Report
Share
Download to read offline
Recommended
Небезопасность сотовых сетей вчера, сегодня, завтра

Ведущие: Кирилл Пузанков, Сергей Машуков, Павел Новиков
Взлом в прямом эфире: как хакеры проникают в ваши системы

Инциденты информационной безопасности в последнее время подчеркнуто демонстрируют, что IT-системы даже в международных высокотехнологичных компаниях и крупных государственных учреждениях не имеют достаточной защиты. Широко распространенных мер тестирования IT может быть достаточно для защиты 99% систем. Однако решающим фактором является то, что оставшийся один процент остается целью цифровых атак. Любой лазейки, какой бы незначительной она ни была, достаточно для того, чтобы хорошо защищенная по всем остальным параметрам IT-инфраструктура оказалась уязвимой в целом. Во время презентации докладчик проведет различные атаки на IT-системы. Он покажет, как невероятно просто можно обойти защитные меры для получения доступа к конфиденциальной информации.
Considerations for a secure enterprise wlan data connectors 2013

Considerations for a Secure Enterprise WLAN - DataConnectors 2013 by Kaustubh Phanse
Recommended
Небезопасность сотовых сетей вчера, сегодня, завтра

Ведущие: Кирилл Пузанков, Сергей Машуков, Павел Новиков
Взлом в прямом эфире: как хакеры проникают в ваши системы

Инциденты информационной безопасности в последнее время подчеркнуто демонстрируют, что IT-системы даже в международных высокотехнологичных компаниях и крупных государственных учреждениях не имеют достаточной защиты. Широко распространенных мер тестирования IT может быть достаточно для защиты 99% систем. Однако решающим фактором является то, что оставшийся один процент остается целью цифровых атак. Любой лазейки, какой бы незначительной она ни была, достаточно для того, чтобы хорошо защищенная по всем остальным параметрам IT-инфраструктура оказалась уязвимой в целом. Во время презентации докладчик проведет различные атаки на IT-системы. Он покажет, как невероятно просто можно обойти защитные меры для получения доступа к конфиденциальной информации.
Considerations for a secure enterprise wlan data connectors 2013

Considerations for a Secure Enterprise WLAN - DataConnectors 2013 by Kaustubh Phanse
Introduction to Security Fabric

Networks are becoming ever more complex, making it difficult to manage and secure, especially if you want to implement a segmented network strategy, which we recommend. The answer is to simplify. Fortinet weaves together security solutions designed to be a fully integrated and collaborative Security Fabric to provide the best protection from end-to-end, from IoT to the cloud.
As Fortinet’s first ever Partner of Excellence UK, Infosec Partners' can help you expertly tailor the Fortinet Security Fabric to fit your organisation perfectly.
4 Easy Steps for Increased Industrial Cybersecurity

This presentation by Westermo’s Technical Lead Engineers Dakota Diehl and Benjamin Campbell, is an integral part of the Westermo webinar on February 27th 2020, covering 4 easy steps for increased cybersecurity protecting your critical industrial assets. https://www.westermo.com/news-and-events/webinars/4-easy-steps-for-increased-cybersecurity
The webinar, including this presentation, aimed to teach attendees how to improve their security posture and defend against cyber threats at the network edge.
Bridging the air gap

A presentation I gave to the International Society of Automation Ireland Section on how relying on air gaps to protect ICS and secure networks is a fallacy. This talk highlights actual incidents resulting from the air gap failing and systems being compromised
Fortinet security fabric

Dans le cadre de la 8ème edition des Cyber Security Days 2018, organisée par l'agence nationale de la sécurité informatique, notre partenaire Fortinet-Exclusive Networks a présenté son module "Fortinet Security Fabric".
Wi fi

Its about the small basic of Wi -Fi .How the wifi acess its access point and what is wifi , component of wifi, security and its application........etc
pls sahre ur experience with me n give feedback
Trusted Wireless Environment (TWE)

Wi-Fi hacking leads to stolen passwords, email, social accounts, malware, and identity theft. The worst part is that 20 year old attacks still work today and nearly no one has the technology to detect Wi-Fi hacks making hotspots and office Wi-Fi easy targets for cybercriminals. Food, medicine, even toothpaste has minimum safety standards but Wi-Fi has nothing. The Trusted Wireless Environment (TWE) Framework is the industry's first safety standard for Wi-Fi explaining the six Wi-Fi threats that a WLAN network needs to be protected from to meet the TWE standards.
Network Security - Fortinet, Dublin June 2017

Ransomware and an introduction to Fortinet Security Fabric presentation from Novosco event in Dublin June 2017.
Cisco Live Cancun Collaboration Press

Cisco Live Cancun Collaboration Press, Pedro Suarez, Collaboration lead Latam
how does bluetooth work?

ever wanted to know the in's and out's of bluetooth? well if you did you are in the right place; in this article we will discuss what bluetooth is, how does it work? and where is it used? hope you enjoy!
More Related Content
What's hot
Introduction to Security Fabric

Networks are becoming ever more complex, making it difficult to manage and secure, especially if you want to implement a segmented network strategy, which we recommend. The answer is to simplify. Fortinet weaves together security solutions designed to be a fully integrated and collaborative Security Fabric to provide the best protection from end-to-end, from IoT to the cloud.
As Fortinet’s first ever Partner of Excellence UK, Infosec Partners' can help you expertly tailor the Fortinet Security Fabric to fit your organisation perfectly.
4 Easy Steps for Increased Industrial Cybersecurity

This presentation by Westermo’s Technical Lead Engineers Dakota Diehl and Benjamin Campbell, is an integral part of the Westermo webinar on February 27th 2020, covering 4 easy steps for increased cybersecurity protecting your critical industrial assets. https://www.westermo.com/news-and-events/webinars/4-easy-steps-for-increased-cybersecurity
The webinar, including this presentation, aimed to teach attendees how to improve their security posture and defend against cyber threats at the network edge.
Bridging the air gap

A presentation I gave to the International Society of Automation Ireland Section on how relying on air gaps to protect ICS and secure networks is a fallacy. This talk highlights actual incidents resulting from the air gap failing and systems being compromised
Fortinet security fabric

Dans le cadre de la 8ème edition des Cyber Security Days 2018, organisée par l'agence nationale de la sécurité informatique, notre partenaire Fortinet-Exclusive Networks a présenté son module "Fortinet Security Fabric".
Wi fi

Its about the small basic of Wi -Fi .How the wifi acess its access point and what is wifi , component of wifi, security and its application........etc
pls sahre ur experience with me n give feedback
Trusted Wireless Environment (TWE)

Wi-Fi hacking leads to stolen passwords, email, social accounts, malware, and identity theft. The worst part is that 20 year old attacks still work today and nearly no one has the technology to detect Wi-Fi hacks making hotspots and office Wi-Fi easy targets for cybercriminals. Food, medicine, even toothpaste has minimum safety standards but Wi-Fi has nothing. The Trusted Wireless Environment (TWE) Framework is the industry's first safety standard for Wi-Fi explaining the six Wi-Fi threats that a WLAN network needs to be protected from to meet the TWE standards.
Network Security - Fortinet, Dublin June 2017

Ransomware and an introduction to Fortinet Security Fabric presentation from Novosco event in Dublin June 2017.
Cisco Live Cancun Collaboration Press

Cisco Live Cancun Collaboration Press, Pedro Suarez, Collaboration lead Latam
how does bluetooth work?

ever wanted to know the in's and out's of bluetooth? well if you did you are in the right place; in this article we will discuss what bluetooth is, how does it work? and where is it used? hope you enjoy!
What's hot (19)
4 Easy Steps for Increased Industrial Cybersecurity

4 Easy Steps for Increased Industrial Cybersecurity
Similar to Benefits of VPN For Businesses
Telus - Network as a service

TELUS’ Network-as-as-Service (previously known as TELUS Smart Networks) a new set of services that is built on Software Defined WAN (SD-WAN) and Network Function Virtualization (NFV) technologies. When combined with process automation it transforms the way TELUS offers and provides services. NaaS is composed of three broad categories: network connectivity, on-premises capabilities such as Wi-Fi, and cloud-based value added services.
Sangfor EasyConnect Brochure 2015 (Full)

As cloud computing and mobile devices continue to reshape the way people work, workforces are becoming increasingly mobile. In order to remain competitive, remote workers need a way to access business resources from any device they own, at any time or place.
To address this new technical challenge Sangfor created EasyConnect, a fast, simple, and secure way to access business applications and files. EasyConnect securely delivers virtual applications from your server, private cloud, or public cloud to any endpoint device.
Safely run Microsoft Office, Quickbooks, AutoCAD, or your own legacy applications from a personal PC, tablet, or smartphone in real-time.
Hosted security

Eliminate the need to buy and manage premise-based, security devices and applicances and let XO Communications security experts monitor and manage the authorized use of your security policies.
Service Catalog

We are an end-to-end solution provider for IT & Telecommunications. A business dedicated to your business.
What is VPN?

Virtual Private Network (VPN) is a secure network connection over the private network to a public network or service provider, such as the Internet are creating owned, is the network technology.
NVIS-Pitch Deck version 6 - 2022 MAR.pdf

Hackers can't hack what they can't see. Our invisibility cloak represents a whole new paradigm to infrastructure protection beyond Zero Trust by taking remote communications "off the grid" while preserving the existing infrastructure and development investments. NVIS is military-grade security built by the team that created a best-in-class unhackable solution approved for DoD-wide use and for Coalition forces. NVIS is revolutionary in the security and privacy space to benefit B2B or B2G greatly, especially in the global threat climate.
Remote Access Security

This is a presentation that I recently gave at the VA SCAN 2011 conference on remote access security.
Cost effective authentic and anonymous data sharing with forward security

Cost effective authentic and anonymous data sharing with forward security
Do Your Projects With Technology Experts
To Get this projects Call : 9566355386 / 99625 88976
Visit : www.lemenizinfotech.com / www.ieeemaster.com
Mail : projects@lemenizinfotech.com
Similar to Benefits of VPN For Businesses (20)
Cost effective authentic and anonymous data sharing with forward security

Cost effective authentic and anonymous data sharing with forward security
More from Centextech
More from Centextech (20)
Data Modeling Practices for Effective Database Design

Data Modeling Practices for Effective Database Design
Security at the Core: Unraveling Secure by Design Principles

Security at the Core: Unraveling Secure by Design Principles
Cybersecurity Incident Management for Small and Medium-sized Businesses

Cybersecurity Incident Management for Small and Medium-sized Businesses
Mobile Application Security: Safeguarding Apps in the Digital Age

Mobile Application Security: Safeguarding Apps in the Digital Age
Incident Management for Ransomware Attacks Best Practices for Response and Re...

Incident Management for Ransomware Attacks Best Practices for Response and Re...
10 Essentials Of Effective Cyber Security Strategy

10 Essentials Of Effective Cyber Security Strategy
Recently uploaded
How to Use Contact Form 7 Like a Pro.pptx

Contact Form 7 is a popular plugins for WordPress. This is an introduction into its features and usage.
一比一原版(SLU毕业证)圣路易斯大学毕业证成绩单专业办理

SLU毕业证原版定制【微信:176555708】【圣路易斯大学毕业证成绩单-学位证】【微信:176555708】(留信学历认证永久存档查询)采用学校原版纸张、特殊工艺完全按照原版一比一制作(包括:隐形水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠,文字图案浮雕,激光镭射,紫外荧光,温感,复印防伪)行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备,十五年致力于帮助留学生解决难题,业务范围有加拿大、英国、澳洲、韩国、美国、新加坡,新西兰等学历材料,包您满意。
◆◆◆◆◆ — — — — — — — — 【留学教育】留学归国服务中心 — — — — — -◆◆◆◆◆
【主营项目】
一.毕业证【微信:176555708】成绩单、使馆认证、教育部认证、雅思托福成绩单、学生卡等!
二.真实使馆公证(即留学回国人员证明,不成功不收费)
三.真实教育部学历学位认证(教育部存档!教育部留服网站永久可查)
四.办理各国各大学文凭(一对一专业服务,可全程监控跟踪进度)
如果您处于以下几种情况:
◇在校期间,因各种原因未能顺利毕业……拿不到官方毕业证【微信:176555708】
◇面对父母的压力,希望尽快拿到;
◇不清楚认证流程以及材料该如何准备;
◇回国时间很长,忘记办理;
◇回国马上就要找工作,办给用人单位看;
◇企事业单位必须要求办理的
◇需要报考公务员、购买免税车、落转户口
◇申请留学生创业基金
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分→ 【关于价格问题(保证一手价格)
我们所定的价格是非常合理的,而且我们现在做得单子大多数都是代理和回头客户介绍的所以一般现在有新的单子 我给客户的都是第一手的代理价格,因为我想坦诚对待大家 不想跟大家在价格方面浪费时间
对于老客户或者被老客户介绍过来的朋友,我们都会适当给一些优惠。
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
选择实体注册公司办理,更放心,更安全!我们的承诺:可来公司面谈,可签订合同,会陪同客户一起到教育部认证窗口递交认证材料,客户在教育部官方认证查询网站查询到认证通过结果后付款,不成功不收费!
学历顾问:微信:176555708
原版仿制(uob毕业证书)英国伯明翰大学毕业证本科学历证书原版一模一样

原版纸张【微信:741003700 】【(uob毕业证书)英国伯明翰大学毕业证】【微信:741003700 】学位证,留信认证(真实可查,永久存档)offer、雅思、外壳等材料/诚信可靠,可直接看成品样本,帮您解决无法毕业带来的各种难题!外壳,原版制作,诚信可靠,可直接看成品样本。行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备。十五年致力于帮助留学生解决难题,包您满意。
本公司拥有海外各大学样板无数,能完美还原海外各大学 Bachelor Diploma degree, Master Degree Diploma
1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。材料咨询办理、认证咨询办理请加学历顾问Q/微741003700
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
APNIC Foundation, presented by Ellisha Heppner at the PNG DNS Forum 2024

Ellisha Heppner, Grant Management Lead, presented an update on APNIC Foundation to the PNG DNS Forum held from 6 to 10 May, 2024 in Port Moresby, Papua New Guinea.
test test test test testtest test testtest test testtest test testtest test ...

salamsasalamlamsalamsalamsalamsalamsalamsalamsalam
1.Wireless Communication System_Wireless communication is a broad term that i...

Wireless communication involves the transmission of information over a distance without the help of wires, cables or any other forms of electrical conductors.
Wireless communication is a broad term that incorporates all procedures and forms of connecting and communicating between two or more devices using a wireless signal through wireless communication technologies and devices.
Features of Wireless Communication
The evolution of wireless technology has brought many advancements with its effective features.
The transmitted distance can be anywhere between a few meters (for example, a television's remote control) and thousands of kilometers (for example, radio communication).
Wireless communication can be used for cellular telephony, wireless access to the internet, wireless home networking, and so on.
Multi-cluster Kubernetes Networking- Patterns, Projects and Guidelines

Talk presented at Kubernetes Community Day, New York, May 2024.
Technical summary of Multi-Cluster Kubernetes Networking architectures with focus on 4 key topics.
1) Key patterns for Multi-cluster architectures
2) Architectural comparison of several OSS/ CNCF projects to address these patterns
3) Evolution trends for the APIs of these projects
4) Some design recommendations & guidelines for adopting/ deploying these solutions.
一比一原版(LBS毕业证)伦敦商学院毕业证成绩单专业办理

LBS毕业证原版定制【微信:176555708】【伦敦商学院毕业证成绩单-学位证】【微信:176555708】(留信学历认证永久存档查询)采用学校原版纸张、特殊工艺完全按照原版一比一制作(包括:隐形水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠,文字图案浮雕,激光镭射,紫外荧光,温感,复印防伪)行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备,十五年致力于帮助留学生解决难题,业务范围有加拿大、英国、澳洲、韩国、美国、新加坡,新西兰等学历材料,包您满意。
◆◆◆◆◆ — — — — — — — — 【留学教育】留学归国服务中心 — — — — — -◆◆◆◆◆
【主营项目】
一.毕业证【微信:176555708】成绩单、使馆认证、教育部认证、雅思托福成绩单、学生卡等!
二.真实使馆公证(即留学回国人员证明,不成功不收费)
三.真实教育部学历学位认证(教育部存档!教育部留服网站永久可查)
四.办理各国各大学文凭(一对一专业服务,可全程监控跟踪进度)
如果您处于以下几种情况:
◇在校期间,因各种原因未能顺利毕业……拿不到官方毕业证【微信:176555708】
◇面对父母的压力,希望尽快拿到;
◇不清楚认证流程以及材料该如何准备;
◇回国时间很长,忘记办理;
◇回国马上就要找工作,办给用人单位看;
◇企事业单位必须要求办理的
◇需要报考公务员、购买免税车、落转户口
◇申请留学生创业基金
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分→ 【关于价格问题(保证一手价格)
我们所定的价格是非常合理的,而且我们现在做得单子大多数都是代理和回头客户介绍的所以一般现在有新的单子 我给客户的都是第一手的代理价格,因为我想坦诚对待大家 不想跟大家在价格方面浪费时间
对于老客户或者被老客户介绍过来的朋友,我们都会适当给一些优惠。
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
选择实体注册公司办理,更放心,更安全!我们的承诺:可来公司面谈,可签订合同,会陪同客户一起到教育部认证窗口递交认证材料,客户在教育部官方认证查询网站查询到认证通过结果后付款,不成功不收费!
学历顾问:微信:176555708
This 7-second Brain Wave Ritual Attracts Money To You.!

Discover the power of a simple 7-second brain wave ritual that can attract wealth and abundance into your life. By tapping into specific brain frequencies, this technique helps you manifest financial success effortlessly. Ready to transform your financial future? Try this powerful ritual and start attracting money today!
The+Prospects+of+E-Commerce+in+China.pptx

The Prospects of E-commerce in China,www.cfye-commerce.shop
Bridging the Digital Gap Brad Spiegel Macon, GA Initiative.pptx

Brad Spiegel Macon GA’s journey exemplifies the profound impact that one individual can have on their community. Through his unwavering dedication to digital inclusion, he’s not only bridging the gap in Macon but also setting an example for others to follow.
一比一原版(CSU毕业证)加利福尼亚州立大学毕业证成绩单专业办理

CSU毕业证原版定制【微信:176555708】【加利福尼亚州立大学毕业证成绩单-学位证】【微信:176555708】(留信学历认证永久存档查询)采用学校原版纸张、特殊工艺完全按照原版一比一制作(包括:隐形水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠,文字图案浮雕,激光镭射,紫外荧光,温感,复印防伪)行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备,十五年致力于帮助留学生解决难题,业务范围有加拿大、英国、澳洲、韩国、美国、新加坡,新西兰等学历材料,包您满意。
◆◆◆◆◆ — — — — — — — — 【留学教育】留学归国服务中心 — — — — — -◆◆◆◆◆
【主营项目】
一.毕业证【微信:176555708】成绩单、使馆认证、教育部认证、雅思托福成绩单、学生卡等!
二.真实使馆公证(即留学回国人员证明,不成功不收费)
三.真实教育部学历学位认证(教育部存档!教育部留服网站永久可查)
四.办理各国各大学文凭(一对一专业服务,可全程监控跟踪进度)
如果您处于以下几种情况:
◇在校期间,因各种原因未能顺利毕业……拿不到官方毕业证【微信:176555708】
◇面对父母的压力,希望尽快拿到;
◇不清楚认证流程以及材料该如何准备;
◇回国时间很长,忘记办理;
◇回国马上就要找工作,办给用人单位看;
◇企事业单位必须要求办理的
◇需要报考公务员、购买免税车、落转户口
◇申请留学生创业基金
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分→ 【关于价格问题(保证一手价格)
我们所定的价格是非常合理的,而且我们现在做得单子大多数都是代理和回头客户介绍的所以一般现在有新的单子 我给客户的都是第一手的代理价格,因为我想坦诚对待大家 不想跟大家在价格方面浪费时间
对于老客户或者被老客户介绍过来的朋友,我们都会适当给一些优惠。
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
选择实体注册公司办理,更放心,更安全!我们的承诺:可来公司面谈,可签订合同,会陪同客户一起到教育部认证窗口递交认证材料,客户在教育部官方认证查询网站查询到认证通过结果后付款,不成功不收费!
学历顾问:微信:176555708
1比1复刻(bath毕业证书)英国巴斯大学毕业证学位证原版一模一样

原版纸张【微信:741003700 】【(bath毕业证书)英国巴斯大学毕业证学位证】【微信:741003700 】学位证,留信认证(真实可查,永久存档)offer、雅思、外壳等材料/诚信可靠,可直接看成品样本,帮您解决无法毕业带来的各种难题!外壳,原版制作,诚信可靠,可直接看成品样本。行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备。十五年致力于帮助留学生解决难题,包您满意。
本公司拥有海外各大学样板无数,能完美还原海外各大学 Bachelor Diploma degree, Master Degree Diploma
1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。材料咨询办理、认证咨询办理请加学历顾问Q/微741003700
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
History+of+E-commerce+Development+in+China-www.cfye-commerce.shop

History+of+E-commerce+Development+in+China-www.cfye-commerce.shop
Internet-Security-Safeguarding-Your-Digital-World (1).pptx

# Internet Security: Safeguarding Your Digital World
In the contemporary digital age, the internet is a cornerstone of our daily lives. It connects us to vast amounts of information, provides platforms for communication, enables commerce, and offers endless entertainment. However, with these conveniences come significant security challenges. Internet security is essential to protect our digital identities, sensitive data, and overall online experience. This comprehensive guide explores the multifaceted world of internet security, providing insights into its importance, common threats, and effective strategies to safeguard your digital world.
## Understanding Internet Security
Internet security encompasses the measures and protocols used to protect information, devices, and networks from unauthorized access, attacks, and damage. It involves a wide range of practices designed to safeguard data confidentiality, integrity, and availability. Effective internet security is crucial for individuals, businesses, and governments alike, as cyber threats continue to evolve in complexity and scale.
### Key Components of Internet Security
1. **Confidentiality**: Ensuring that information is accessible only to those authorized to access it.
2. **Integrity**: Protecting information from being altered or tampered with by unauthorized parties.
3. **Availability**: Ensuring that authorized users have reliable access to information and resources when needed.
## Common Internet Security Threats
Cyber threats are numerous and constantly evolving. Understanding these threats is the first step in protecting against them. Some of the most common internet security threats include:
### Malware
Malware, or malicious software, is designed to harm, exploit, or otherwise compromise a device, network, or service. Common types of malware include:
- **Viruses**: Programs that attach themselves to legitimate software and replicate, spreading to other programs and files.
- **Worms**: Standalone malware that replicates itself to spread to other computers.
- **Trojan Horses**: Malicious software disguised as legitimate software.
- **Ransomware**: Malware that encrypts a user's files and demands a ransom for the decryption key.
- **Spyware**: Software that secretly monitors and collects user information.
### Phishing
Phishing is a social engineering attack that aims to steal sensitive information such as usernames, passwords, and credit card details. Attackers often masquerade as trusted entities in email or other communication channels, tricking victims into providing their information.
### Man-in-the-Middle (MitM) Attacks
MitM attacks occur when an attacker intercepts and potentially alters communication between two parties without their knowledge. This can lead to the unauthorized acquisition of sensitive information.
### Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks
急速办(bedfordhire毕业证书)英国贝德福特大学毕业证成绩单原版一模一样

原版纸张【微信:741003700 】【(bedfordhire毕业证书)英国贝德福特大学毕业证成绩单】【微信:741003700 】学位证,留信认证(真实可查,永久存档)offer、雅思、外壳等材料/诚信可靠,可直接看成品样本,帮您解决无法毕业带来的各种难题!外壳,原版制作,诚信可靠,可直接看成品样本。行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备。十五年致力于帮助留学生解决难题,包您满意。
本公司拥有海外各大学样板无数,能完美还原海外各大学 Bachelor Diploma degree, Master Degree Diploma
1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。材料咨询办理、认证咨询办理请加学历顾问Q/微741003700
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
Recently uploaded (20)
APNIC Foundation, presented by Ellisha Heppner at the PNG DNS Forum 2024

APNIC Foundation, presented by Ellisha Heppner at the PNG DNS Forum 2024
test test test test testtest test testtest test testtest test testtest test ...

test test test test testtest test testtest test testtest test testtest test ...
guildmasters guide to ravnica Dungeons & Dragons 5...

guildmasters guide to ravnica Dungeons & Dragons 5...
1.Wireless Communication System_Wireless communication is a broad term that i...

1.Wireless Communication System_Wireless communication is a broad term that i...
Multi-cluster Kubernetes Networking- Patterns, Projects and Guidelines

Multi-cluster Kubernetes Networking- Patterns, Projects and Guidelines
This 7-second Brain Wave Ritual Attracts Money To You.!

This 7-second Brain Wave Ritual Attracts Money To You.!
Bridging the Digital Gap Brad Spiegel Macon, GA Initiative.pptx

Bridging the Digital Gap Brad Spiegel Macon, GA Initiative.pptx
History+of+E-commerce+Development+in+China-www.cfye-commerce.shop

History+of+E-commerce+Development+in+China-www.cfye-commerce.shop
Internet-Security-Safeguarding-Your-Digital-World (1).pptx

Internet-Security-Safeguarding-Your-Digital-World (1).pptx
Benefits of VPN For Businesses
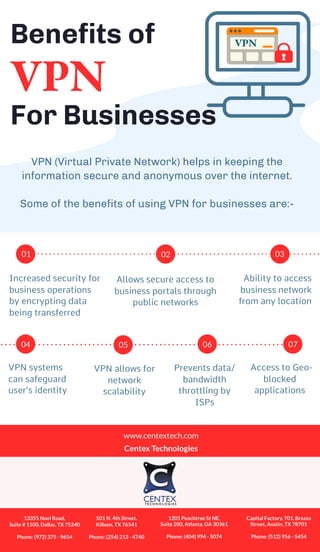
- 1. For Businesses Benefits of VPN VPN (Virtual Private Network) helps in keeping the information secure and anonymous over the internet. Some of the benefits of using VPN for businesses are:- VPN Increased security for business operations by encrypting data being transferred Allows secure access to business portals through public networks Ability to access business network from any location VPN systems can safeguard user’s identity VPN allows for network scalability Prevents data/ bandwidth throttling by ISPs Access to Geo- blocked applications 01 02 03 04 05 06 07 www.centextech.com Centex Technologies 13355 Noel Road, Suite # 1100, Dallas, TX 75240 Phone: (972) 375 - 9654 501 N. 4th Street, Killeen, TX 76541 Phone: (254) 213 - 4740 1201 Peachtree St NE, Suite 200, Atlanta, GA 30361 Phone: (404) 994 - 5074 Capital Factory, 701, Brazos Street, Austin, TX 78701 Phone: (512) 956 - 5454