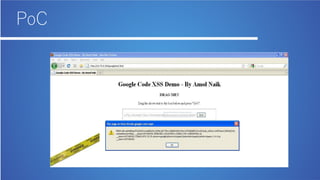
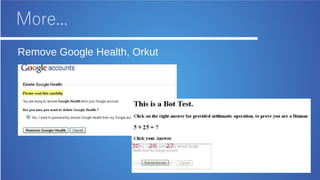
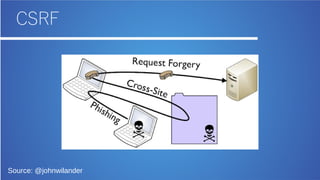
The document discusses bug bounty hunting and provides suggestions for finding bugs. It introduces the author and their background in security. It encourages participants in bug bounty programs to look beyond XSS and use manual testing to find bugs like clickjacking. Resources listed include active bug bounty program lists and tools like Firefox to aid the process. The overall message is having a dream and asking questions to continue learning about security.