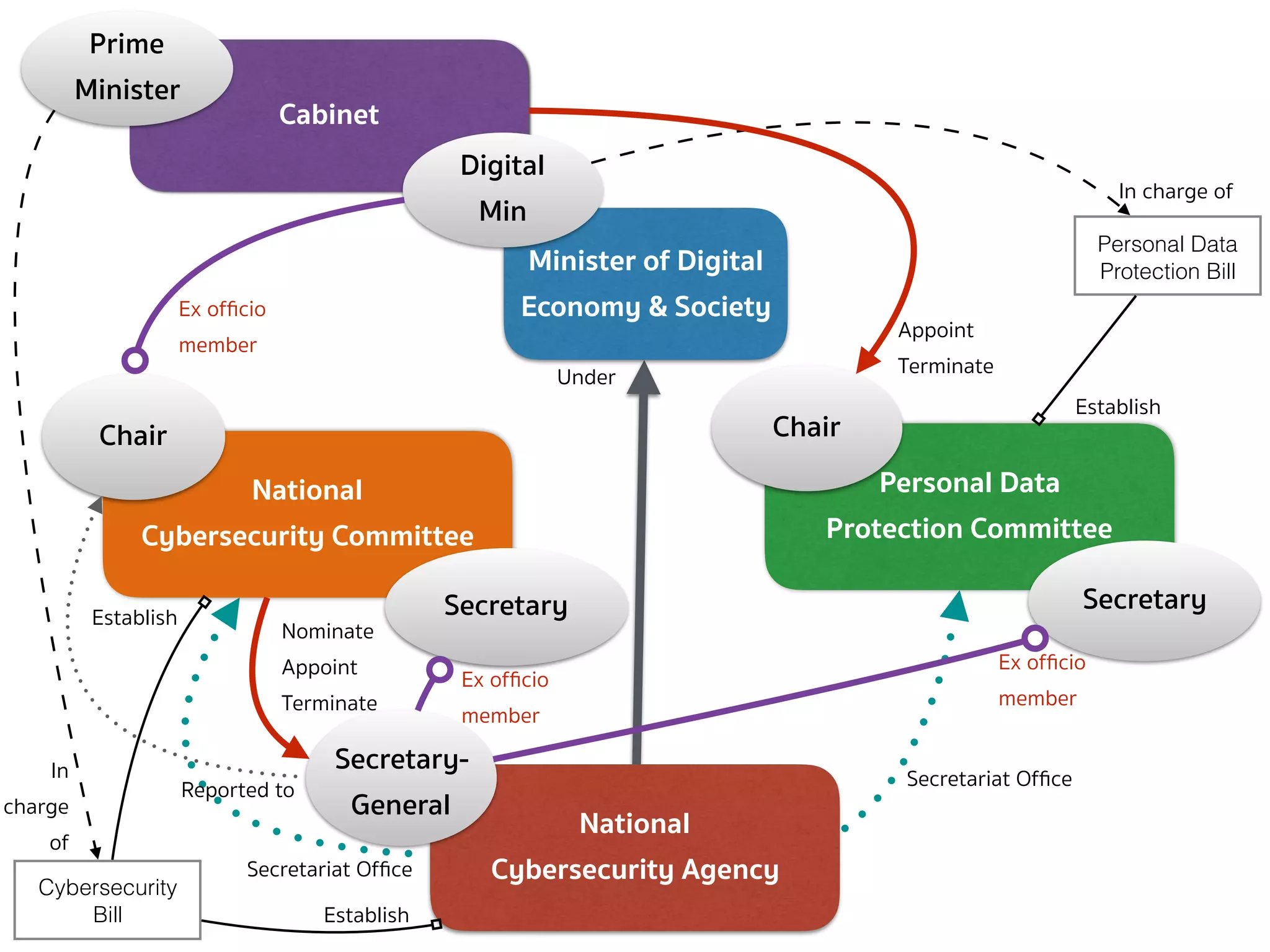
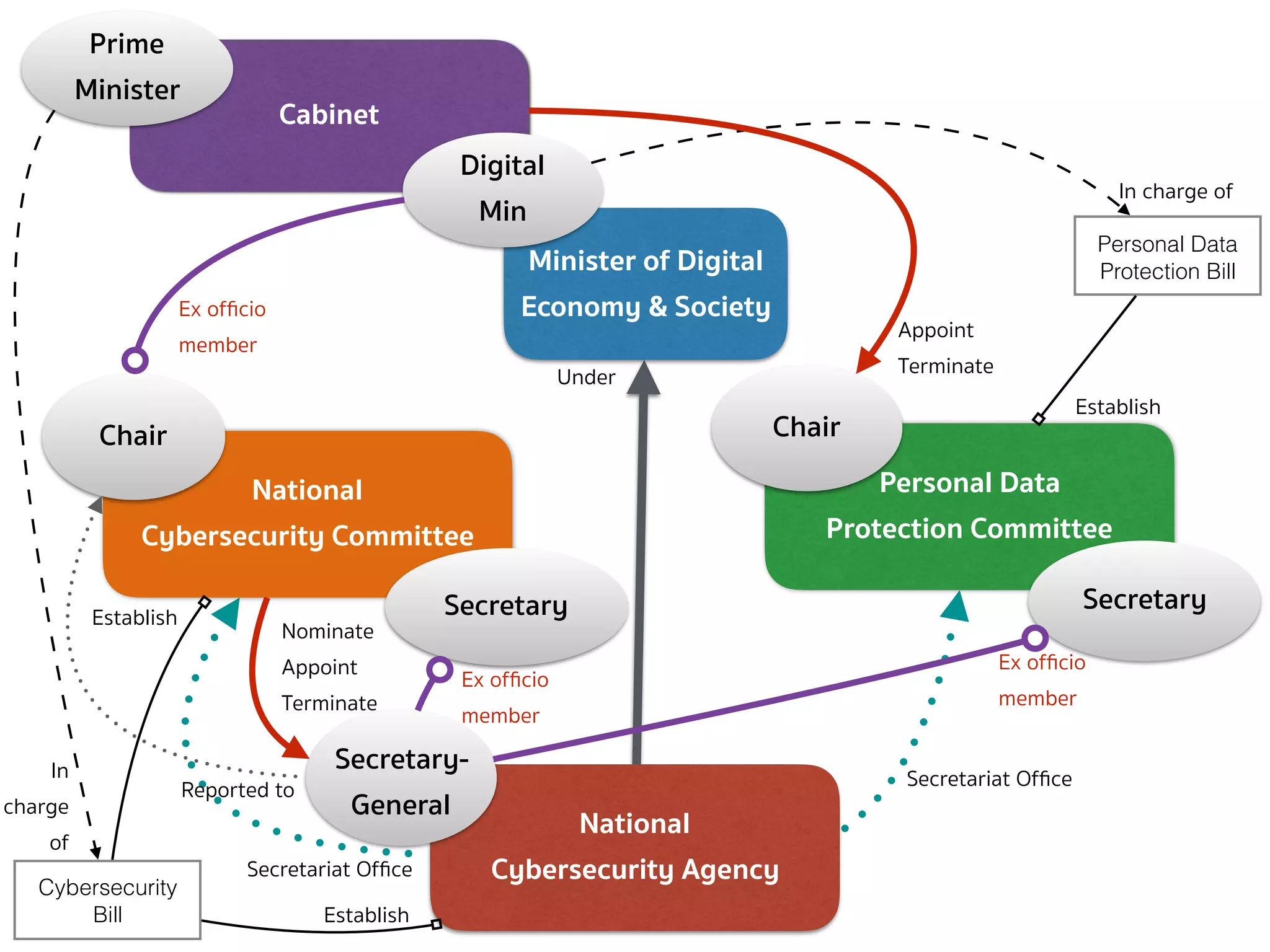
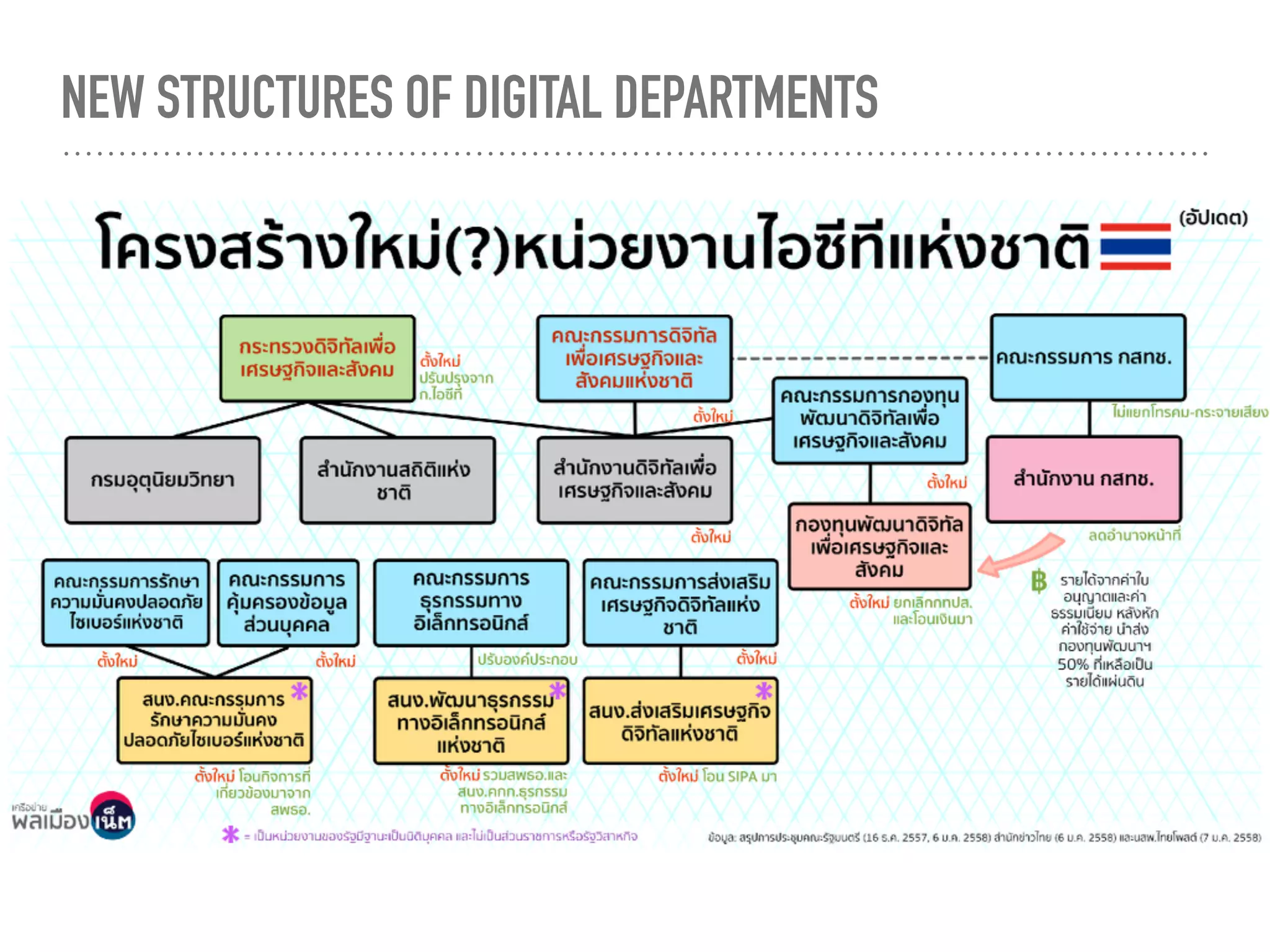
The document provides an in-depth overview of stakeholder mapping and cyber policy development in Thailand, focusing on the roles and relationships among various entities such as the personal data protection committee and the national cybersecurity agency. It highlights several cases of digital regulation, including amendments to the computer-related crime act and online media regulation post-2014 coup. There is a critical analysis of the structural dynamics that may lead to conflicts and inefficiencies in data protection and cybersecurity governance.



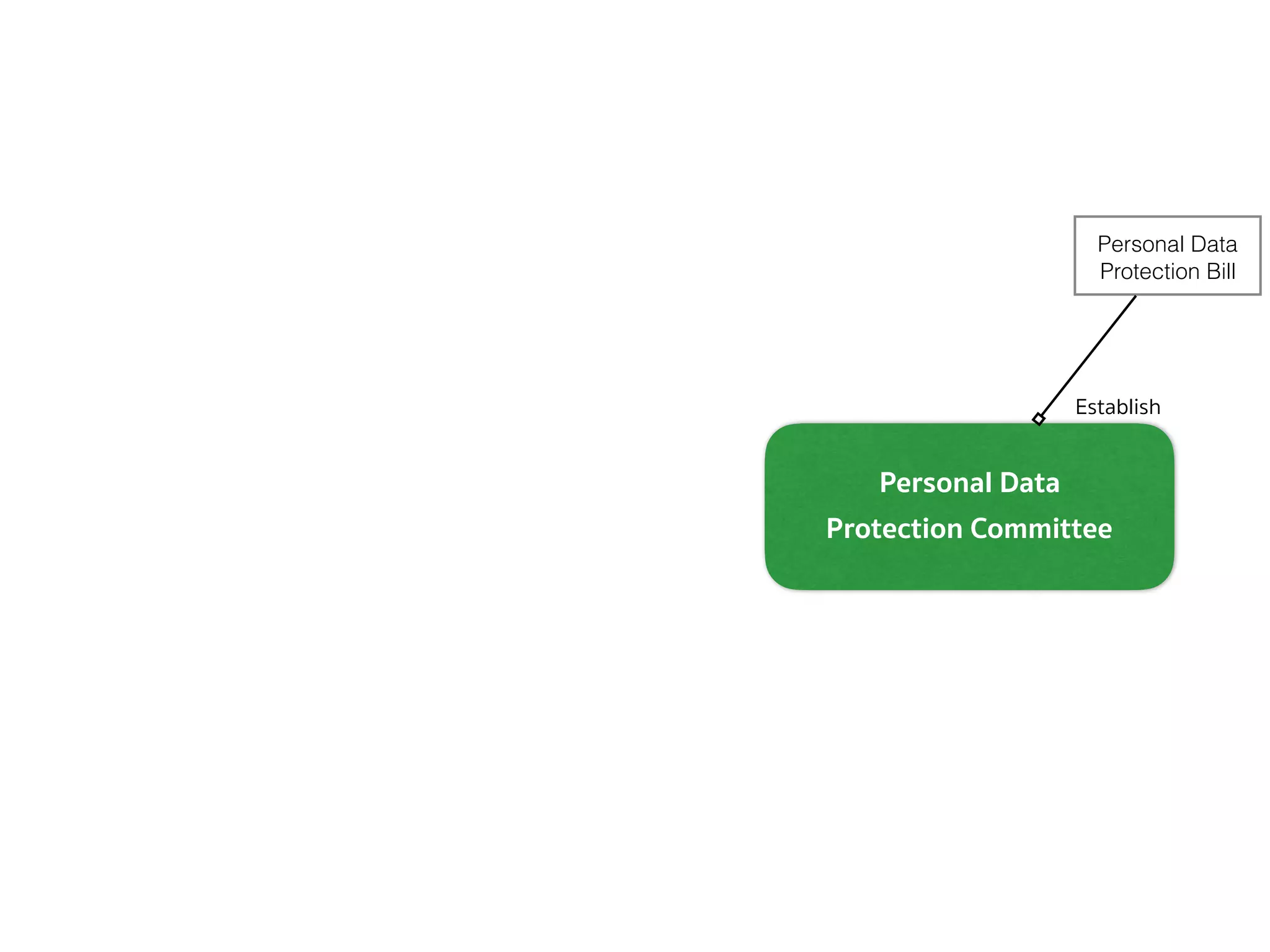
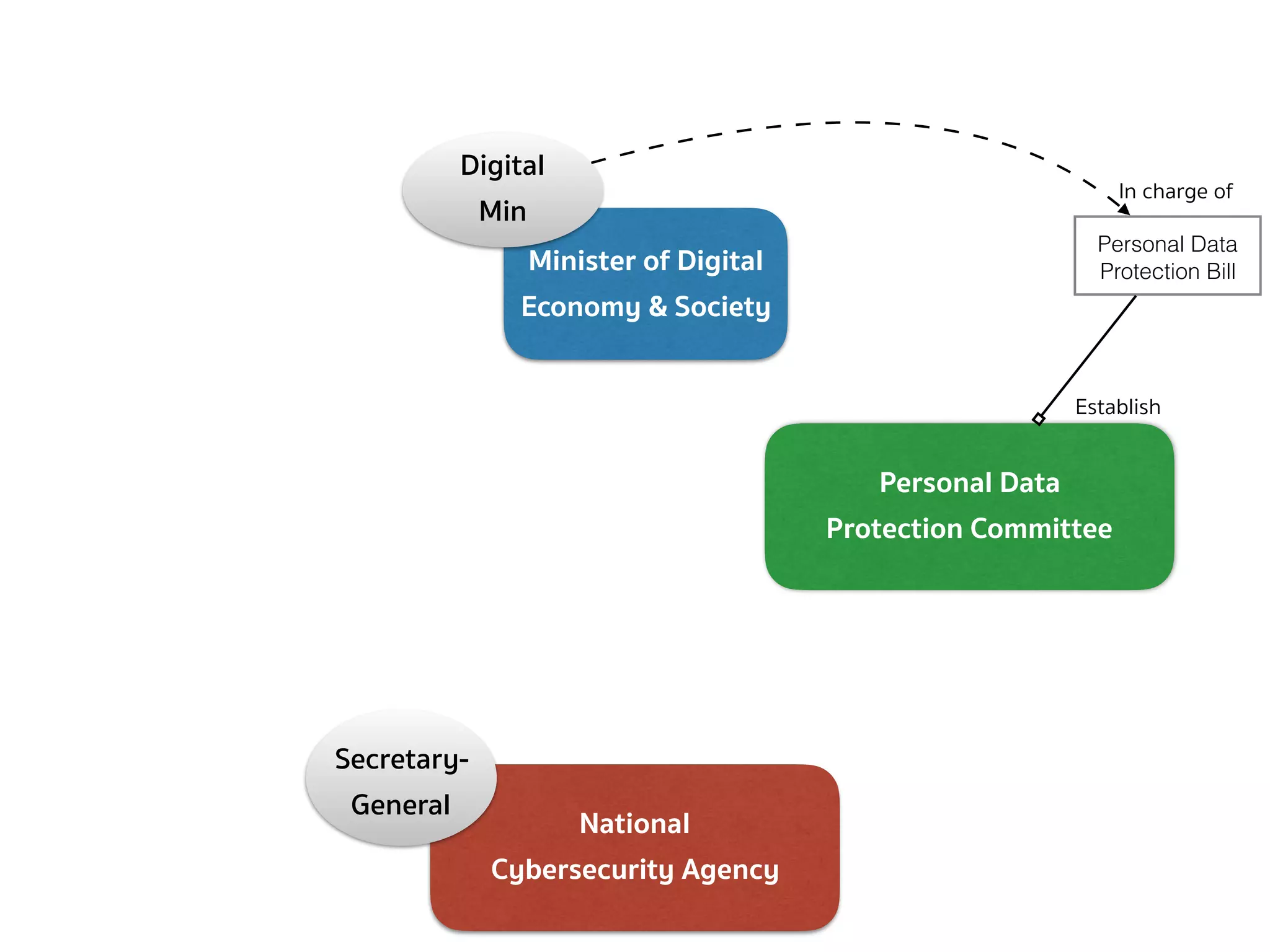
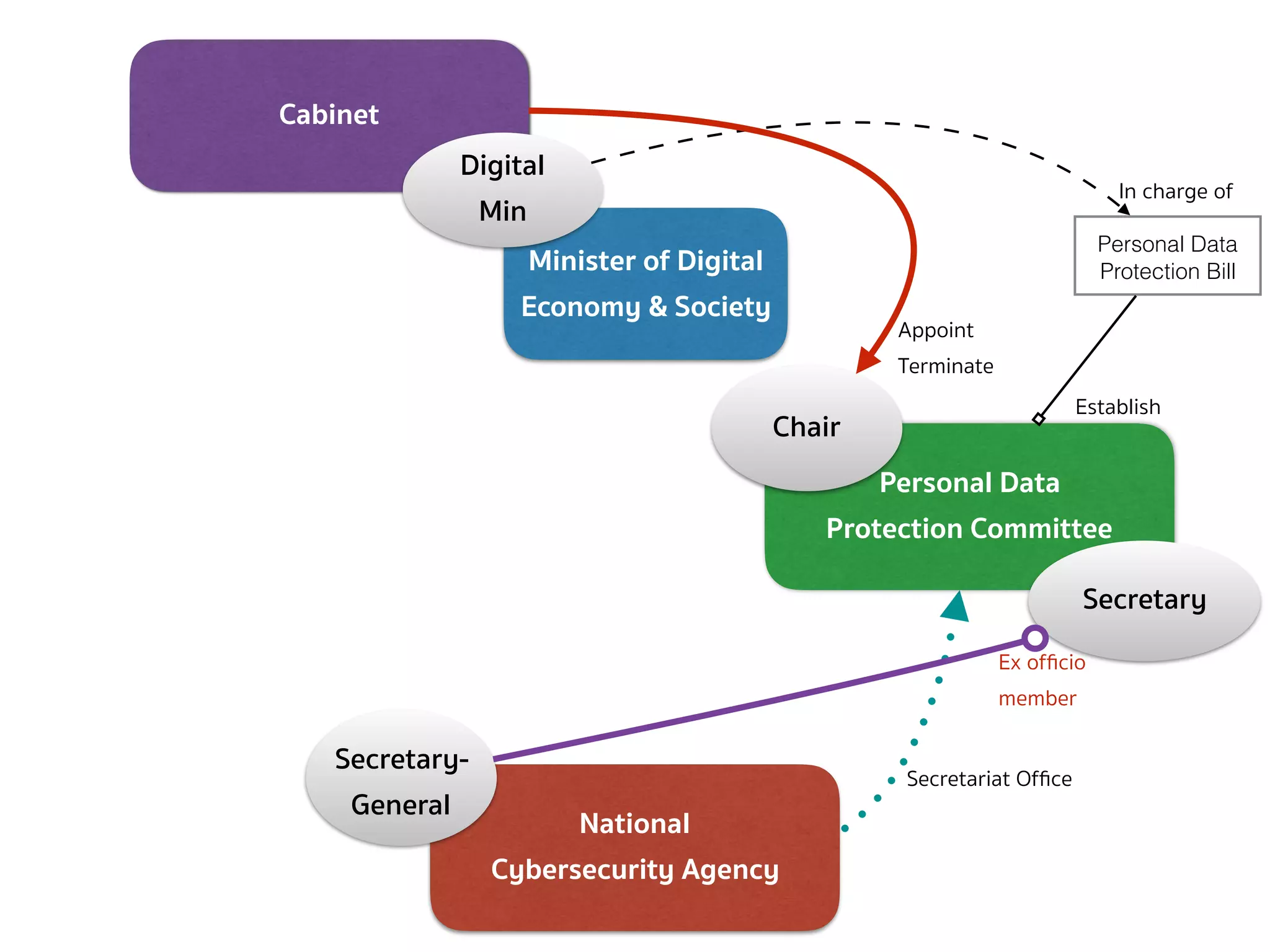
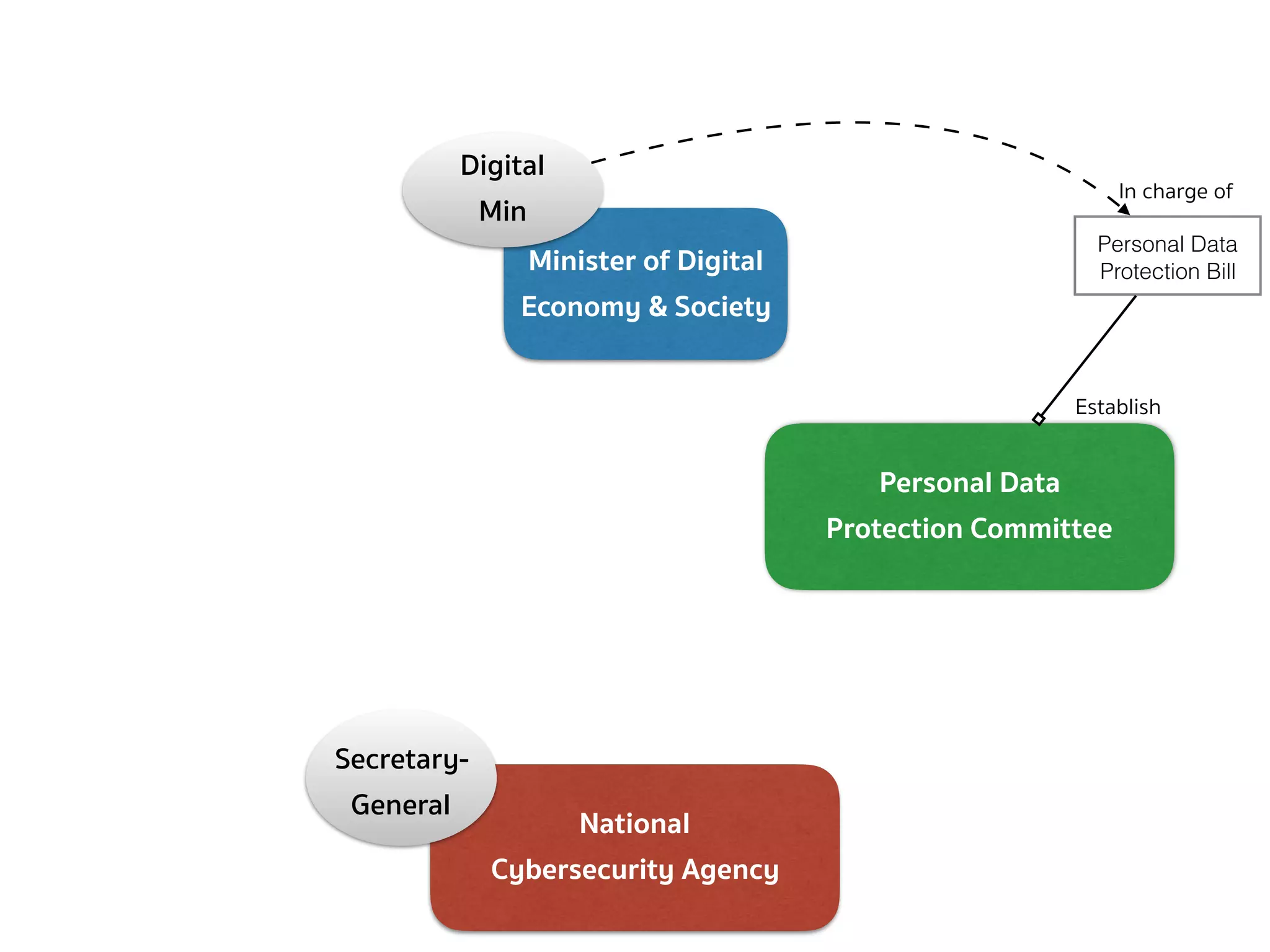
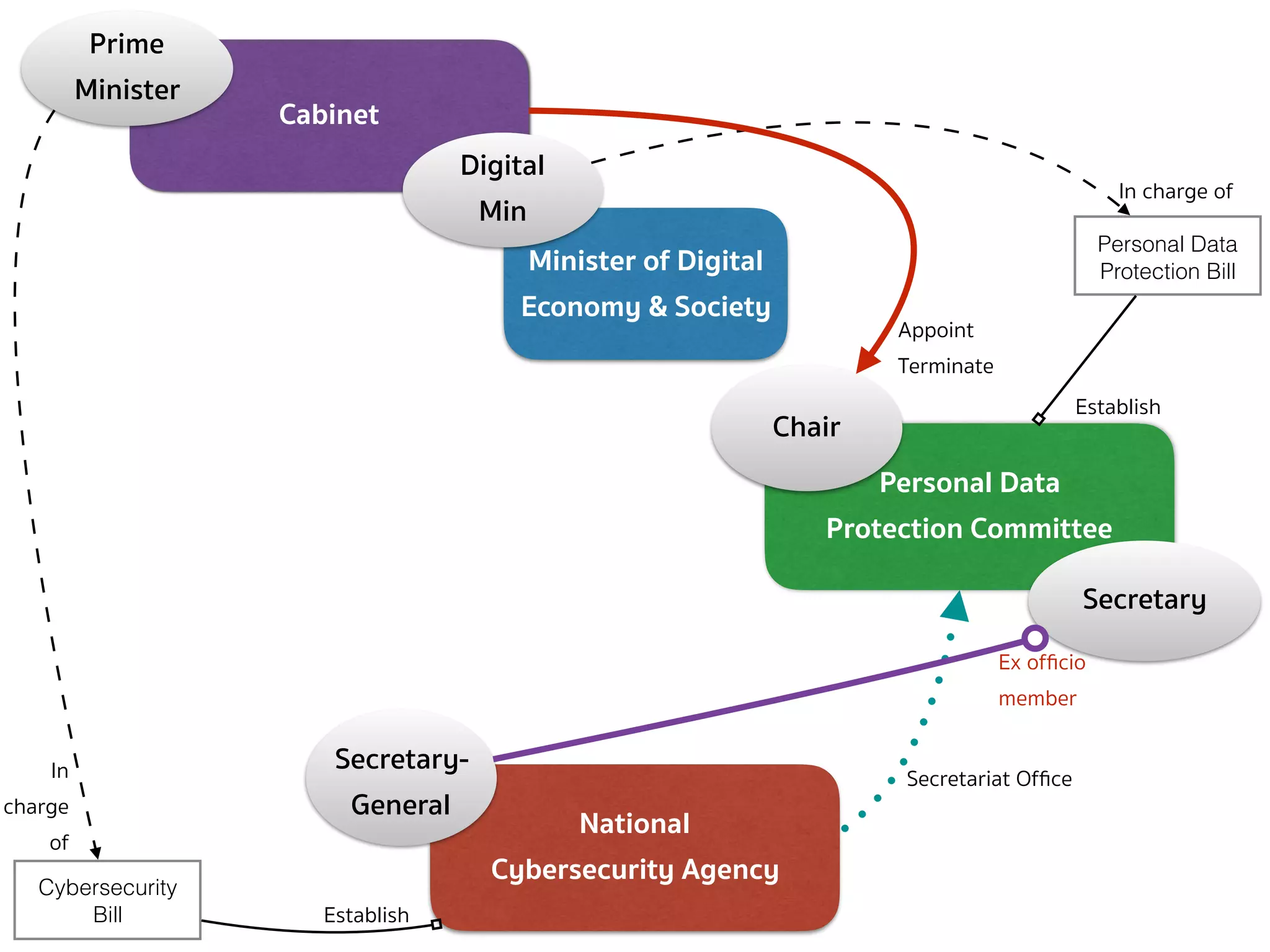
![PERSONAL DATA PROTECTION BILL (DEFINITION — SEC.5, 6)
➤ Section 5 — In this Act, […]
➤ “Committee” means the Personal Data Protection Committee;
➤ “Office” means the National Cybersecurity Agency;
➤ “Secretary-General” means the Secretary-General of the National
Cybersecurity Agency;
➤ “Minister” means the minister having the charge and control of
the execution of this Act.
➤ Section 6 — The Minister of Digital Economy and Society shall
have the charge and control of the execution of this Act.](https://image.slidesharecdn.com/mapping-stakeholders-arthit-netizen-nlu-delhi-20170410-170410134602/75/Mapping-Stakeholders-Decision-makers-and-Implementers-in-Thailand-s-Cyber-Policy-6-2048.jpg)
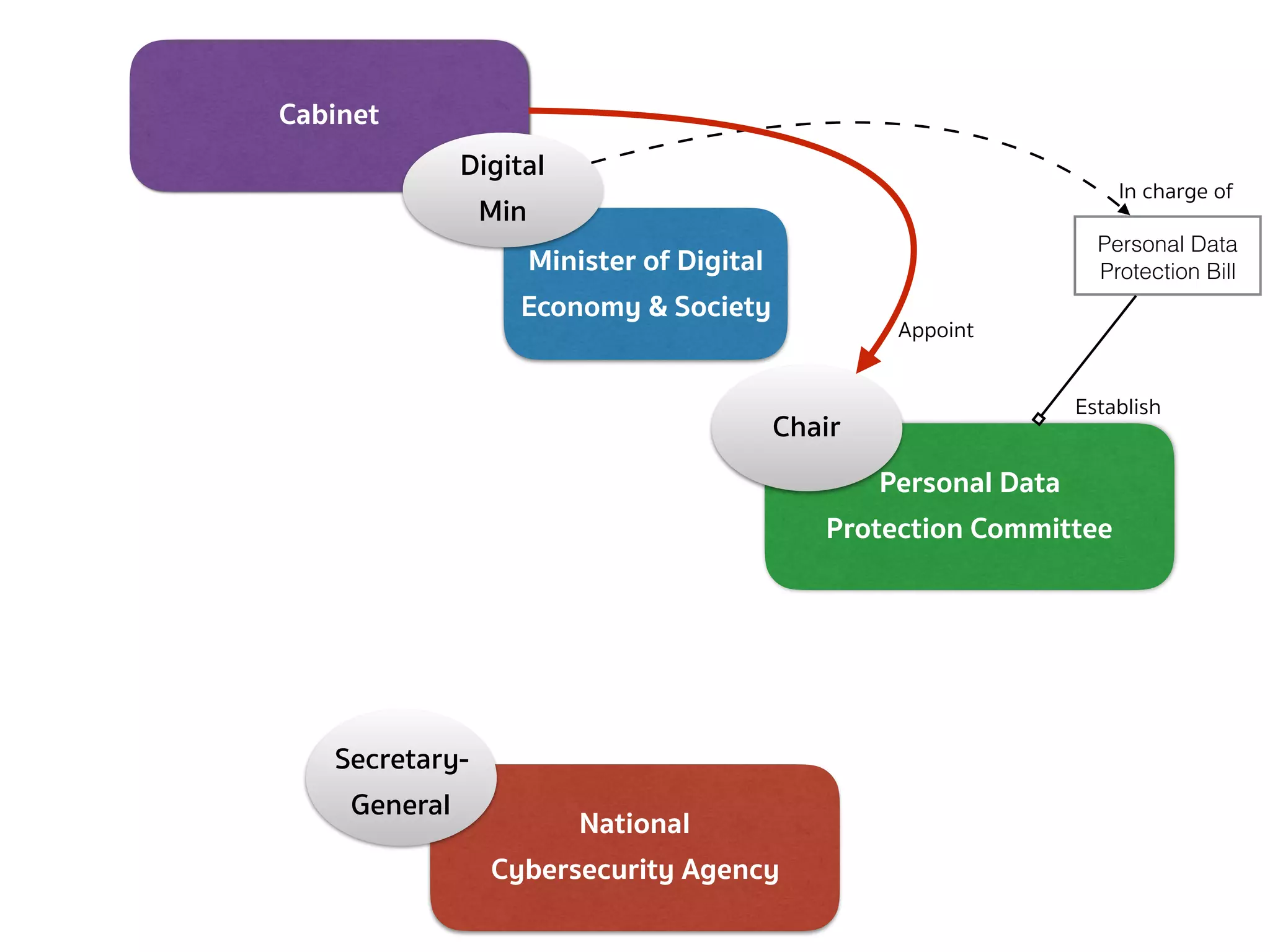
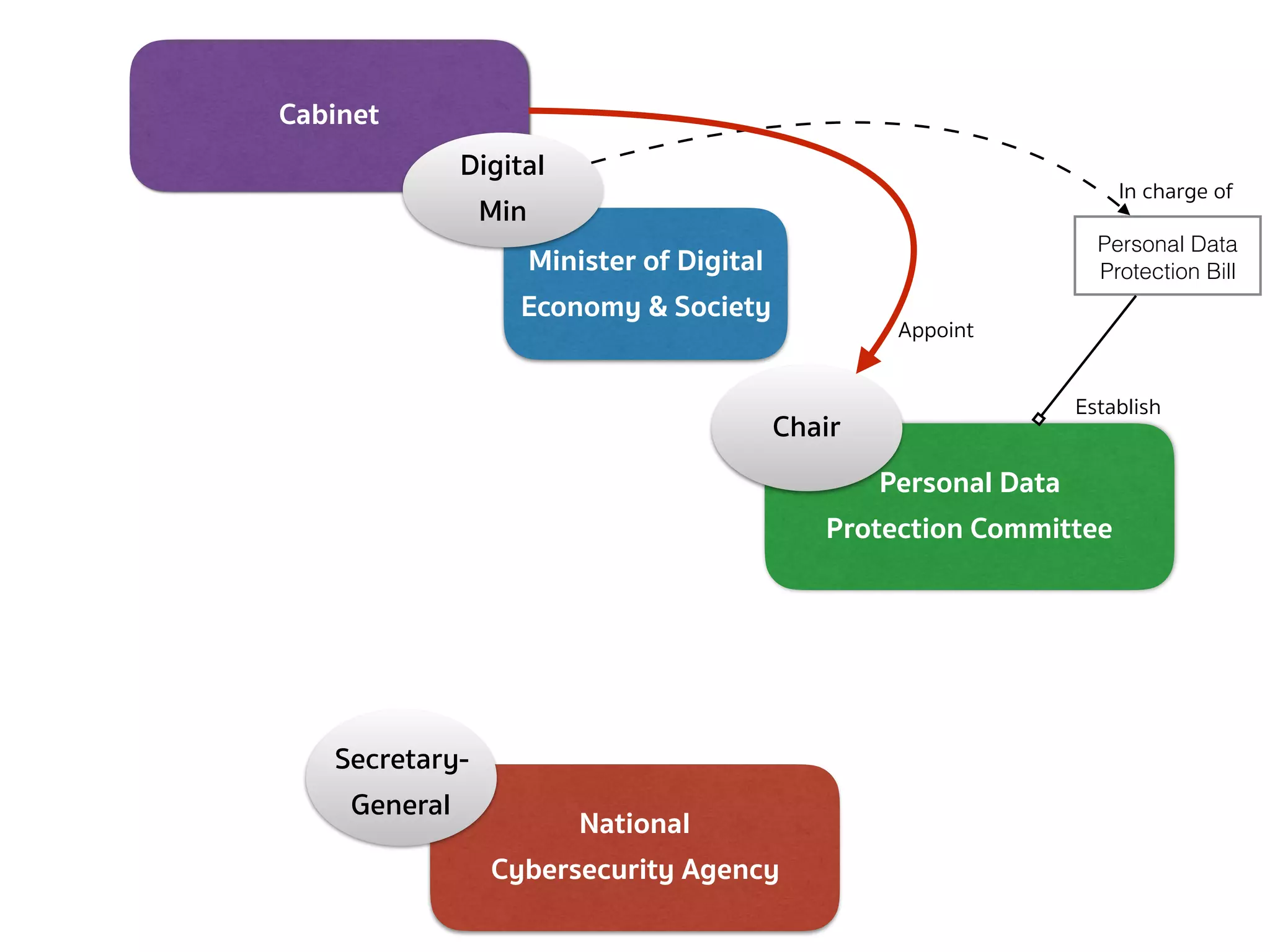
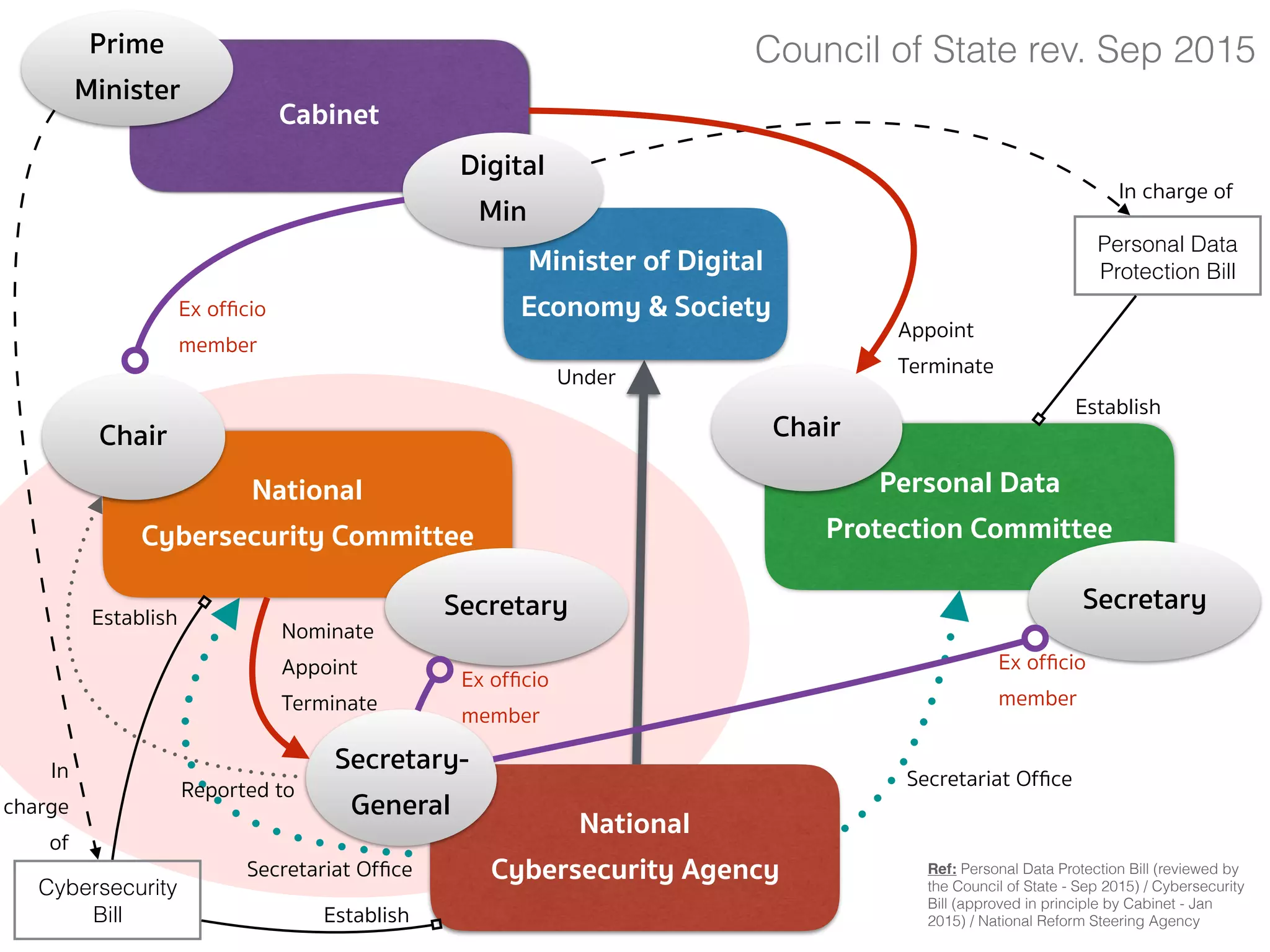
![PERSONAL DATA PROTECTION BILL (COMMITTEE — SEC.7)
➤ Section 7 — There shall be a committee called “Personal Data
Protection Committee”, consisting of:
➤ (1) a Chairperson appointed by the Cabinet from the persons having
distinguished knowledge, skills, and experience in the field of
personal data protection, or information and communication
technology, or any other field that is relevant and useful for the
protection of personal data;
➤ (2) 4 ex officio members consisting of the Permanent Secretary of the Office
of the Prime Minister, the Permanent Secretary of the Ministry of Digital
Economy and Society, the Permanent Secretary of the Ministry of Interior, and
the Secretary-General of the National Security Council;
➤ (3) not more than 4 qualified members, appointed by the Cabinet
[…]](https://image.slidesharecdn.com/mapping-stakeholders-arthit-netizen-nlu-delhi-20170410-170410134602/75/Mapping-Stakeholders-Decision-makers-and-Implementers-in-Thailand-s-Cyber-Policy-8-2048.jpg)
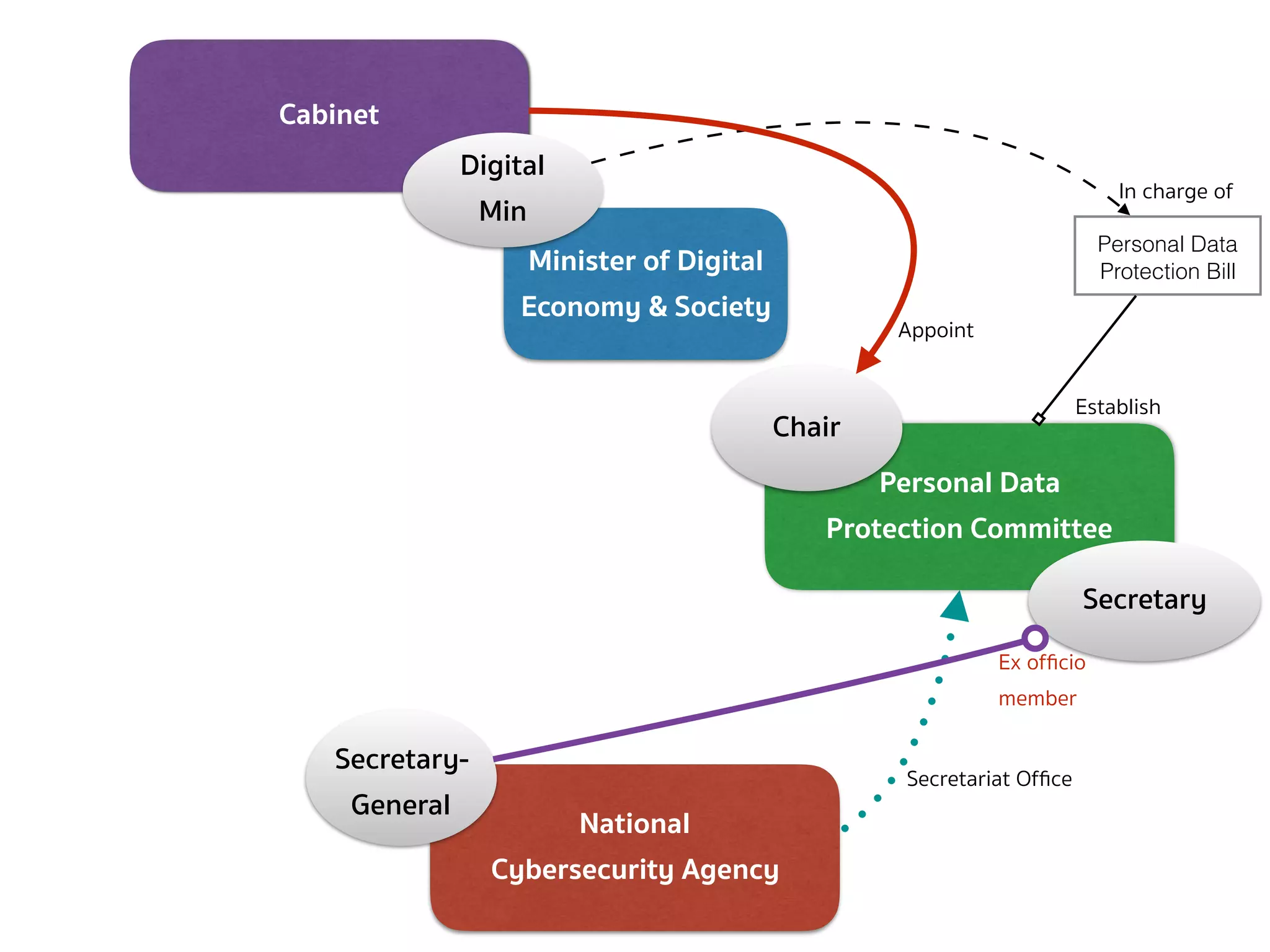
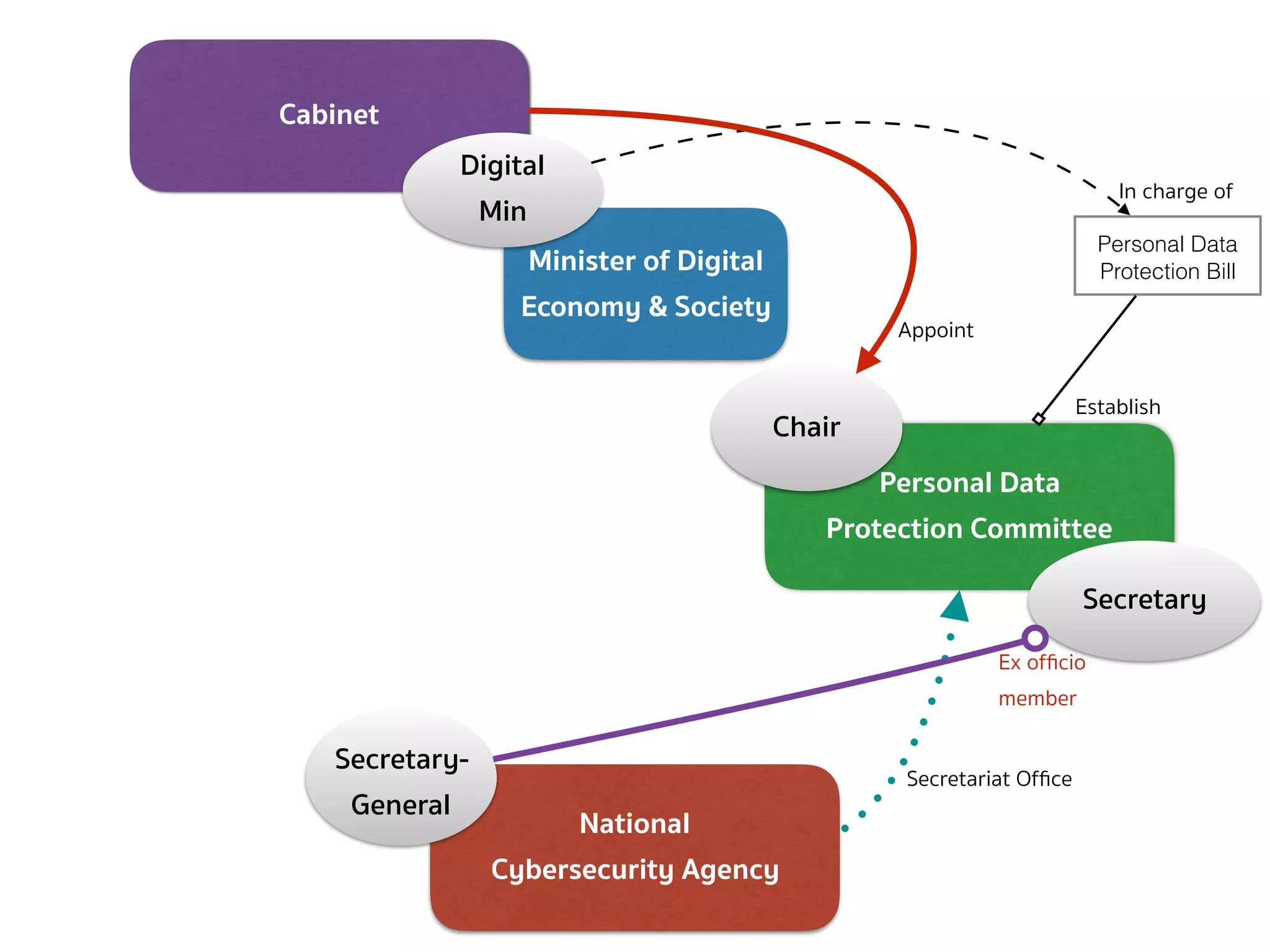
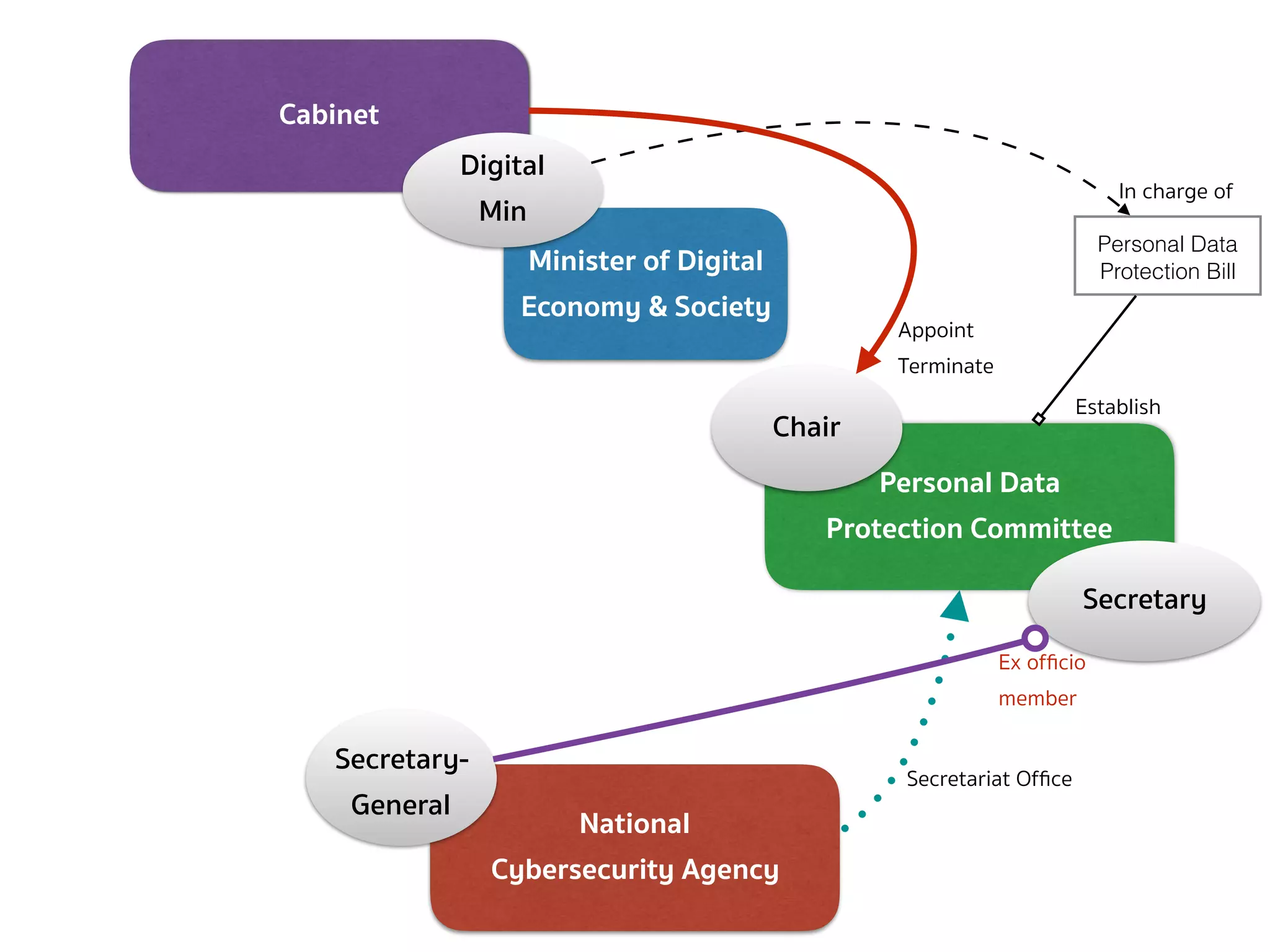
![PERSONAL DATA PROTECTION BILL (COMMITTEE — SEC.7 CONT.)
➤ The Secretary-General shall ex officio be member and secretary and
shall have the power to appoint assistant secretary as deemed
necessary.
➤ The rules and procedures on the selection of persons to be
appointed as Chairman and qualified members, including the
selection of persons to replace the qualified members who
vacate office before the expiration of the term under section
10, shall be as prescribed by the Rules issued by the Minister.
➤ The Office shall perform the duties as the secretariat office for the
Committee established under this Act […]](https://image.slidesharecdn.com/mapping-stakeholders-arthit-netizen-nlu-delhi-20170410-170410134602/75/Mapping-Stakeholders-Decision-makers-and-Implementers-in-Thailand-s-Cyber-Policy-10-2048.jpg)


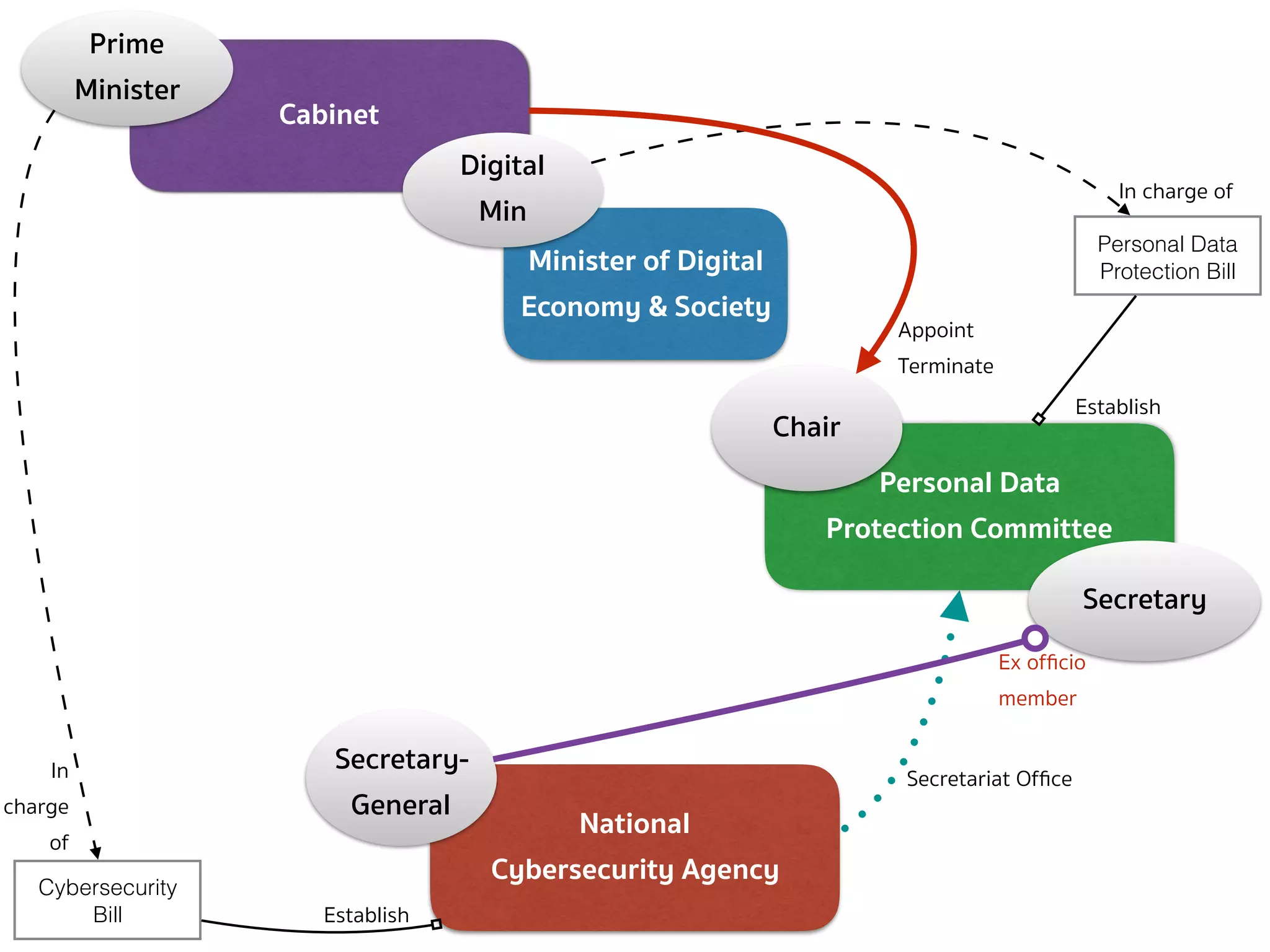

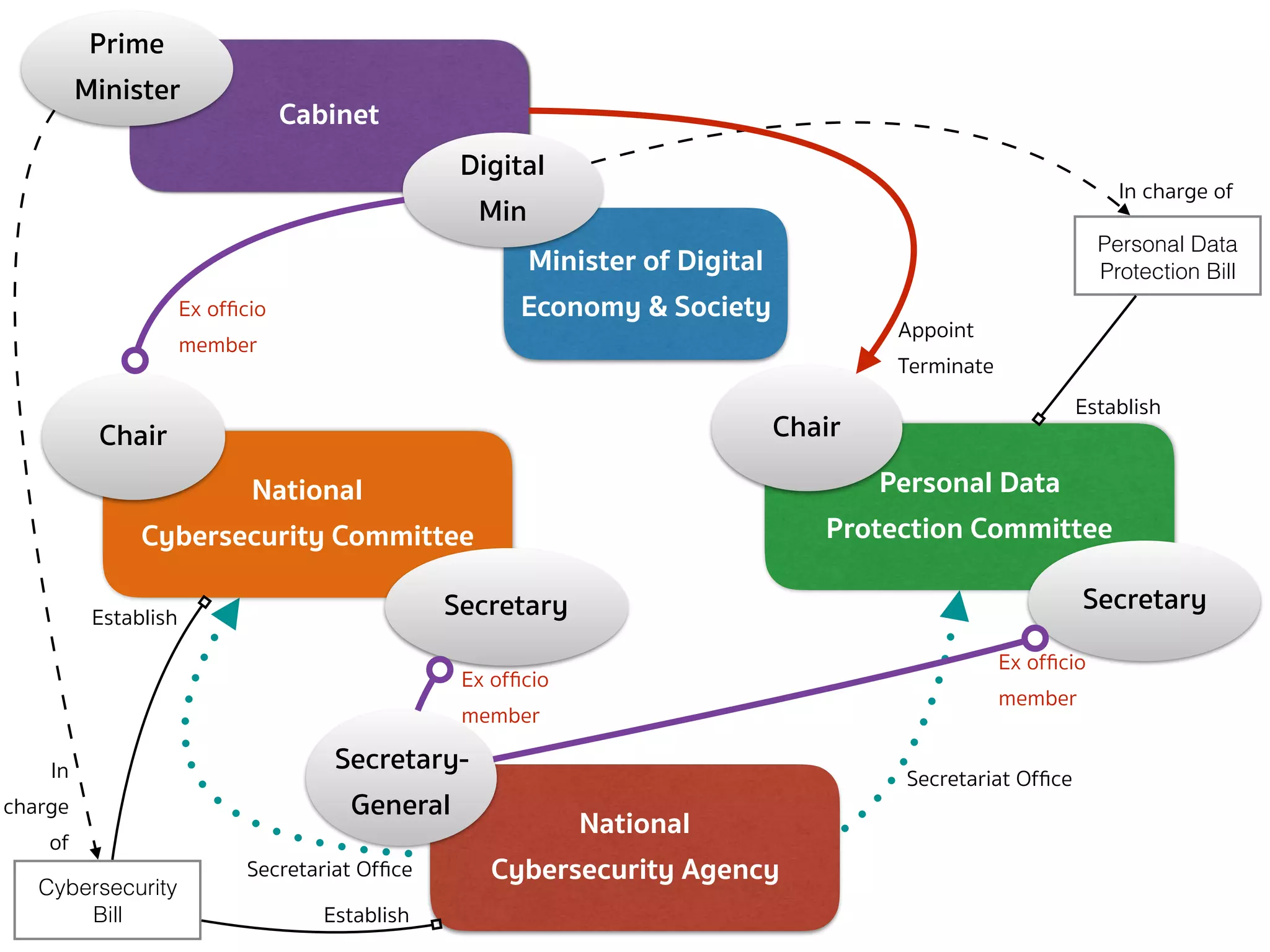
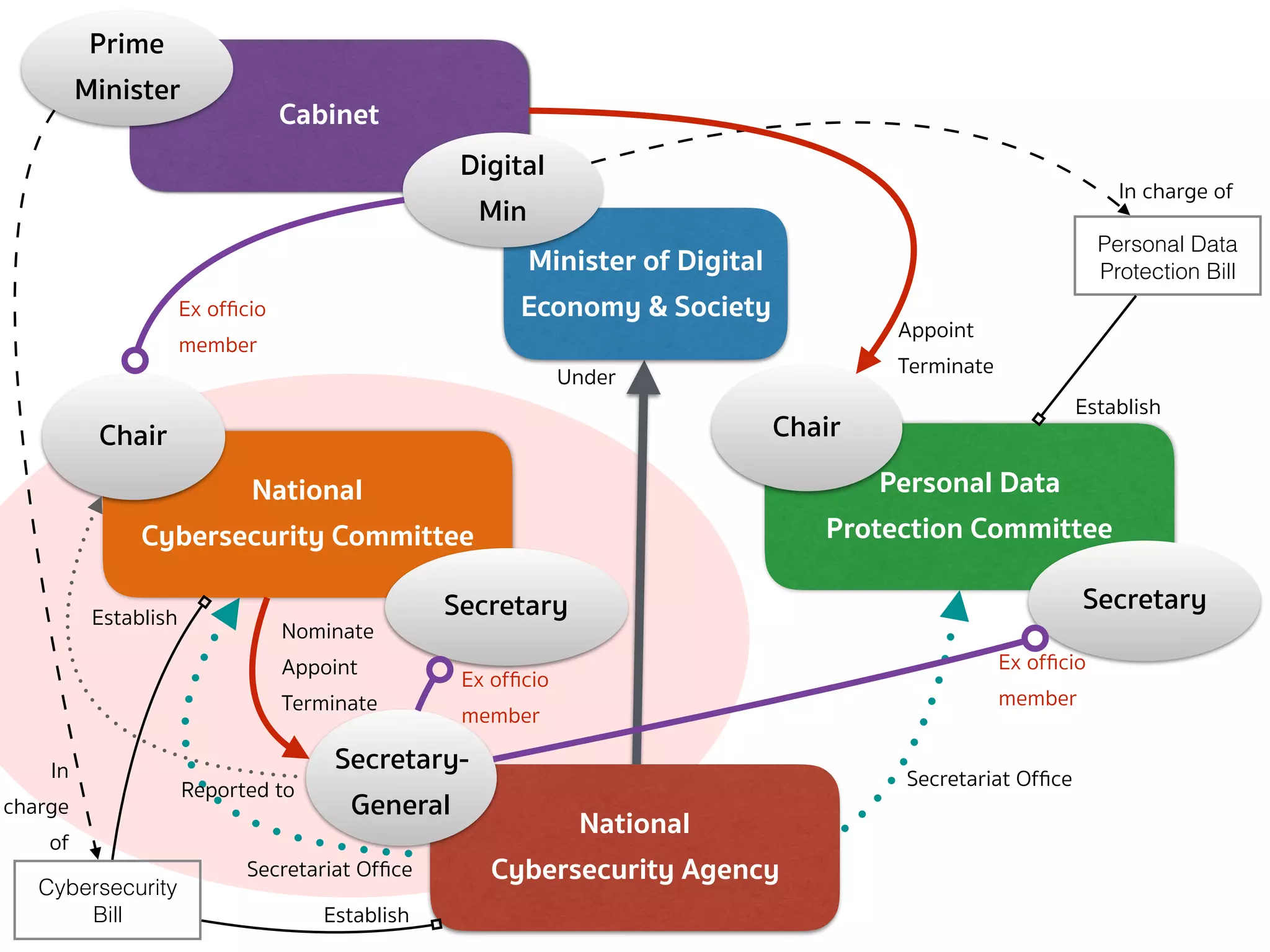
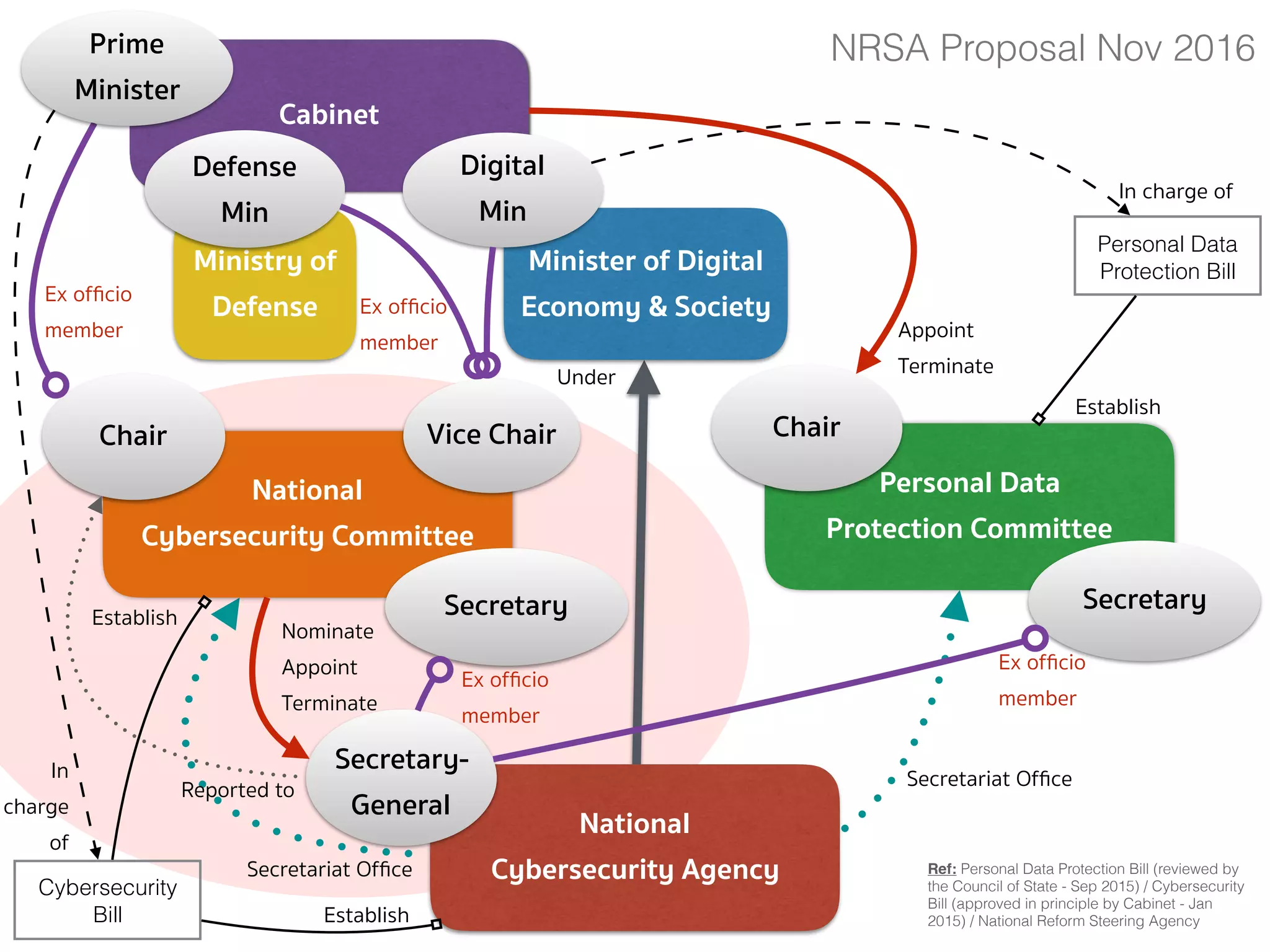
![CYBERSECURITY (COMMITTEE — SEC.6)
➤ Section 6 — There shall be a committee called the “National
Cybersecurity Committee” (NCSC) consisting of:
➤ (1) Minister of Digital Economy and Society as Chairperson;
➤ (2) Secretary-General of the National Security Council, Permanent Secretary
of the Ministry of Digital Economy and Society, Permanent Secretary of the
Ministry of Defense, Commander of the Technological Crime Suppression
Division of the Royal Thai Police as 4 ex officio members;
➤ (3) Not more than 7 qualified members appointed by the Cabinet […];
➤ The Secretary-General shall ex officio be member and secretary, and
assistant secretary shall be appointed as deemed necessary.
➤ The selection of the qualified members in paragraph 1 shall comply
with the Procedures specified by the Cabinet […]](https://image.slidesharecdn.com/mapping-stakeholders-arthit-netizen-nlu-delhi-20170410-170410134602/75/Mapping-Stakeholders-Decision-makers-and-Implementers-in-Thailand-s-Cyber-Policy-17-2048.jpg)

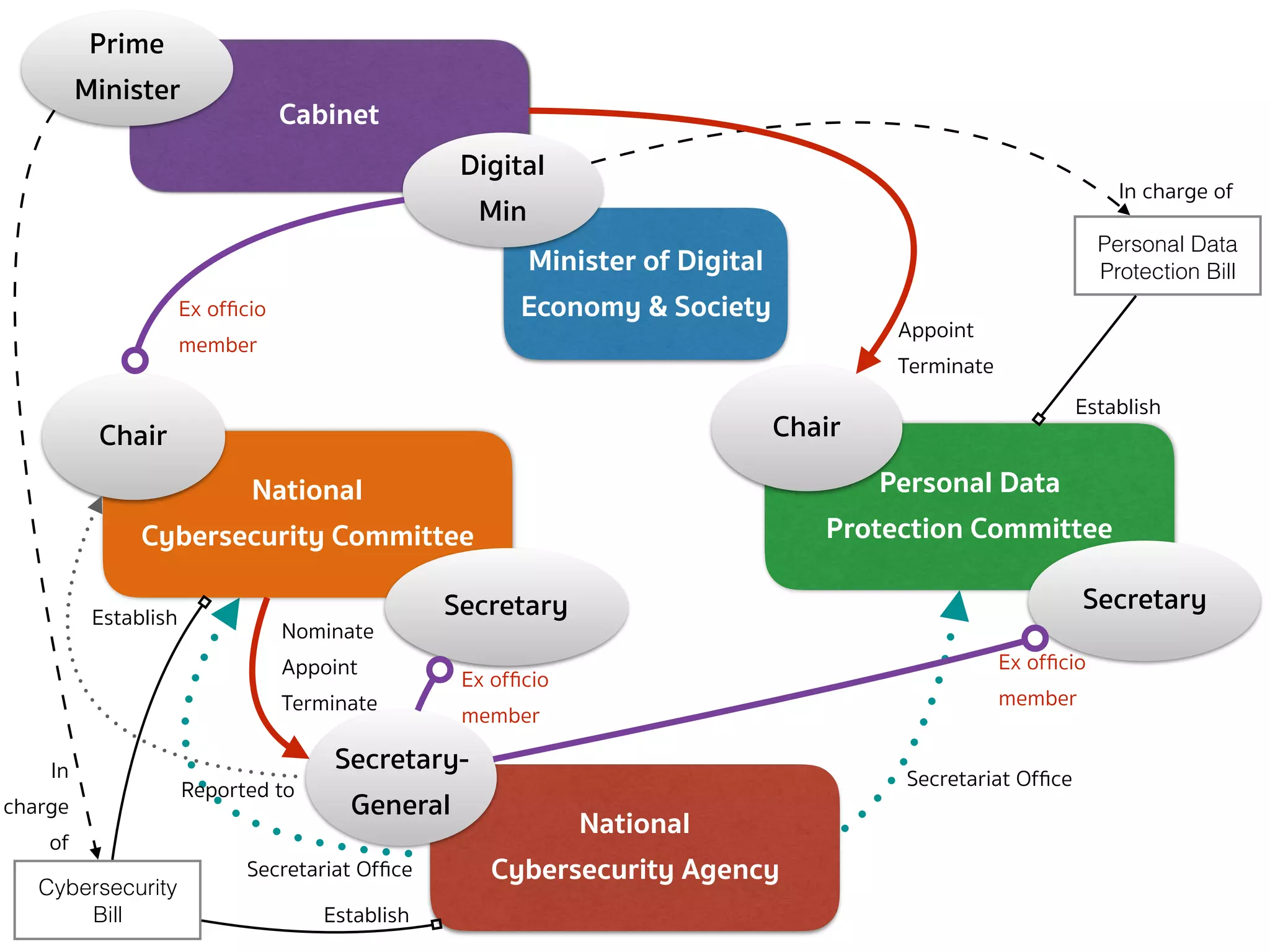
![CYBERSECURITY (SECRETARY-GENERAL — SEC.21)
➤ Section 21 — There shall be a Secretary-General who is directly
reported to the Chairperson of the NCSC as regards the operation
of the Office and supervises the Officials and employees of the
Office.
➤ As regards activities dealing with third parties, the Secretary-
General shall represent the Office. […]
➤ The Committee shall have the power to nominate, appoint and
remove the Secretary-General.](https://image.slidesharecdn.com/mapping-stakeholders-arthit-netizen-nlu-delhi-20170410-170410134602/75/Mapping-Stakeholders-Decision-makers-and-Implementers-in-Thailand-s-Cyber-Policy-19-2048.jpg)








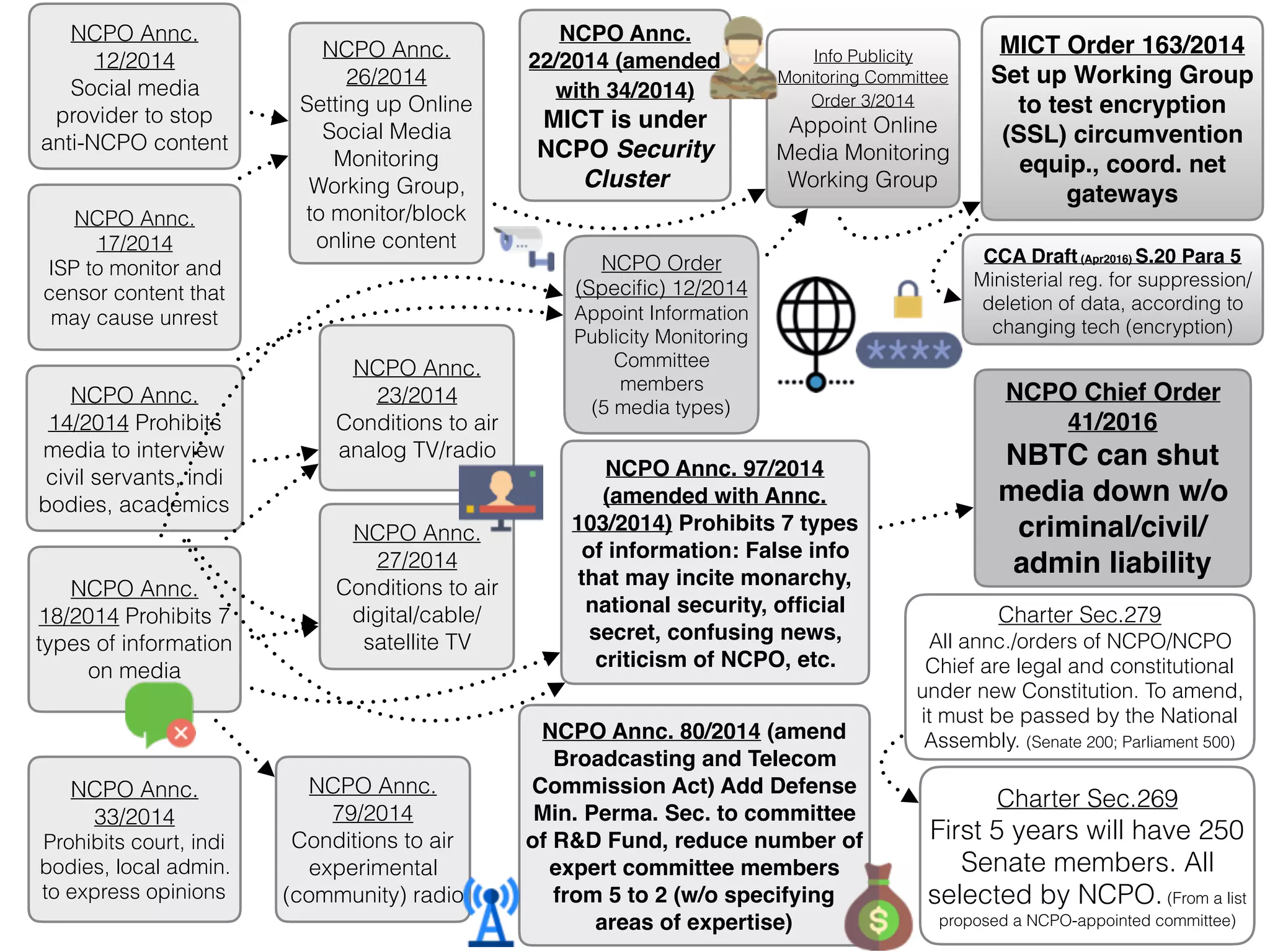
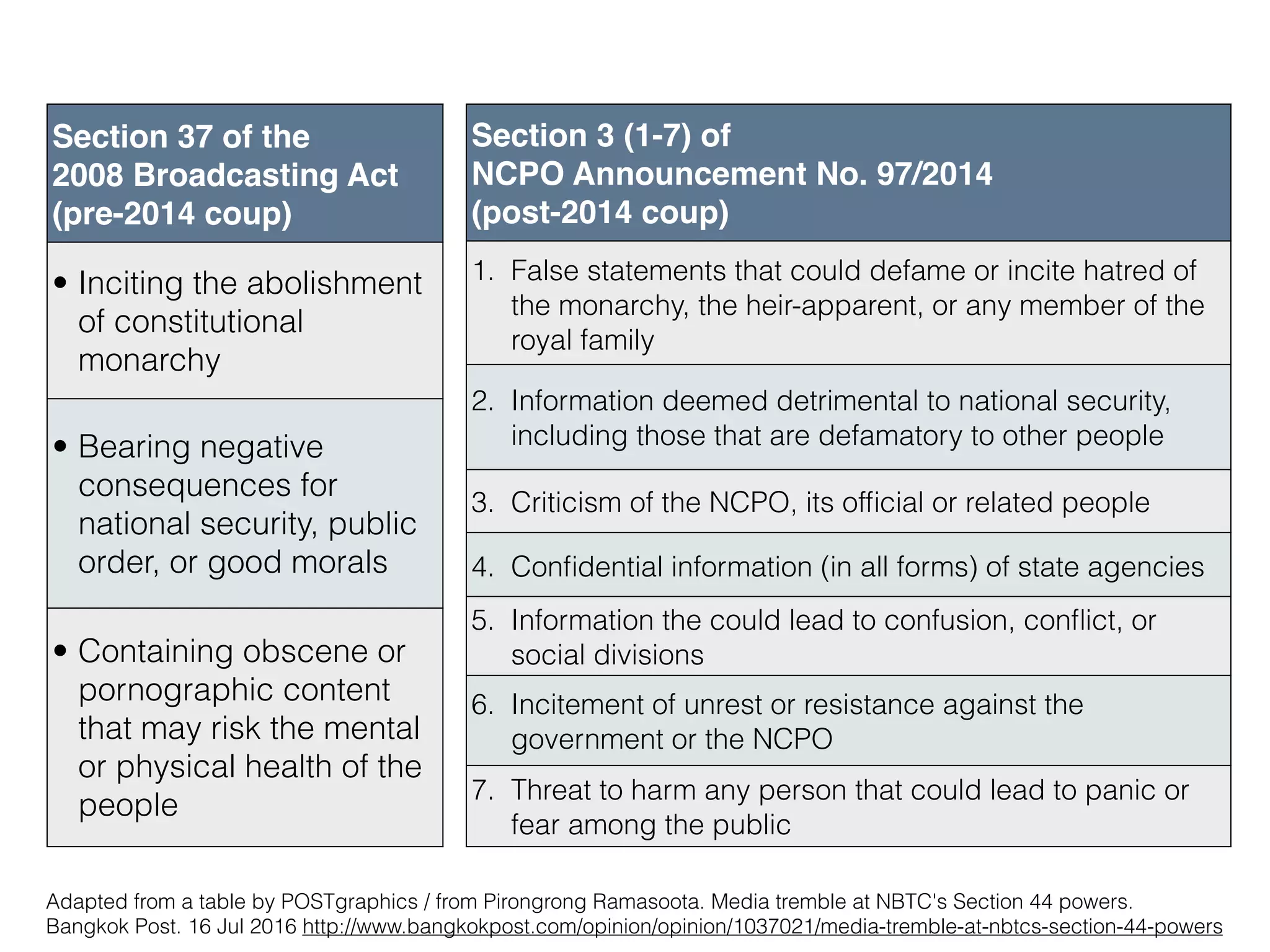
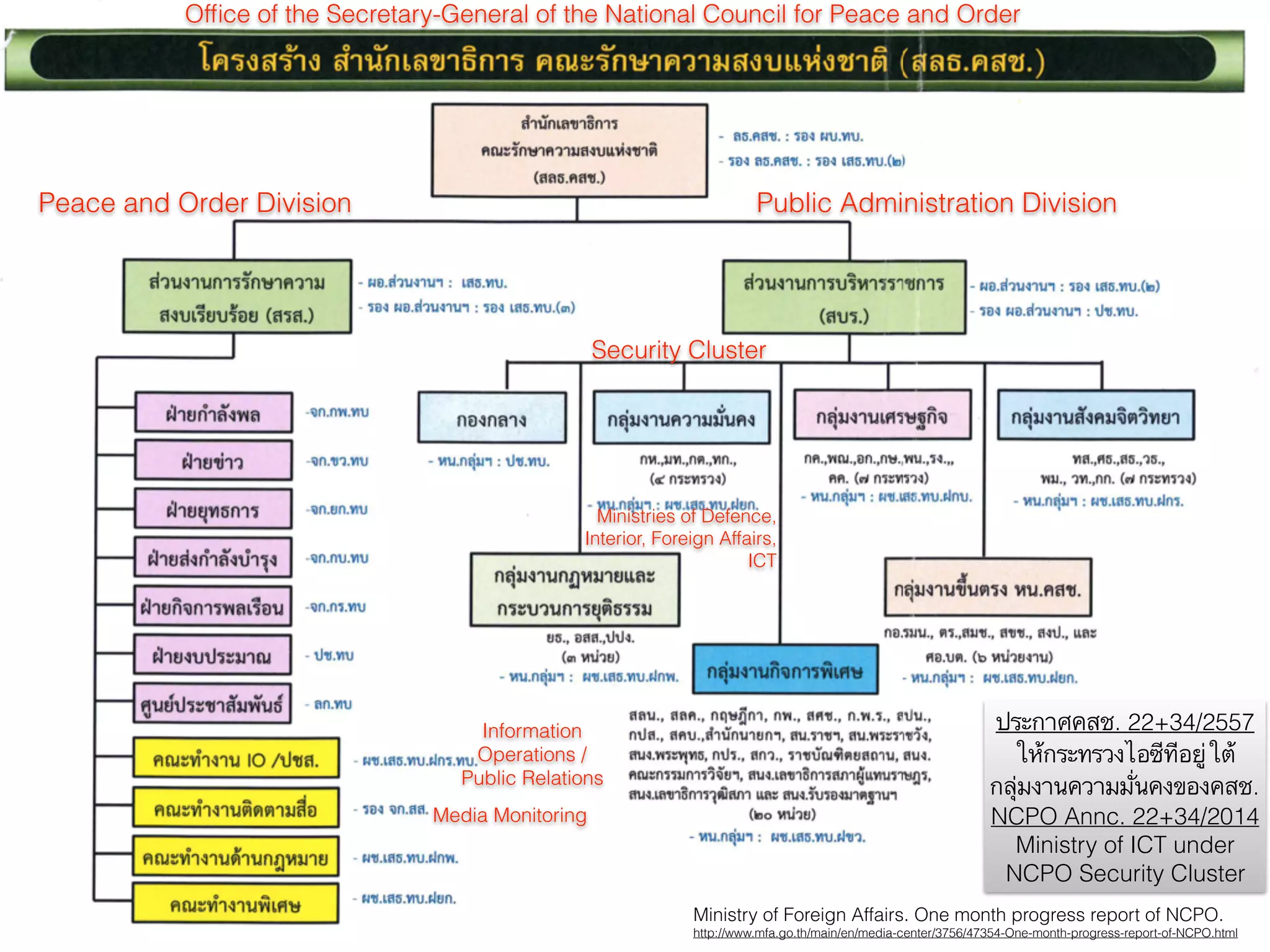


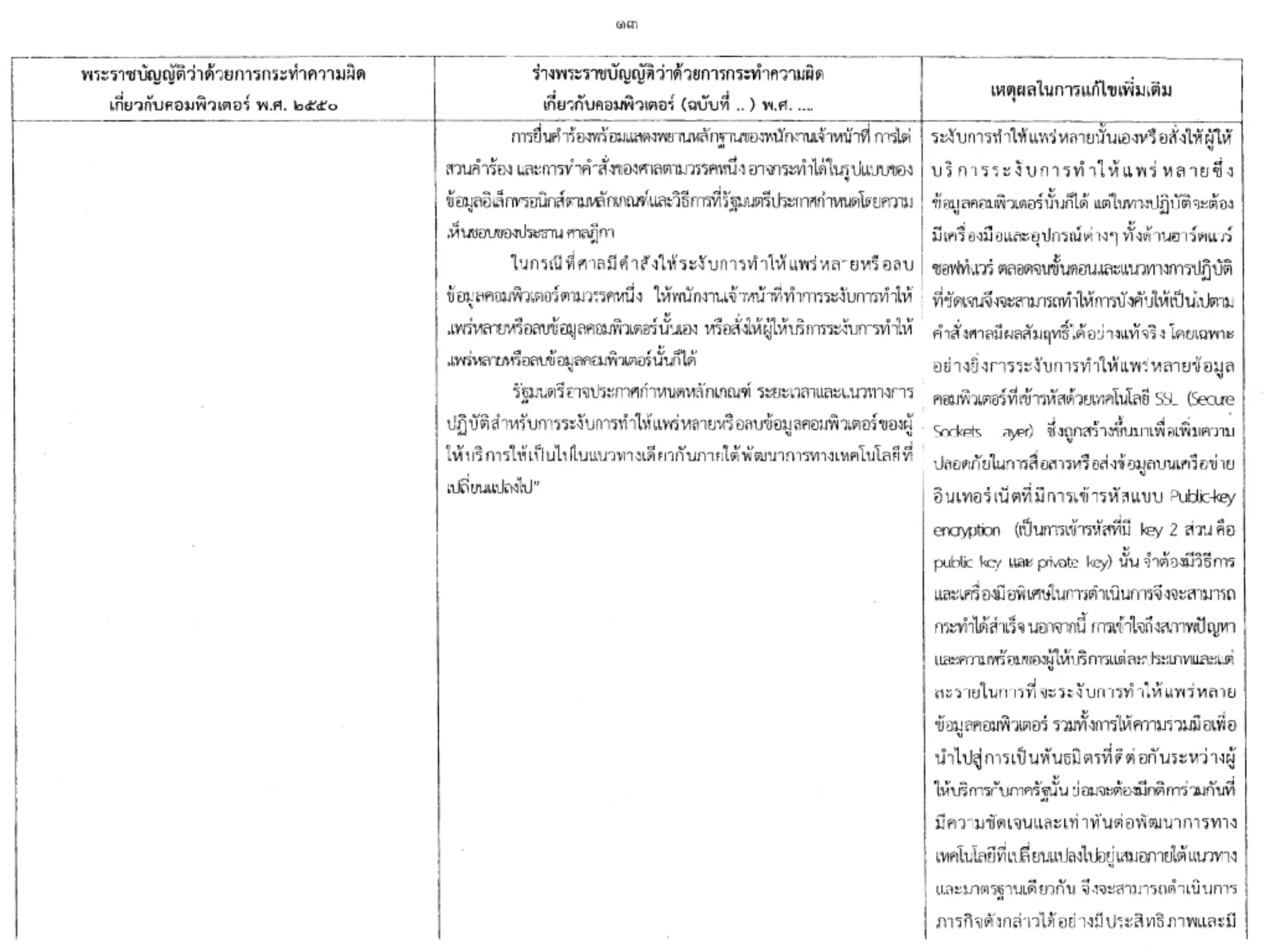
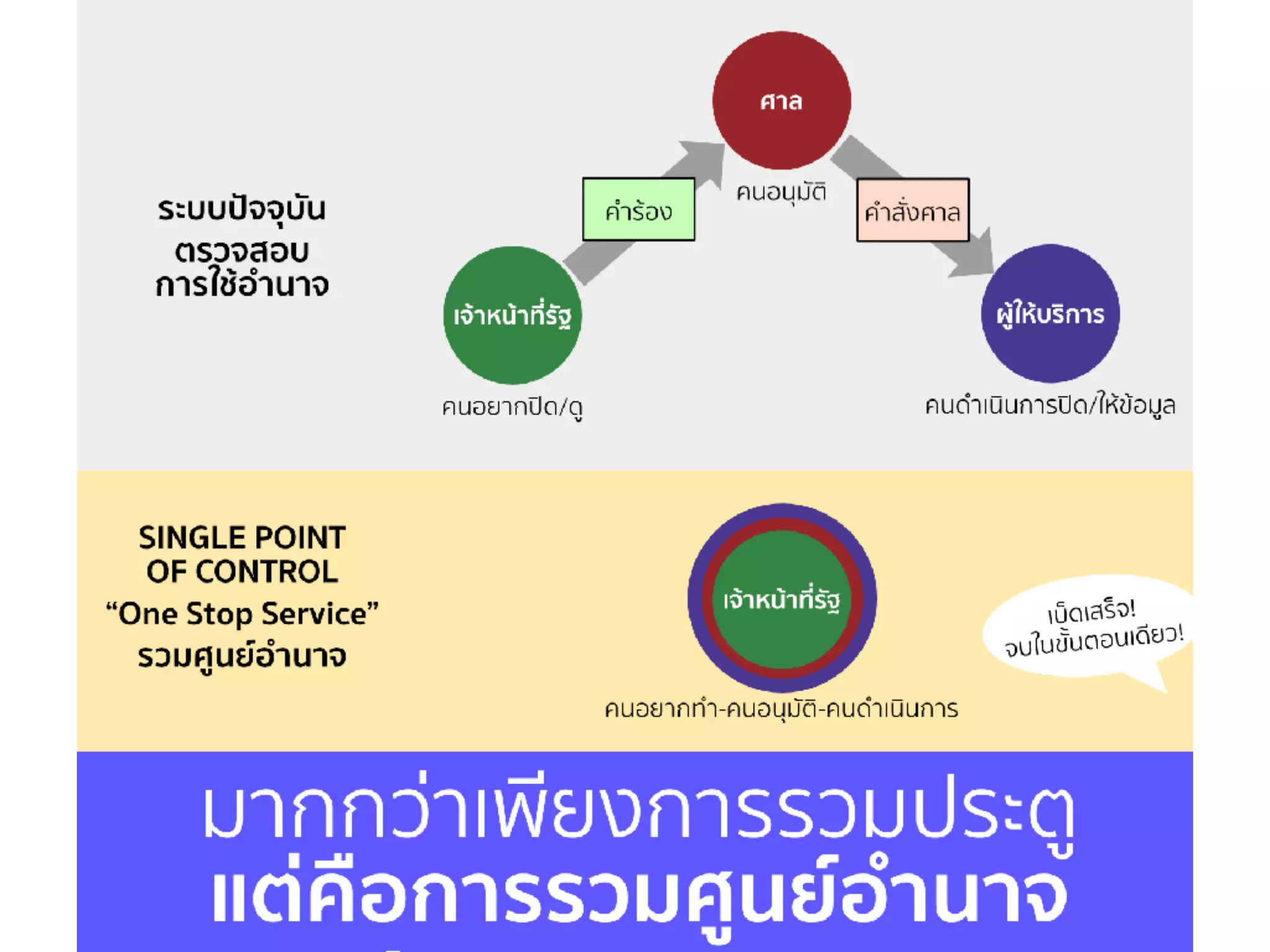
![COMPUTER-RELATED CRIME BILL (DATA BLOCKING/REMOVAL — SEC.20)
➤ […] When the Court issues a warrant to suppress the
distribution or to remove such data per Paragraph One or
Two, the competent official may suppress the distribution or
remove the computer data themselves or instruct the service
provider to suppress the distribution or remove the computer
data in their behalf. The Minister may determine the procedure,
duration and guidelines for the service provider to suppress the
distribution or remove the computer data, and they shall be made
compatible to each other and in response to the changing
technology, except when the Court makes any exemption. […]](https://image.slidesharecdn.com/mapping-stakeholders-arthit-netizen-nlu-delhi-20170410-170410134602/75/Mapping-Stakeholders-Decision-makers-and-Implementers-in-Thailand-s-Cyber-Policy-47-2048.jpg)