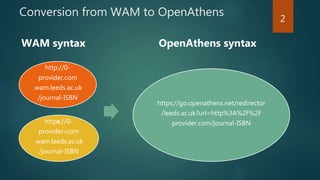
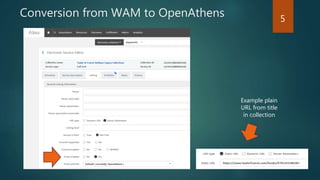
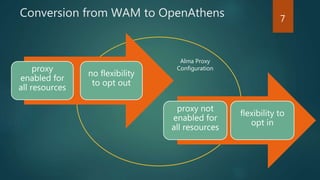
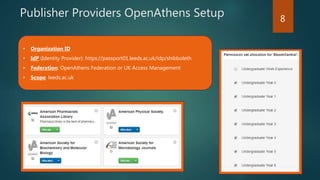
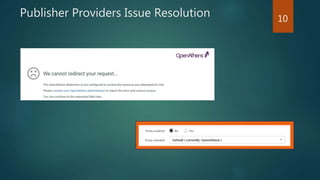
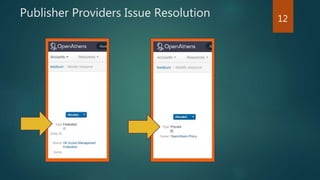
The document outlines the transition from WAM to OpenAthens for access management at the University of Leeds, detailing the conversion process, including syntax changes and proxy configurations. It addresses publisher provider issues, including the need for IP whitelisting and the resolution of federated access challenges. Additionally, it mentions various tips and resources for troubleshooting during the implementation process.