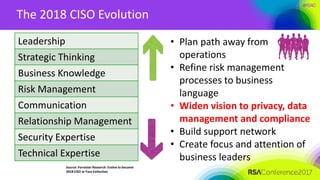
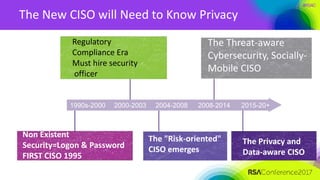
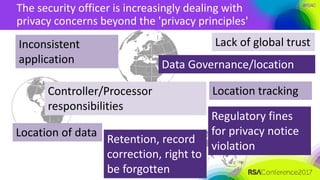
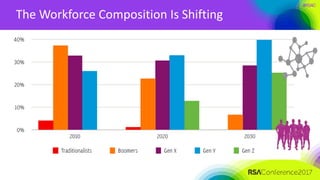
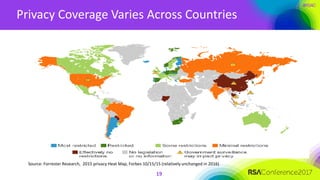
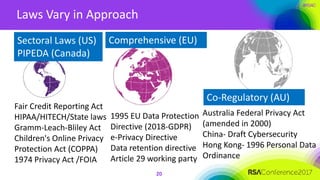
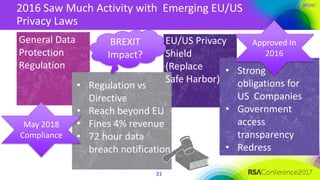
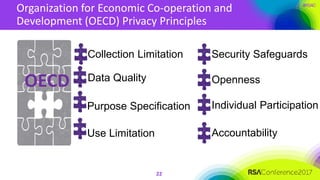
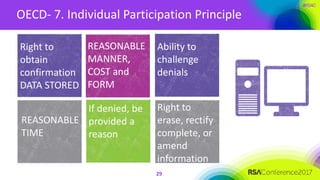
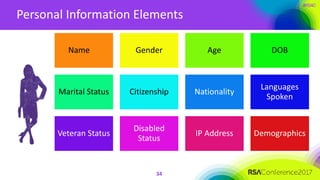
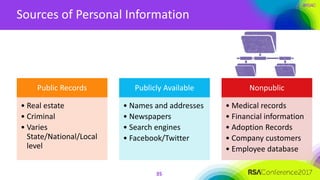
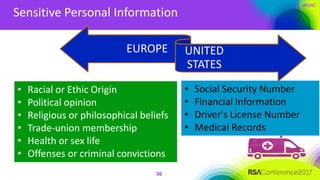
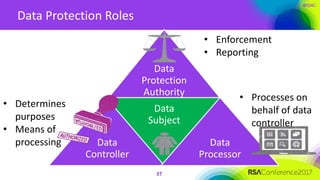
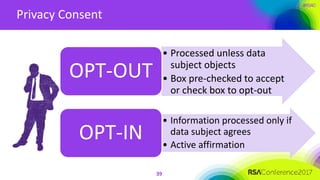
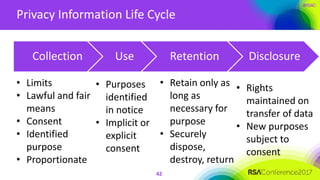
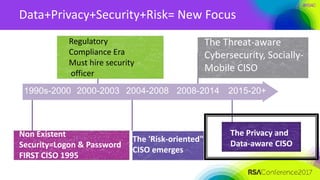
The document outlines a job description for a senior information security position, emphasizing the need for strong knowledge in information security practices, privacy regulation, and risk management. It details the responsibilities, including managing security programs, conducting risk assessments, ensuring compliance, and training staff. Additionally, it discusses the evolving role of the CISO in relation to privacy concerns and the importance of communication and collaboration across departments.