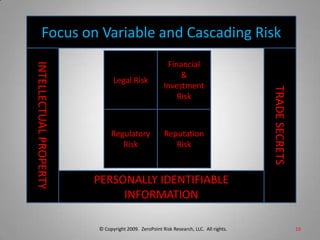
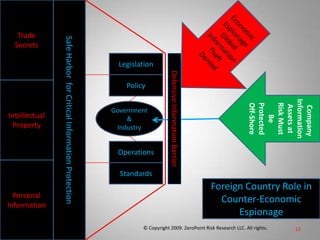
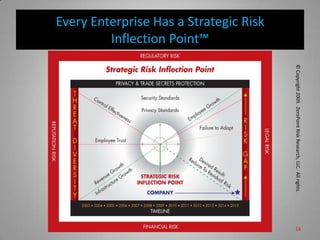
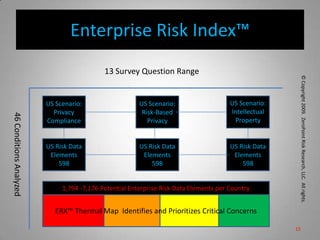
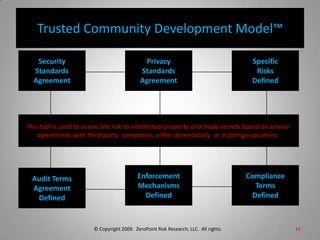
This document is from ZeroPoint Risk Research, an expert firm in protecting critical information assets from economic espionage and identity theft. It summarizes the global threat of espionage targeting US technology and intellectual property. More than 100 nations target US assets, with China and Russia being the top offenders. The document outlines the firm's services in consulting, research, and developing strategies, policies, and tools to assess risks to intellectual property, trade secrets, and personally identifiable information from foreign hosts and third parties.