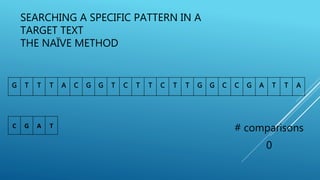
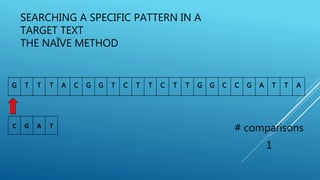
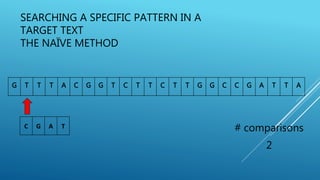
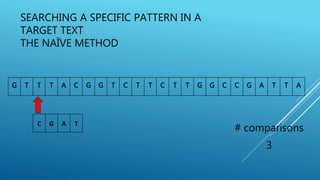
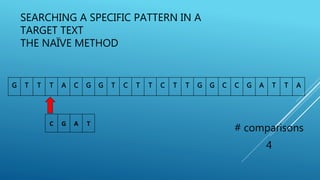
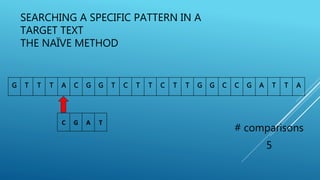
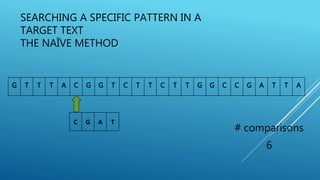
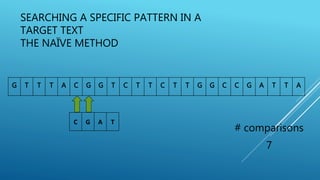
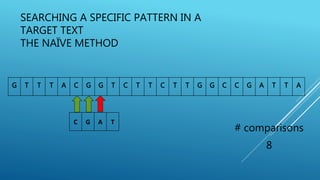
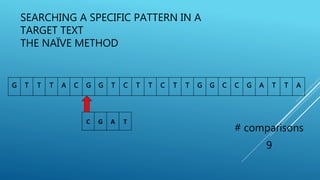
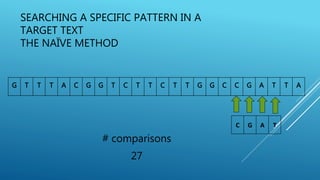
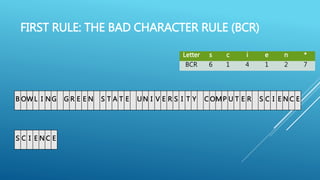
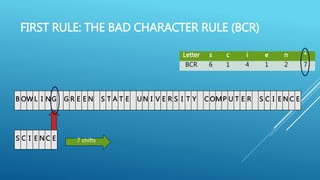
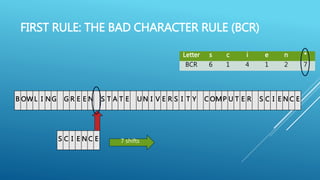
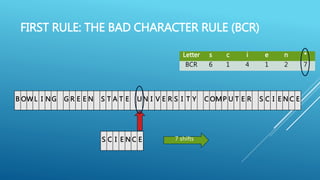
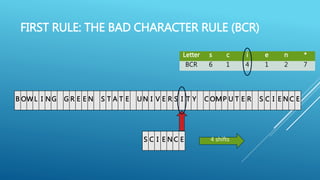
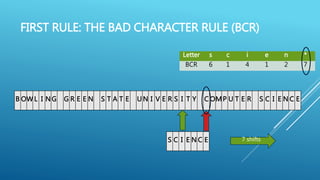
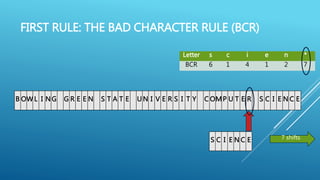
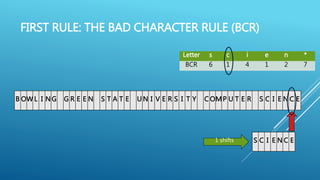
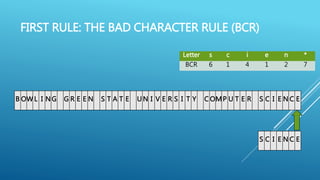
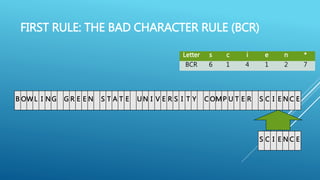
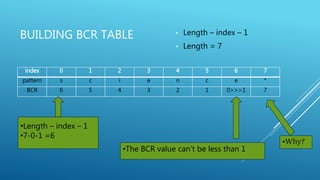
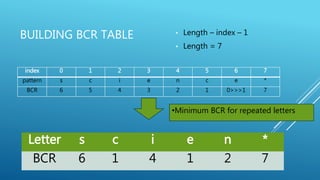
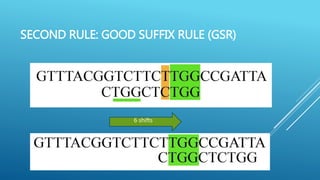
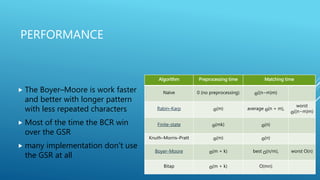
The document describes the Boyer-Moore string search algorithm, which improves on the naive string matching algorithm. It uses two rules - the bad character rule and good suffix rule - to skip unnecessary character comparisons, making string searches more efficient. The bad character rule uses a table to determine how far to shift the pattern when a mismatch occurs, while the good suffix rule allows reusing matches when they are found. Together these rules allow Boyer-Moore to significantly outperform the naive algorithm.






![REFRENCES
[1] Robert S. Boyer and J. Strother Moore. 1977. A fast string searching
algorithm. Commun. ACM 20, 10 (October 1977), 762-772.
DOI=http://dx.doi.org/10.1145/359842.359859
[2] Wikipedia contributors, "Boyer–Moore string search algorithm," Wikipedia,
The Free Encyclopedia,
https://en.wikipedia.org/w/index.php?title=Boyer%E2%80%93Moore_string_sear
ch_algorithm&oldid=688111014 (accessed November 20, 2015).](https://image.slidesharecdn.com/boyer-moore-151218204112/85/Boyer-Moore-string-search-algorithm-33-320.jpg)