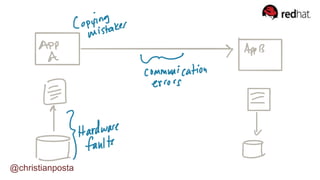
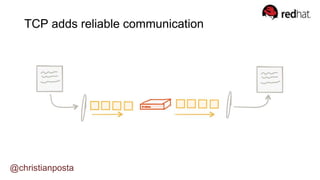
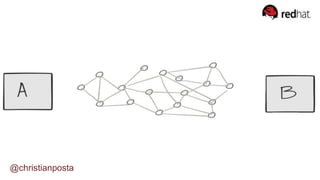
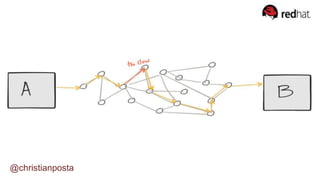
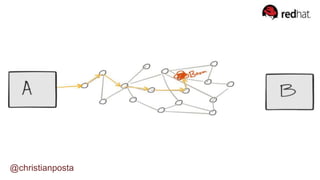
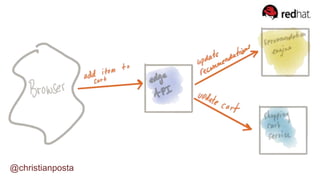
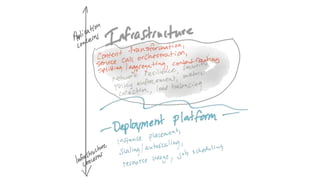
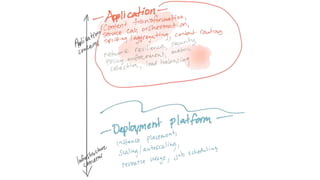
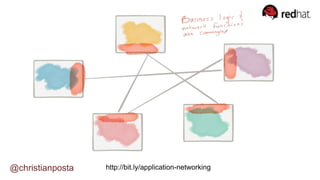
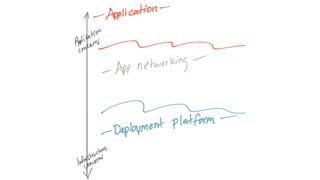
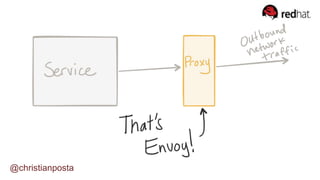
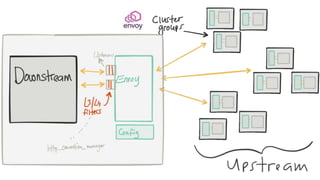
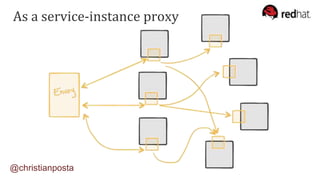
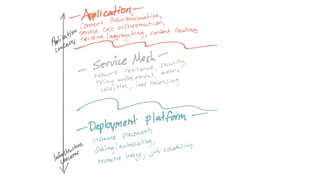
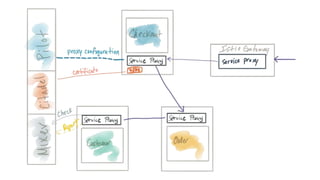
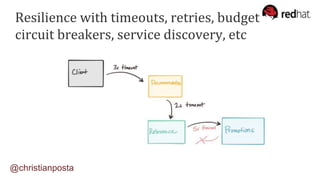
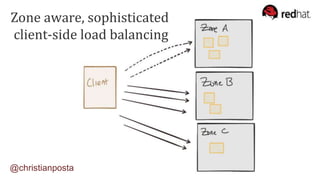
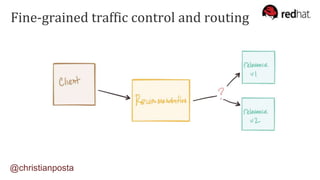
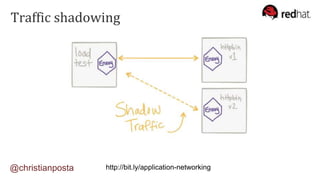
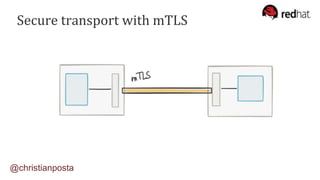
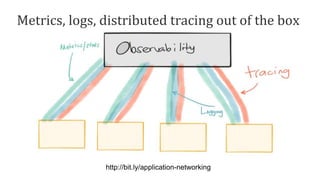
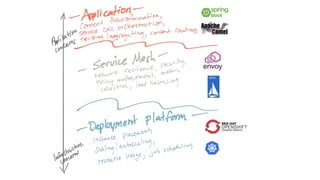
The document discusses the evolution of integration and microservice patterns within a service mesh, emphasizing the complexity of distributed systems and the importance of application safety and correctness. It introduces tools like Envoy and Istio for managing microservices communication, including features like service discovery, load balancing, and traffic management. The content highlights how service meshes offer resiliency, security, observability, and routing control, aiming to improve application networking infrastructure.