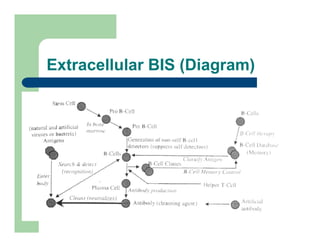
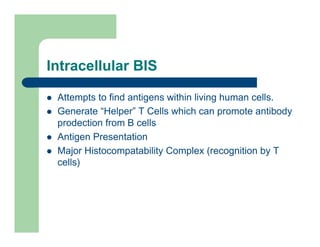
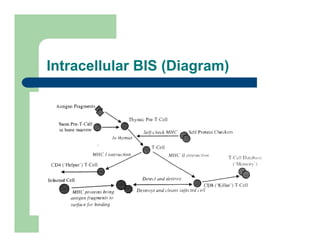
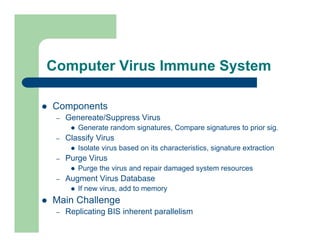
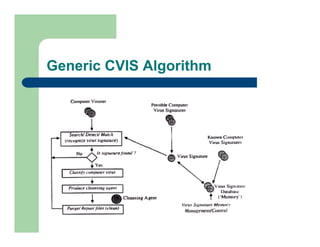
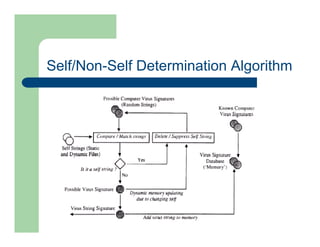
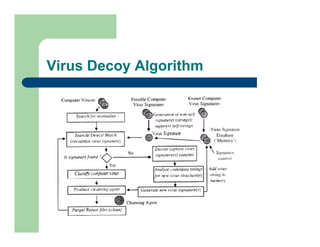
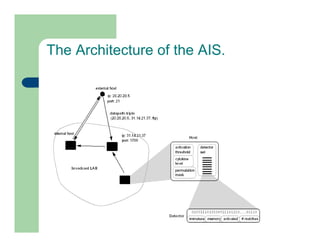
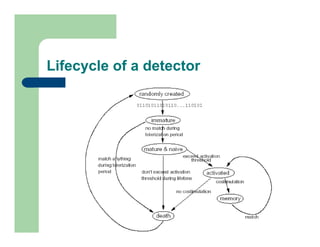
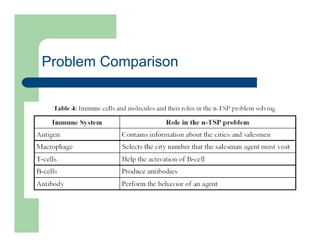
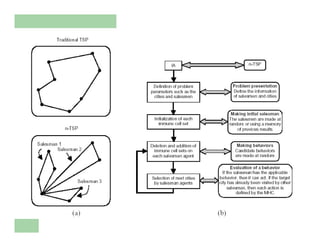
The document discusses various applications of artificial immune systems (AIS) computing, including computer security, pattern recognition, and optimization problems. It then provides more detail on using AIS approaches for computer virus detection. A proposed Computer Virus Immune System (CVIS) would incorporate components modeled after the biological immune system, such as generating/suppressing viruses, classifying viruses, and purging/repairing infected systems. Main challenges include replicating the parallelism of the natural immune system. Several example algorithms are also described.