Randall Degges introduces PASETO (Platform-Agnostic Security Tokens) as an alternative to JWTs. PASETOs address issues with JWT cryptography and misuse by using stronger algorithms and enforcing strict validation. PASETOs can be local and encrypted with a shared key, or public and signed with asymmetric keys. They provide tamper-proof payloads and different types for various use cases. Developers are encouraged to try PASETOs as a more secure token standard.

![@rdegges @oktadev
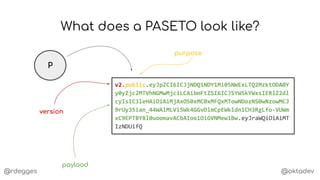
What's PASETO?
P
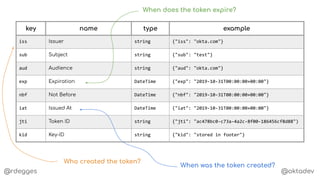
{
"id": "a5db284d-d22c-4a3d-b67e-60776fc24526",
"email": "r@rdegges.com",
"permissions": [
"download:file-a.mp4",
"download:file-b.mp4",
"download:file-c.mp4"
]
}
Randall Degges
PASETOs are always
authenticated.](https://image.slidesharecdn.com/anintroductiontopasetotokens-191023144403/85/An-Introduction-to-PASETO-Tokens-3-320.jpg)


![@rdegges @oktadev
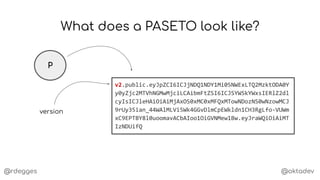
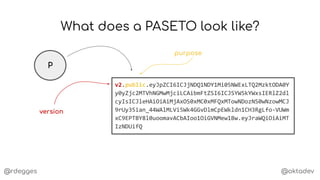
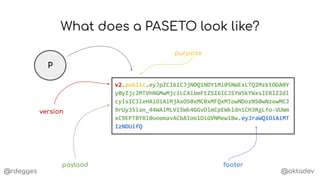
What's inside a PASETO?
P
{
"id": "a5db284d-d22c-4a3d-b67e-60776fc24526",
"email": "r@rdegges.com",
"permissions": [
"download:file-a.mp4",
"download:file-b.mp4",
"download:file-c.mp4"
]
}
claims](https://image.slidesharecdn.com/anintroductiontopasetotokens-191023144403/85/An-Introduction-to-PASETO-Tokens-11-320.jpg)
![@rdegges @oktadev
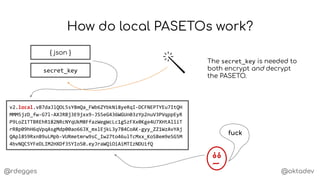
How do I use local PASETOs?
www.
P
secret_key
dl.
{
"purchaseID": "1234567",
"permissions": [
"download:video1.mp4",
"download:video2.mp4",
"download:video3.mp4"
]
}
?token=v2.local.xxx&
file=video1.mp4
- Parse URL params
- Decrypt token
- Verify purchaseID
- Verify permissions
- Stream file to user
video1.mp4
I want to download
video1.mp4.
secret_key
- Validate request
- Generate PASETO
- Redirect](https://image.slidesharecdn.com/anintroductiontopasetotokens-191023144403/85/An-Introduction-to-PASETO-Tokens-15-320.jpg)