Shamsa al mazrooei
•Download as PPTX, PDF•
0 likes•328 views
20 common ports
Report
Share
Report
Share
Recommended
BlueHat v17 || TLS 1.3 - Full speed ahead... mind the warnings - the great, t...

BlueHat v17 || TLS 1.3 - Full speed ahead... mind the warnings - the great, t...BlueHat Security Conference
Recommended
BlueHat v17 || TLS 1.3 - Full speed ahead... mind the warnings - the great, t...

BlueHat v17 || TLS 1.3 - Full speed ahead... mind the warnings - the great, t...BlueHat Security Conference
More Related Content
What's hot
What's hot (20)
Hypertexttransferprotocolhttp 131012171813-phpapp02

Hypertexttransferprotocolhttp 131012171813-phpapp02
Viewers also liked
Viewers also liked (9)
Similar to Shamsa al mazrooei
Similar to Shamsa al mazrooei (20)
09 Systems Software Programming-Network Programming.pptx

09 Systems Software Programming-Network Programming.pptx
PACE-IT, Security+1.4: Common Network Protocols (part 2)

PACE-IT, Security+1.4: Common Network Protocols (part 2)
Recently uploaded
Recently uploaded (20)
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...

Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
08448380779 Call Girls In Greater Kailash - I Women Seeking Men

08448380779 Call Girls In Greater Kailash - I Women Seeking Men
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
Boost PC performance: How more available memory can improve productivity

Boost PC performance: How more available memory can improve productivity
Understanding Discord NSFW Servers A Guide for Responsible Users.pdf

Understanding Discord NSFW Servers A Guide for Responsible Users.pdf
The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf

The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf
Tech Trends Report 2024 Future Today Institute.pdf

Tech Trends Report 2024 Future Today Institute.pdf
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
08448380779 Call Girls In Civil Lines Women Seeking Men

08448380779 Call Girls In Civil Lines Women Seeking Men
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
Shamsa al mazrooei
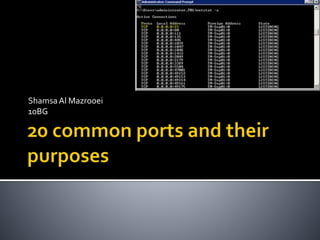
- 2. » A standard protocol for transferring files between computing systems. Assigned to port 20 and to port 21 (mostly uses port 20).
- 3. » An encrypted version of FTP, which uses Secure Shell (SSH). Assigned to port 22.
- 4. »The protocol used to transfer email from a client to an email server; it is also used to transfer email between servers. Assigned to port 25.
- 5. . »The protocol used by clients to retrieve email from servers. • Assigned to port 110. Common ports and protocols.
- 6. Technology In actuality, SSL should no longer be used. • Assigned to port 443. Common ports and protocols.
- 7. » A protocol used by clients to access email on email servers. Allows the client to organize email on the server into folders. Assigned to port 143
- 8. »The primary protocol used to transfer data over the Internet. Assigned to port 80.
- 9. »The primary protocol to securely transfer data over the Internet using SSL (Secure Socket Layer) or
- 10. »The protocol that is used to map computer names to their IP addresses (e.g., www.google.com to 74.125.28.104). • Assigned to port 53.
- 11. » Used in Microsoft networks by Remote Desktop Connection and Remote Assistance to make remote connections. • Assigned to port 3389.
- 12. – DHCP (Dynamic Host Configuration Protocol). »The protocol used within networks to automatically configure computers with the correct IP configurations (e.g., IP address, subnet mask, default gateway, and DNS server location).
- 13. . – SMB (Server Message Block). » A protocol used to transfer files over a network; the process is transparent to the user. • Assigned to port 445. Common ports and protocols.
- 14. »The protocol used for accessing and maintaining distributed directory information services (e.g., Active Directory Domain Services). • Assigned to port 389
- 15. » A protocol used to monitor and manage local area networks. • Assigned to port 161.
- 16. » A protocol used to share files across intranets (internal private networks) and the Internet. • Assigned to port 3020.
- 17. » A protocol used for remote access to systems; it is unsecure. It is a bi-directional terminal service. • Assigned to port 23.
- 18. » A protocol used to encrypt data traffic on a network. • Assigned to port 22.