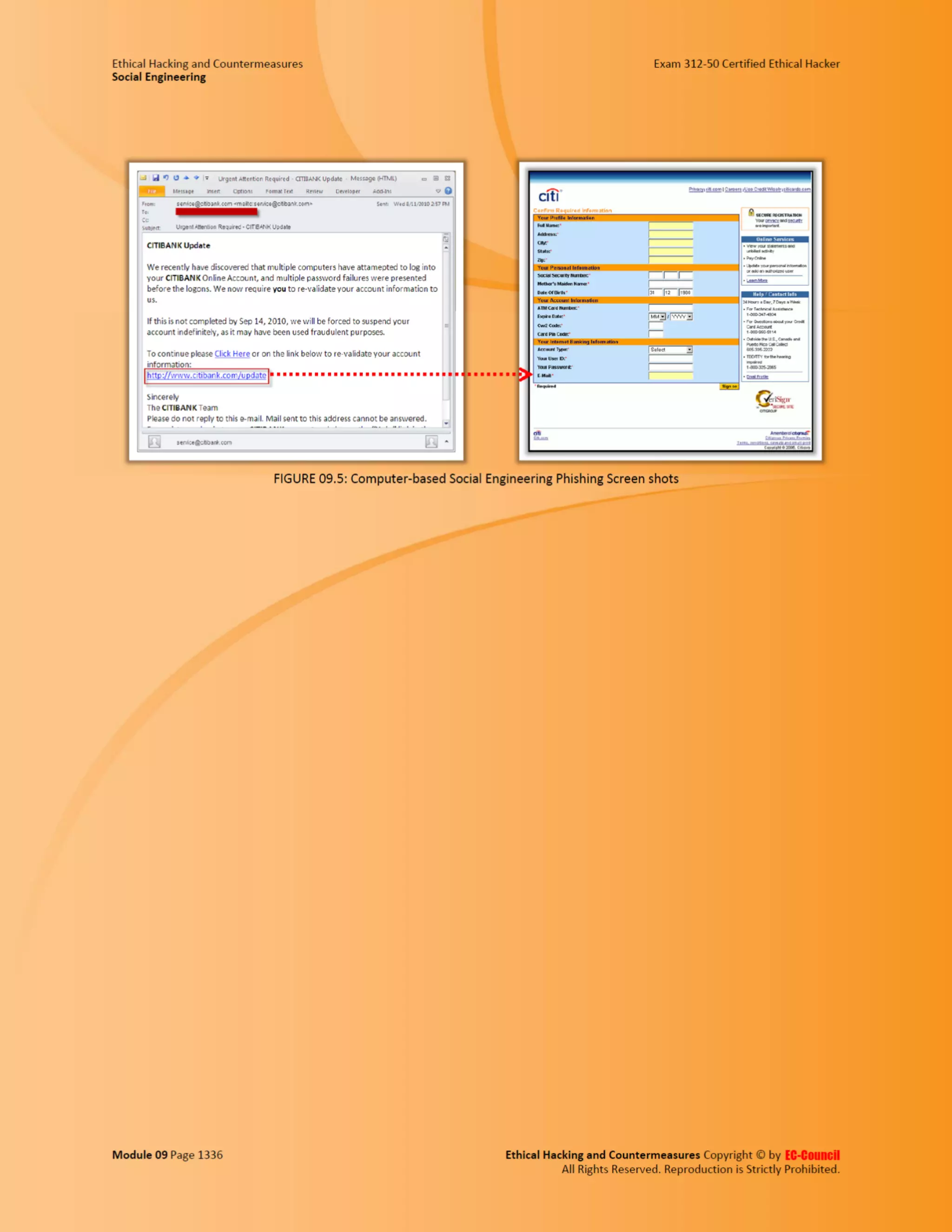
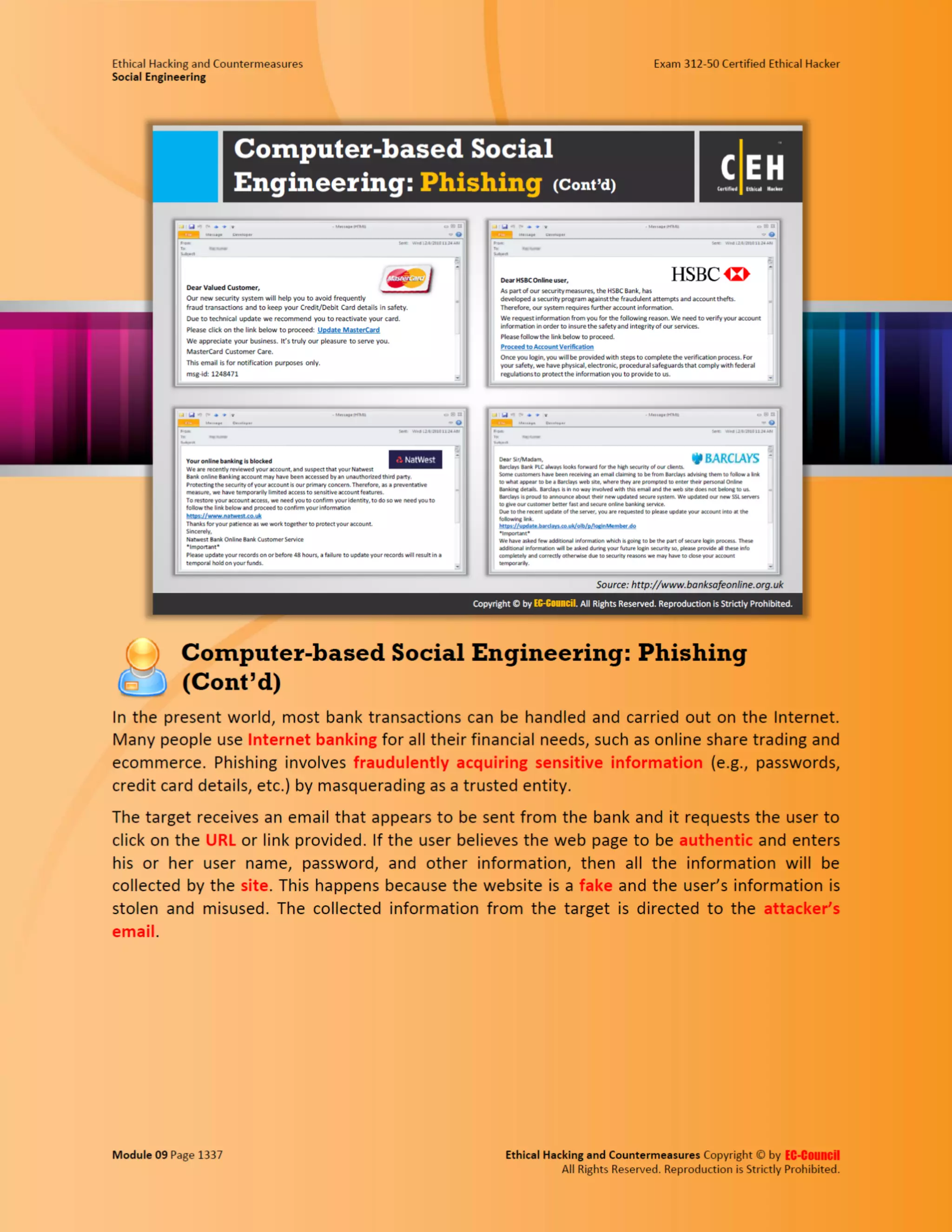
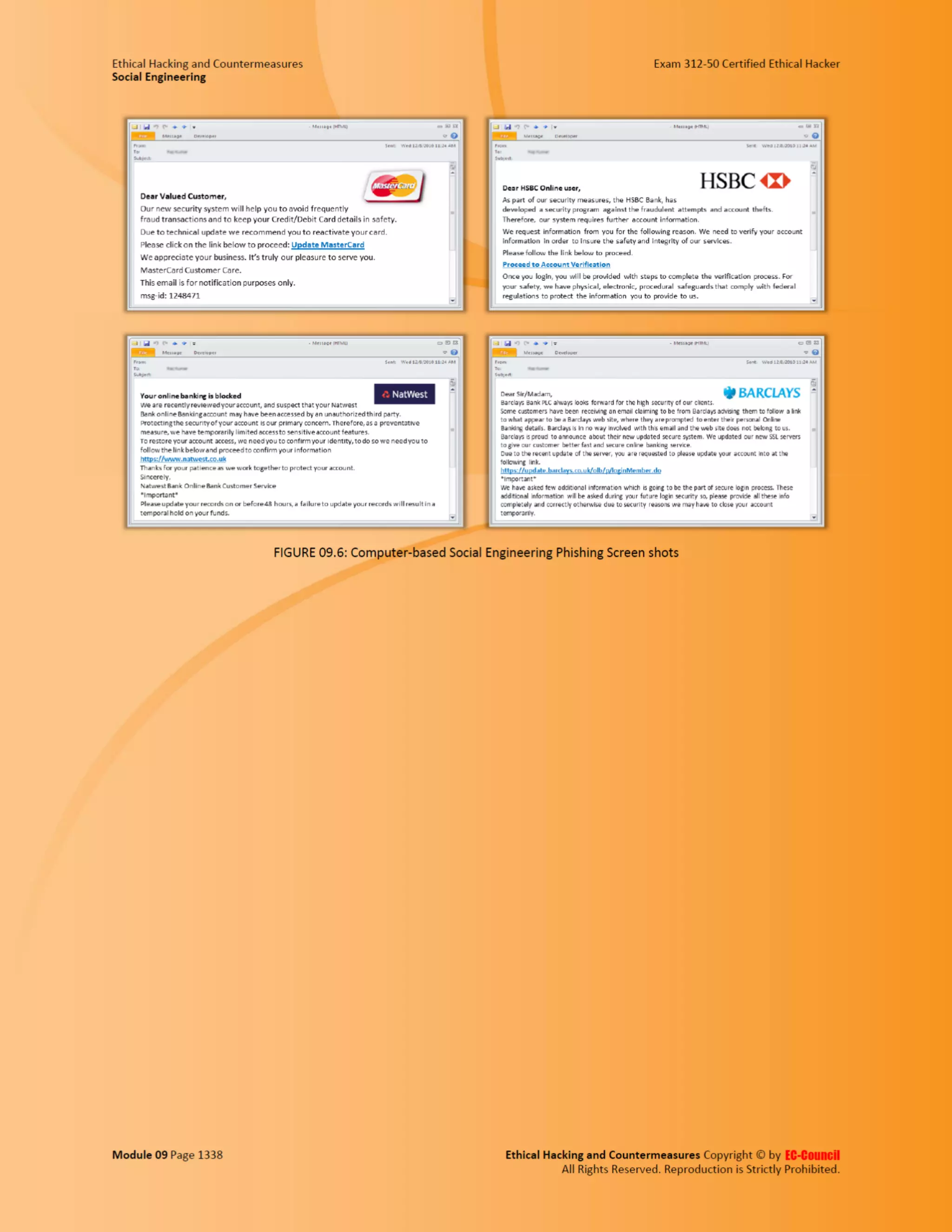


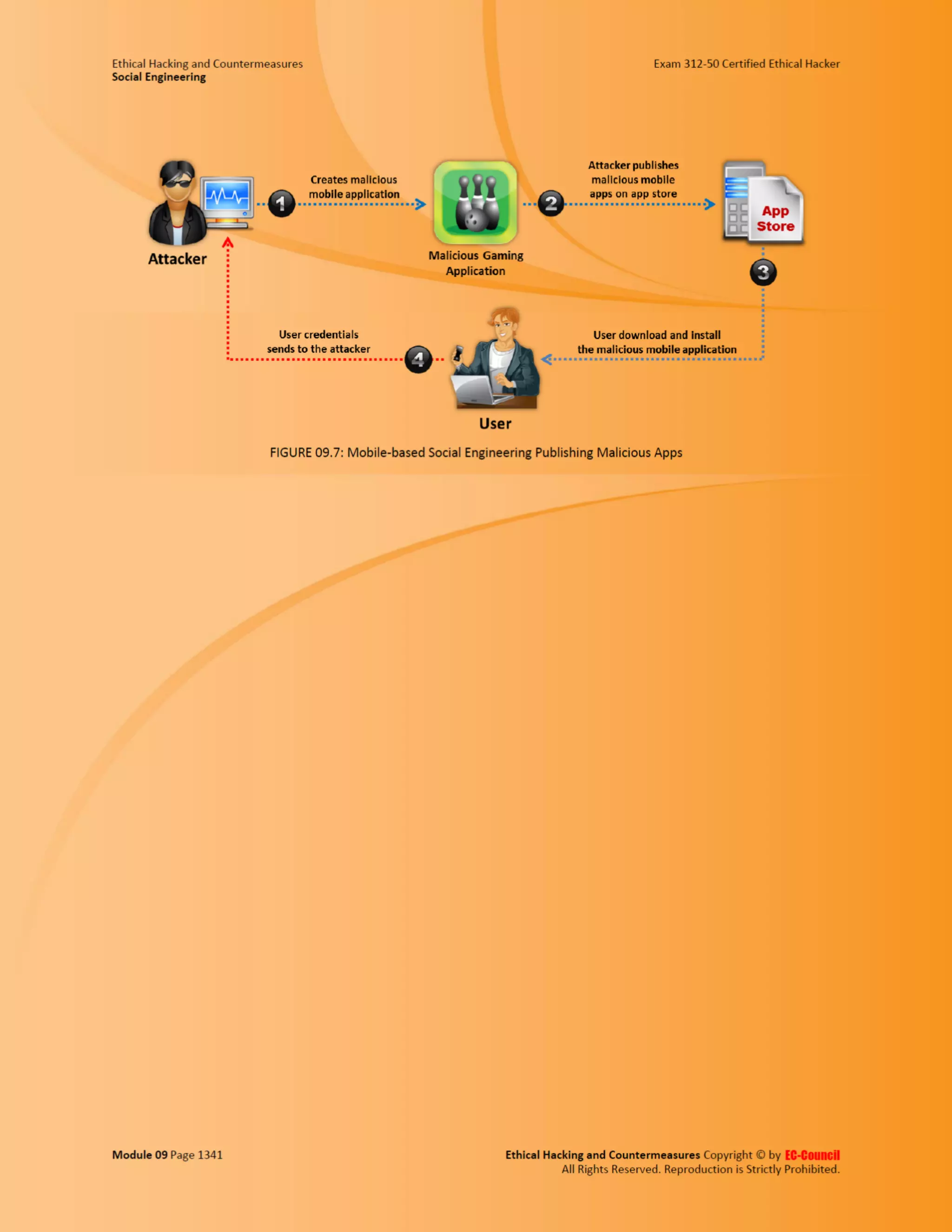

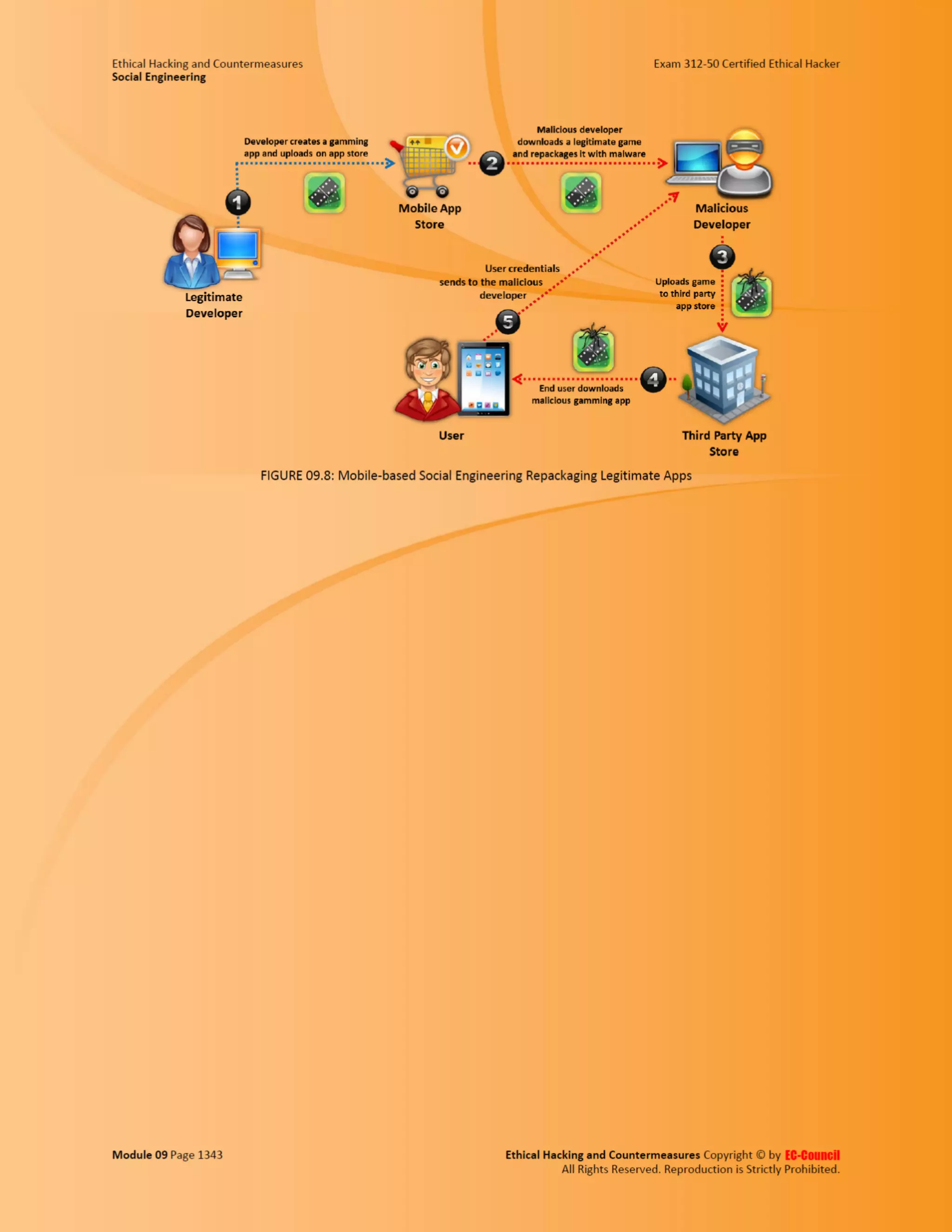


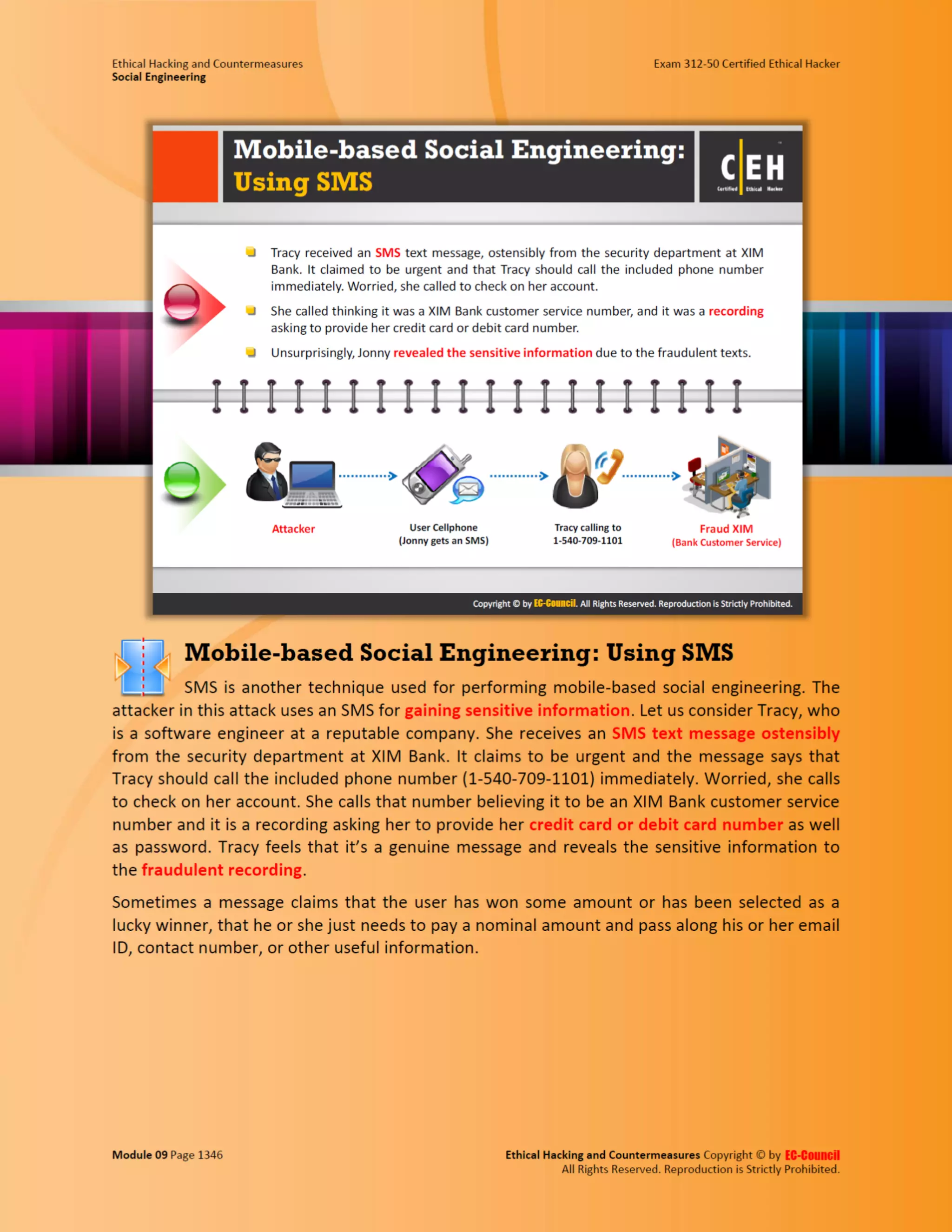

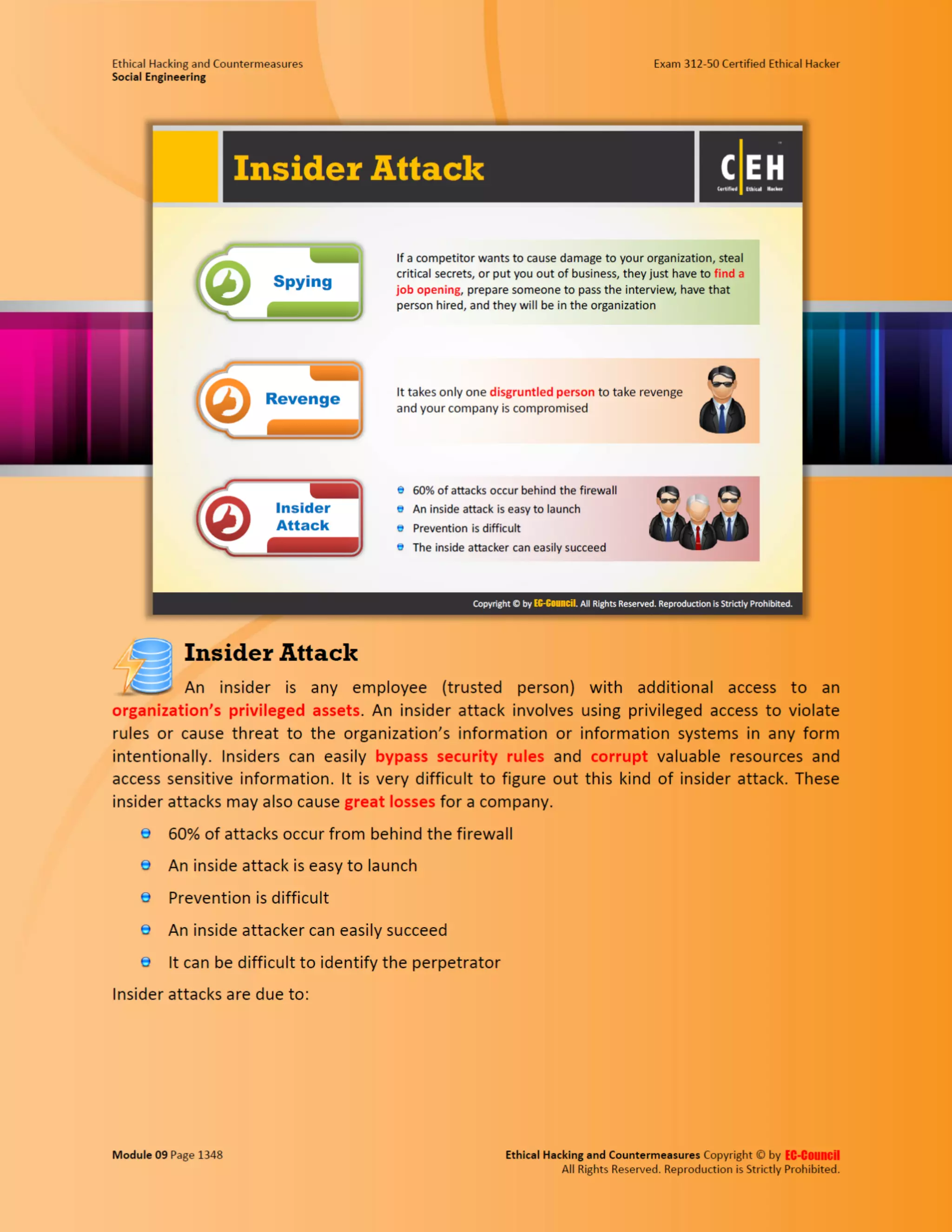

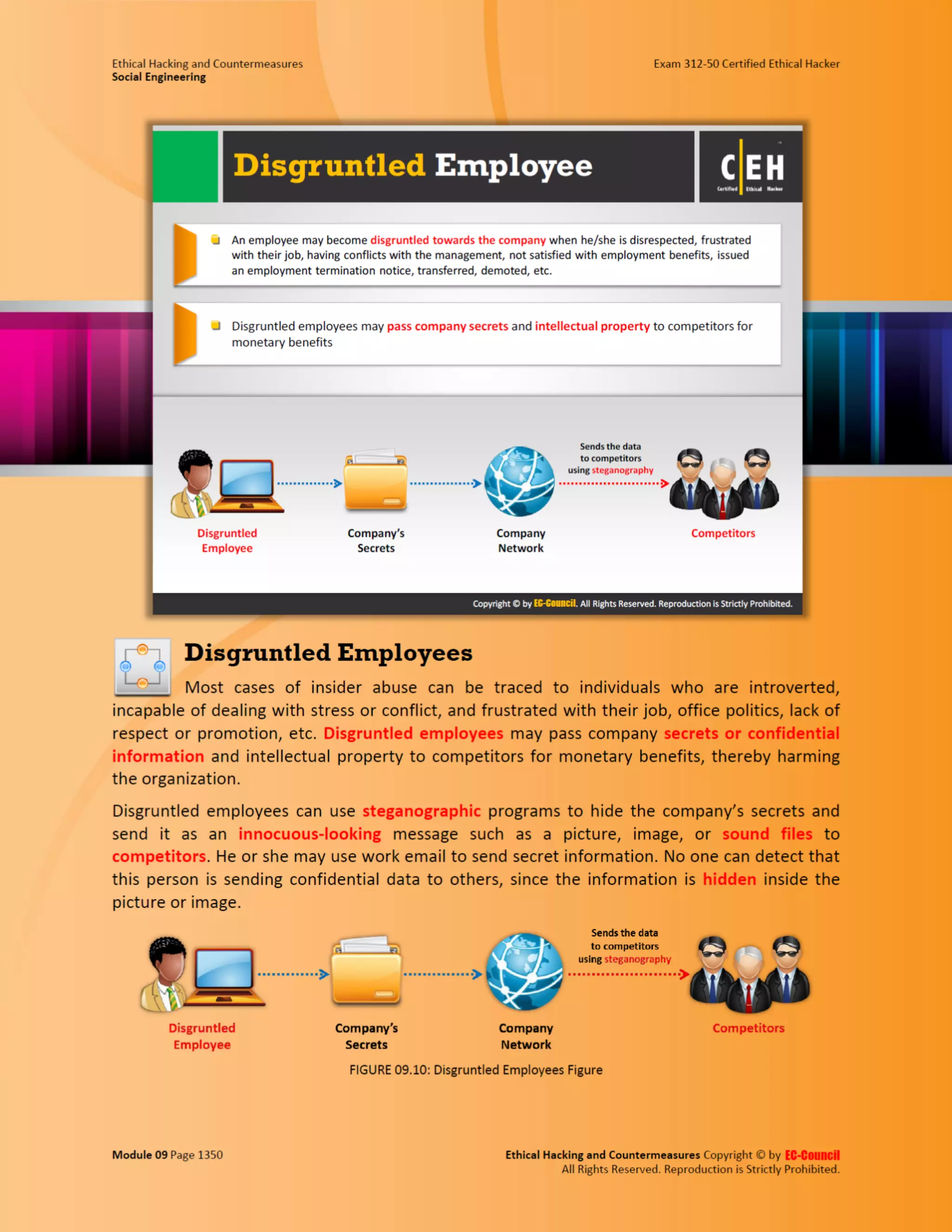



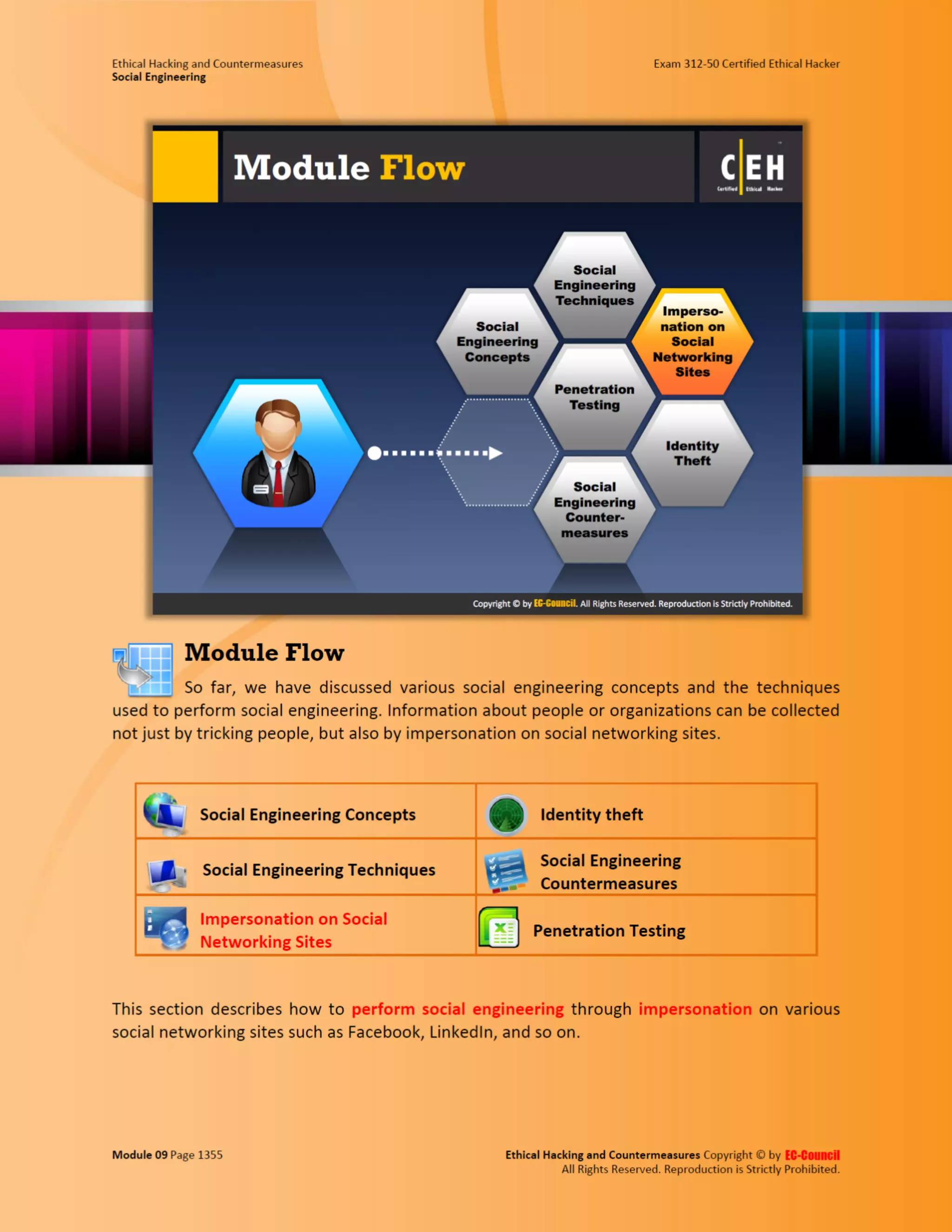

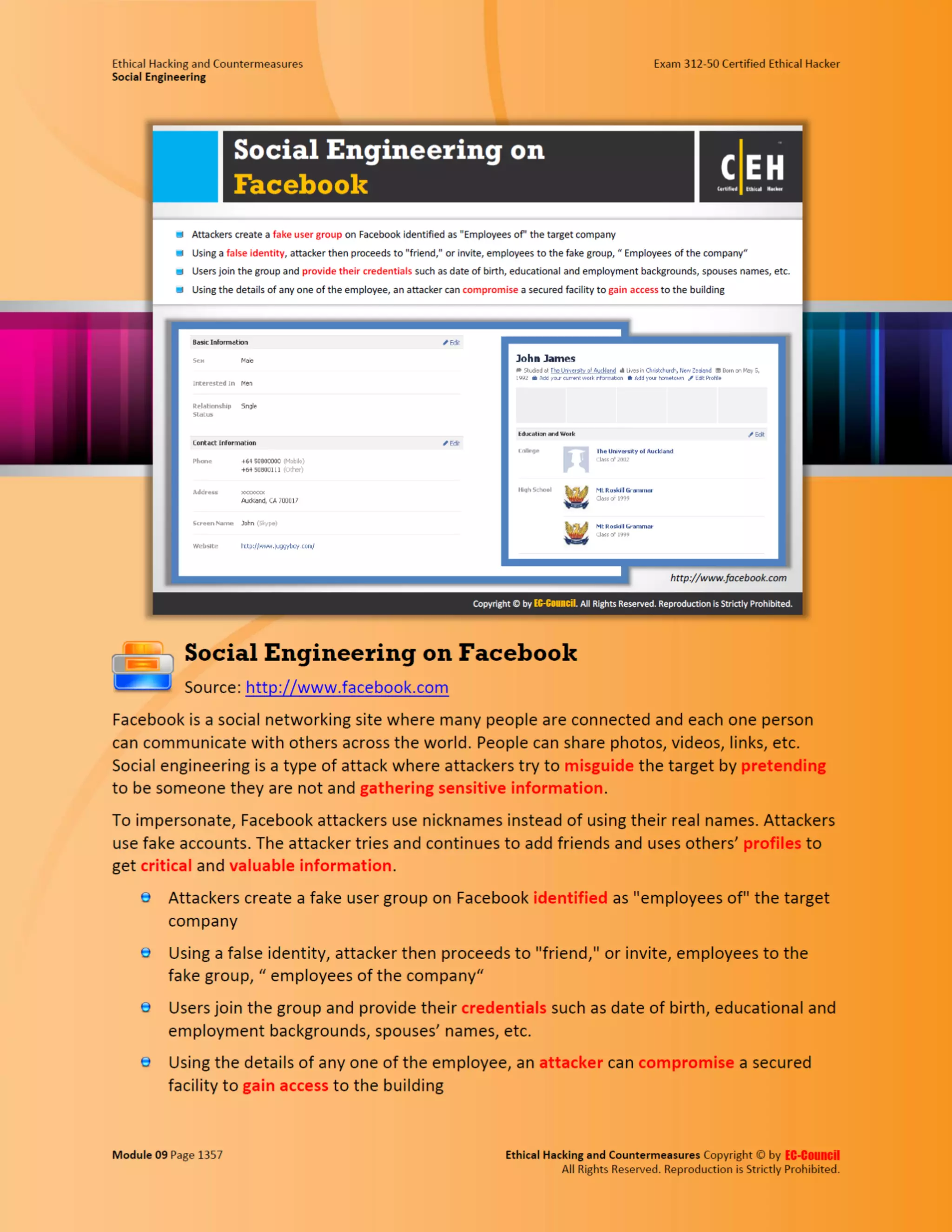
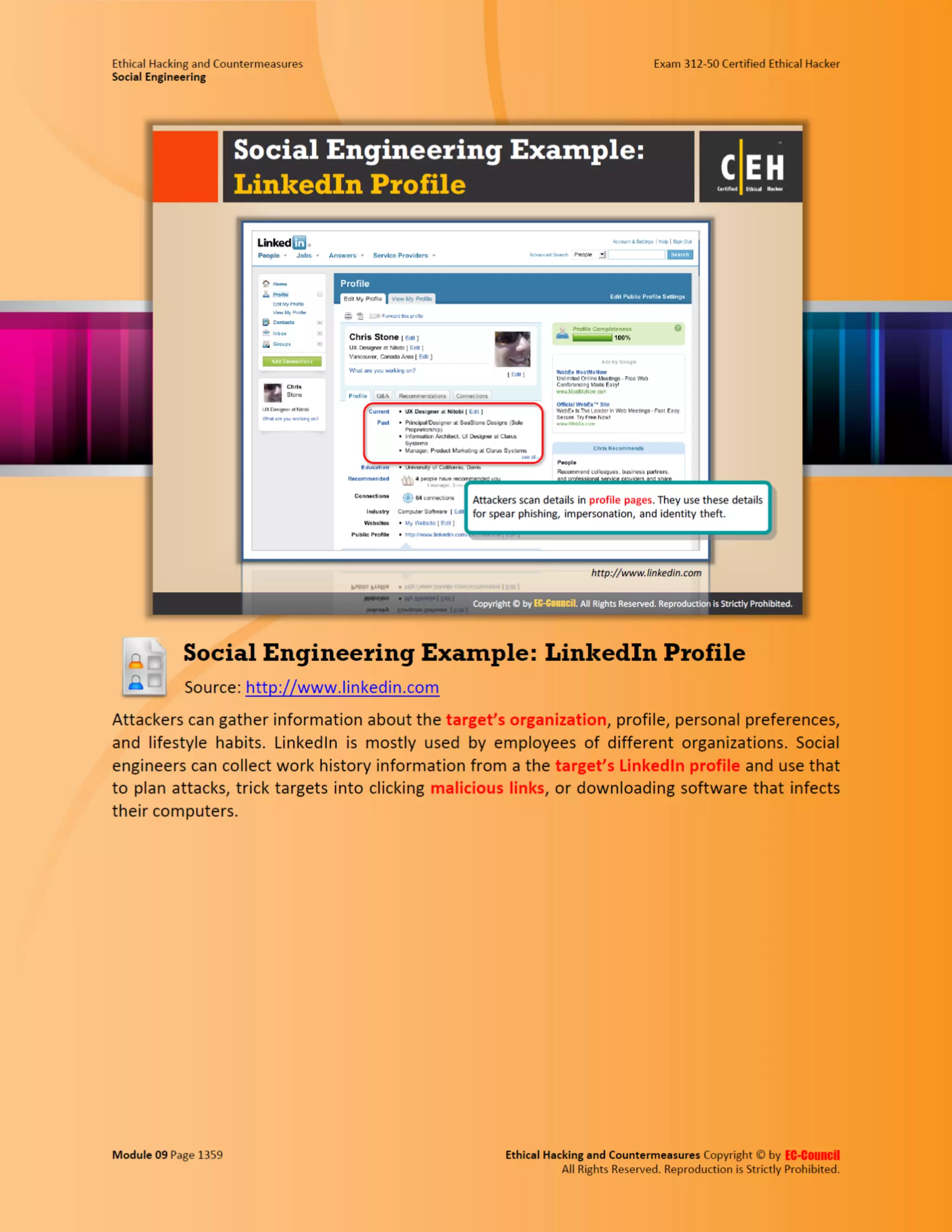
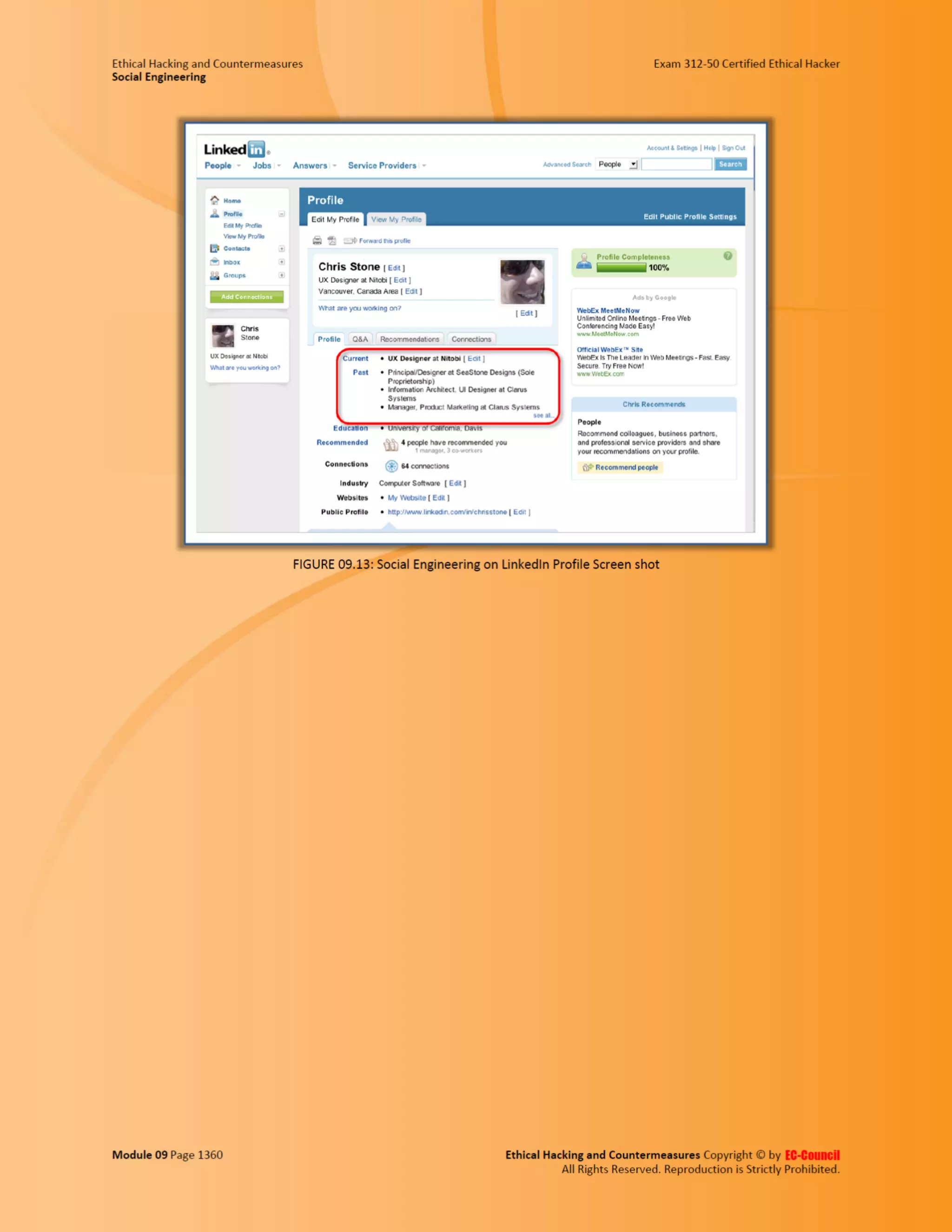
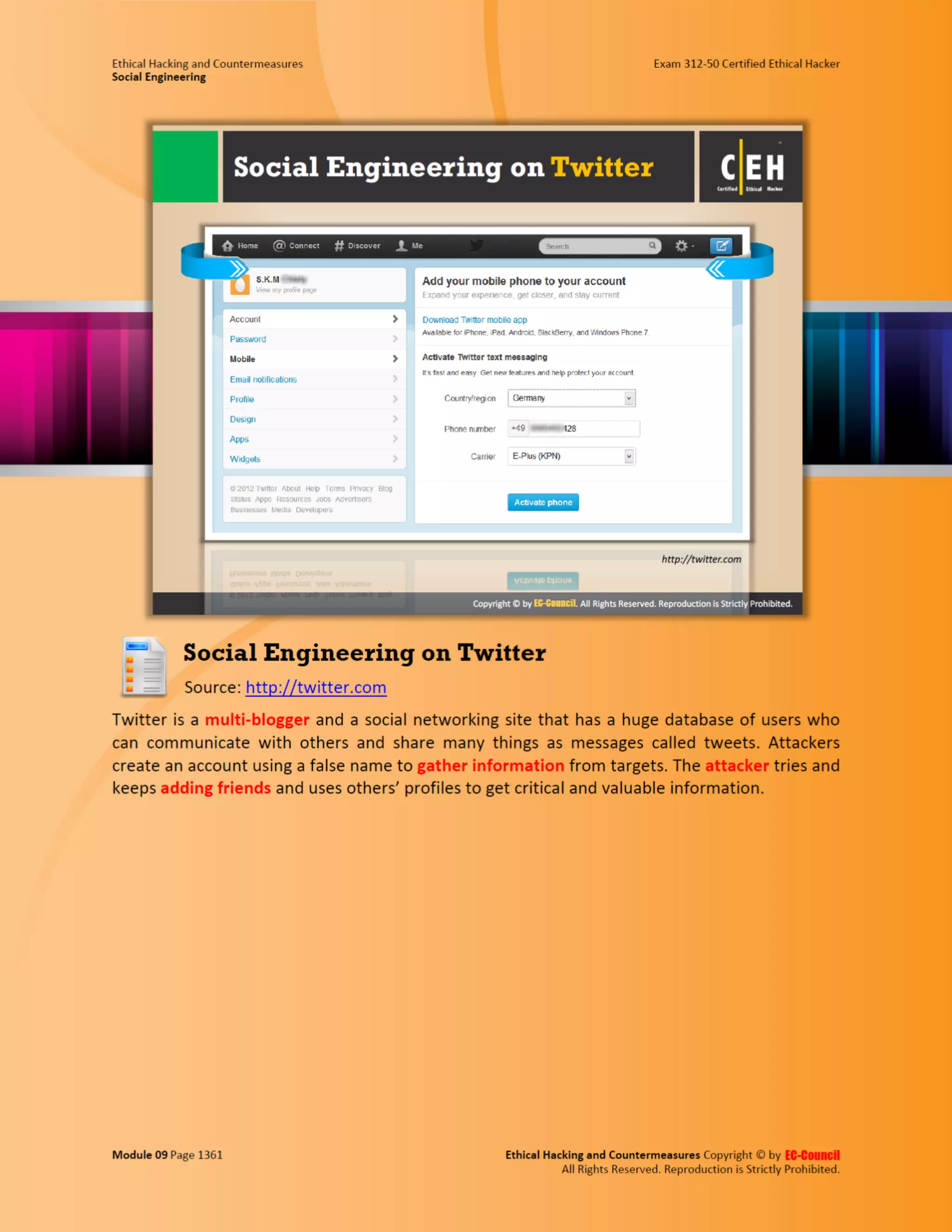
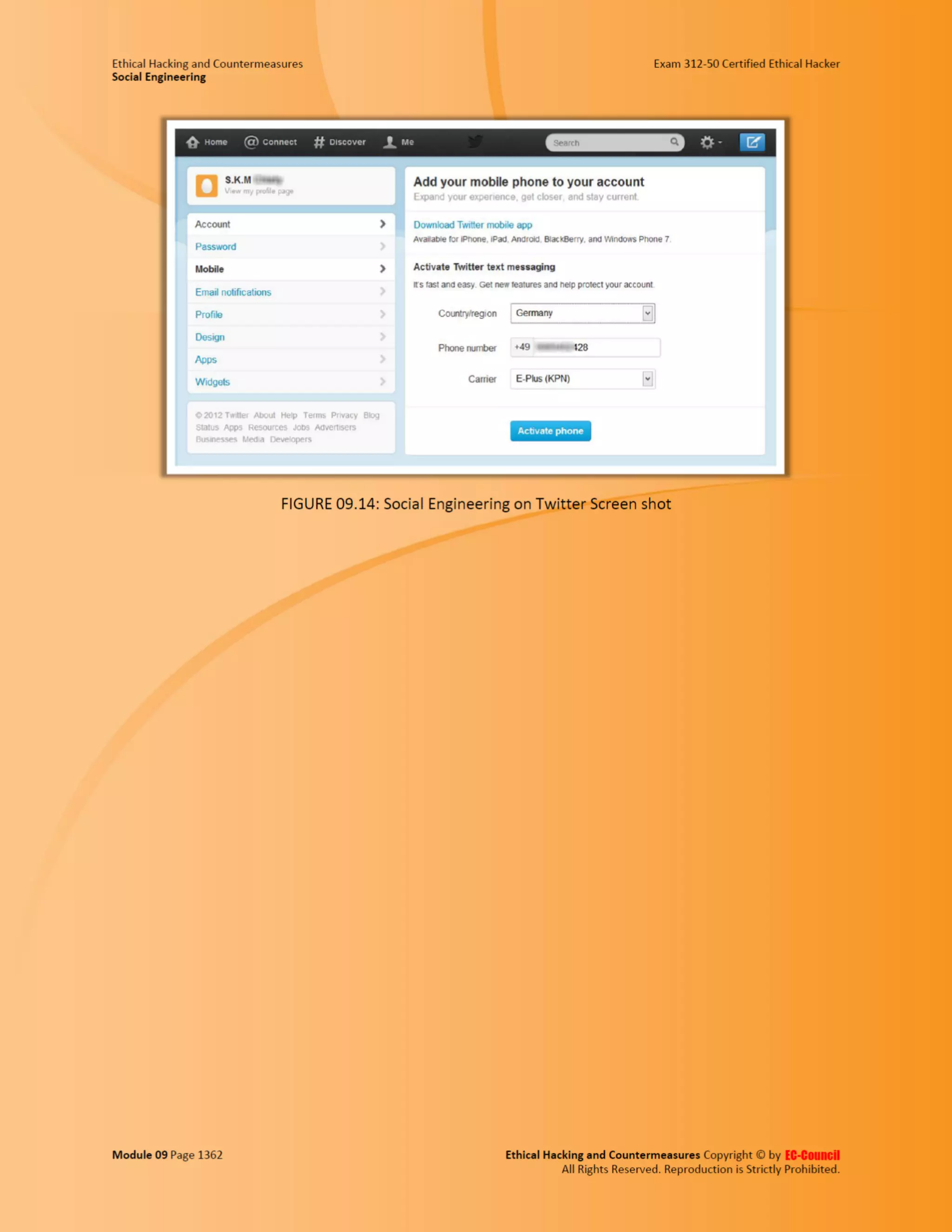

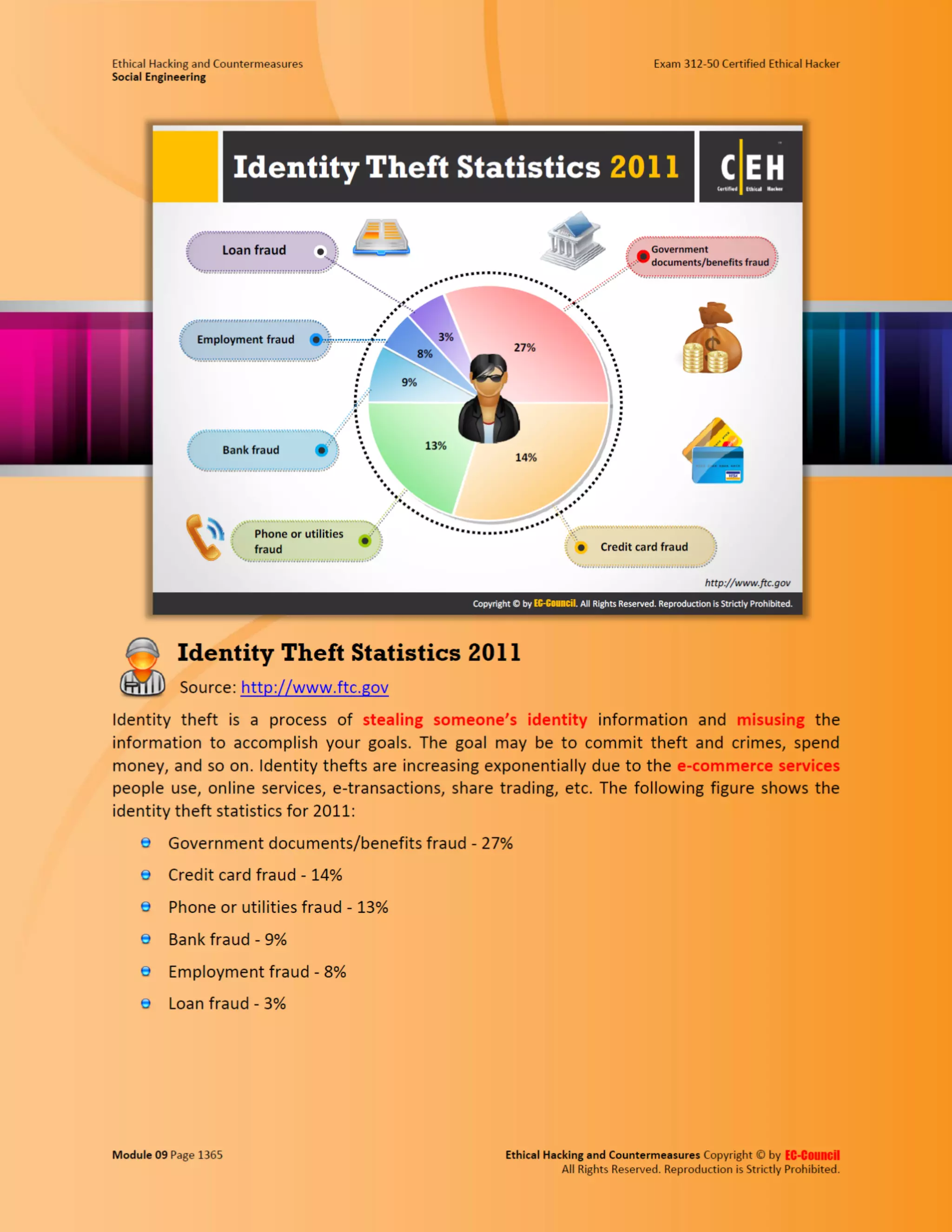
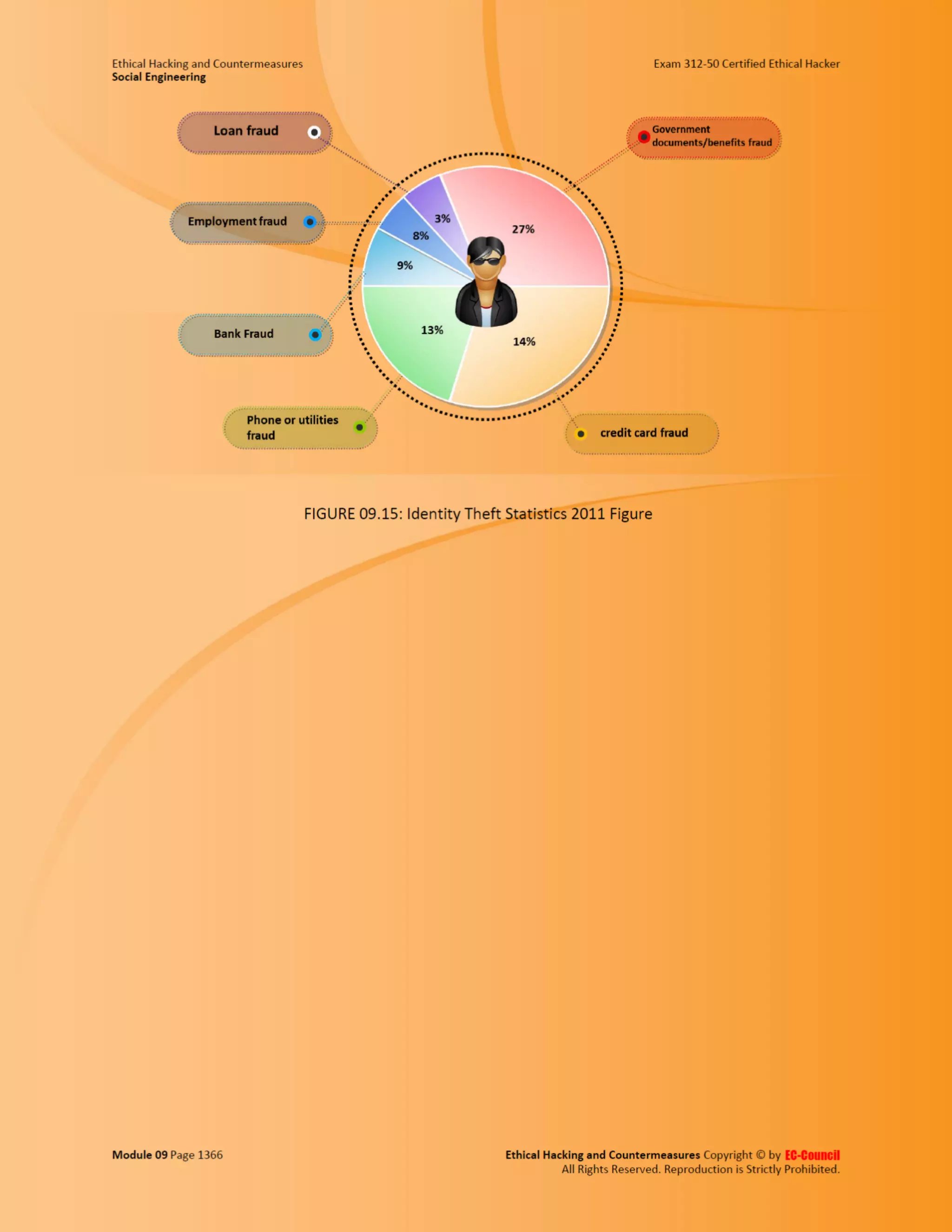
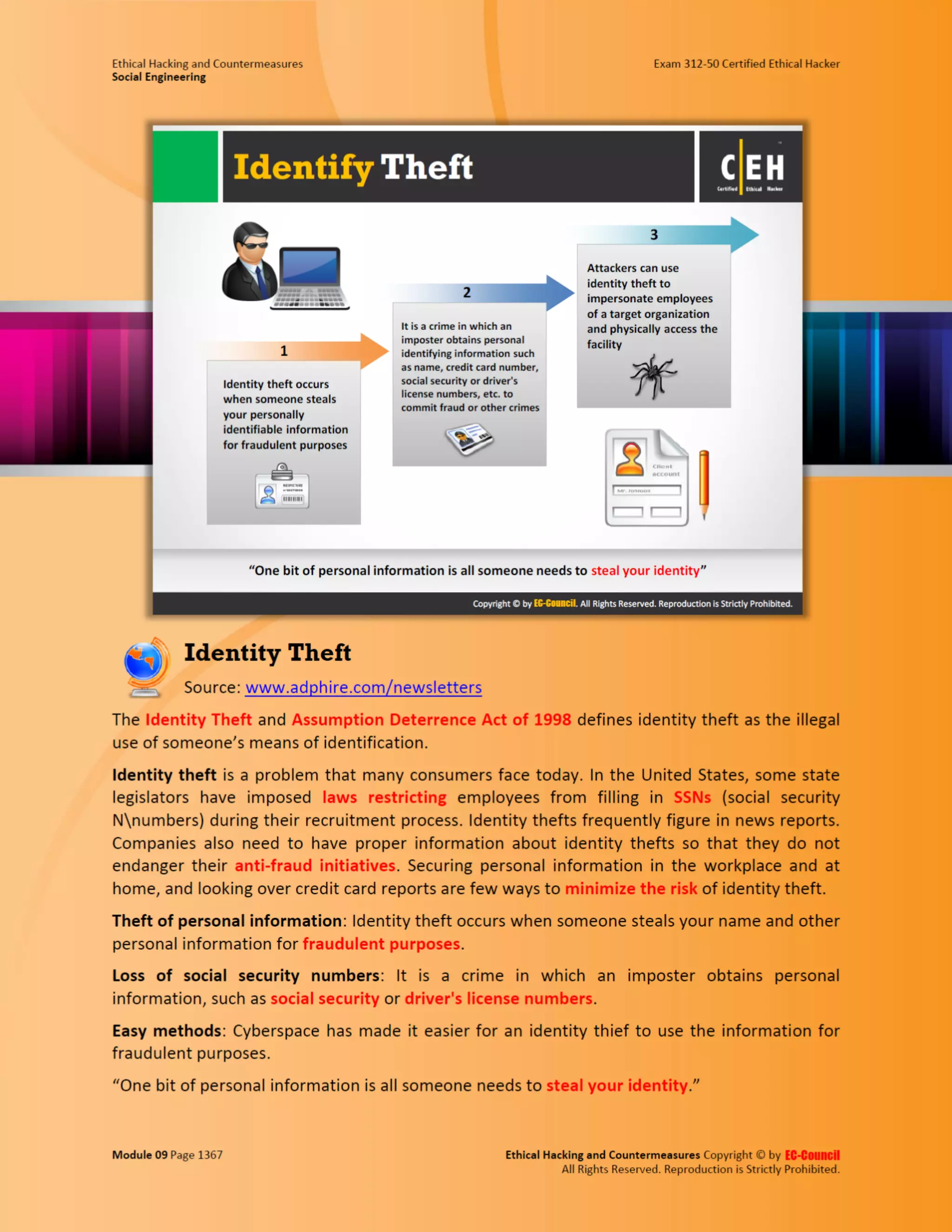

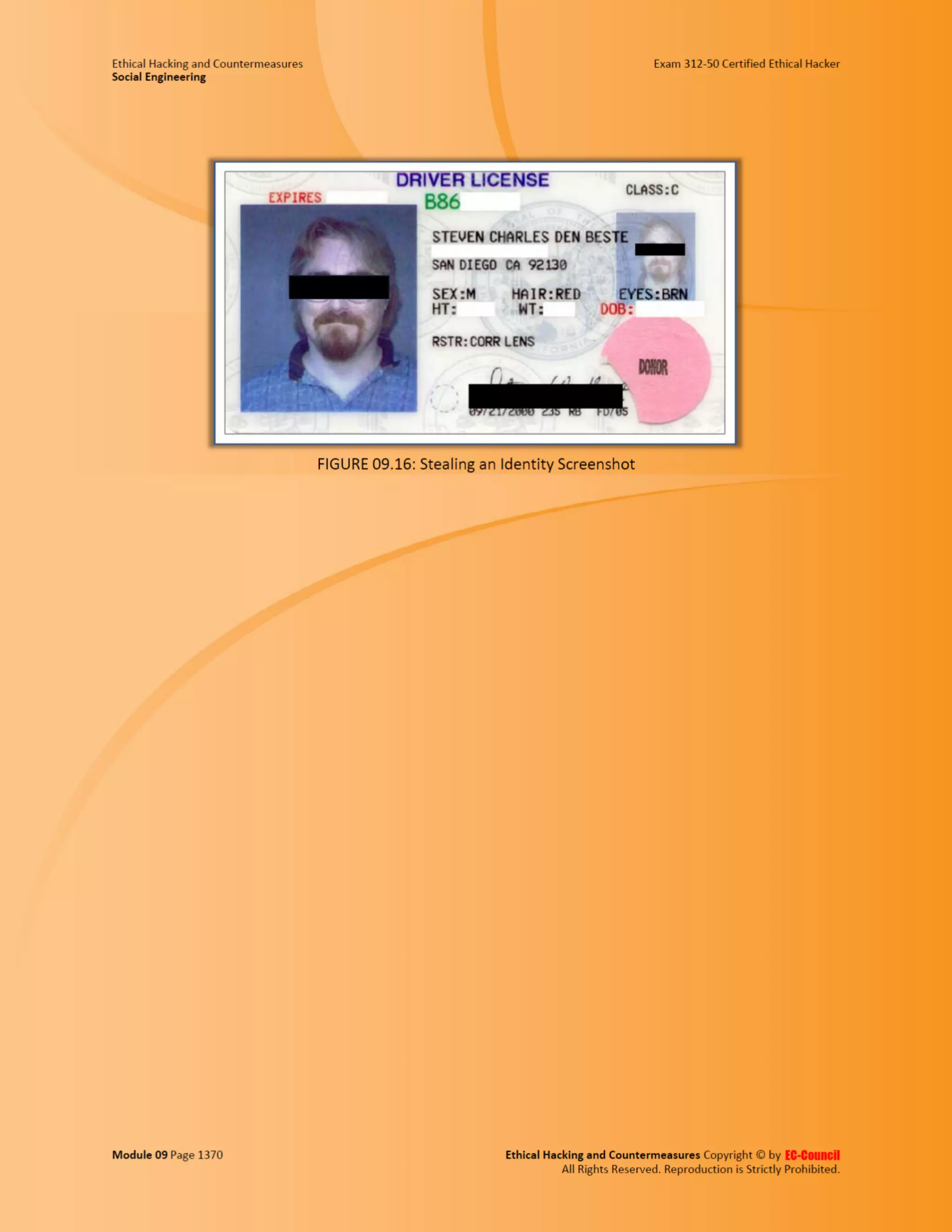
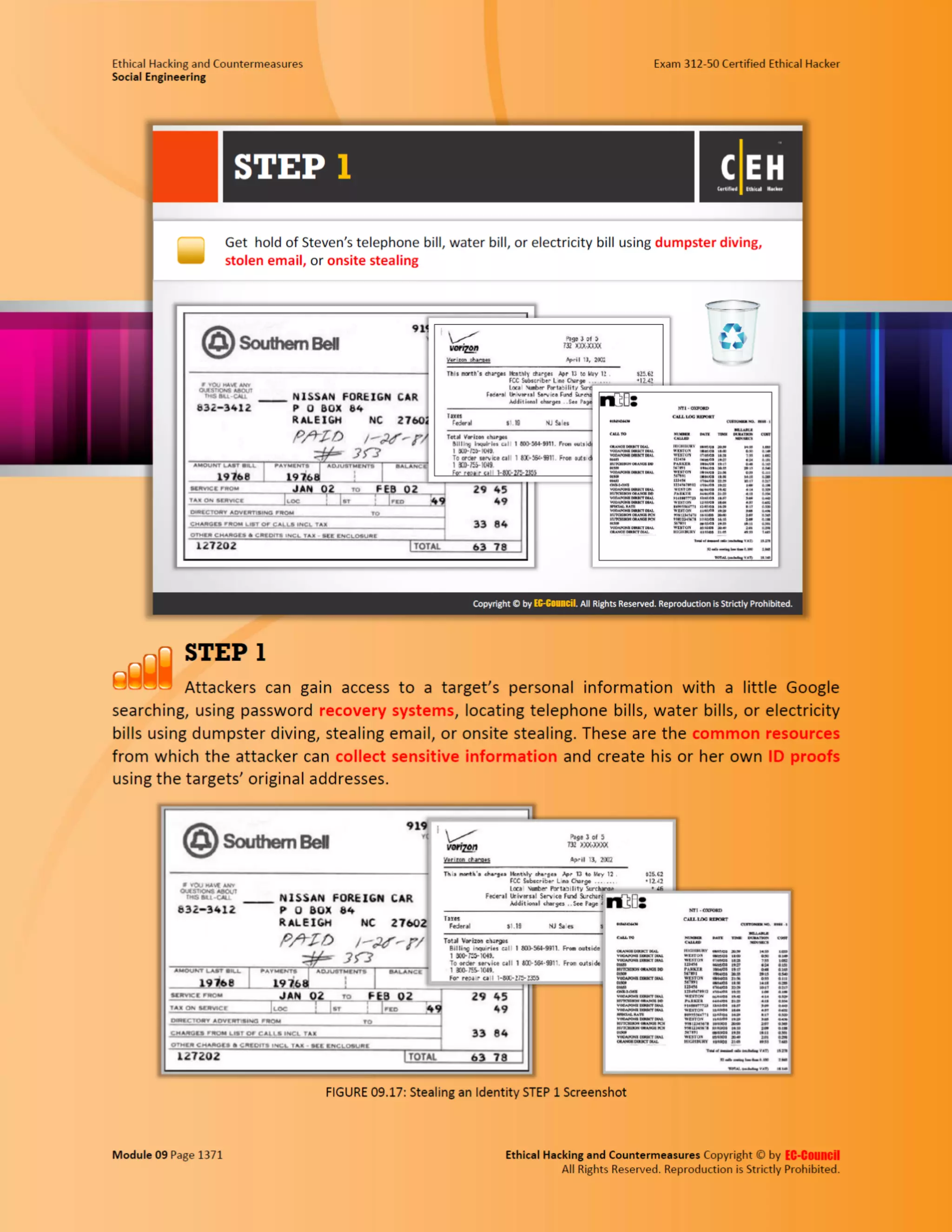
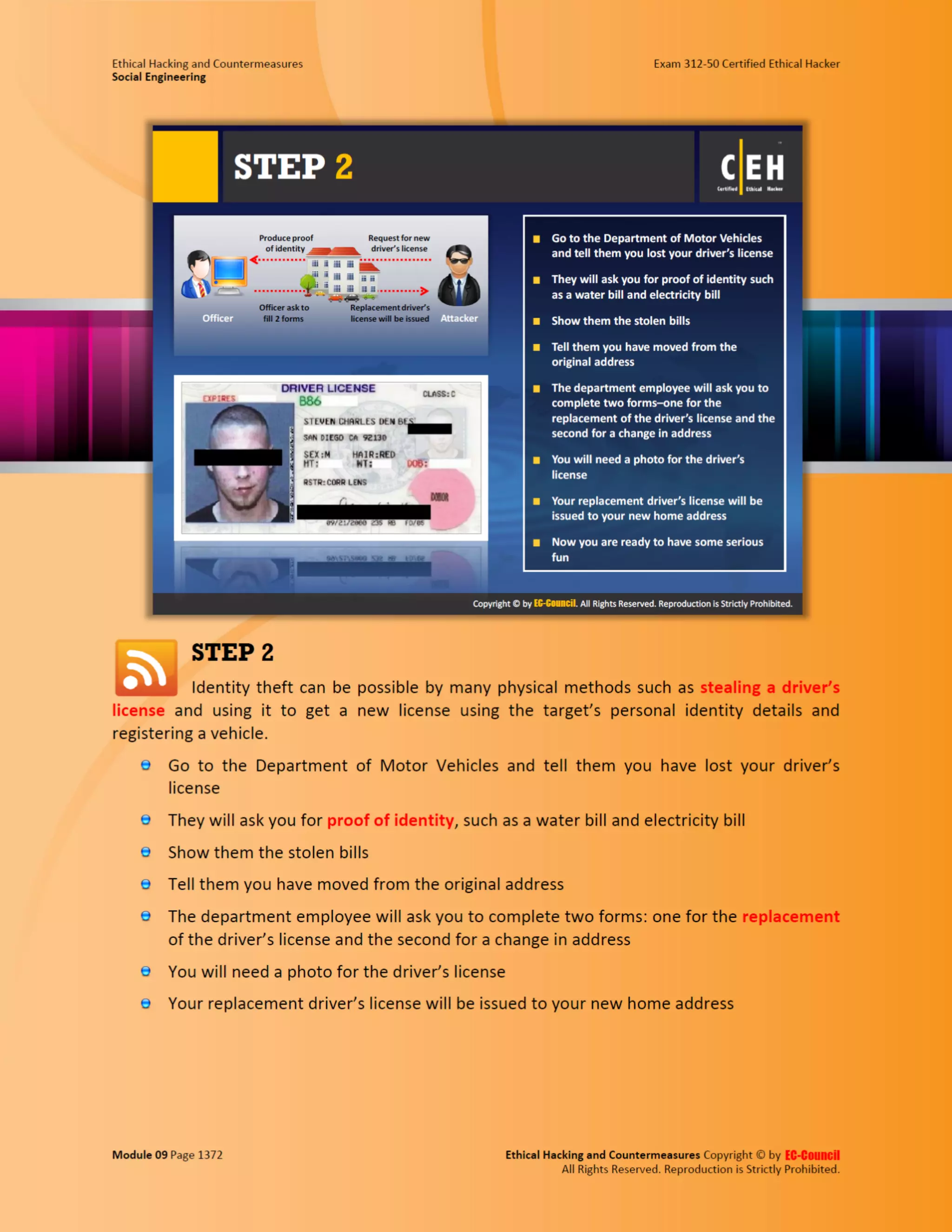
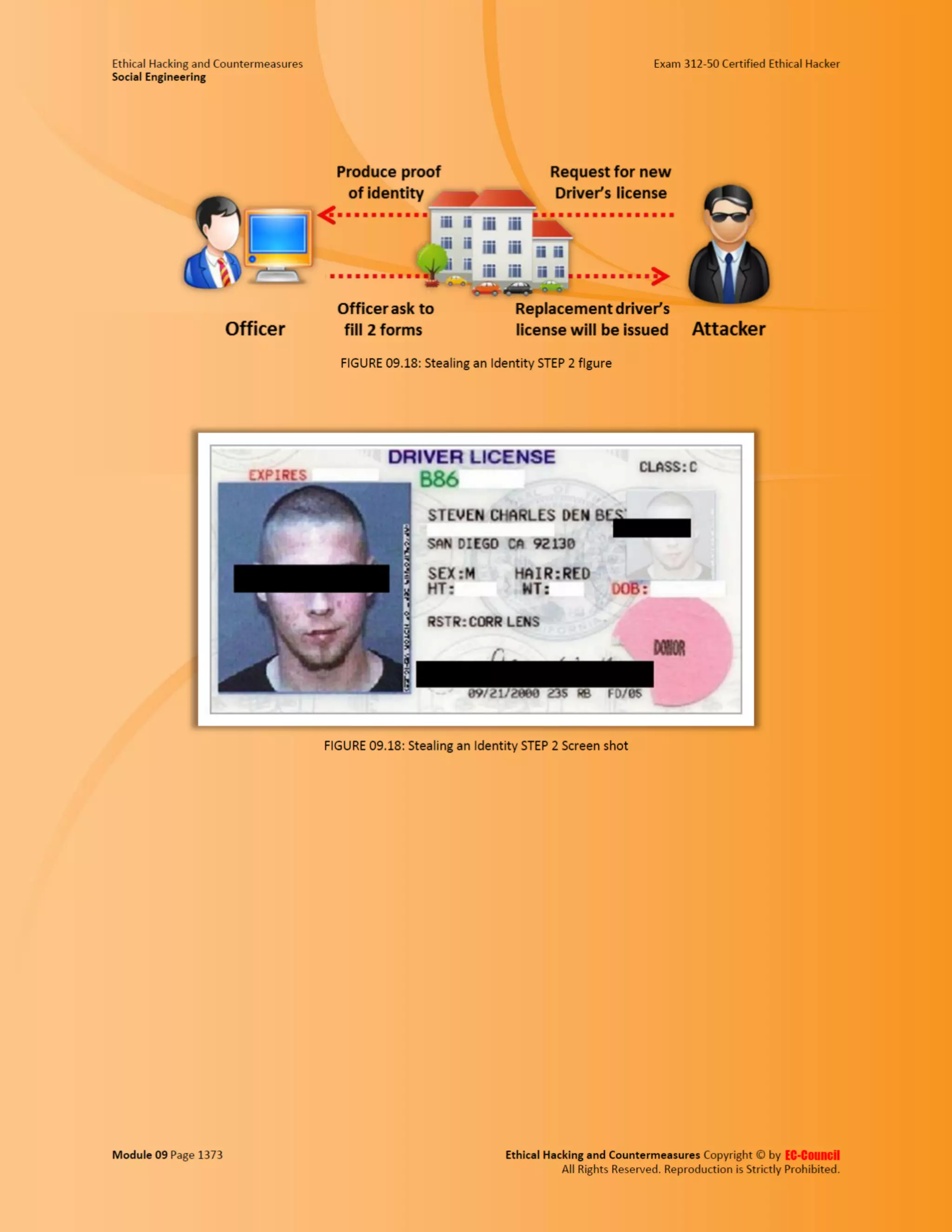
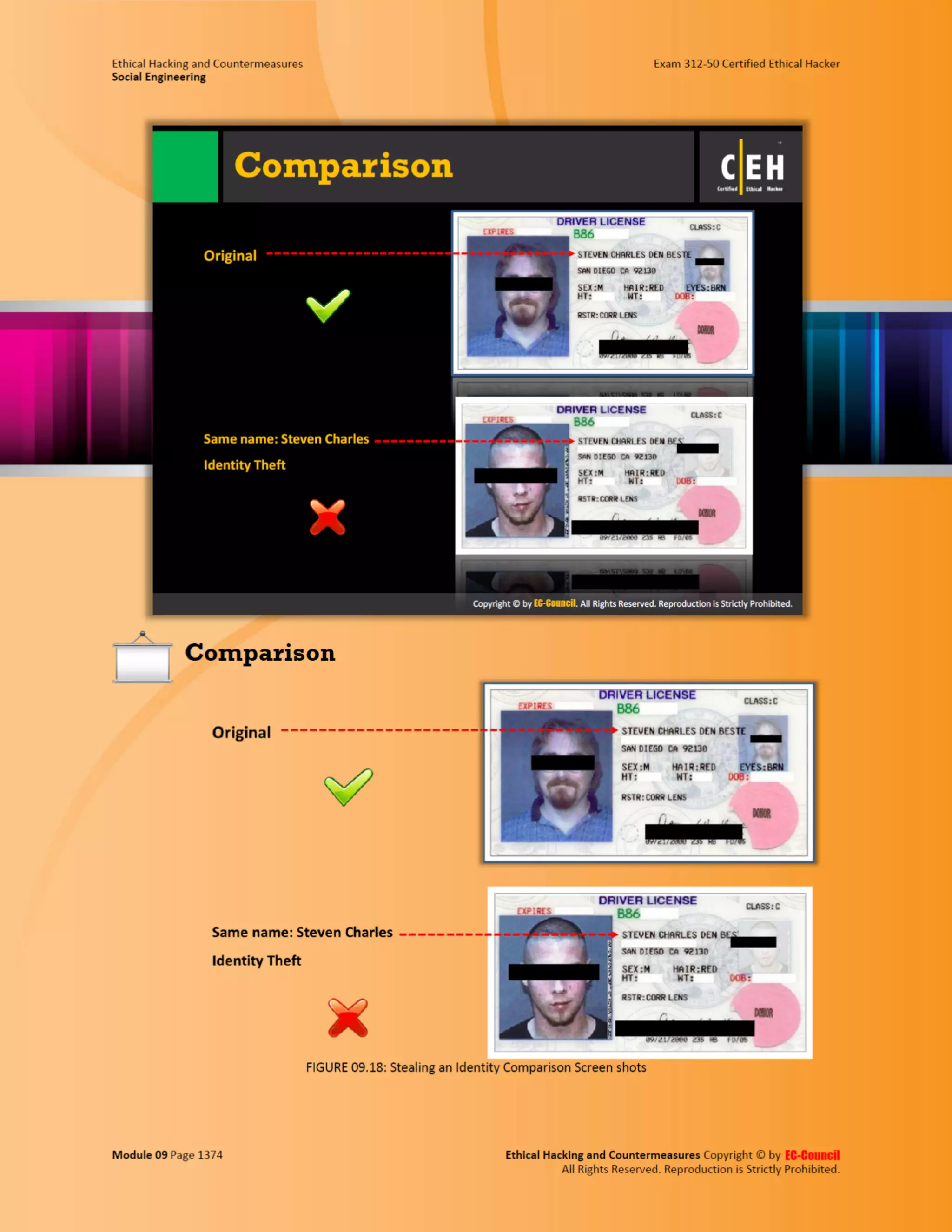

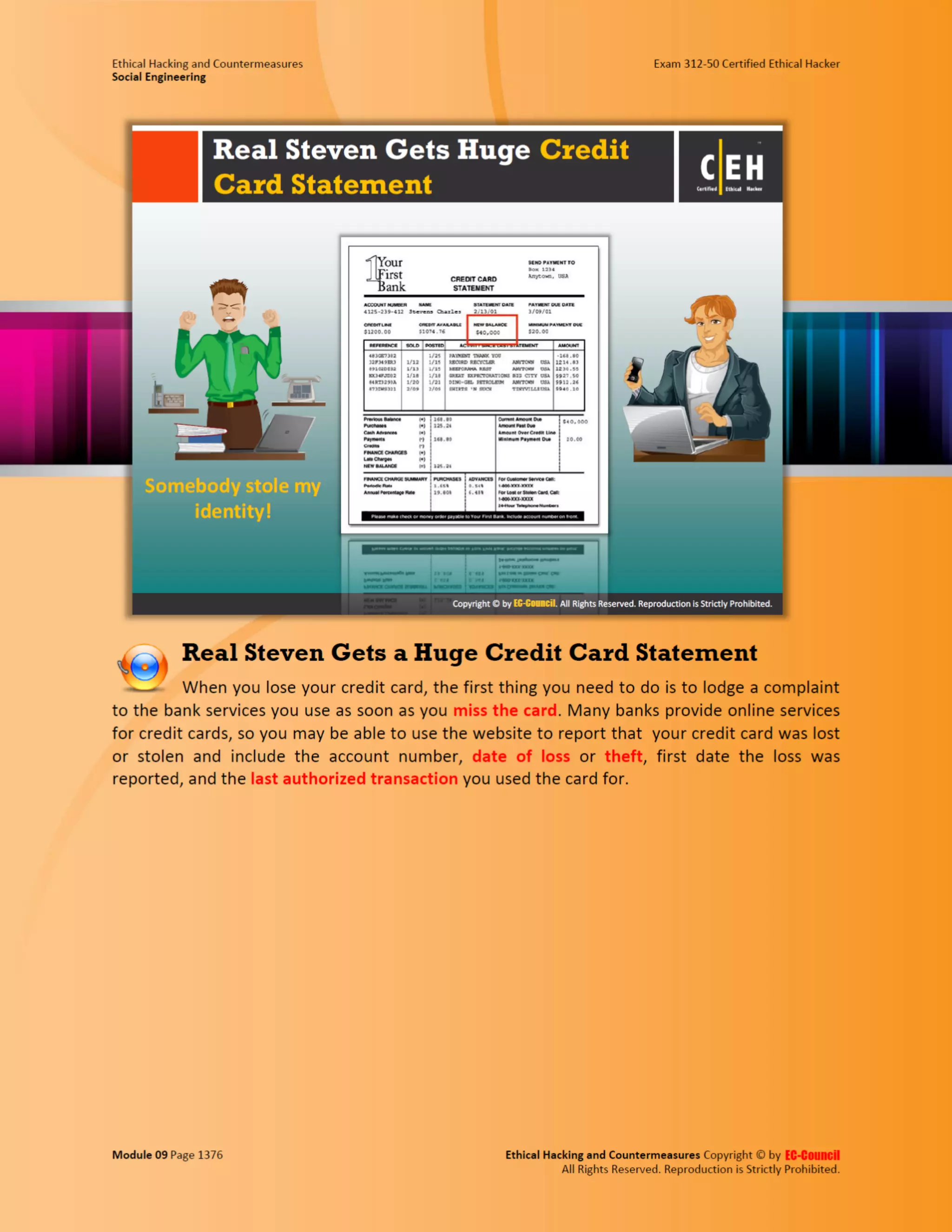



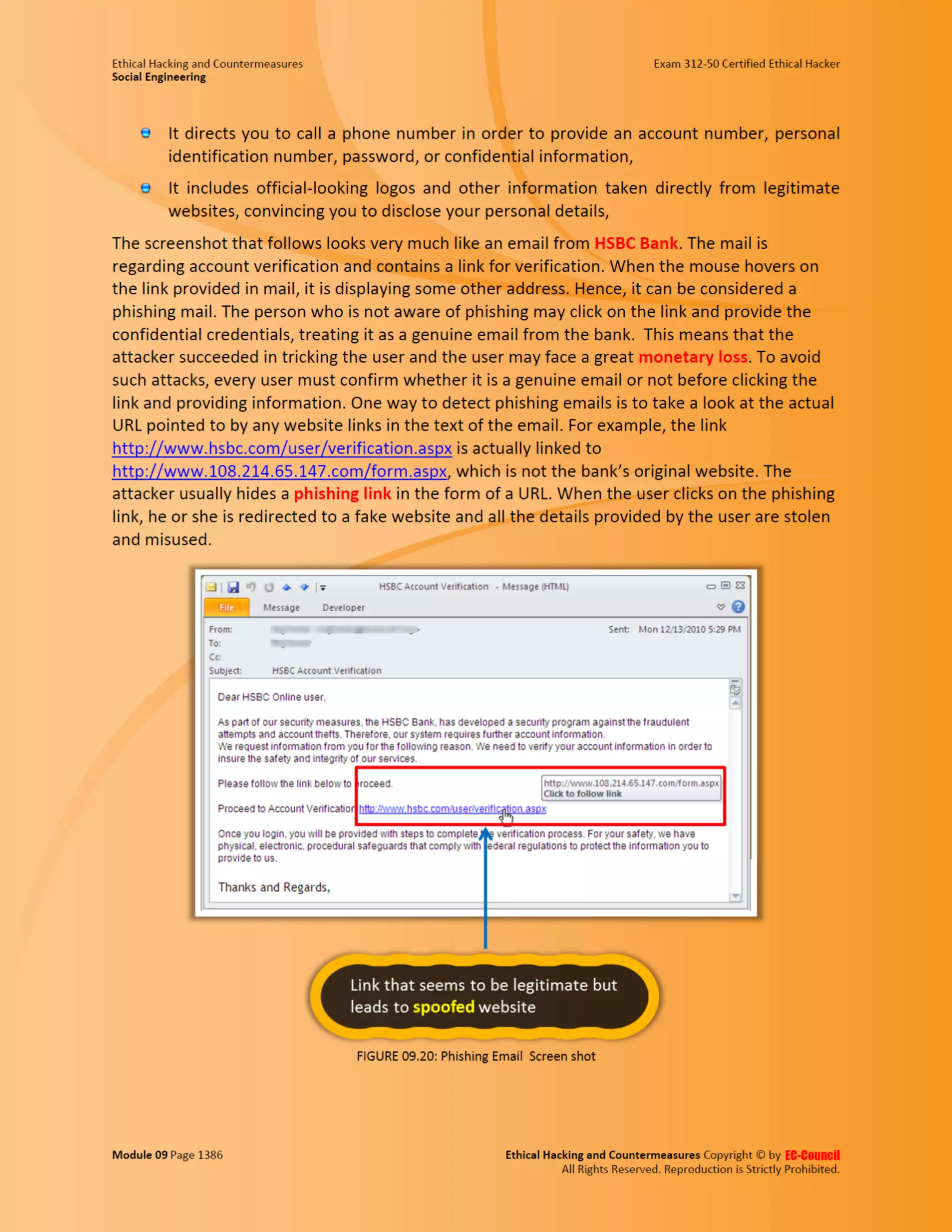
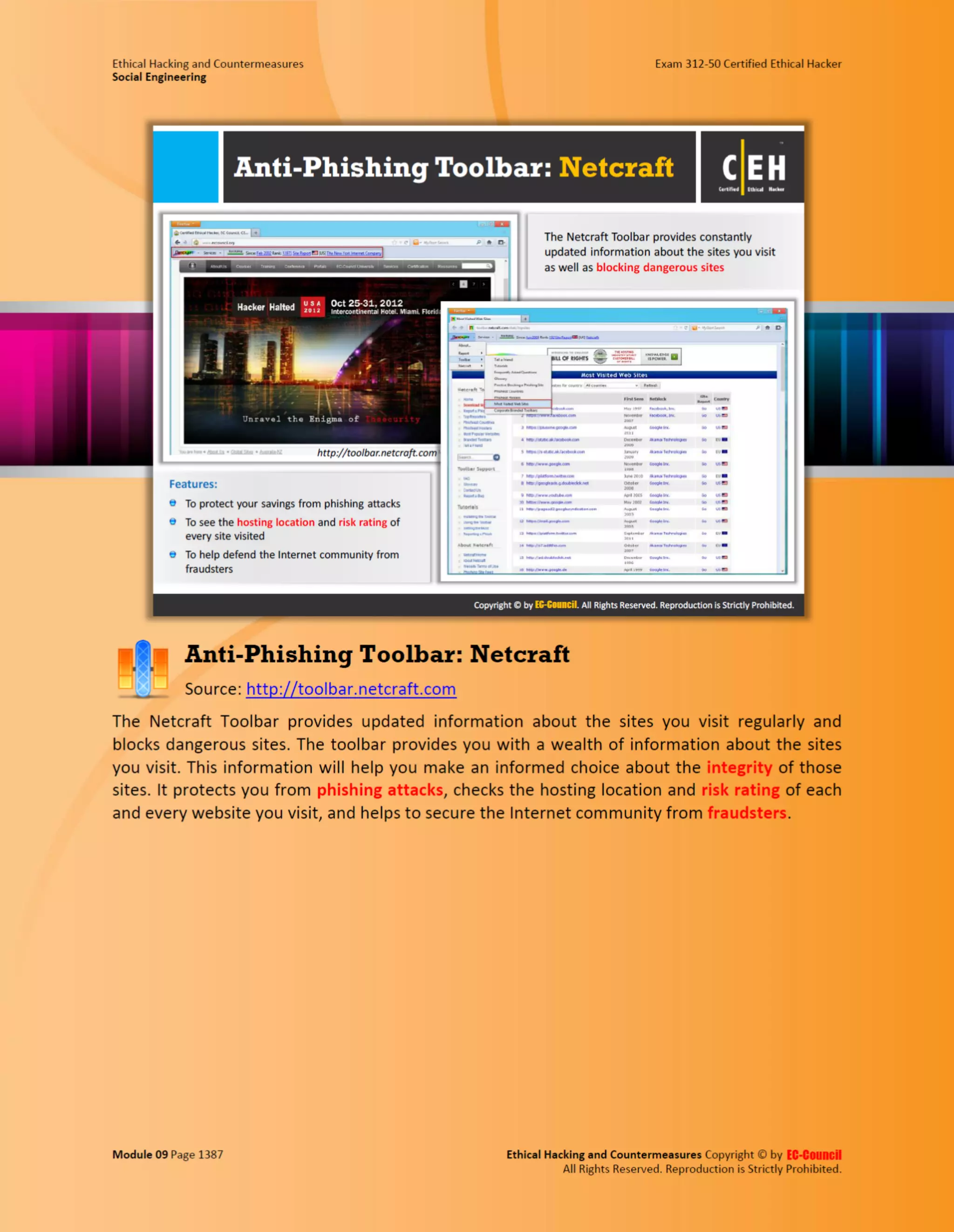
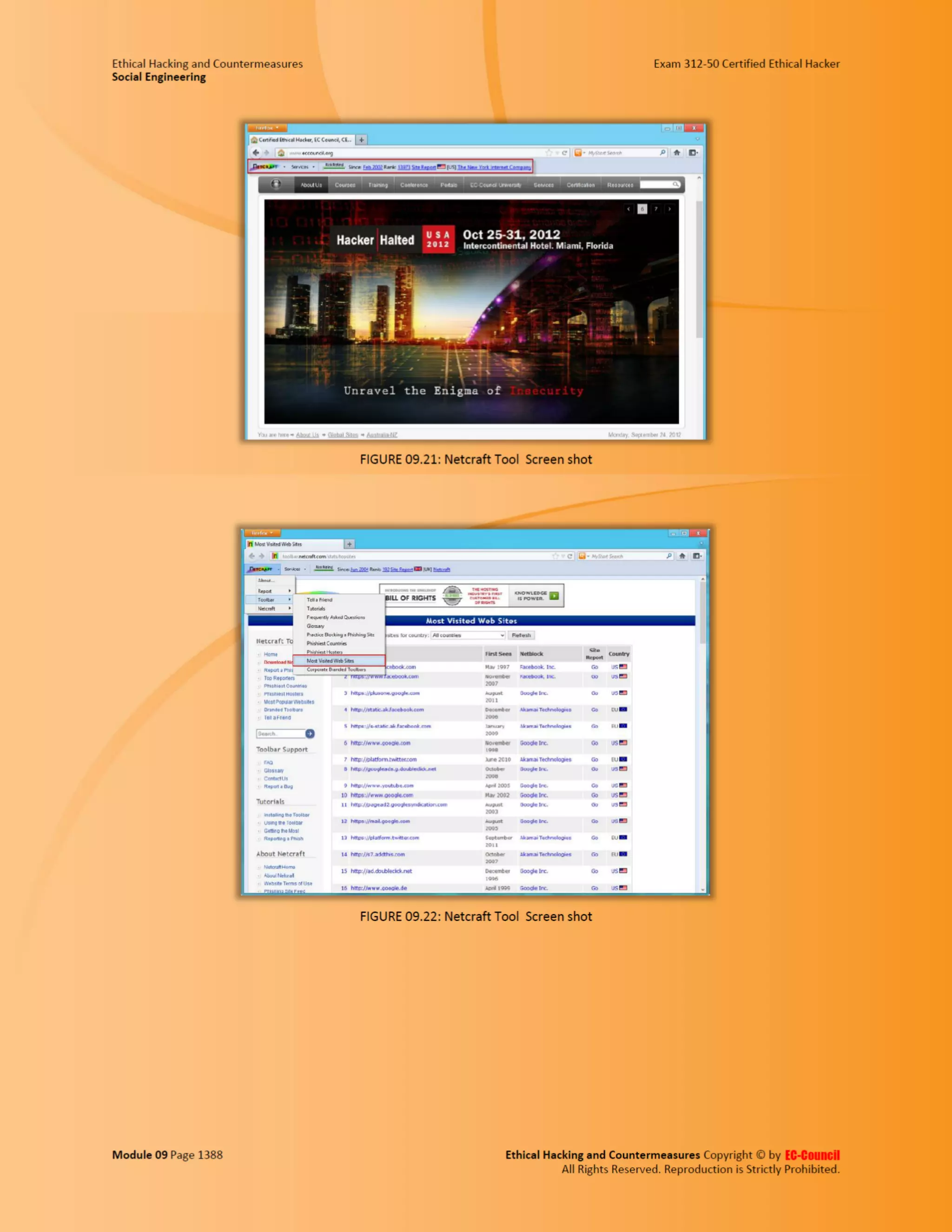
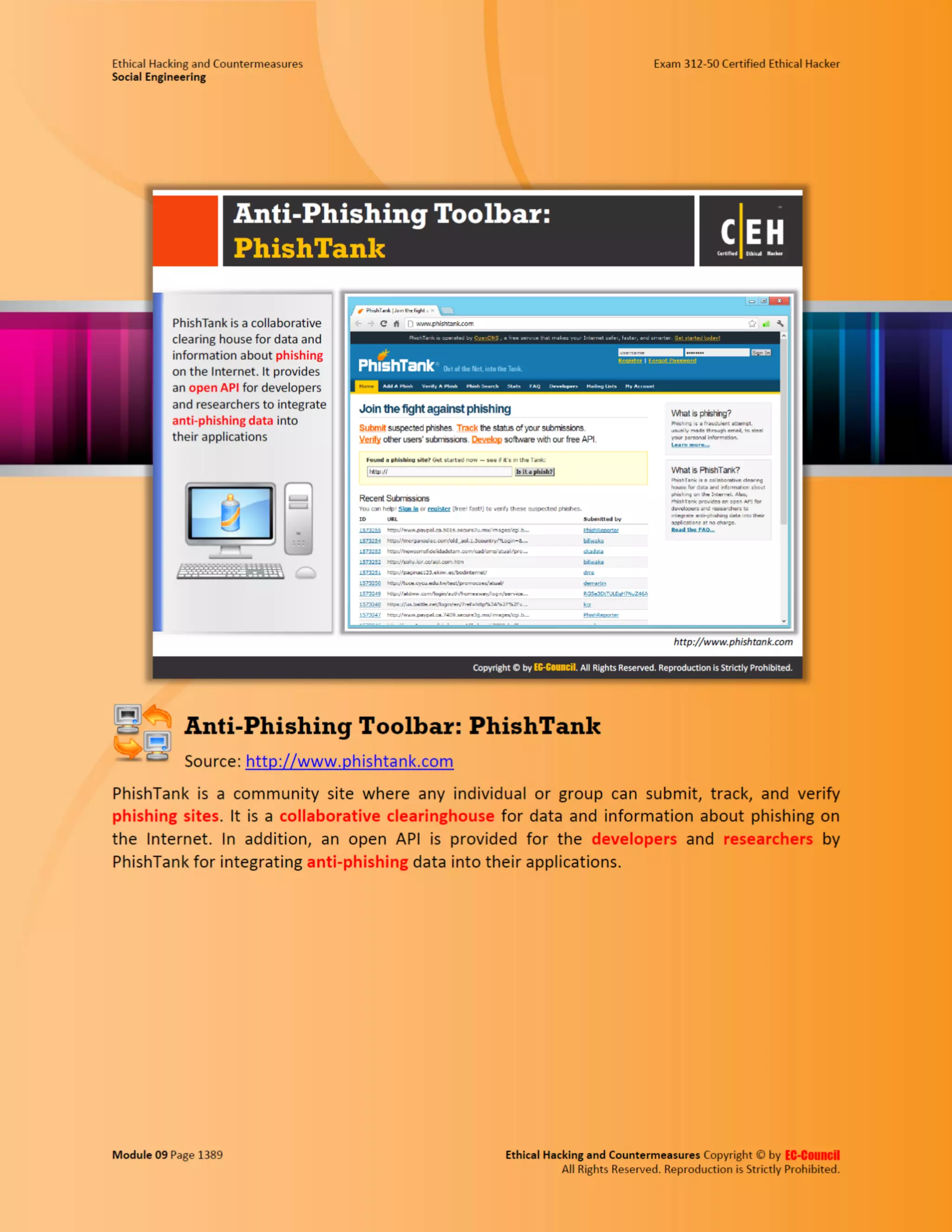






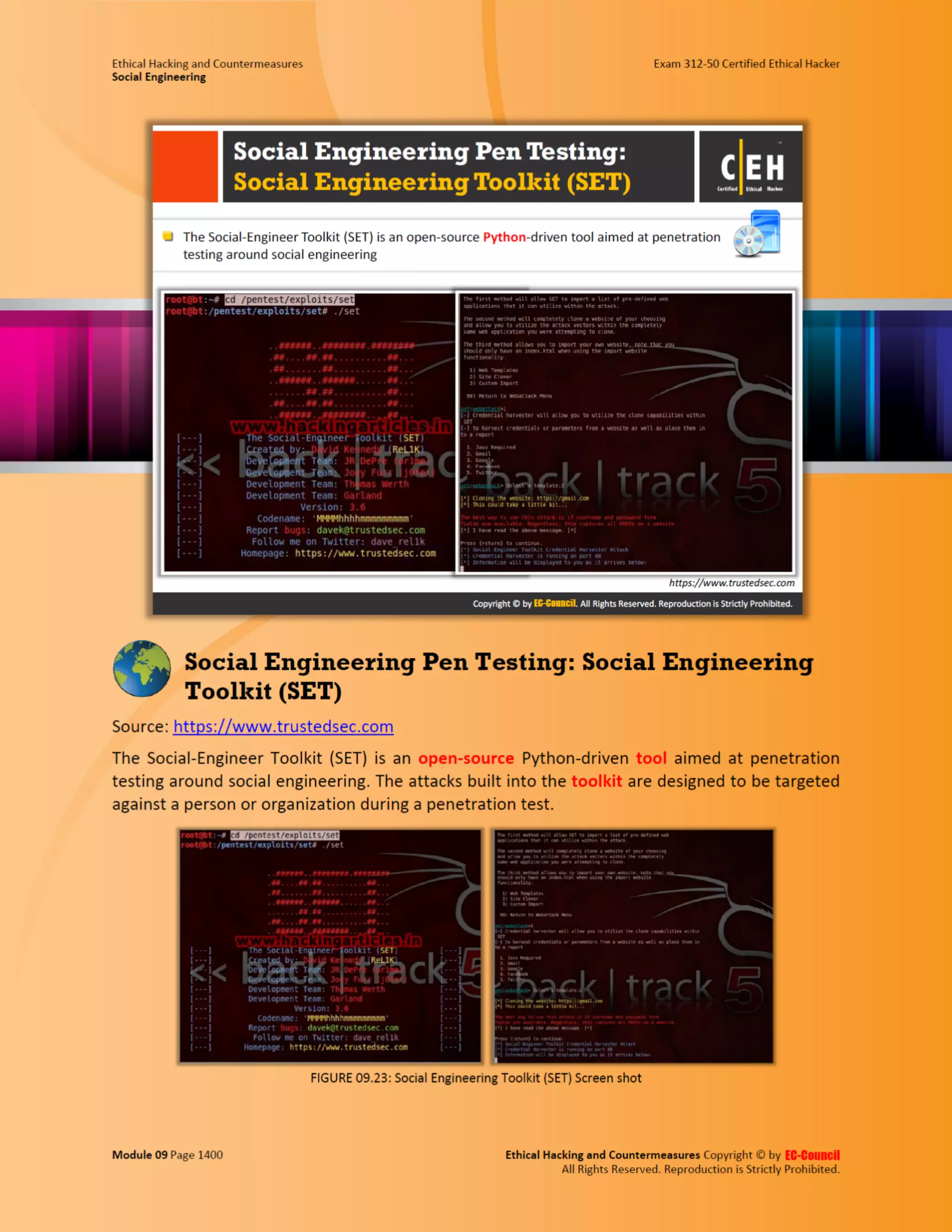


This document outlines the key features and benefits of a new software application designed to improve productivity. It highlights user-friendly interfaces, integration capabilities with existing systems, and support for remote work. Additionally, the document discusses potential impacts on team collaboration and efficiency.













































































































