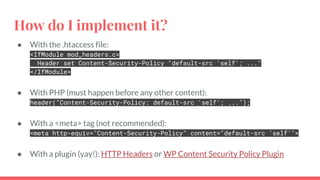
Content Security Policy (CSP) is a computer security standard designed to prevent code injection attacks by allowing website owners to define approved content sources through HTTP headers. It includes directives that dictate security rules for various resource types and enables whitelisting of trusted sources. While it adds a layer of security, implementing CSP may result in website functionality issues, making it particularly beneficial for high-risk organizations.

![What is it?
“Content Security Policy (CSP) is a computer security standard introduced to prevent
cross-site scripting (XSS), clickjacking and other code injection attacks resulting from
execution of malicious content in the trusted web page context. [...] CSP provides a
standard method for website owners to declare approved origins of content that browsers
should be allowed to load on that website—covered types are JavaScript, CSS, HTML
frames, web workers, fonts, images, embeddable objects such as Java applets, ActiveX,
audio and video files, and other HTML5 features.”
- https://en.wikipedia.org/wiki/Content_Security_Policy](https://image.slidesharecdn.com/contentsecuritypolicy-171117185428/85/Content-Security-Policy-2-320.jpg)