Akamai
•
0 likes•168 views
Akamai provides cloud-based web application firewall and DDoS protection solutions for enterprises. Their solutions are easy to deploy, require low maintenance, and receive automatic updates. On-premises WAFs require 3 or more full-time employees to manage, are difficult to manage, introduce latency, produce many alerts, and are vulnerable to DDoS outages. Akamai's cloud-based solutions provide stronger protection, better performance, and freedom from DDoS attacks compared to on-premises alternatives.
Report
Share
Report
Share
Download to read offline
Recommended
Akamai Intelligent Edge Security

This document discusses edge security and Akamai's intelligent edge security platform. It notes that security remains a challenge as the threat landscape and attack surfaces continue to change rapidly. Akamai's edge security platform provides strategic protection around applications, infrastructure, and users by enforcing consistent security policies across its global network. It offers visibility into billions of daily attacks and adapts to protect assets anywhere. The platform includes services like DDoS protection, web application firewall, zero trust network access, and bot management.
Webinar

The document advertises a webinar about F5 Secure Application Services & WAF Administration. It notes that as organizations manage hundreds or thousands of applications that are frequently updated, an app-centric security approach is needed to prevent data breaches and noncompliance. The webinar will discuss how their SAS-WAFA service can help reduce the burden on in-house security teams by taking over basic WAF administration, allowing teams to focus on other priorities without compromising security. Attendees will learn how it can simplify WAF management and speed up deploying new policies.
Kona Site Defender Product Brief - Multi-layered defense to protect websites ...

Kona Site Defender is a security solution from Akamai that protects against DDoS attacks, web application attacks, and direct attacks on origin servers. It leverages Akamai's global network of servers to mitigate attacks close to their source before reaching the customer. The solution includes features like web application firewall, rate controls, IP whitelisting/blacklisting, and origin cloaking to hide customer servers. It provides visibility into security events and defense actions through an advanced security monitor.
3 reasons for online reputation

Website performance monitoring is important for three main reasons:
1. A website is a company's identity and brand reputation, which takes years to build but can be lost in seconds due to downtime or other issues.
2. Downtime, malware, phishing and other factors can damage an organization's online reputation, which may be costly to recover from.
3. Regular monitoring allows issues to be addressed proactively through features like uptime tracking, page speed analysis, blacklist monitoring and alerting, to help maintain efficiency and service quality.
CIS 2015 Identity and Data Security : Breaking the Boundaries - Nathanael Cof...

IAM and the rest of the security stack -- network and applications firewalls, threat and intrusion detection -- are often treated as entirely separate silos. It's time this changed. By orchestrating and integrating these disparate systems, information from the data security tier can inform your IAM processes in real-time, leading to better Authorization decisions and provide user experience improvements. This workshop, informed by and demonstrating real-world examples, will provide insight into the kind of cross-system orchestration that can help make a tangible difference to your security and to usability.
IP-guard Catalog

The document discusses network security threats, both external and internal. It states that internal threats from employees are one of the most common problems, as staff can intentionally or unintentionally steal or modify important company data. It then promotes IP-guard as a solution to secure a company's computer network and protect against data loss. IP-guard is described as a centralized monitoring and management system that gives administrators control and visibility over employee devices and activities on the network.
CMTPS (Cloud-base Multi-engine Threat Prevention System)

1) CMTPS is a cloud-based multi-engine threat prevention system that brings the security of multiple well-known antiviruses to clients' devices with zero impact on performance.
2) Unlike traditional antivirus software, CMTPS does not slow down devices or cause them to malfunction since it operates from the cloud rather than locally.
3) CMTPS prevents threats before infection by scanning at the cloud level, as opposed to traditional antivirus which can only cure infections after the fact.
Top Application Security Threats 

The following slides present an
application security checklist — a look at how your company can counter the
impact of seven top application security threats.
Recommended
Akamai Intelligent Edge Security

This document discusses edge security and Akamai's intelligent edge security platform. It notes that security remains a challenge as the threat landscape and attack surfaces continue to change rapidly. Akamai's edge security platform provides strategic protection around applications, infrastructure, and users by enforcing consistent security policies across its global network. It offers visibility into billions of daily attacks and adapts to protect assets anywhere. The platform includes services like DDoS protection, web application firewall, zero trust network access, and bot management.
Webinar

The document advertises a webinar about F5 Secure Application Services & WAF Administration. It notes that as organizations manage hundreds or thousands of applications that are frequently updated, an app-centric security approach is needed to prevent data breaches and noncompliance. The webinar will discuss how their SAS-WAFA service can help reduce the burden on in-house security teams by taking over basic WAF administration, allowing teams to focus on other priorities without compromising security. Attendees will learn how it can simplify WAF management and speed up deploying new policies.
Kona Site Defender Product Brief - Multi-layered defense to protect websites ...

Kona Site Defender is a security solution from Akamai that protects against DDoS attacks, web application attacks, and direct attacks on origin servers. It leverages Akamai's global network of servers to mitigate attacks close to their source before reaching the customer. The solution includes features like web application firewall, rate controls, IP whitelisting/blacklisting, and origin cloaking to hide customer servers. It provides visibility into security events and defense actions through an advanced security monitor.
3 reasons for online reputation

Website performance monitoring is important for three main reasons:
1. A website is a company's identity and brand reputation, which takes years to build but can be lost in seconds due to downtime or other issues.
2. Downtime, malware, phishing and other factors can damage an organization's online reputation, which may be costly to recover from.
3. Regular monitoring allows issues to be addressed proactively through features like uptime tracking, page speed analysis, blacklist monitoring and alerting, to help maintain efficiency and service quality.
CIS 2015 Identity and Data Security : Breaking the Boundaries - Nathanael Cof...

IAM and the rest of the security stack -- network and applications firewalls, threat and intrusion detection -- are often treated as entirely separate silos. It's time this changed. By orchestrating and integrating these disparate systems, information from the data security tier can inform your IAM processes in real-time, leading to better Authorization decisions and provide user experience improvements. This workshop, informed by and demonstrating real-world examples, will provide insight into the kind of cross-system orchestration that can help make a tangible difference to your security and to usability.
IP-guard Catalog

The document discusses network security threats, both external and internal. It states that internal threats from employees are one of the most common problems, as staff can intentionally or unintentionally steal or modify important company data. It then promotes IP-guard as a solution to secure a company's computer network and protect against data loss. IP-guard is described as a centralized monitoring and management system that gives administrators control and visibility over employee devices and activities on the network.
CMTPS (Cloud-base Multi-engine Threat Prevention System)

1) CMTPS is a cloud-based multi-engine threat prevention system that brings the security of multiple well-known antiviruses to clients' devices with zero impact on performance.
2) Unlike traditional antivirus software, CMTPS does not slow down devices or cause them to malfunction since it operates from the cloud rather than locally.
3) CMTPS prevents threats before infection by scanning at the cloud level, as opposed to traditional antivirus which can only cure infections after the fact.
Top Application Security Threats 

The following slides present an
application security checklist — a look at how your company can counter the
impact of seven top application security threats.
Why you need to secure mobile apps - now

No matter what size of company you’re at, you probably have a work phone. It might not have been given to you by your company, but you use it for work in one way or another. That means there is company data on your phone. Why do companies need a solution that secures the apps rather than the device – so employees can have the freedom and flexibility they need to get their work done.
OSB160: Trust Your Apps. See How with Ivanti Application Control

This document provides an agenda for a presentation on Ivanti Application Control. The presentation covers how Application Control works under the hood to whitelist trusted applications using file ownership. It discusses the challenges of user-targeted attacks and why traditional approaches like blacklisting and antivirus are not enough. Customer success stories are shared where Application Control has prevented malware infections and improved security posture. Tips are provided such as following expert guidance, getting business buy-in, and using discovery tools to understand the existing application estate before deploying controls. A demo of Application Control is planned and time for questions is allotted at the end.
Disaster recovery glossary

This document defines key terms related to disaster recovery including: alerts, backups, continuity availability, disaster recovery, exercises, recovery time objective (RTO), recovery point objective (RPO), shared responsibility model, risk assessment, redundancy, business continuity, application recovery, high availability, remote sites, assets, and alternative work area. It provides brief explanations of each term and its relevance to maintaining operations and recovering from a disaster.
airwatchexpress_infographic(2)

Small and medium-sized businesses face significant internet security threats, with 43% of small businesses and 22% of medium businesses being compromised in 2015. However, AirWatch Express provides a simplified mobile device management system that allows SMBs to protect their organizations from lost or stolen devices by remotely wiping business data while keeping personal information intact, without needing additional software, hardware, or IT expertise.
How to Cut Through the “Fog of More” to Achieve a Solid Security Foundation 

Why do security programs fail? How does a company that passed a recent audit suffer a breach? Is there a silver bullet for securing my environment? It seems there are more questions than answers in cybersecurity today. In this session we'll provide guidance and talk about ways to focus your security strategy to reduce the volume of incidents so you can focus on business initiatives instead.
Cloud Security Myths Vs Facts

The belief that cloud computing is not as secure as on-site servers stems from a number of myths that have been floating around since the first cloud-based solutions were introduced. Some of the most common myths about cloud security are presented on the following slides — along with the facts that dispel these myths.
Web App Sec Roadmap

This document provides a roadmap for web application security. It notes that web application security is still immature, traditional operations teams do not understand the risks, and companies often struggle to assign responsibility for security to one person due to organizational challenges. The document aims to help companies better manage web application security.
Streamline and Secure Your Network and Users

This document discusses the benefits of using Zscaler's cloud-based network and internet security solution over traditional on-premise appliance solutions. It summarizes that Zscaler provides comprehensive security across multiple threat vectors through a single cloud platform. It is more cost effective than appliance solutions and improves performance and user experience while reducing complexity and management overhead. The document also highlights key capabilities of Zscaler such as real-time inspection of all traffic including SSL, global policy management, and unified reporting and administration.
Cloud Computing Risks by Ravi Namboori Cisco Evangelist

Cloud computing is nothing but accessing and using applications and files over the Internet rather than on your own computing devices. Learn what is Cloud computing and what are the risks it facing & conclusions given by Ravi Namboori a Network Architect. He is having 20+years of experience in IT field & Entrepreneurship.
Security in Remote Business 

www.apexlogics.net
Managing a remote business requires clear strategy for communication. This does not only require the strategy and modes of communication to be defined but this process needs to be secure as well.
Stop Attacks and Mitigate Risk with Application and Device Control

Application and device control features in Symantec Endpoint Protection allow organizations to restrict applications and devices used on endpoints, mitigate risks, and prevent attacks. These features whitelist approved applications and devices, blacklist those known to be bad, and block unauthorized access. They also prevent data loss through external storage devices and help enforce corporate security policies and compliance standards.
Are Cloud Apps the Invisible Man?

This document describes IBM's Cloud Security Enforcer, a new SaaS solution that integrates identity and access control, threat prevention, policy enforcement, and discovery/visibility capabilities into a single platform. It consolidates leading IBM security technologies to help organizations securely adopt cloud services. Key features include risk scoring for thousands of apps, continuous monitoring of cloud activity, mapping network data to users, mobile integration, single sign-on, connectors to popular apps, access controls, activity monitoring, behavioral analysis, alerting/reporting, intrusion prevention, and threat protection from IBM X-Force. The solution aims to help customers securely deploy cloud services for their employees.
Introducing IBM Cloud Security Enforcer, CASB, IDaaS and Threat Prevention

View on demand webinar:
https://securityintelligence.com/events/introducing-ibm-cloud-security-enforcer-casb-idaas-and-threat-prevention/
Cloud Security Enforcer is the first solution to combine Cloud Access Security Broker (CASB) functionality with identity services (IDaaS), policy enforcement and dynamic threat prevention intelligence into a single integrated SaaS solution.
Join Daniel Wolff, Program Director Cloud Security Product Management, and Gonzalo de la Hoz, IAM European Segment Leader, as we discuss how IBM Cloud Security Enforcer has integrated multiple technologies crucial to enabling safe adoption of cloud applications in the enterprise:
- Cloud application discovery and risk
- Cloud identity services and application on-boarding
- Closing the mobile device gap
- Policy enforcement and threat prevention
Big Fix Q-Radar Ahmed Sharaf - EmbeddedSecurity.net

IBM Security and Xband can help enterprises remediate vulnerabilities faster. The perimeter is no longer fixed as endpoints are everywhere. Cybercrime is becoming more sophisticated and severe, with 600 million records leaked in 2015. Most breaches are caused by ineffective patch management as 75% of attacks use known vulnerabilities and it takes on average 256 days to detect advanced threats. IBM BigFix can find unmanaged endpoints, fix vulnerabilities across systems, and continuously monitor compliance to help secure organizations. It bridges the gap between security and IT operations for shared visibility and control.
Antivirus management lexington ky

IT safety measures disciplines for a much price reduction, such seeing that antivirus managing, firewall managing, intrusion discovery and deterrence, system setup and managing and exclusive private communities. For more information on click here: http://www.integrityky.com/antivirus-management-with-integrity-it/
Don’t Drown in a Sea of Cyberthreats: Mitigate Attacks with IBM BigFix & QRadar

view on demand: https://securityintelligence.com/events/dont-drown-in-a-sea-of-cyberthreats/
Security teams can be overwhelmed by a sea of vulnerabilities–without the contextual data to help them focus their efforts on the weaknesses that are most likely to be exploited. Cyberthreats need to be stopped before they cause significant financial and reputational damages to an organization. You need a security system that can detect an attack, prioritize risks and respond within minutes to shut down an attack or vulnerability that could compromise your endpoints and data.
Join this webinar and learn how IBM BigFix seamlessly integrates with IBM QRadar to provide accelerated risk prioritization and incident response to mitigate potential attacks giving you an integrated threat protection system to keep your corporate and customer data secure.
Saas security stock company

Cloud SaaS company has high stack revenue. It's reviewed current SaaS company status at the 70% growth. And it found security SaaS company were still need costly.
Security framework shakedown_-_chart_your_journey_with_aws_best_practices_ini...

Security framework shakedown_-_chart_your_journey_with_aws_best_practices_ini...Amazon Web Services LATAM
Security Framework Sakedown apresentado no Initiate Day São Paulo para setor público na Amazon Web ServicesEnabling Cloud Smart, Zero-Trust, and TIC

The document outlines Matt Jordan's presentation on enabling cloud smart, zero-trust networking, and trusted internet connections (TIC) at a public sector summit. It discusses the concepts of cloud smart, focusing on making informed technology decisions aligned with agency missions. Zero-trust networking principles of identity assurance, least privilege access, and auditing are described. Iterating TIC to leverage commercial innovation through collaboration and automated verification is presented, with benefits including efficient deployment, relying on continuous research and development, and multilayered security.
Panda Cloud Services

The document describes Panda Cloud Protection, a SaaS security solution that protects endpoints, email, and web traffic from cyber threats. It works by connecting client systems and traffic in real time to Panda's Collective Intelligence for proactive protection with 15 security modules. Benefits include robust protection, no upfront investment or maintenance costs, automatic updates, and centralized remote management through a web console.
B&W Netsparker overview

The Netsparker Web Application #Security #Scanners employ a unique and dead-accurate vulnerability scanning technology that automatically verify the vulnerabilities by producing a proof of exploit.
Discover how Netsparker find security flaws in websites, applications and services and protect whole system in 3 clicks.
Softprom by ERC official Value added #distributor of #Netsparker in Europe.
Top 10 Azure Security Best Practices (1).pptx

Attack services like ransomware, zero-days, exploit kits, and denial of service can be purchased at relatively low prices online. Ransomware costs $66 upfront or 30% of profits, exploit kits cost $1,400 per month, and denial of service attacks cost $766.67 per month. Other services like compromised accounts and device loads also have relatively low price points. It is important for organizations to implement security best practices like enabling threat protection, practicing secure DevOps, and using tools like Azure Security Center to monitor for attacks.
More Related Content
What's hot
Why you need to secure mobile apps - now

No matter what size of company you’re at, you probably have a work phone. It might not have been given to you by your company, but you use it for work in one way or another. That means there is company data on your phone. Why do companies need a solution that secures the apps rather than the device – so employees can have the freedom and flexibility they need to get their work done.
OSB160: Trust Your Apps. See How with Ivanti Application Control

This document provides an agenda for a presentation on Ivanti Application Control. The presentation covers how Application Control works under the hood to whitelist trusted applications using file ownership. It discusses the challenges of user-targeted attacks and why traditional approaches like blacklisting and antivirus are not enough. Customer success stories are shared where Application Control has prevented malware infections and improved security posture. Tips are provided such as following expert guidance, getting business buy-in, and using discovery tools to understand the existing application estate before deploying controls. A demo of Application Control is planned and time for questions is allotted at the end.
Disaster recovery glossary

This document defines key terms related to disaster recovery including: alerts, backups, continuity availability, disaster recovery, exercises, recovery time objective (RTO), recovery point objective (RPO), shared responsibility model, risk assessment, redundancy, business continuity, application recovery, high availability, remote sites, assets, and alternative work area. It provides brief explanations of each term and its relevance to maintaining operations and recovering from a disaster.
airwatchexpress_infographic(2)

Small and medium-sized businesses face significant internet security threats, with 43% of small businesses and 22% of medium businesses being compromised in 2015. However, AirWatch Express provides a simplified mobile device management system that allows SMBs to protect their organizations from lost or stolen devices by remotely wiping business data while keeping personal information intact, without needing additional software, hardware, or IT expertise.
How to Cut Through the “Fog of More” to Achieve a Solid Security Foundation 

Why do security programs fail? How does a company that passed a recent audit suffer a breach? Is there a silver bullet for securing my environment? It seems there are more questions than answers in cybersecurity today. In this session we'll provide guidance and talk about ways to focus your security strategy to reduce the volume of incidents so you can focus on business initiatives instead.
Cloud Security Myths Vs Facts

The belief that cloud computing is not as secure as on-site servers stems from a number of myths that have been floating around since the first cloud-based solutions were introduced. Some of the most common myths about cloud security are presented on the following slides — along with the facts that dispel these myths.
Web App Sec Roadmap

This document provides a roadmap for web application security. It notes that web application security is still immature, traditional operations teams do not understand the risks, and companies often struggle to assign responsibility for security to one person due to organizational challenges. The document aims to help companies better manage web application security.
Streamline and Secure Your Network and Users

This document discusses the benefits of using Zscaler's cloud-based network and internet security solution over traditional on-premise appliance solutions. It summarizes that Zscaler provides comprehensive security across multiple threat vectors through a single cloud platform. It is more cost effective than appliance solutions and improves performance and user experience while reducing complexity and management overhead. The document also highlights key capabilities of Zscaler such as real-time inspection of all traffic including SSL, global policy management, and unified reporting and administration.
Cloud Computing Risks by Ravi Namboori Cisco Evangelist

Cloud computing is nothing but accessing and using applications and files over the Internet rather than on your own computing devices. Learn what is Cloud computing and what are the risks it facing & conclusions given by Ravi Namboori a Network Architect. He is having 20+years of experience in IT field & Entrepreneurship.
Security in Remote Business 

www.apexlogics.net
Managing a remote business requires clear strategy for communication. This does not only require the strategy and modes of communication to be defined but this process needs to be secure as well.
Stop Attacks and Mitigate Risk with Application and Device Control

Application and device control features in Symantec Endpoint Protection allow organizations to restrict applications and devices used on endpoints, mitigate risks, and prevent attacks. These features whitelist approved applications and devices, blacklist those known to be bad, and block unauthorized access. They also prevent data loss through external storage devices and help enforce corporate security policies and compliance standards.
Are Cloud Apps the Invisible Man?

This document describes IBM's Cloud Security Enforcer, a new SaaS solution that integrates identity and access control, threat prevention, policy enforcement, and discovery/visibility capabilities into a single platform. It consolidates leading IBM security technologies to help organizations securely adopt cloud services. Key features include risk scoring for thousands of apps, continuous monitoring of cloud activity, mapping network data to users, mobile integration, single sign-on, connectors to popular apps, access controls, activity monitoring, behavioral analysis, alerting/reporting, intrusion prevention, and threat protection from IBM X-Force. The solution aims to help customers securely deploy cloud services for their employees.
Introducing IBM Cloud Security Enforcer, CASB, IDaaS and Threat Prevention

View on demand webinar:
https://securityintelligence.com/events/introducing-ibm-cloud-security-enforcer-casb-idaas-and-threat-prevention/
Cloud Security Enforcer is the first solution to combine Cloud Access Security Broker (CASB) functionality with identity services (IDaaS), policy enforcement and dynamic threat prevention intelligence into a single integrated SaaS solution.
Join Daniel Wolff, Program Director Cloud Security Product Management, and Gonzalo de la Hoz, IAM European Segment Leader, as we discuss how IBM Cloud Security Enforcer has integrated multiple technologies crucial to enabling safe adoption of cloud applications in the enterprise:
- Cloud application discovery and risk
- Cloud identity services and application on-boarding
- Closing the mobile device gap
- Policy enforcement and threat prevention
Big Fix Q-Radar Ahmed Sharaf - EmbeddedSecurity.net

IBM Security and Xband can help enterprises remediate vulnerabilities faster. The perimeter is no longer fixed as endpoints are everywhere. Cybercrime is becoming more sophisticated and severe, with 600 million records leaked in 2015. Most breaches are caused by ineffective patch management as 75% of attacks use known vulnerabilities and it takes on average 256 days to detect advanced threats. IBM BigFix can find unmanaged endpoints, fix vulnerabilities across systems, and continuously monitor compliance to help secure organizations. It bridges the gap between security and IT operations for shared visibility and control.
Antivirus management lexington ky

IT safety measures disciplines for a much price reduction, such seeing that antivirus managing, firewall managing, intrusion discovery and deterrence, system setup and managing and exclusive private communities. For more information on click here: http://www.integrityky.com/antivirus-management-with-integrity-it/
Don’t Drown in a Sea of Cyberthreats: Mitigate Attacks with IBM BigFix & QRadar

view on demand: https://securityintelligence.com/events/dont-drown-in-a-sea-of-cyberthreats/
Security teams can be overwhelmed by a sea of vulnerabilities–without the contextual data to help them focus their efforts on the weaknesses that are most likely to be exploited. Cyberthreats need to be stopped before they cause significant financial and reputational damages to an organization. You need a security system that can detect an attack, prioritize risks and respond within minutes to shut down an attack or vulnerability that could compromise your endpoints and data.
Join this webinar and learn how IBM BigFix seamlessly integrates with IBM QRadar to provide accelerated risk prioritization and incident response to mitigate potential attacks giving you an integrated threat protection system to keep your corporate and customer data secure.
Saas security stock company

Cloud SaaS company has high stack revenue. It's reviewed current SaaS company status at the 70% growth. And it found security SaaS company were still need costly.
Security framework shakedown_-_chart_your_journey_with_aws_best_practices_ini...

Security framework shakedown_-_chart_your_journey_with_aws_best_practices_ini...Amazon Web Services LATAM
Security Framework Sakedown apresentado no Initiate Day São Paulo para setor público na Amazon Web ServicesEnabling Cloud Smart, Zero-Trust, and TIC

The document outlines Matt Jordan's presentation on enabling cloud smart, zero-trust networking, and trusted internet connections (TIC) at a public sector summit. It discusses the concepts of cloud smart, focusing on making informed technology decisions aligned with agency missions. Zero-trust networking principles of identity assurance, least privilege access, and auditing are described. Iterating TIC to leverage commercial innovation through collaboration and automated verification is presented, with benefits including efficient deployment, relying on continuous research and development, and multilayered security.
What's hot (19)
OSB160: Trust Your Apps. See How with Ivanti Application Control

OSB160: Trust Your Apps. See How with Ivanti Application Control
How to Cut Through the “Fog of More” to Achieve a Solid Security Foundation 

How to Cut Through the “Fog of More” to Achieve a Solid Security Foundation
Cloud Computing Risks by Ravi Namboori Cisco Evangelist

Cloud Computing Risks by Ravi Namboori Cisco Evangelist
Stop Attacks and Mitigate Risk with Application and Device Control

Stop Attacks and Mitigate Risk with Application and Device Control
Introducing IBM Cloud Security Enforcer, CASB, IDaaS and Threat Prevention

Introducing IBM Cloud Security Enforcer, CASB, IDaaS and Threat Prevention
Big Fix Q-Radar Ahmed Sharaf - EmbeddedSecurity.net

Big Fix Q-Radar Ahmed Sharaf - EmbeddedSecurity.net
Don’t Drown in a Sea of Cyberthreats: Mitigate Attacks with IBM BigFix & QRadar

Don’t Drown in a Sea of Cyberthreats: Mitigate Attacks with IBM BigFix & QRadar
Security framework shakedown_-_chart_your_journey_with_aws_best_practices_ini...

Security framework shakedown_-_chart_your_journey_with_aws_best_practices_ini...
Similar to Akamai
Panda Cloud Services

The document describes Panda Cloud Protection, a SaaS security solution that protects endpoints, email, and web traffic from cyber threats. It works by connecting client systems and traffic in real time to Panda's Collective Intelligence for proactive protection with 15 security modules. Benefits include robust protection, no upfront investment or maintenance costs, automatic updates, and centralized remote management through a web console.
B&W Netsparker overview

The Netsparker Web Application #Security #Scanners employ a unique and dead-accurate vulnerability scanning technology that automatically verify the vulnerabilities by producing a proof of exploit.
Discover how Netsparker find security flaws in websites, applications and services and protect whole system in 3 clicks.
Softprom by ERC official Value added #distributor of #Netsparker in Europe.
Top 10 Azure Security Best Practices (1).pptx

Attack services like ransomware, zero-days, exploit kits, and denial of service can be purchased at relatively low prices online. Ransomware costs $66 upfront or 30% of profits, exploit kits cost $1,400 per month, and denial of service attacks cost $766.67 per month. Other services like compromised accounts and device loads also have relatively low price points. It is important for organizations to implement security best practices like enabling threat protection, practicing secure DevOps, and using tools like Azure Security Center to monitor for attacks.
Temperfield vSphere Executive Presentation

This document discusses how VMware vSphere 4.0 can help businesses manage risk, costs, and change by increasing IT infrastructure efficiency, control, and choice. It outlines how vSphere allows businesses to build high-performance, cost-efficient data centers and realize fiscal advantages through consolidation and cost reductions. It also enables increased flexibility without sacrificing security and delivers applications as dynamic, cost-efficient IT services.
Ransomeware Recovery by Veeam

Ransomeware Recovery by Veeam. if you have problem about Ransomeware veeam will help you to prevention and resolve problem.
AppTrana SECaaS (Security as a Service)

If you want to improve your security system without draining your budget, considering SECaaS is worth looking into. Get the complete guide.
Solution Brief

This document summarizes a web server protection solution called the IPS 5500 provided by Top Layer Networks. The IPS 5500 uses three-dimensional protection (3DP) through content inspection, stateful firewall filtering, and attack mitigation to address threats like exploits, unauthorized access, and denial of service attacks. It provides benefits like uptime, bandwidth availability, and performance. Customers report an immediate ROI from costs savings and increased revenues. Sample customers using it include top banks, retailers, and advertisers.
Kona Web Application Firewall Product Brief - Application-layer defense to pr...

Kona Web Application Firewall provides always-on and highly scalable protection against web application attacks including SQL injections, cross-site scripting and remote file inclusion – while keeping application performance high. By leveraging the globally distributed Akamai Intelligent Platform™ Kona Web Application Firewall scales automatically to defend against massive application attacks and frees companies from the complexities and investment in dedicated hardware. Akamai’s Threat Intelligence Team continuously refines Kona WAF rules for known website attacks and responds to new threats as they emerge.
Visit us to learn more: http://www.akamai.com/html/solutions/web-application-firewall.html
Site Shield Product Brief - Origin defense by cloaking web infrastructure and...

This document provides an overview of Akamai's Site Shield product, which protects websites and applications by cloaking them from the public internet and restricting direct client access to the origin infrastructure. It works by providing a whitelist of allowed Akamai source addresses and forcing traffic through Akamai's intelligent platform where threats can be detected and mitigated. Site Shield enhances security, works with other Akamai cloud security technologies, and reduces infrastructure costs by consolidating connections to the origin.
VM Ware Market Analysis

The document summarizes virtualization opportunities for small and mid-sized businesses (SMBs) using VMware solutions. It outlines that 1/3 of SMBs have started virtualizing, with 50% planning to in the next 12 months. VMware has 3x the market share of its nearest competitor for SMBs. The document discusses VMware's SMB packaging and pricing, and provides tips on presenting virtualization to customers by highlighting benefits like increased productivity, availability, and cost savings. It also addresses common customer objections and goals for 2011 sales and projects.
Vm Ware Market Analysis

This document provides an overview and sales approach for selling virtualization solutions to small and mid-sized businesses (SMBs). It outlines that 1/3 of SMBs have started virtualizing and 50% plan to in the next 12 months. The presentation covers how virtualization can increase productivity, availability, and reduce costs. It introduces SMB-focused virtualization packages from VMware and handles common objections regarding VMware versus Microsoft and open source solutions.
What You're Missing With Your Current WAF Provider

Preventing data breaches and stopping malicious bots has become a top priority for many companies. Cloudflare blocks over 400 million malicious requests each day and from this we know that installing and forgetting a Web Application Firewall is no longer enough. In order to keep up, rules must not only be updated and monitored constantly, but they must also be augmented with other security services to provide an effective solution.
Remote Workforces Secure by Barracuda

1) The document discusses how Barracuda Networks provides solutions to securely enable remote access and scale networks, prevent advanced threats, and secure email, data, and web applications.
2) It highlights specific challenges companies currently face around securing remote workers accessing corporate networks, preventing phishing and social engineering attacks, and backing up Office 365 data.
3) Barracuda offers products including cloud-based firewalls, content filtering, email security, web application firewalls, and backup services to help secure remote access and scaling, protect email and data, and detect and prevent threats.
VIPRE Business Takes a Bite out of Bloatware

The remedy to bloatware is a better, more efficient product that is specifically engineered to scan, detect and remove myriad security threats without impacting performance and taking a big bite out of the IT capital expenditure budgets. Learn about the scope of the malware problem and strategies that can help you defend against evolving malware threats.
Closing the Loop on Web Application Vulnerabilities - John Dilley, Akamai

Join Akamai Security Engineering for an overview of our WAF rule process. Starting with the OWASP rule set, learn how Akamai incorporates our experience and security intelligence to improve core rules and create new rules. We'll explore how teams create further customized rules for individual application patching and close the loop, bringing these rules back through engineering to be normalized and delivered as common rules. Will include a view into how we're changing our process to take advantage of new security intelligence capabilities. See John Dilley's Edge Presentation: http://www.akamai.com/html/custconf/edgetv-security.html#closing-the-loop
The Akamai Edge Conference is a gathering of the industry revolutionaries who are committed to creating leading edge experiences, realizing the full potential of what is possible in a Faster Forward World. From customer innovation stories, industry panels, technical labs, partner and government forums to Web security and developers' tracks, there’s something for everyone at Edge 2013.
Learn more at http://www.akamai.com/edge
Avaya Emergency Preparedness Business Continuity

The document discusses the importance of including communications in business continuity planning. It notes that downtime from communications outages can be very costly for many industries. The key message is that organizations should not take the availability of communications for granted and ensure their systems are resilient, easy to use, able to reach necessary people, and enable quick recovery from disruptions. The document recommends adopting strategies like enabling remote work, distributing work locations, expanding self-service options, and supporting isolated work to maintain communications continuity during emergencies.
Presentation Flow Part A – The Challenge

The document discusses the need for application-level security to protect customers' websites from hacking attempts. It introduces dotDefender as a solution that plugs into servers to automatically stop hacking and allows hosting providers to offer improved security as an additional service. The partnership between dotDefender and Applicure is also described, where Applicure provides support and marketing assistance for dotDefender to hosting providers and their customers.
Presentation Flow Part A – The Challenge

The document discusses the need for improved application security to protect customers' websites from hacking attempts. It introduces dotDefender as a solution that can automatically stop hacking attempts through a server plug-in. The solution benefits hosting providers by allowing them to offer improved security as an additional service without impacting traffic. The document proposes a partnership where the hosting provider would resell the dotDefender solution to its customers, generating additional revenue through a software-as-a-service model.
State of the Internet: Mirai, IOT and History of Botnets

This document discusses the history and evolution of botnets, focusing on the Mirai botnet. It describes how Mirai was able to assemble a large botnet by exploiting vulnerabilities in internet of things devices with default passwords. Mirai launched large distributed denial of service attacks in late 2016 by harnessing the power of its botnet. The document advises steps companies can take to strengthen security and mitigate risks from botnet attacks.
Similar to Akamai (20)
Kona Web Application Firewall Product Brief - Application-layer defense to pr...

Kona Web Application Firewall Product Brief - Application-layer defense to pr...
Site Shield Product Brief - Origin defense by cloaking web infrastructure and...

Site Shield Product Brief - Origin defense by cloaking web infrastructure and...
Cloudflare_Everywhere_Security_Solution_Brief (1).pdf

Cloudflare_Everywhere_Security_Solution_Brief (1).pdf
What You're Missing With Your Current WAF Provider

What You're Missing With Your Current WAF Provider
Closing the Loop on Web Application Vulnerabilities - John Dilley, Akamai

Closing the Loop on Web Application Vulnerabilities - John Dilley, Akamai
State of the Internet: Mirai, IOT and History of Botnets

State of the Internet: Mirai, IOT and History of Botnets
Recently uploaded
Removing Uninteresting Bytes in Software Fuzzing

Imagine a world where software fuzzing, the process of mutating bytes in test seeds to uncover hidden and erroneous program behaviors, becomes faster and more effective. A lot depends on the initial seeds, which can significantly dictate the trajectory of a fuzzing campaign, particularly in terms of how long it takes to uncover interesting behaviour in your code. We introduce DIAR, a technique designed to speedup fuzzing campaigns by pinpointing and eliminating those uninteresting bytes in the seeds. Picture this: instead of wasting valuable resources on meaningless mutations in large, bloated seeds, DIAR removes the unnecessary bytes, streamlining the entire process.
In this work, we equipped AFL, a popular fuzzer, with DIAR and examined two critical Linux libraries -- Libxml's xmllint, a tool for parsing xml documents, and Binutil's readelf, an essential debugging and security analysis command-line tool used to display detailed information about ELF (Executable and Linkable Format). Our preliminary results show that AFL+DIAR does not only discover new paths more quickly but also achieves higher coverage overall. This work thus showcases how starting with lean and optimized seeds can lead to faster, more comprehensive fuzzing campaigns -- and DIAR helps you find such seeds.
- These are slides of the talk given at IEEE International Conference on Software Testing Verification and Validation Workshop, ICSTW 2022.
“I’m still / I’m still / Chaining from the Block”

“An Outlook of the Ongoing and Future Relationship between Blockchain Technologies and Process-aware Information Systems.” Invited talk at the joint workshop on Blockchain for Information Systems (BC4IS) and Blockchain for Trusted Data Sharing (B4TDS), co-located with with the 36th International Conference on Advanced Information Systems Engineering (CAiSE), 3 June 2024, Limassol, Cyprus.
Communications Mining Series - Zero to Hero - Session 1

This session provides introduction to UiPath Communication Mining, importance and platform overview. You will acquire a good understand of the phases in Communication Mining as we go over the platform with you. Topics covered:
• Communication Mining Overview
• Why is it important?
• How can it help today’s business and the benefits
• Phases in Communication Mining
• Demo on Platform overview
• Q/A
20240607 QFM018 Elixir Reading List May 2024

Everything I found interesting about the Elixir programming ecosystem in May 2024
Artificial Intelligence for XMLDevelopment

In the rapidly evolving landscape of technologies, XML continues to play a vital role in structuring, storing, and transporting data across diverse systems. The recent advancements in artificial intelligence (AI) present new methodologies for enhancing XML development workflows, introducing efficiency, automation, and intelligent capabilities. This presentation will outline the scope and perspective of utilizing AI in XML development. The potential benefits and the possible pitfalls will be highlighted, providing a balanced view of the subject.
We will explore the capabilities of AI in understanding XML markup languages and autonomously creating structured XML content. Additionally, we will examine the capacity of AI to enrich plain text with appropriate XML markup. Practical examples and methodological guidelines will be provided to elucidate how AI can be effectively prompted to interpret and generate accurate XML markup.
Further emphasis will be placed on the role of AI in developing XSLT, or schemas such as XSD and Schematron. We will address the techniques and strategies adopted to create prompts for generating code, explaining code, or refactoring the code, and the results achieved.
The discussion will extend to how AI can be used to transform XML content. In particular, the focus will be on the use of AI XPath extension functions in XSLT, Schematron, Schematron Quick Fixes, or for XML content refactoring.
The presentation aims to deliver a comprehensive overview of AI usage in XML development, providing attendees with the necessary knowledge to make informed decisions. Whether you’re at the early stages of adopting AI or considering integrating it in advanced XML development, this presentation will cover all levels of expertise.
By highlighting the potential advantages and challenges of integrating AI with XML development tools and languages, the presentation seeks to inspire thoughtful conversation around the future of XML development. We’ll not only delve into the technical aspects of AI-powered XML development but also discuss practical implications and possible future directions.
Climate Impact of Software Testing at Nordic Testing Days

My slides at Nordic Testing Days 6.6.2024
Climate impact / sustainability of software testing discussed on the talk. ICT and testing must carry their part of global responsibility to help with the climat warming. We can minimize the carbon footprint but we can also have a carbon handprint, a positive impact on the climate. Quality characteristics can be added with sustainability, and then measured continuously. Test environments can be used less, and in smaller scale and on demand. Test techniques can be used in optimizing or minimizing number of tests. Test automation can be used to speed up testing.
Pushing the limits of ePRTC: 100ns holdover for 100 days

At WSTS 2024, Alon Stern explored the topic of parametric holdover and explained how recent research findings can be implemented in real-world PNT networks to achieve 100 nanoseconds of accuracy for up to 100 days.
GraphSummit Singapore | Neo4j Product Vision & Roadmap - Q2 2024

Maruthi Prithivirajan, Head of ASEAN & IN Solution Architecture, Neo4j
Get an inside look at the latest Neo4j innovations that enable relationship-driven intelligence at scale. Learn more about the newest cloud integrations and product enhancements that make Neo4j an essential choice for developers building apps with interconnected data and generative AI.
Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf

Discover how MongoDB Atlas and vector search technology can revolutionize your application's search capabilities. This comprehensive presentation covers:
* What is Vector Search?
* Importance and benefits of vector search
* Practical use cases across various industries
* Step-by-step implementation guide
* Live demos with code snippets
* Enhancing LLM capabilities with vector search
* Best practices and optimization strategies
Perfect for developers, AI enthusiasts, and tech leaders. Learn how to leverage MongoDB Atlas to deliver highly relevant, context-aware search results, transforming your data retrieval process. Stay ahead in tech innovation and maximize the potential of your applications.
#MongoDB #VectorSearch #AI #SemanticSearch #TechInnovation #DataScience #LLM #MachineLearning #SearchTechnology
Alt. GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using ...

Effective Application Security in Software Delivery lifecycle using Deployment Firewall and DBOM
The modern software delivery process (or the CI/CD process) includes many tools, distributed teams, open-source code, and cloud platforms. Constant focus on speed to release software to market, along with the traditional slow and manual security checks has caused gaps in continuous security as an important piece in the software supply chain. Today organizations feel more susceptible to external and internal cyber threats due to the vast attack surface in their applications supply chain and the lack of end-to-end governance and risk management.
The software team must secure its software delivery process to avoid vulnerability and security breaches. This needs to be achieved with existing tool chains and without extensive rework of the delivery processes. This talk will present strategies and techniques for providing visibility into the true risk of the existing vulnerabilities, preventing the introduction of security issues in the software, resolving vulnerabilities in production environments quickly, and capturing the deployment bill of materials (DBOM).
Speakers:
Bob Boule
Robert Boule is a technology enthusiast with PASSION for technology and making things work along with a knack for helping others understand how things work. He comes with around 20 years of solution engineering experience in application security, software continuous delivery, and SaaS platforms. He is known for his dynamic presentations in CI/CD and application security integrated in software delivery lifecycle.
Gopinath Rebala
Gopinath Rebala is the CTO of OpsMx, where he has overall responsibility for the machine learning and data processing architectures for Secure Software Delivery. Gopi also has a strong connection with our customers, leading design and architecture for strategic implementations. Gopi is a frequent speaker and well-known leader in continuous delivery and integrating security into software delivery.
Goodbye Windows 11: Make Way for Nitrux Linux 3.5.0!

As the digital landscape continually evolves, operating systems play a critical role in shaping user experiences and productivity. The launch of Nitrux Linux 3.5.0 marks a significant milestone, offering a robust alternative to traditional systems such as Windows 11. This article delves into the essence of Nitrux Linux 3.5.0, exploring its unique features, advantages, and how it stands as a compelling choice for both casual users and tech enthusiasts.
Uni Systems Copilot event_05062024_C.Vlachos.pdf

Unlocking Productivity: Leveraging the Potential of Copilot in Microsoft 365, a presentation by Christoforos Vlachos, Senior Solutions Manager – Modern Workplace, Uni Systems
Securing your Kubernetes cluster_ a step-by-step guide to success !

Today, after several years of existence, an extremely active community and an ultra-dynamic ecosystem, Kubernetes has established itself as the de facto standard in container orchestration. Thanks to a wide range of managed services, it has never been so easy to set up a ready-to-use Kubernetes cluster.
However, this ease of use means that the subject of security in Kubernetes is often left for later, or even neglected. This exposes companies to significant risks.
In this talk, I'll show you step-by-step how to secure your Kubernetes cluster for greater peace of mind and reliability.
20 Comprehensive Checklist of Designing and Developing a Website

Dive into the world of Website Designing and Developing with Pixlogix! Looking to create a stunning online presence? Look no further! Our comprehensive checklist covers everything you need to know to craft a website that stands out. From user-friendly design to seamless functionality, we've got you covered. Don't miss out on this invaluable resource! Check out our checklist now at Pixlogix and start your journey towards a captivating online presence today.
Introducing Milvus Lite: Easy-to-Install, Easy-to-Use vector database for you...

Join us to introduce Milvus Lite, a vector database that can run on notebooks and laptops, share the same API with Milvus, and integrate with every popular GenAI framework. This webinar is perfect for developers seeking easy-to-use, well-integrated vector databases for their GenAI apps.
UiPath Test Automation using UiPath Test Suite series, part 5

Welcome to UiPath Test Automation using UiPath Test Suite series part 5. In this session, we will cover CI/CD with devops.
Topics covered:
CI/CD with in UiPath
End-to-end overview of CI/CD pipeline with Azure devops
Speaker:
Lyndsey Byblow, Test Suite Sales Engineer @ UiPath, Inc.
Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf

Monitoring and observability aren’t traditionally found in software curriculums and many of us cobble this knowledge together from whatever vendor or ecosystem we were first introduced to and whatever is a part of your current company’s observability stack.
While the dev and ops silo continues to crumble….many organizations still relegate monitoring & observability as the purview of ops, infra and SRE teams. This is a mistake - achieving a highly observable system requires collaboration up and down the stack.
I, a former op, would like to extend an invitation to all application developers to join the observability party will share these foundational concepts to build on:
Recently uploaded (20)
Monitoring Java Application Security with JDK Tools and JFR Events

Monitoring Java Application Security with JDK Tools and JFR Events
Communications Mining Series - Zero to Hero - Session 1

Communications Mining Series - Zero to Hero - Session 1
Climate Impact of Software Testing at Nordic Testing Days

Climate Impact of Software Testing at Nordic Testing Days
Pushing the limits of ePRTC: 100ns holdover for 100 days

Pushing the limits of ePRTC: 100ns holdover for 100 days
GraphSummit Singapore | Neo4j Product Vision & Roadmap - Q2 2024

GraphSummit Singapore | Neo4j Product Vision & Roadmap - Q2 2024
Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf

Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf
Alt. GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using ...

Alt. GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using ...
Goodbye Windows 11: Make Way for Nitrux Linux 3.5.0!

Goodbye Windows 11: Make Way for Nitrux Linux 3.5.0!
Securing your Kubernetes cluster_ a step-by-step guide to success !

Securing your Kubernetes cluster_ a step-by-step guide to success !
20 Comprehensive Checklist of Designing and Developing a Website

20 Comprehensive Checklist of Designing and Developing a Website
Introducing Milvus Lite: Easy-to-Install, Easy-to-Use vector database for you...

Introducing Milvus Lite: Easy-to-Install, Easy-to-Use vector database for you...
UiPath Test Automation using UiPath Test Suite series, part 5

UiPath Test Automation using UiPath Test Suite series, part 5
Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf

Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf
Akamai
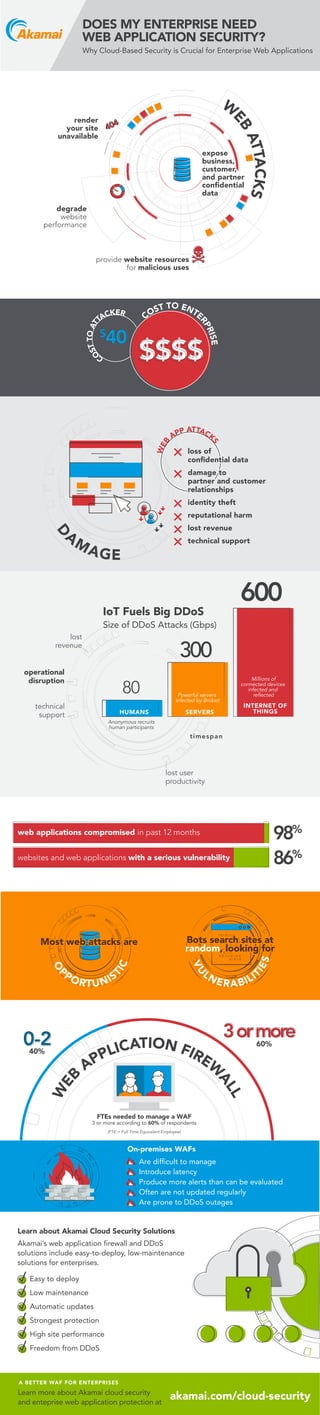
- 1. Learn more about Akamai cloud security and enteprise web application protection at A BETTER WAF FOR ENTERPRISES akamai.com/cloud-security Learn about Akamai Cloud Security Solutions Akamai’s web application firewall and DDoS solutions include easy-to-deploy, low-maintenance solutions for enterprises. Easy to deploy Low maintenance Automatic updates Strongest protection High site performance Freedom from DDoS Are difficult to manage Introduce latency Produce more alerts than can be evaluated Often are not updated regularly Are prone to DDoS outages On-premises WAFs 0-2 3ormore FTEs needed to manage a WAF 3 or more according to 60% of respondents (FTE = Full Time Equivalent Employee) W EB APPLICATION FIREW ALL W EB APPLICATION FIREW ALL 40% 60% Most web attacks areMost web attacks are O P PORTUNIS TIC O P PORTUNIS TIC VU LNERABILI TIES VU LNERABILI TIES Bots search sites at random, looking for Bots search sites at random, looking for 98% 86% web applications compromised in past 12 months websites and web applications with a serious vulnerability operational disruption lost user productivity lost user productivity lost revenue lost revenue technical support 80 HUMANS SERVERS INTERNET OF THINGS 300 600 timespan IoT Fuels Big DDoS Size of DDoS Attacks (Gbps) Anonymous recruits human participants Powerful servers infected by Brobot Millions of connected devices infected and reflected WEB APP ATTACK S loss of confidential data damage to partner and customer relationships identity theft reputational harm lost revenue technical support loss of confidential data damage to partner and customer relationships identity theft reputational harm lost revenue technical support D A MAGE $ 40 COST TO ENTE RPRISE C OSTTOAT TACKER expose business, customer, and partner confidential data expose business, customer, and partner confidential data provide website resources for malicious uses render your site unavailable degrade website performance W EB ATTACKS DOES MY ENTERPRISE NEED WEB APPLICATION SECURITY? Why Cloud-Based Security is Crucial for Enterprise Web Applications
