Building High-Performing Teams: A Leadership Brief for ISSA Colorado Springs
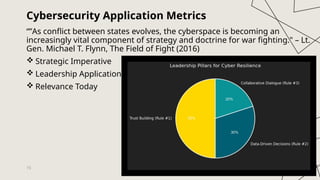
This leadership class was developed for the Colorado Springs chapter of the Information Systems Security Association (ISSA®), a global nonprofit organization dedicated to advancing the professional growth of cybersecurity practitioners. The session focused on cultivating high-performing teams by strengthening three foundational pillars: accountability, transparency, and mutual respect.
Designed specifically for information security professionals, the class explored practical strategies for:
Establishing clear expectations and ownership across roles
Promoting open communication and trust within technical teams
Fostering a culture of respect that drives collaboration and innovation
By aligning leadership principles with the unique demands of cybersecurity environments, this brief empowers ISSA members to lead with clarity, integrity, and impact.