Infographic | Insider Threats: Top 20 Alarming Statistics and Figures
•
0 likes•18 views
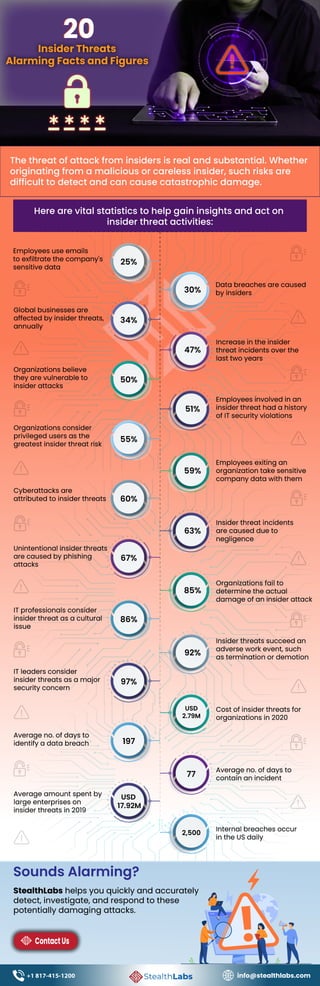
The document summarizes alarming statistics about insider threats that organizations face. Over 25% of employees use email to exfiltrate sensitive data, and 30% of data breaches are caused by insiders. Insider threats cost organizations an average of $2.79 million in 2020, and privileged users are considered the greatest risk. The document advocates contacting StealthLabs to help detect, investigate, and respond to these potentially damaging insider attacks.
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
More Related Content
What's hot
What's hot (20)
Cyber Risks & Liabilities - Cyber Security for Small Businesses

Cyber Risks & Liabilities - Cyber Security for Small Businesses
Unintentional Insider Threat featuring Dr. Eric Cole

Unintentional Insider Threat featuring Dr. Eric Cole
Stop occupational fraud - Three simple steps to help stop fraud

Stop occupational fraud - Three simple steps to help stop fraud
Symantec 2011 Encryption Flash Poll Global Results

Symantec 2011 Encryption Flash Poll Global Results
Network Security and Privacy Liability - Four Reasons Why You need This Cove...

Network Security and Privacy Liability - Four Reasons Why You need This Cove...
Role of The Board In IT Governance & Cyber Security-Steve Howse

Role of The Board In IT Governance & Cyber Security-Steve Howse
Infographic: Stopping Attacks at the Identity Perimeter

Infographic: Stopping Attacks at the Identity Perimeter
Implement Effective Cybersecurity Practices In 2021 With Top LA Prevention Re...

Implement Effective Cybersecurity Practices In 2021 With Top LA Prevention Re...
Similar to Infographic | Insider Threats: Top 20 Alarming Statistics and Figures
Similar to Infographic | Insider Threats: Top 20 Alarming Statistics and Figures (20)
trellix-mind-of-the-ciso-report-ebook-behind-the-breach.pdf

trellix-mind-of-the-ciso-report-ebook-behind-the-breach.pdf
Cybersecurity - you are being targeted -Keyven Lewis, CMIT SOLUTIONS

Cybersecurity - you are being targeted -Keyven Lewis, CMIT SOLUTIONS
We are living in a world where cyber security is a top priority for .pdf

We are living in a world where cyber security is a top priority for .pdf
The Shifting State of Endpoint Risk: Key Strategies to Implement in 2011

The Shifting State of Endpoint Risk: Key Strategies to Implement in 2011
Executive Summary of the 2016 Scalar Security Study

Executive Summary of the 2016 Scalar Security Study
Global Megatrends in Cybersecurity – A Survey of 1,000 CxOs

Global Megatrends in Cybersecurity – A Survey of 1,000 CxOs
Recently uploaded
Recently uploaded (20)
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
What Are The Drone Anti-jamming Systems Technology?

What Are The Drone Anti-jamming Systems Technology?
Advantages of Hiring UIUX Design Service Providers for Your Business

Advantages of Hiring UIUX Design Service Providers for Your Business
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
Tata AIG General Insurance Company - Insurer Innovation Award 2024

Tata AIG General Insurance Company - Insurer Innovation Award 2024
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...

Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
HTML Injection Attacks: Impact and Mitigation Strategies

HTML Injection Attacks: Impact and Mitigation Strategies
Axa Assurance Maroc - Insurer Innovation Award 2024

Axa Assurance Maroc - Insurer Innovation Award 2024
Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe

Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024

Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Infographic | Insider Threats: Top 20 Alarming Statistics and Figures
- 1. Insider Threats Alarming Facts and Figures 20 20 The threat of attack from insiders is real and substantial. Whether originating from a malicious or careless insider, such risks are difficult to detect and can cause catastrophic damage. Here are vital statistics to help gain insights and act on insider threat activities: 25% Employees use emails to exfiltrate the company's sensitive data 30% Data breaches are caused by insiders 34% Global businesses are affected by insider threats, annually 47% Increase in the insider threat incidents over the last two years 50% Organizations believe they are vulnerable to insider attacks 51% Employees involved in an insider threat had a history of IT security violations 55% Organizations consider privileged users as the greatest insider threat risk 60% Cyberattacks are attributed to insider threats 59% Employees exiting an organization take sensitive company data with them 63% Insider threat incidents are caused due to negligence 67% Unintentional insider threats are caused by phishing attacks 85% Organizations fail to determine the actual damage of an insider attack 86% IT professionals consider insider threat as a cultural issue 92% Insider threats succeed an adverse work event, such as termination or demotion 97% IT leaders consider insider threats as a major security concern USD 2.79M Cost of insider threats for organizations in 2020 197 Average no. of days to identify a data breach 77 Average no. of days to contain an incident USD 17.92M Average amount spent by large enterprises on insider threats in 2019 2,500 Internal breaches occur in the US daily Sounds Alarming? StealthLabs helps you quickly and accurately detect, investigate, and respond to these potentially damaging attacks. info@stealthlabs.com ContactUs
