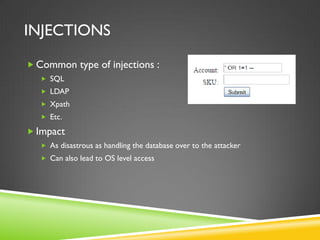
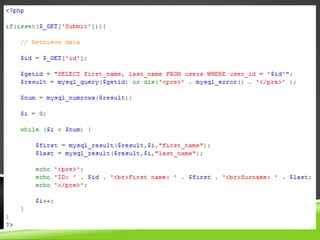
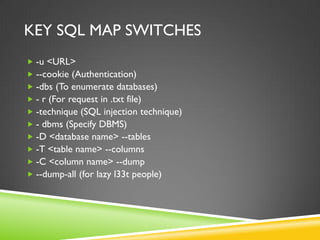
This document provides an overview of SQL injection and how to use the SQLMap tool to exploit SQL injection vulnerabilities. It begins with background on SQL injection as the first OWASP Top 10 vulnerability. It then explains how SQL injection works and common techniques. The bulk of the document focuses on using SQLMap to identify and exploit SQL injection flaws, including enumerating databases, tables, columns, and extracting data. It describes options to escalate access using SQLMap to interface with the operating system and access the file system and registry. Tamper scripts for bypassing web application firewalls are also discussed. The goal is to achieve "one click 0wnage" of systems with SQL injection vulnerabilities using SQLMap's powerful features.