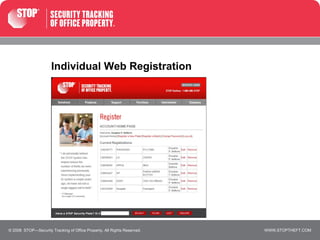
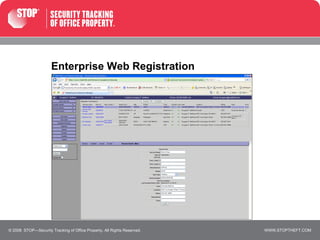
The document discusses STOP, a security system that protects electronic devices from theft on college campuses. STOP assigns unique ID numbers to devices and includes warning messages and a toll-free number to call for device verification. Various college departments and services use STOP to register thousands of devices, resulting in much lower theft rates compared to schools without STOP. The system aims to eliminate the resale value of stolen goods and facilitate their prompt return if recovered.