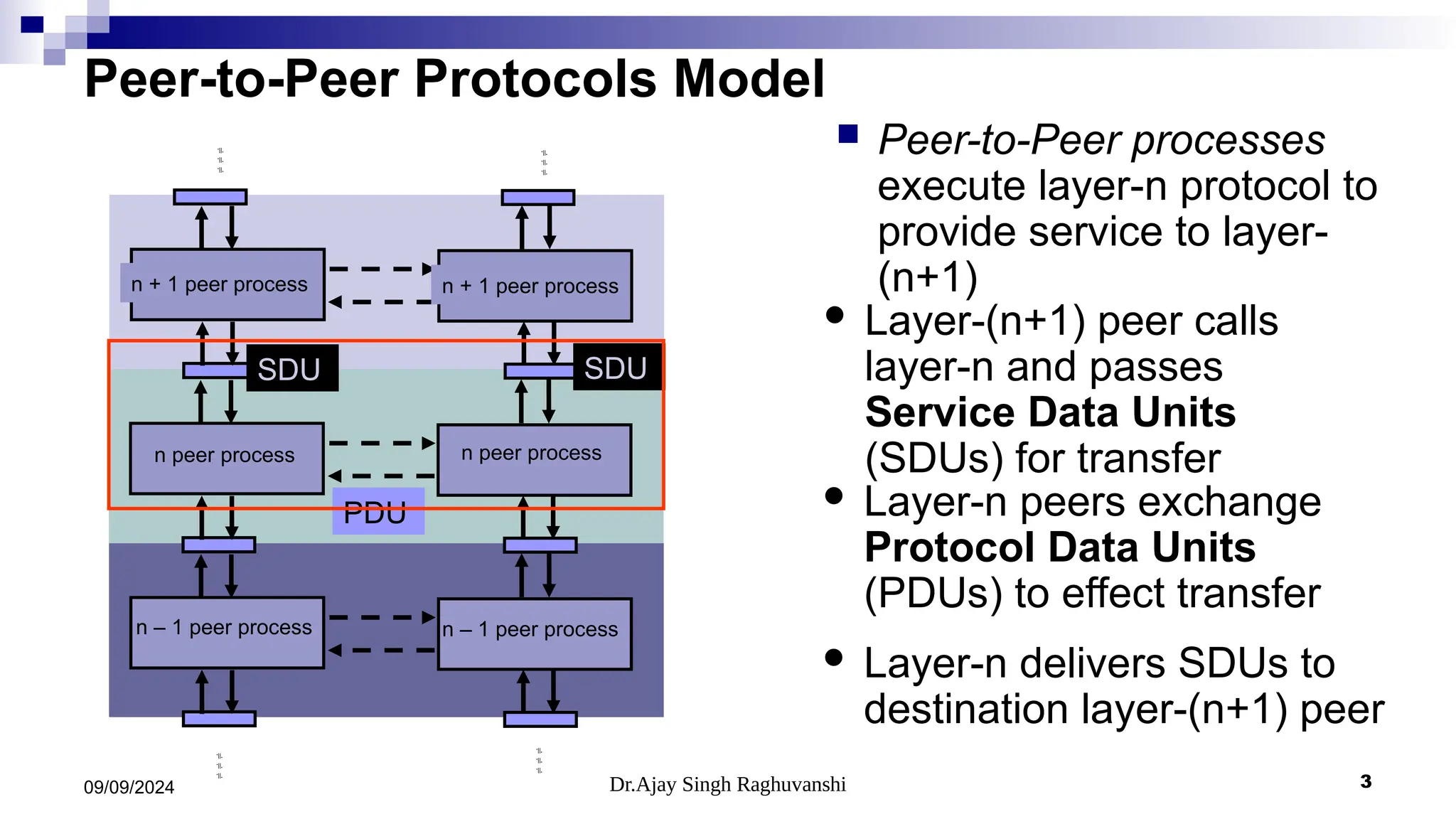
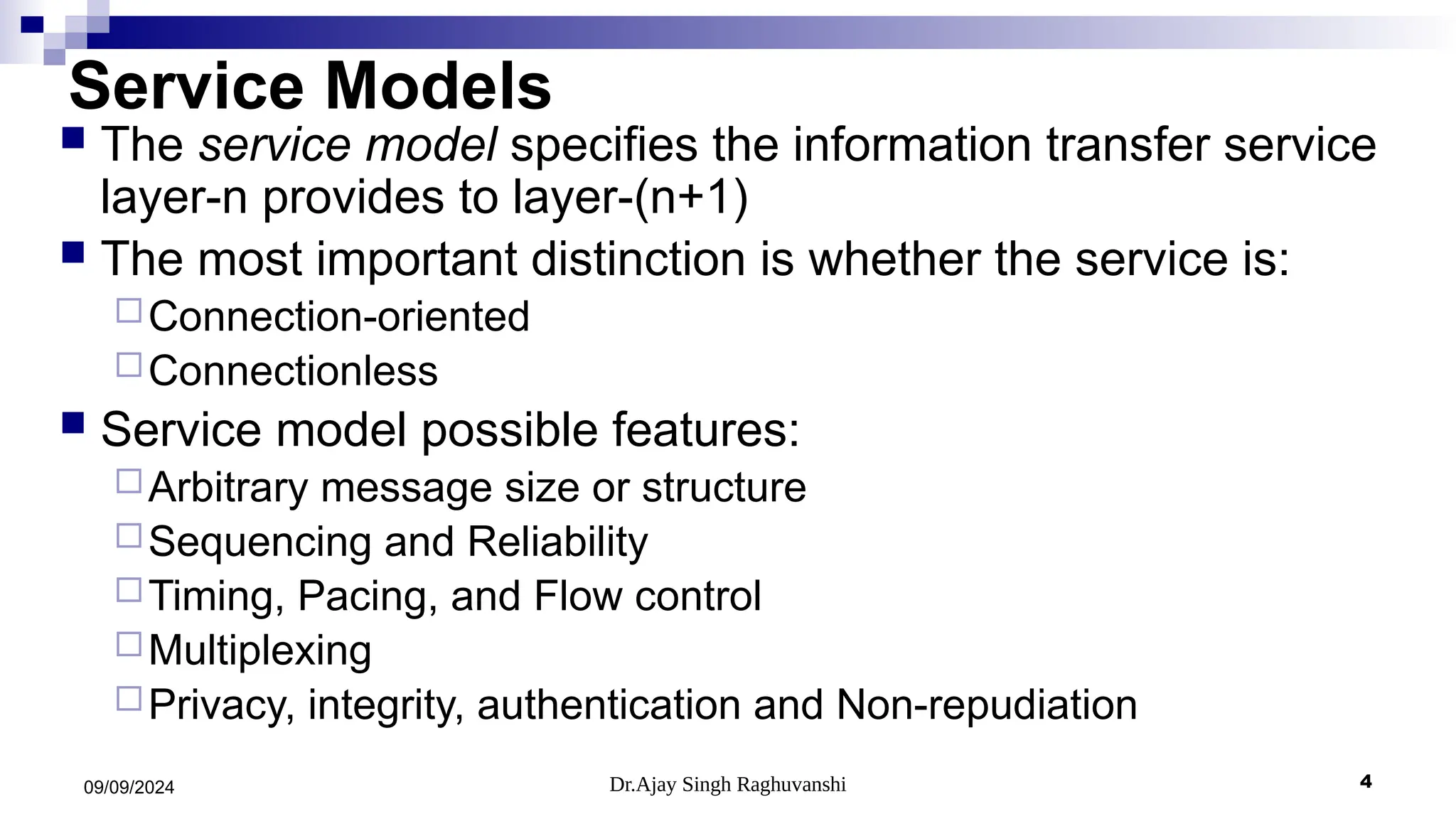
The document provides a comprehensive overview of peer-to-peer protocols, detailing the seven layers of networking from the application layer down to the physical layer. It discusses various service models, including connection-oriented and connectionless services, and covers concepts such as message size, reliability, flow control, timing, multiplexing, and security features like privacy and authentication. Key examples of protocols related to these concepts include TCP for connection-oriented services and UDP for connectionless services.