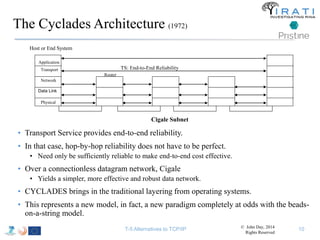
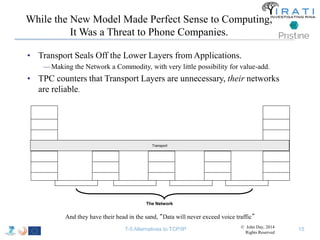
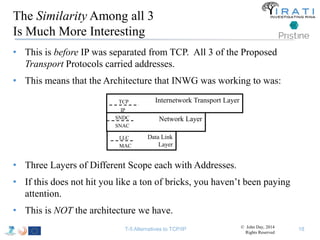
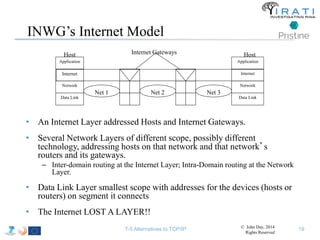
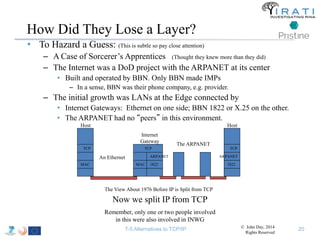
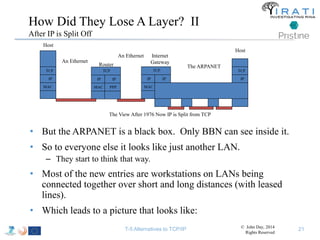
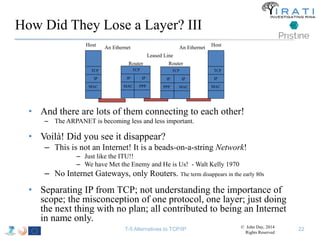
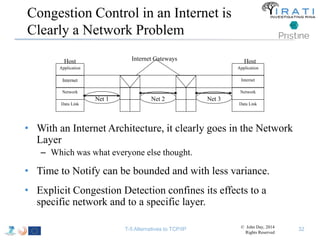
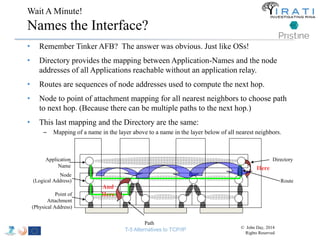
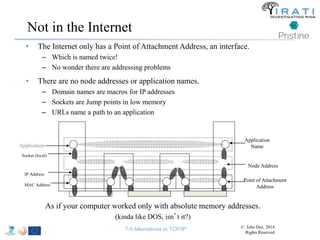
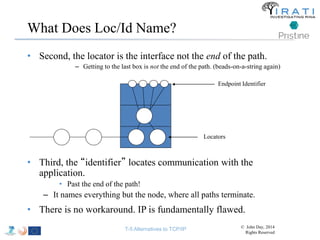
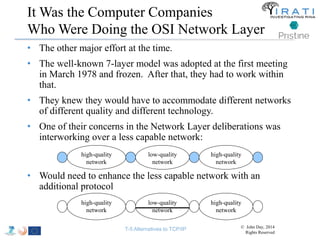
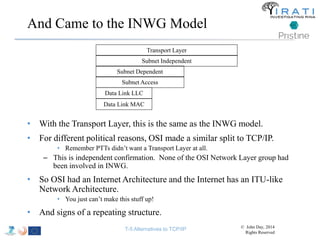
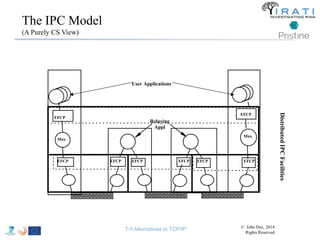
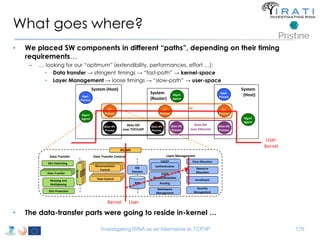
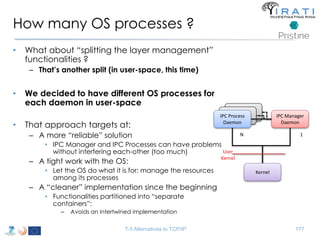
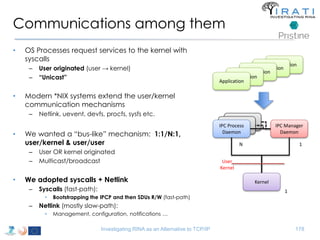
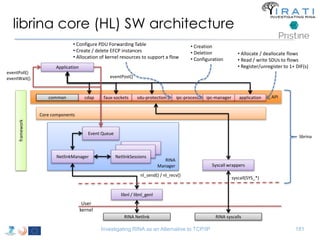
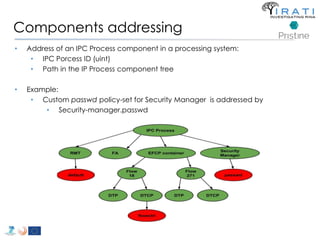
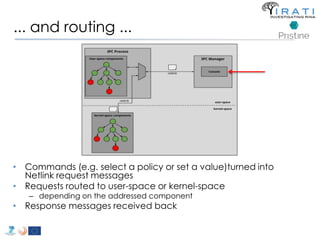
The document summarizes a tutorial on alternatives to TCP/IP given at IEEE Globecom 2014. It discusses the origins of packet switching networks and how they represented a shift from earlier circuit-switched "beads on a string" telephone networks. It also describes the layered CYCLADES network architecture from 1972 which introduced the concept of layers borrowed from operating systems. This represented a new distributed computing paradigm compared to earlier hierarchical models. The document outlines debates in the early Internetworking Working Group on proposed transport protocols and how they converged towards a three-layer model addressing hosts and gateways unlike the current TCP/IP model.
















![What Do We Mean by
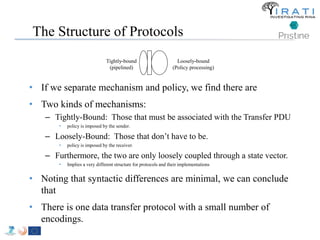
Separating Mechanism and Policy
• Concept first proposed by Bill Wulf [1975] for operating
systems.
• Separating what is common across solutions from what is uncommon.
• Mechanics of memory management are the same, allocation scheme or
page replacement policy is what varies.
• In protocols, there are a few mechanisms. Virtually all of the
variation is in the policies.
– Acknowledgement is mechanism; when to Ack is policy.
– This has major implication for the structure of protocols.
– By not separating mechanism and policy, we have been saying there is
one point in ~8 dimensional space that solves everything!
• Absurd! No one would expect that!
• We will apply this across the board to simplify and ensure that
cooperating layers behave in a compatible manner.
• Leverage is in the commonality, but letting what must vary vary.
– Never take it to extremes. It is subtle task.](https://image.slidesharecdn.com/tutorial-5-slides-globecom-2014-141216030720-conversion-gate02/85/RINA-Tutorial-IEEE-Globecom-2014-26-320.jpg)




![Loc/ID Split
(these are people who
lost a layer to begin with, right?)
• There are 3 problems with loc/id split:
• First off:
– Saltzer [1977] defines “resolve” as in “resolving a name” as “to
locate an object in a particular context, given its name.”
– In computing, all names locate something.
• So either nothing can be identified without locating it, nor located
without identifying it, OR
• Hence this is either a false distinction or it is meaningless.
T-5 Alternatives to TCP/IP © John Day, 2014
Rights Reserved](https://image.slidesharecdn.com/tutorial-5-slides-globecom-2014-141216030720-conversion-gate02/85/RINA-Tutorial-IEEE-Globecom-2014-37-320.jpg)








![Others Saw There Were Problems
• Nearly 15 Years Ago, DARPA Funded NewArch
– All the top minds of the Internet to find a new architecture
– Two years later, they came up dry
• At the same time, the National Research Council issued a report that said in
part “t
he insiders [network researchers] had not shown that they had managed to exercise the usual elements
of a successful research program, so a back-to-basics message was fitting.”
– Must have been sobering.
• When DARPA was unwilling to throw good money after bad, they went to NSF to
fund FIND and GENI, massive projects to FIND the Answer.
– At first, there promises of bold new ideas! Clean-slate! Start from Scratch! Etc.
– That gave way to ‘The Internet is best when it evolves to new solutions.’
– Which has now given way to ‘The Internet is such a success, we should build on that
success’
– By 2010, Having not come up with anything, consensus was that they must look outside
networking: Classic indicator of running out of ideas. Someone else must have them.
• What was the problem?
T-5 Alternatives to TCP/IP 49 © John Day, 2014
Rights Reserved](https://image.slidesharecdn.com/tutorial-5-slides-globecom-2014-141216030720-conversion-gate02/85/RINA-Tutorial-IEEE-Globecom-2014-49-320.jpg)









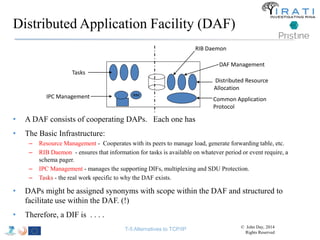
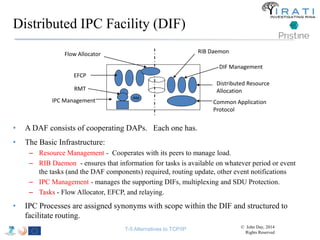
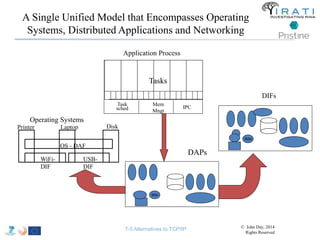

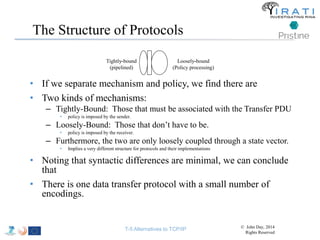







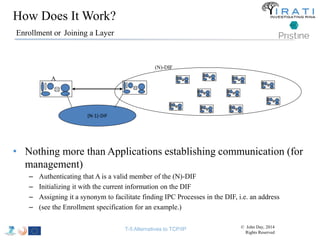

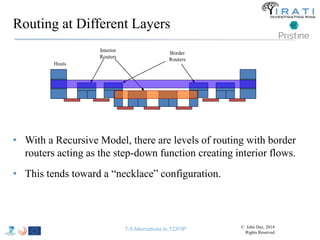
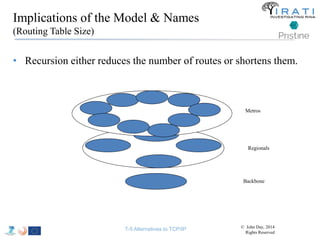
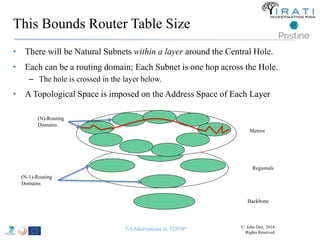
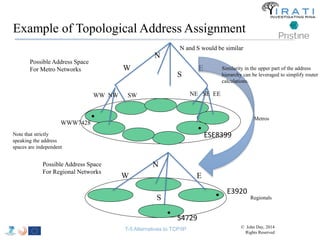
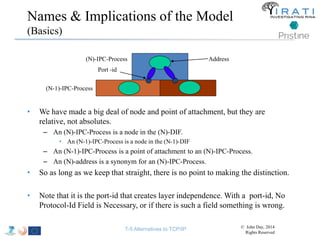
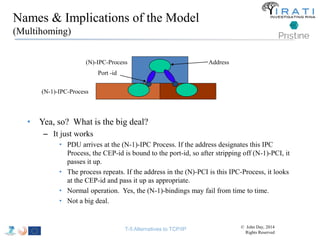
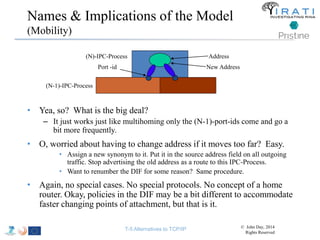


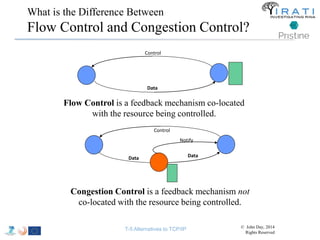
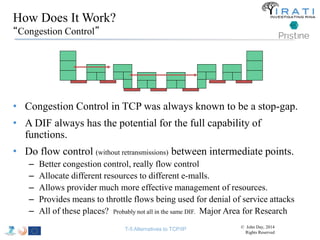


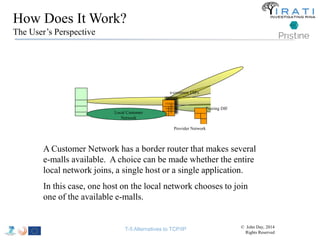

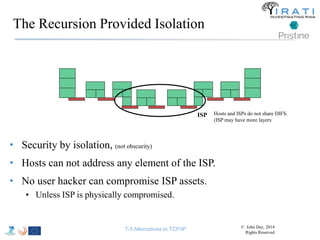









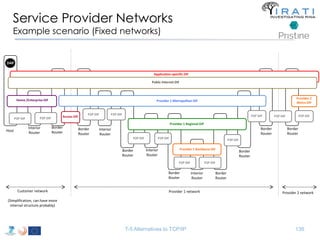
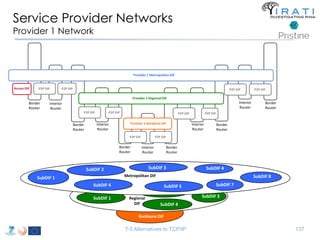
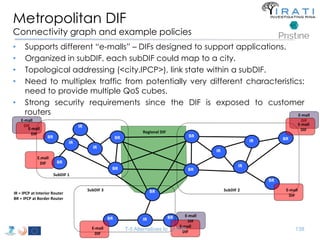
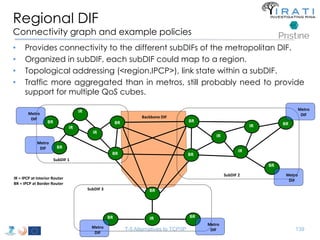
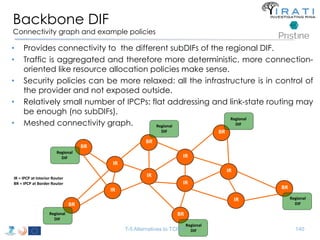

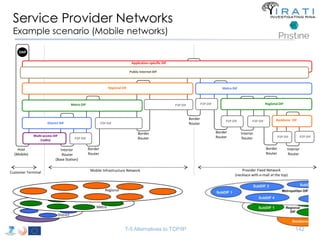
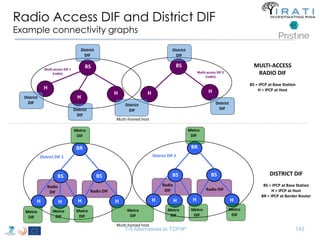
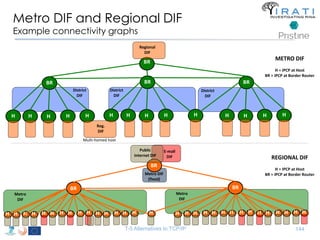


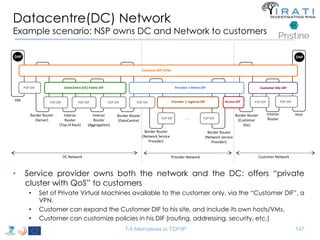
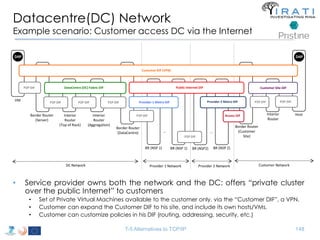
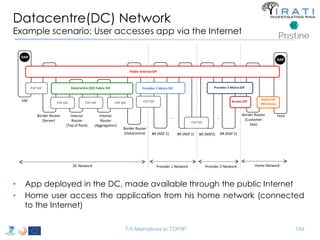
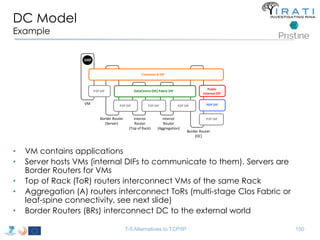






![IRATI - Outline
• FP7 Project grant #317814 (www.irati.eu)
• From Jan 2013 to Dec 2014 (2 years)
• 5 partners
– [Research] Fundació Privada i2CAT (Spain)
– [Research] iMinds VZW(Belgium)
– [SME] Nextworks s.r.l. (Italy)
– [Industry] Interoute (UK/Italy)
– [Academia] Boston University (US)
167](https://image.slidesharecdn.com/tutorial-5-slides-globecom-2014-141216030720-conversion-gate02/85/RINA-Tutorial-IEEE-Globecom-2014-167-320.jpg)
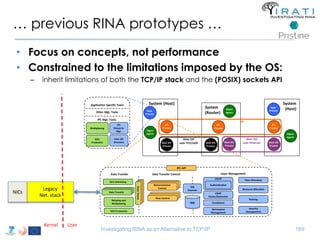
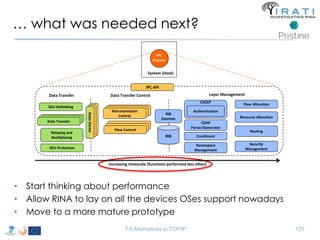


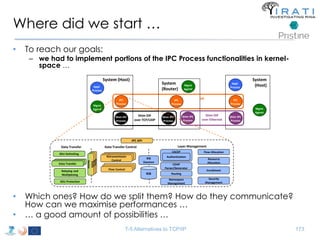
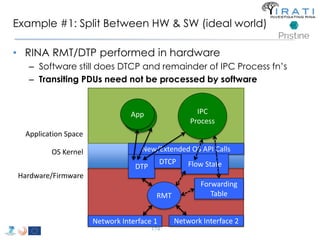
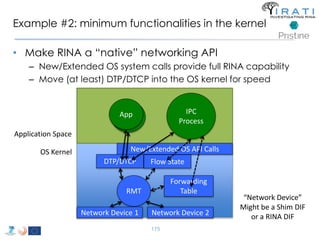
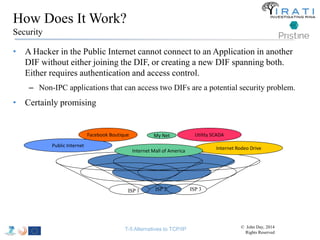
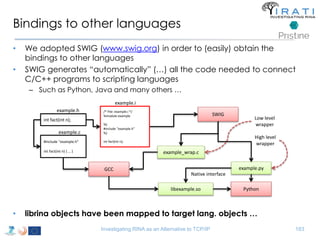
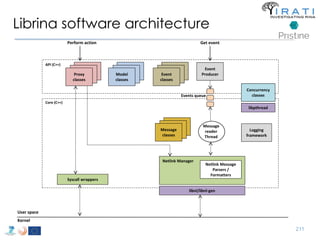
![Avoid (major) wreckages … librina
• Syscalls are “wrapped” by libc [(g)libc in GNU/Linux]
– i.e. syscall(SYS_write, …) → write(…)
• All applications are linked to (g)libc
• Changes to the syscalls → changes to (g)libc
– Breaking (g)libc could break the whole host
• Sandboxed environments are necessary
– Dependencies invalidation → Time consuming compilations
– That sort of changes are really hard to get approved upstream
– etc.
• Instead of changing (g)libc …
• we introduced librina (an external library aside (g)libc), as the initial way to
overcome these problems …
– … use the code without potentially wrecking the whole OS
RINA fn’s libc librina
Investigating RINA as an Alternative to TCP/IP 179
Application
libc
kernel
Application
kernel](https://image.slidesharecdn.com/tutorial-5-slides-globecom-2014-141216030720-conversion-gate02/85/RINA-Tutorial-IEEE-Globecom-2014-179-320.jpg)


![The Linux object model
• Linux has its “generic” object abstraction: kobject, kref and kset
Garbage collection & SysFS integration
struct kref { atomic_t refcount; }
struct kobject {
Naming & sysfs
const char * name; struct kset {
struct list_head entry; struct list_head list;
struct kobject * parent; spinlock_t klist_lock;
struct kset * kset; struct kobject kobj;
struct kobj_type * ktype; const struct kset set_uevent_ops * uevent_ops;
struct sysfs_dirent * sd; };
struct kref kref;
unsigned int state_initialized:1;
unsigned int state_in_sysfs:1;
unsigned int state_add_uevent_sent:1;
unsigned int state_remove_uevent_sent:1;
unsigned int uevent_suppress:1;
};
• Generic enough to be applied “everywhere”
– E.g. FS, HW Subsystems, Device drivers
Objects (dynamic) [re-]parenting
(loosely typed)
Objects grouping
References counting (explicit)
Investigating RINA as an Alternative to TCP/IP 186
SysFS integration](https://image.slidesharecdn.com/tutorial-5-slides-globecom-2014-141216030720-conversion-gate02/85/RINA-Tutorial-IEEE-Globecom-2014-186-320.jpg)



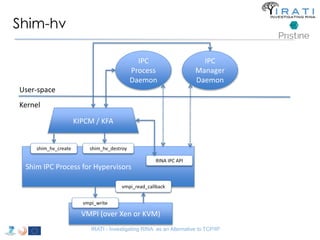














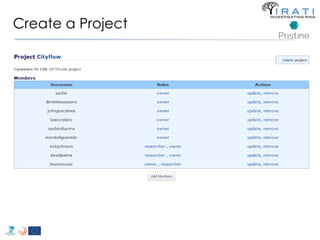
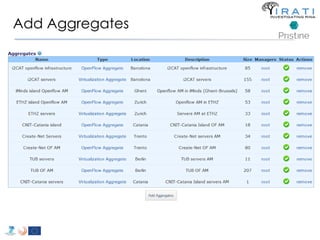
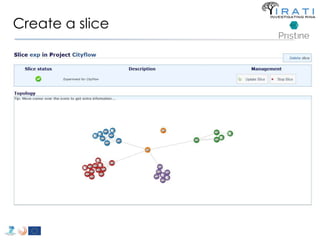
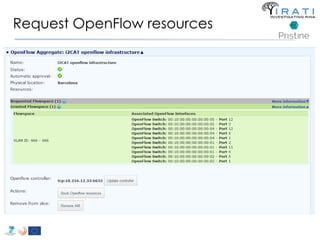
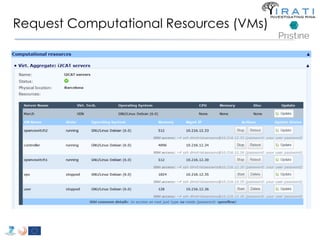


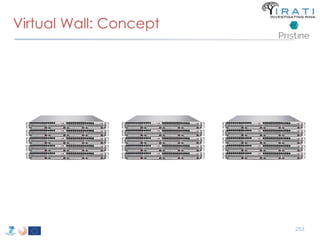
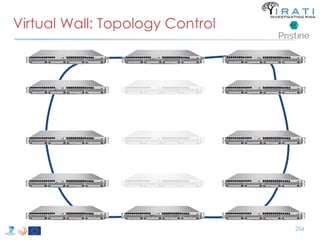




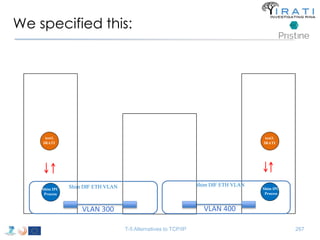
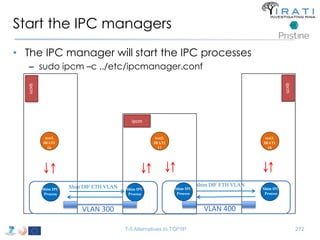
![ipcmanager.conf:
Specify the (shim) IPC processes
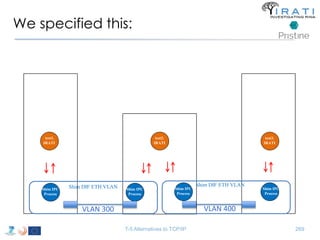
• "ipcProcessesToCreate“
– "apName" : "test-eth-vlan“
– "apInstance" : "1“
– "difName" : “300“
– "apName" : "test1.IRATI“
– "apInstance" : "1”
– "difName" : "normal.DIF"
– "difsToRegisterAt" : [“300"]
• "ipcProcessesToCreate“
– "apName" : "test-eth-vlan4“
– "apInstance" : "1“
– "difName" : “400“
– "apName" : "test3.IRATI“
– "apInstance" : "1”
– "difName" : "normal.DIF"
– "difsToRegisterAt" : [“400"]
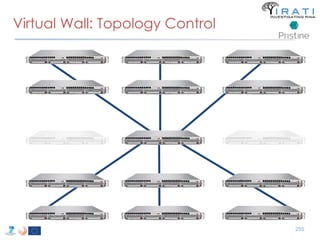
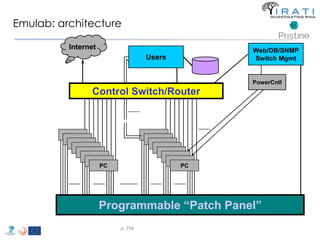
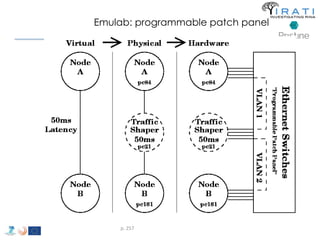
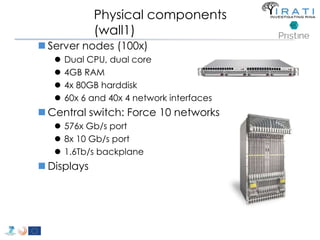
T-5 Alternatives to TCP/IP 266](https://image.slidesharecdn.com/tutorial-5-slides-globecom-2014-141216030720-conversion-gate02/85/RINA-Tutorial-IEEE-Globecom-2014-266-320.jpg)
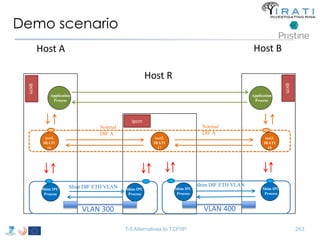
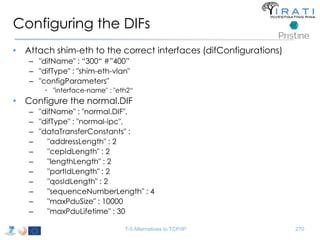
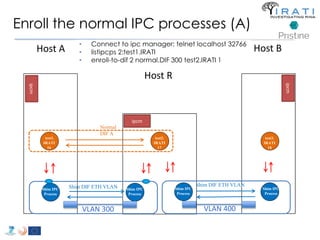
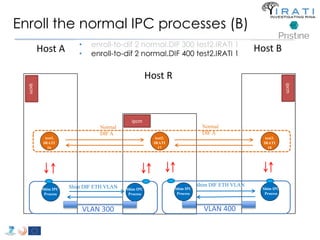
![Configure the (shim) IPC processes
Host R
• "ipcProcessesToCreate"
– "apName" : "test-eth-vlan“
– "apInstance" : "1“
– "difName" : “300"
– "apName" : "test-eth-vlan2“
– "apInstance" : "1“
– "difName" : “400" }
– "apName" : "test2.IRATI“
– "apInstance" : "1“
– "difName" : "normal.DIF“
– "difsToRegisterAt" : [“300", “400"]
T-5 Alternatives to TCP/IP 268](https://image.slidesharecdn.com/tutorial-5-slides-globecom-2014-141216030720-conversion-gate02/85/RINA-Tutorial-IEEE-Globecom-2014-268-320.jpg)
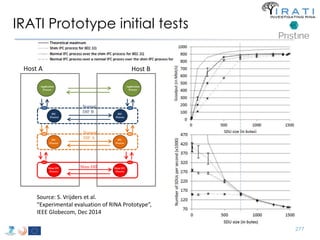
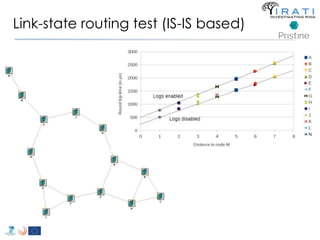
![Future plans
• IRINA [03/2015]
– Use case analysis of RINA as the future NREN and GEANT
architecture
– Experimental analysis using Open IRATI prototype
– Contribution of traffic generation tools to Open IRATI
• PRISTINE [06/2016]
– Research on RINA in the areas of congestion control,
distributed resource allocation, addressing and routing,
security, resiliency and network management.
– Software Development Kit for Open IRATI
– Policies developed with the SDK for Open IRATI
– Network Management System for Open IRATI
– First RINA Simulator (based on OMNeT++)
T-5 Alternatives to TCP/IP 279](https://image.slidesharecdn.com/tutorial-5-slides-globecom-2014-141216030720-conversion-gate02/85/RINA-Tutorial-IEEE-Globecom-2014-279-320.jpg)
