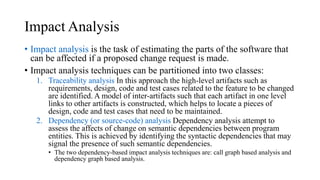
The document provides an overview of key concepts related to software maintenance and evolution, including:
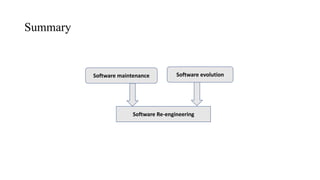
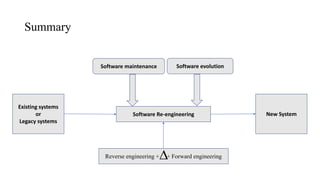
- Software maintenance focuses on preventing failures and involves bug fixing without major design changes.
- Software evolution describes how software grows over time to support new features and changes in technology.
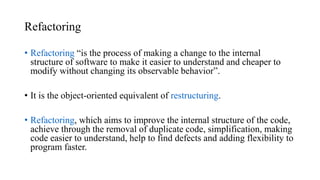
- Reengineering examines a system to restructure it in a new form through reverse and forward engineering.
- Legacy systems are old systems still valuable to organizations that are in the phase out stage of their lifecycle.