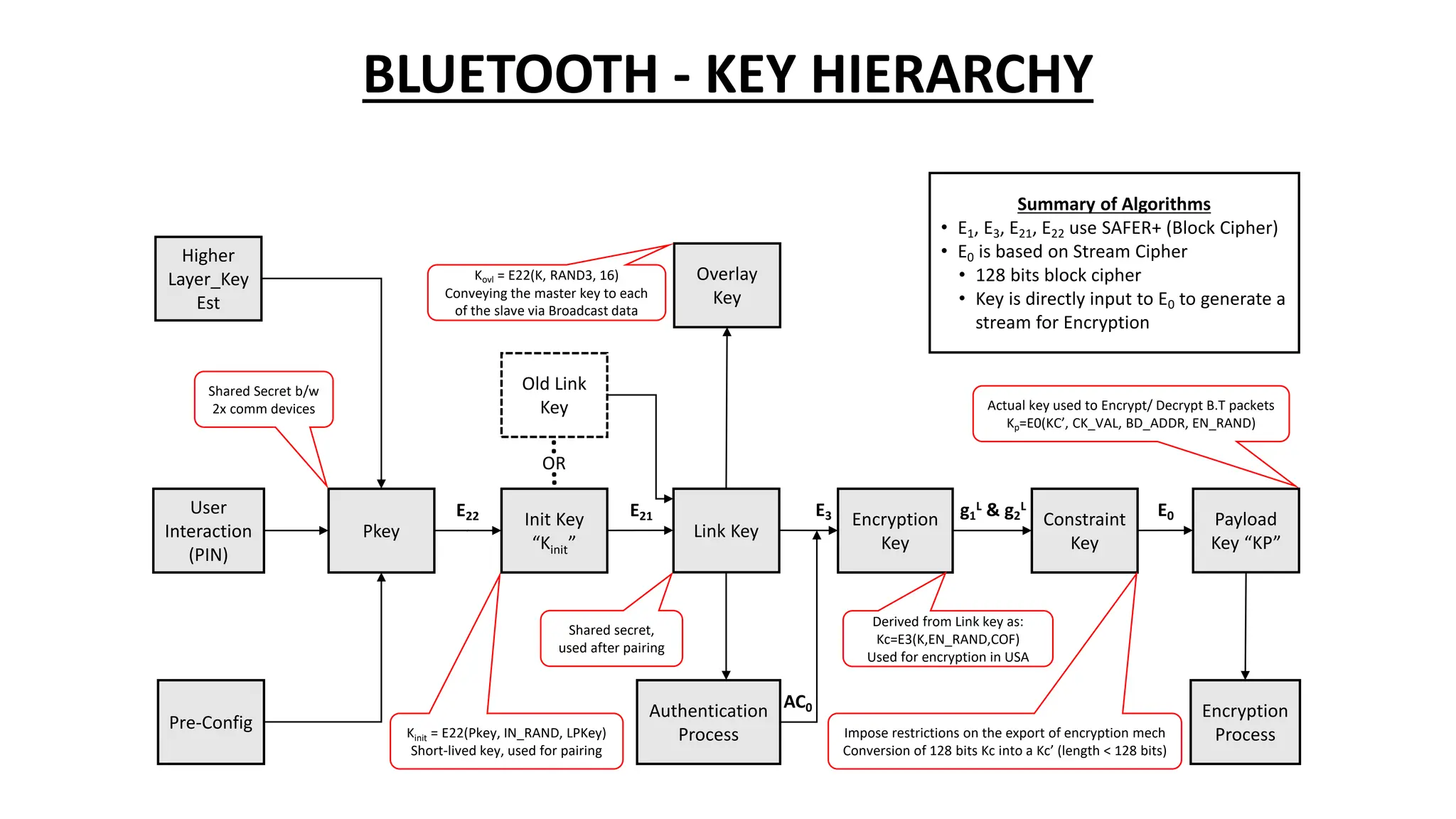
The document discusses cryptographic processes related to key generation and encryption in Bluetooth communication, highlighting key concepts such as link keys, master/slave relationships, and the constraints on encryption mechanisms. It outlines various algorithms utilized in encryption, including block and stream ciphers, and the transformations of key lengths. Specific operations like kinit and kc derive key values for secure pairing and communication between devices.