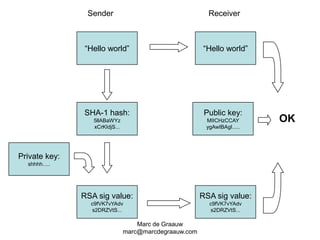
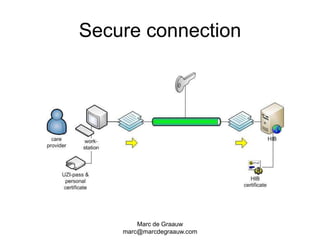
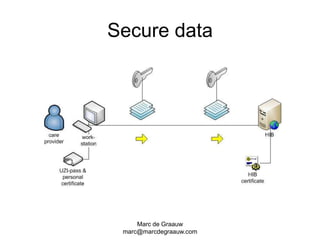
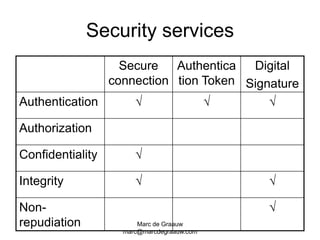
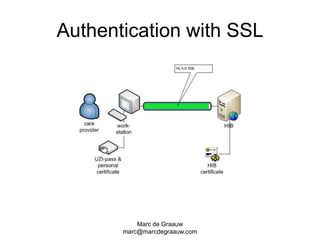
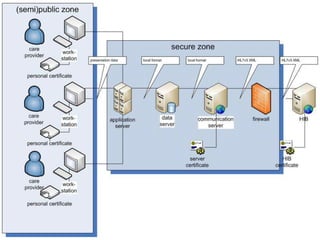
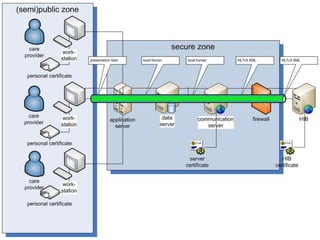
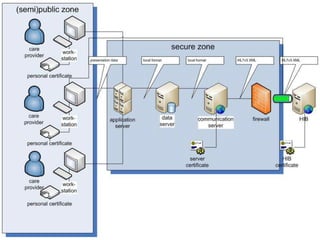
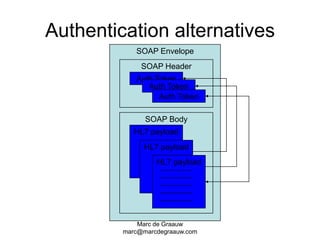
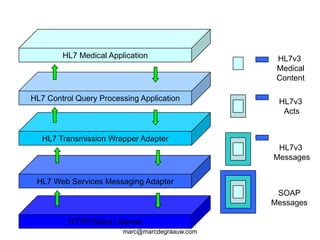
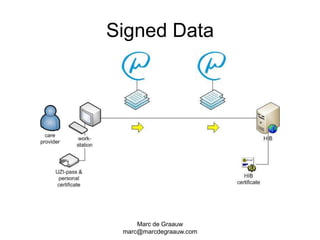
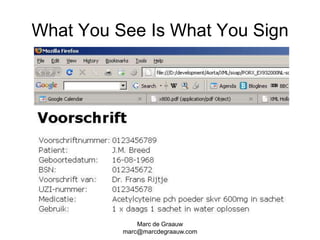
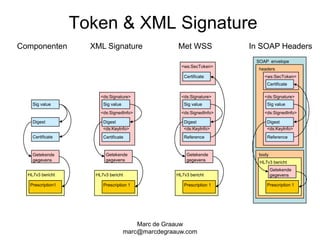
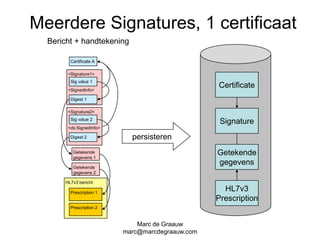
The document discusses authentication and digital signatures for healthcare messaging. It describes using smartcards with private/public key pairs for authentication. Lightweight authentication tokens containing a digital signature are proposed as an alternative to using SSL for every message. These tokens would include a message ID, time limits, and signed elements like patient ID and message type. Full digital signatures are still recommended for prescriptions while tokens may suffice for queries. Signing multiple parts of a message with the same certificate is also discussed.