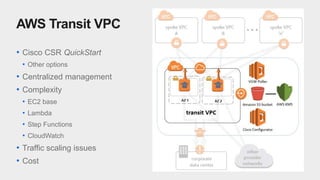
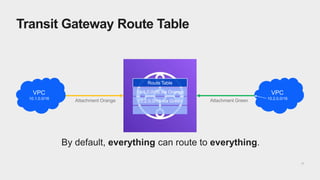
The document discusses AWS Transit Gateway, an advanced networking solution designed for routing between Amazon VPCs and on-premise data centers. It contrasts this solution with traditional options like transit VPCs and VPC peering, while outlining its key concepts, features, and limitations. A case study illustrates a client's migration to Transit Gateway, highlighting connectivity considerations and lessons learned during the transition.