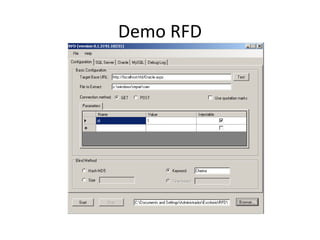
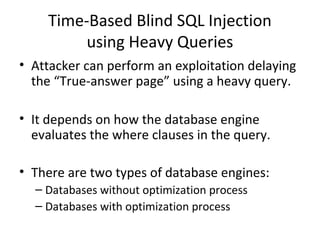
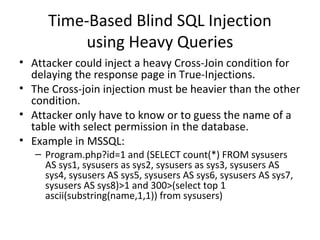
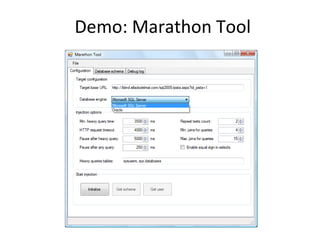
The document discusses various SQL injection techniques, including serialized and arithmetic SQL injection, as well as methods for downloading files and performing time-based blind SQL injections. It includes demonstrations for extracting data using complex queries and highlights the importance of query sanitization to prevent such attacks. The document also introduces a tool named 'Marathon' that automates these time-based blind SQL injection attacks across different database engines.




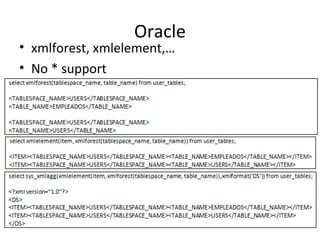





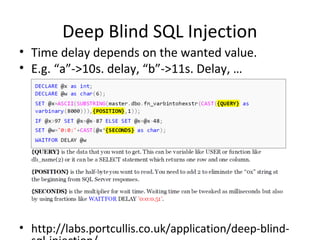
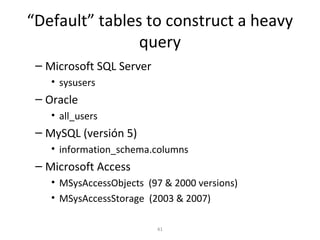
![Arithmetic Blind SQL Injection
• Divide by zero (David Litchfield)
– Id=A+(1/(ASCII(B)-C))
•A-> Param value originally used in the query.
•B -> Value we are searching for, e.g.:
Substring(passwd,1,1)
•C-> Counter [0..255]
– When ASCII(B)=C, the DB will generate a divide by
zero exception.](https://image.slidesharecdn.com/chemaalonso-palako-replayingblindsqli-140520002851-phpapp02/85/ShmooCON-2009-Re-playing-with-Blind-SQL-Injection-17-320.jpg)
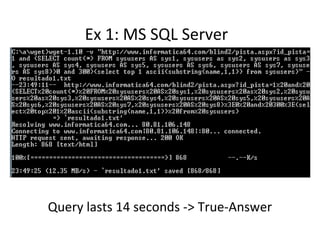
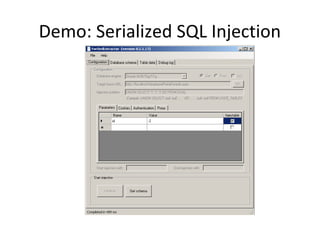
![Arithmetic Blind SQL Injection
• Sums and subtractions
– Id=A+ASCII(B)-C
•A-> Param value originally used in the query.
•B -> Value we are searching for, e.g.:
Substring(passwd,1,1)
•C-> Counter [0..255]
– When ASCII(B)=C, then the response page of
id=A+ASCII(B)-C will be the same as id=A](https://image.slidesharecdn.com/chemaalonso-palako-replayingblindsqli-140520002851-phpapp02/85/ShmooCON-2009-Re-playing-with-Blind-SQL-Injection-18-320.jpg)
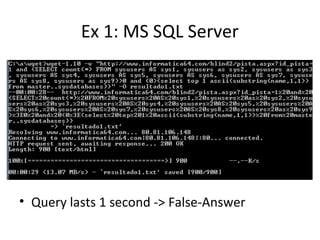
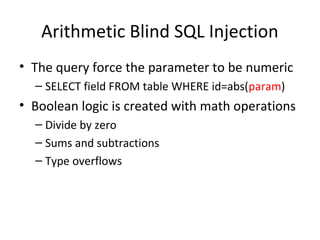
![Arithmetic Blind SQL Injection
• Value type overflow
– Id=A+((C/ASCII(B))*(K))
•A-> Param value originally used in the query.
•B -> Value we are searching for, e.g.:
Substring(passwd,1,1)
•C-> Counter [0..255]
•K-> Value that overflows the type defined for A
–(e.g. if A is integer, then K=2^32)
– When C/ASCII(B)==1, K*1 overflows the data type](https://image.slidesharecdn.com/chemaalonso-palako-replayingblindsqli-140520002851-phpapp02/85/ShmooCON-2009-Re-playing-with-Blind-SQL-Injection-19-320.jpg)