Today's Third Party Vendor Risk Threat Plane
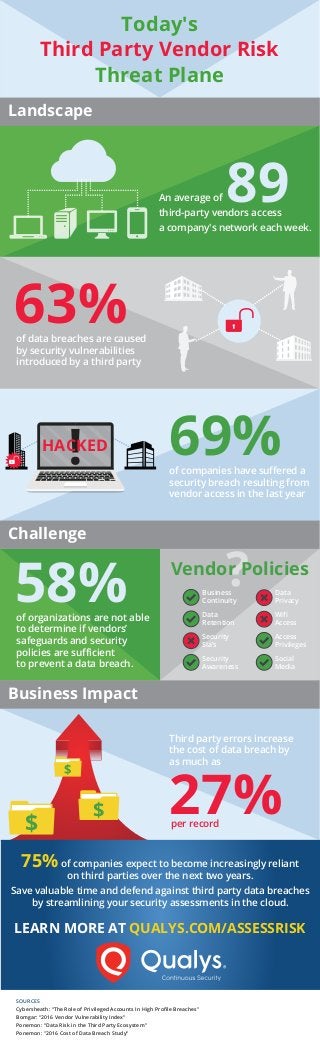
An average of 89 third-party vendors access a company's network each week. 63% of data breaches are caused by security vulnerabilities introduced by a third party. 69% of companies have suffered a security breach resulting from vendor access in the last year. 58% of organizations are not able to determine if vendors' safeguards and security policies are sufficient to prevent a data breach. Third party errors increase the cost of a data breach by as much as 27% per record. And, 75% of companies expect to become increasingly reliant on third parties over the next two years. Save valuable time and defend against third party data breaches by streamlining your security assessments in the cloud. Learn more and get a free trial of Qualys Security Assessment Questionnaire (SAQ) at www.qualys.com/assessrisk.
Recommended
Recommended
More Related Content
Recently uploaded
Recently uploaded (20)
Featured
Featured (20)
Today's Third Party Vendor Risk Threat Plane
- 1. Today's Third Party Vendor Risk Threat Plane 63%of data breaches are caused by security vulnerabilities introduced by a third party 27% Third party errors increase the cost of data breach by as much as per record 69% ? of companies have suffered a security breach resulting from vendor access in the last year 58%of organizations are not able to determine if vendors’ safeguards and security policies are sufficient to prevent a data breach. 89An average of third-party vendors access a company's network each week. HACKED Business Continuity Data Privacy Data Retention Wifi Access Security Sla’s Access Privileges Security Awareness Social Media Vendor Policies $ $ $ Landscape Challenge Business Impact LEARN MORE AT QUALYS.COM/ASSESSRISK SOURCES Cybersheath: “The Role of Privileged Accounts In High Profile Breaches” Bomgar: “2016 Vendor Vulnerability Index” Ponemon: “Data Risk in the Third Party Ecosystem” Ponemon: "2016 Cost of Data Breach Study” 75%of companies expect to become increasingly reliant on third parties over the next two years. Save valuable time and defend against third party data breaches by streamlining your security assessments in the cloud.
