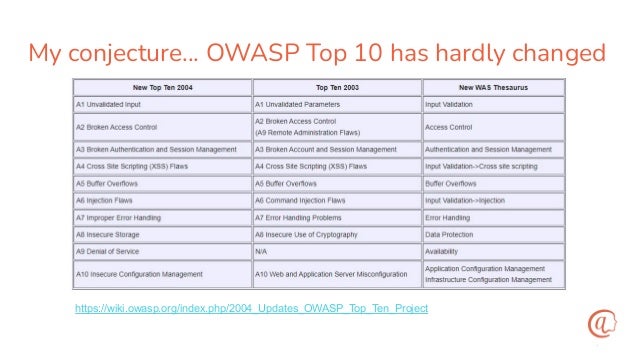
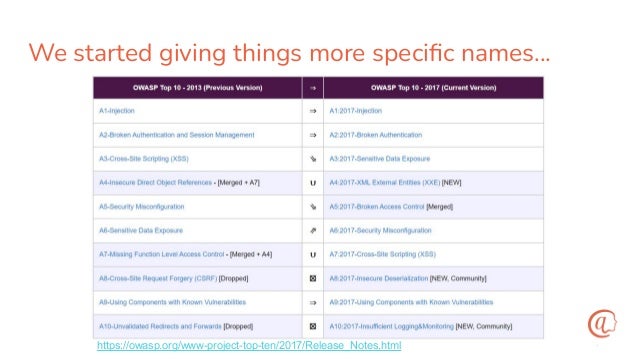
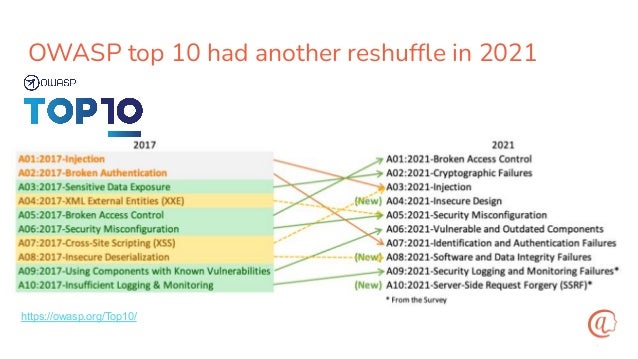
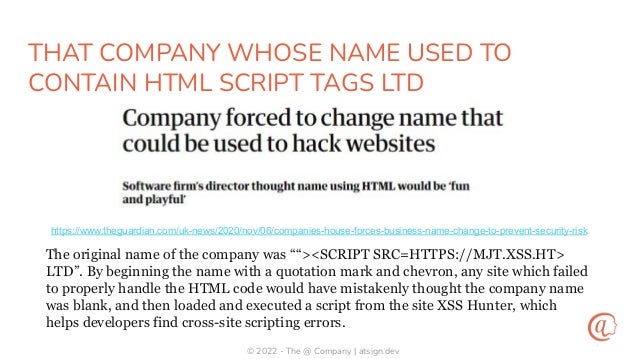
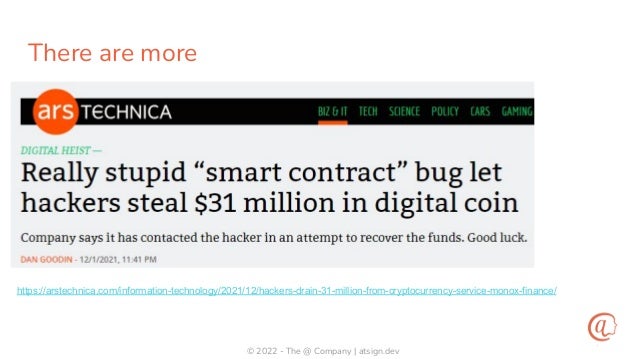
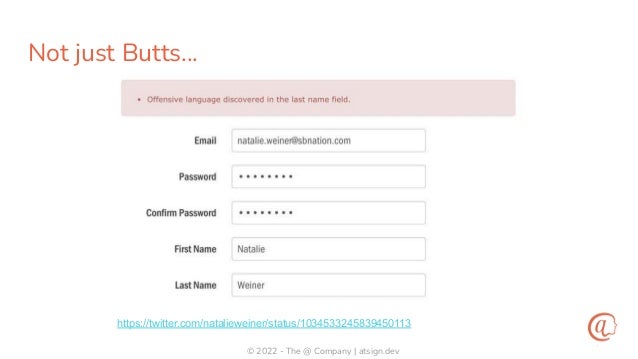
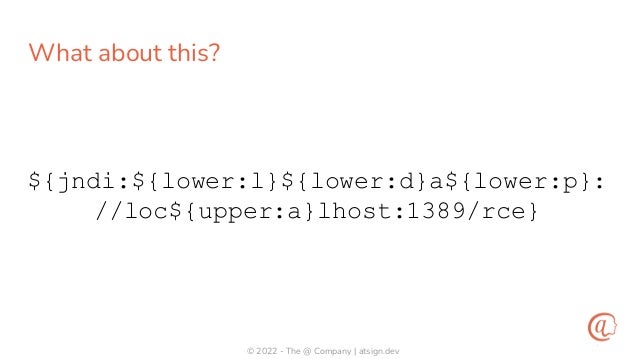
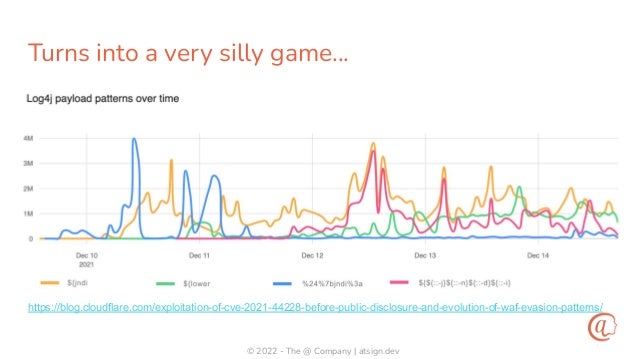
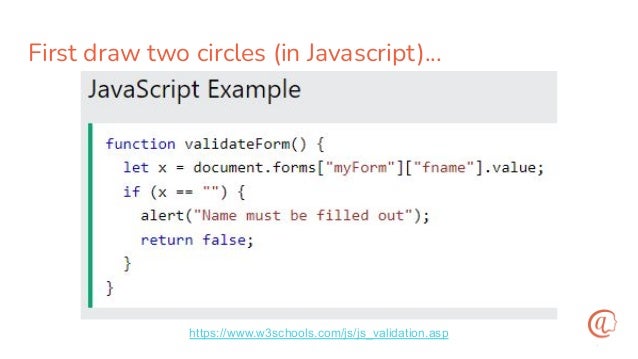
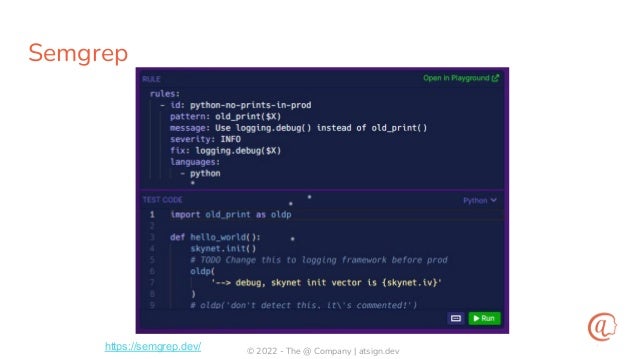
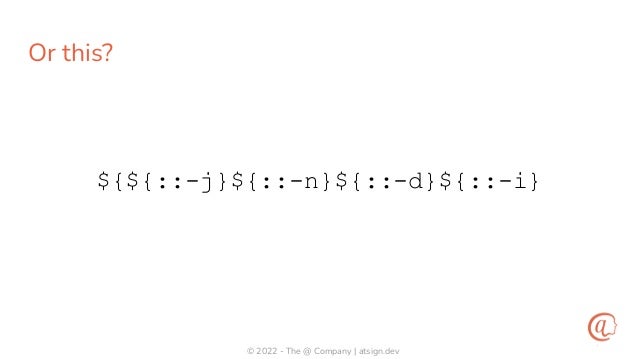The document discusses the importance of input validation in application security, proposing that it should be inherently integrated into programming languages to prevent injection vulnerabilities. It highlights that these vulnerabilities persist in the OWASP Top 10 list, suggesting that a more robust approach to input validation could significantly enhance security by 2030. The author emphasizes the need for better developer experience and tools to support secure coding practices.