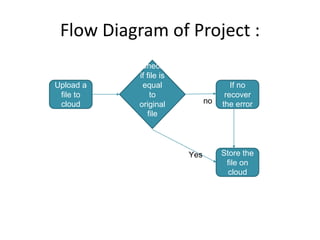
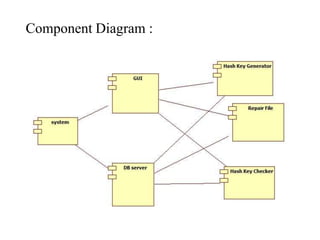
The document describes a student project titled "Error Detection in Big Data on Cloud". The project aims to develop a time-efficient approach for detecting and correcting errors in large sensor data stored on the cloud. If errors are found, the approach also involves error recovery and storing the corrected data in its original format. The proposed method uses algorithms like cyclic redundancy check, Hamming code, and secure hash algorithm to detect and locate errors in big data sets efficiently. Design documents like data flow diagrams, use case diagrams and class diagrams were created to plan the system architecture and implementation of the project.