IT General Controls Key Performance Indicator & Key Risk Indicator
Explore the world of IT General Controls through this informative presentation on Key Performance Indicators (KPIs) and Key Risk Indicators (KRIs). In this comprehensive slideshow, we delve into the critical aspects of ITGCs, shedding light on how KPIs and KRIs play a pivotal role in ensuring the effectiveness and security of your organization's IT systems. Key Topics Covered: Understanding IT General Controls (ITGCs) Importance of Monitoring ITGCs Key Performance Indicators (KPIs) for ITGCs Identifying and Defining KPIs Key Risk Indicators (KRIs) in ITGCs Setting Up Effective KPIs and KRIs Real-world Examples and Case Studies Benefits of Implementing KPIs and KRIs Ensuring Compliance and Security Best Practices for Managing ITGCs Unlock the potential of IT General Controls with actionable insights into KPIs and KRIs that will help you enhance your organization's IT governance, risk management, and compliance strategies. Don't miss this opportunity to bolster your IT control framework and stay ahead in the ever-evolving landscape of technology.
Recommended
More Related Content
What's hot
What's hot (20)
Similar to IT General Controls Key Performance Indicator & Key Risk Indicator
Similar to IT General Controls Key Performance Indicator & Key Risk Indicator (17)
More from Bim Akinfenwa
More from Bim Akinfenwa (13)
Recently uploaded
Recently uploaded (20)
IT General Controls Key Performance Indicator & Key Risk Indicator
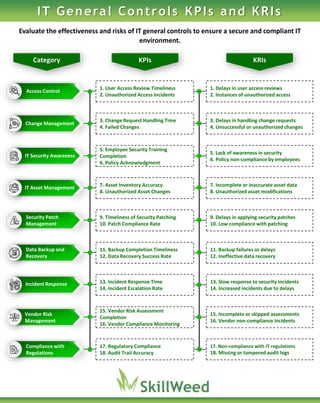
- 1. Access Control 1. User Access Review Timeliness 2. Unauthorized Access Incidents 1. Delays in user access reviews 2. Instances of unauthorized access Change Management 3. Change Request Handling Time 4. Failed Changes 3. Delays in handling change requests 4. Unsuccessful or unauthorized changes IT Security Awareness 5. Employee Security Training Completion 6. Policy Acknowledgment 5. Lack of awareness in security 6. Policy non-compliance by employees IT Asset Management 7. Asset Inventory Accuracy 8. Unauthorized Asset Changes 7. Incomplete or inaccurate asset data 8. Unauthorized asset modifications Security Patch Management 9. Timeliness of Security Patching 10. Patch Compliance Rate 9. Delays in applying security patches 10. Low compliance with patching Data Backup and Recovery 11. Backup Completion Timeliness 12. Data Recovery Success Rate 11. Backup failures or delays 12. Ineffective data recovery Incident Response 13. Incident Response Time 14. Incident Escalation Rate 13. Slow response to security incidents 14. Increased incidents due to delays Vendor Risk Management 15. Vendor Risk Assessment Completion 16. Vendor Compliance Monitoring 15. Incomplete or skipped assessments 16. Vendor non-compliance incidents Compliance with Regulations 17. Regulatory Compliance 18. Audit Trail Accuracy 17. Non-compliance with IT regulations 18. Missing or tampered audit logs Category KPIs KRIs IT General Controls KPIs and KRIs Evaluate the effectiveness and risks of IT general controls to ensure a secure and compliant IT environment.