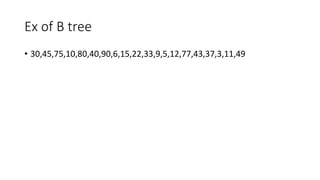
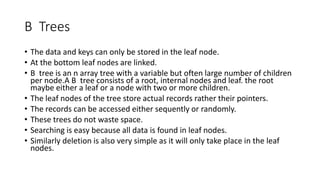
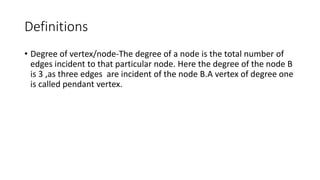
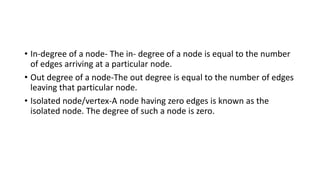
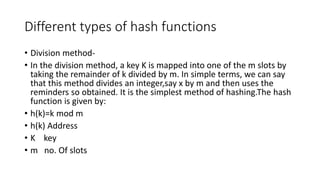
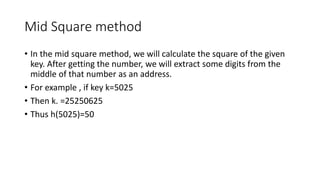
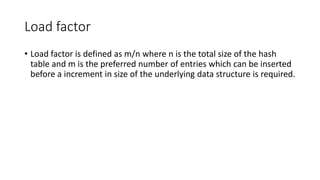
The document discusses various types of trees (m-way search trees, complete binary trees, extended binary trees, perfect binary trees, and B-trees) and their properties, as well as different representations and traversal techniques for graphs (using adjacency matrices and lists), and hashing as a data structure for efficient searching. It outlines characteristics of hash functions and methods for hashing data, including division method, mid-square method, and folding method. Furthermore, the document explains how these concepts interrelate in computer science, particularly in data structures and algorithms.