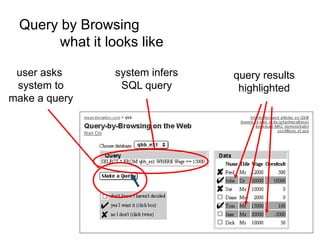
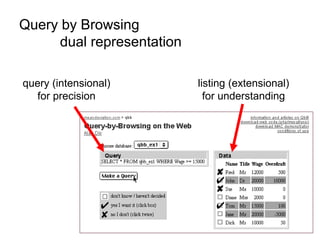
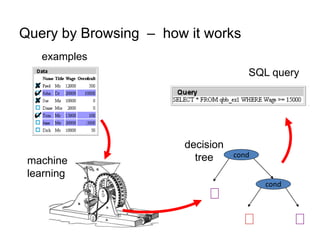
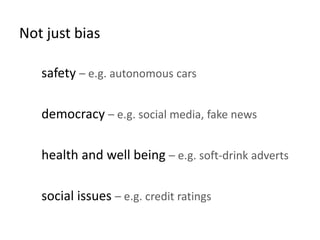
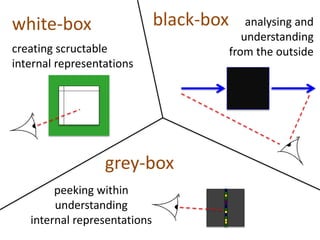
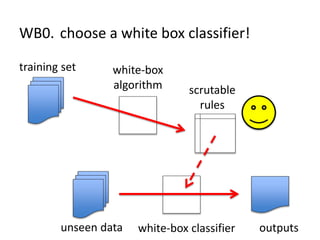
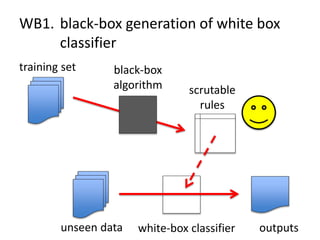
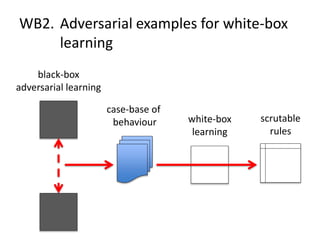
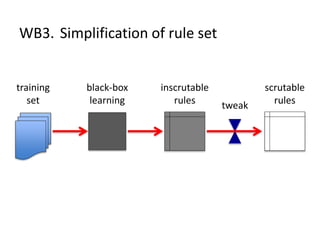
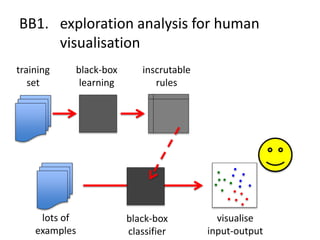
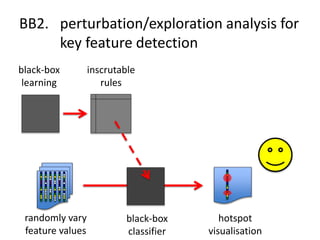
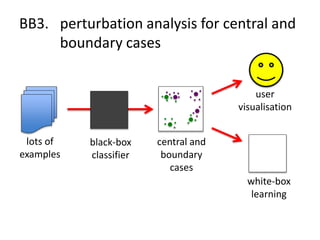
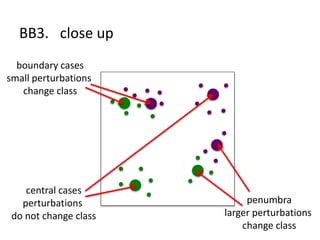
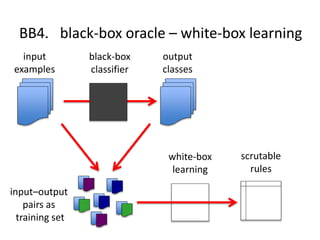
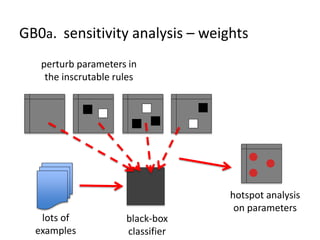
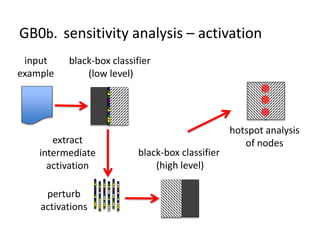
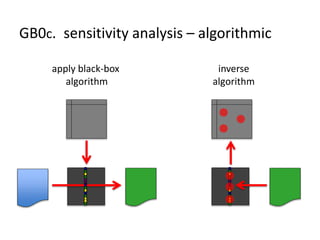
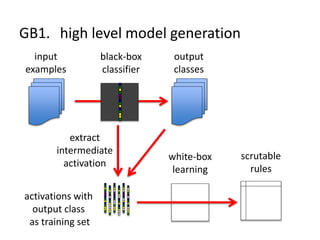
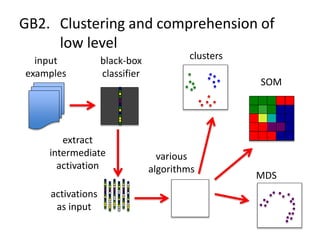
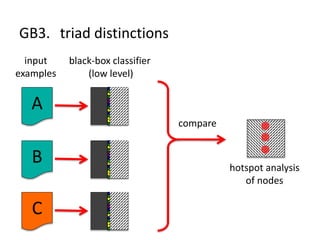
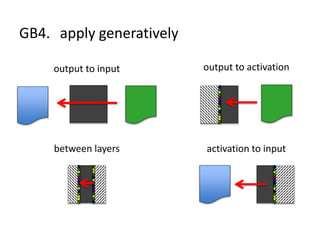
The document discusses the implications of algorithmic bias in machine learning, emphasizing the need for transparency and accountability in these systems to avoid reinforcing societal inequalities. It highlights historical insights on query-by-browsing as a potential solution for creating interpretable algorithms, and the importance of creating scrutable internal representations. The author calls for a transformative approach beyond mere publication, advocating for active engagement in policy and public discourse regarding algorithmic ethics.