In hands-on tests, VMRay Email Threat Defender caught malware and phishing attacks that bypassed Microsoft 365 security
•
0 likes•94 views
When paired with Microsoft 365, VMRay provided added protection against novel attacks, sophisticated malware, and phishing attempts
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
Information system security is a hot topic and a major focus for most organizations. As technology spreads throughout your business, so do security threats associated with technology. E-mail, one of the most prevalent IT systems, reaches into all areas of business. It can pose a security threat because e-mail transports information between users and from the Internet to your user desktops.Microsoft Unified Communications - Securing Exchange Server 2007 Messaging Wh...

Microsoft Unified Communications - Securing Exchange Server 2007 Messaging Wh...Microsoft Private Cloud
Discover how PetaBytz's Microsoft 365's enhanced security and privacy features, from Advanced Threat Protection to Multi-Factor Authentication, fortify your data and ensure robust digital protection. Safeguard your organization with the latest defenses.
Fortifying Your Data Unveiling Enhanced Security And Privacy Features in Micr...

Fortifying Your Data Unveiling Enhanced Security And Privacy Features in Micr...PetaBytz Technologies
The 4th Generation Intel Xeon Scalable processor‑powered solution deployed in less than two hours and ran a generative AI workload effectively
Conclusion
The appeal of incorporating GenAI into your organization’s operations is likely great. Getting started with an efficient solution for your next LLM workload or application can seem daunting because of the changing hardware and software landscape, but Dell APEX Cloud Platform for Red Hat OpenShift powered by 4th Gen Intel Xeon Scalable processors could provide the solution you need. We started with a Dell Validated Design as a reference, and then went on to modify the deployment as necessary for our Llama 2 workload. The Dell APEX Cloud Platform for Red Hat OpenShift solution worked well for our LLM, and by using this deployment guide in conjunction with numerous Dell documents and some flexibility, you could be well on your way to innovating your next GenAI breakthrough.Dell APEX Cloud Platform for Red Hat OpenShift: An easily deployable and powe...

Dell APEX Cloud Platform for Red Hat OpenShift: An easily deployable and powe...Principled Technologies
Compared to a cluster of PowerEdge R750 servers running VMware Cloud Foundation (VCF)
For organizations running clusters of moderately configured, older Dell PowerEdge servers with a previous version of VCF, upgrading to better-configured modern servers can provide a significant performance boost and more.
Upgrade your cloud infrastructure with Dell PowerEdge R760 servers and VMware...

Upgrade your cloud infrastructure with Dell PowerEdge R760 servers and VMware...Principled Technologies
More Related Content
Similar to In hands-on tests, VMRay Email Threat Defender caught malware and phishing attacks that bypassed Microsoft 365 security
Information system security is a hot topic and a major focus for most organizations. As technology spreads throughout your business, so do security threats associated with technology. E-mail, one of the most prevalent IT systems, reaches into all areas of business. It can pose a security threat because e-mail transports information between users and from the Internet to your user desktops.Microsoft Unified Communications - Securing Exchange Server 2007 Messaging Wh...

Microsoft Unified Communications - Securing Exchange Server 2007 Messaging Wh...Microsoft Private Cloud
Discover how PetaBytz's Microsoft 365's enhanced security and privacy features, from Advanced Threat Protection to Multi-Factor Authentication, fortify your data and ensure robust digital protection. Safeguard your organization with the latest defenses.
Fortifying Your Data Unveiling Enhanced Security And Privacy Features in Micr...

Fortifying Your Data Unveiling Enhanced Security And Privacy Features in Micr...PetaBytz Technologies
Similar to In hands-on tests, VMRay Email Threat Defender caught malware and phishing attacks that bypassed Microsoft 365 security (20)
Infographic - Three steps to stopping advanced email threats

Infographic - Three steps to stopping advanced email threats
Webinar Mastering Microsoft Security von Baggenstos

Webinar Mastering Microsoft Security von Baggenstos
Presentation-PracticalGuideToHavingACustomerConversationOnSecurity (1).pptx

Presentation-PracticalGuideToHavingACustomerConversationOnSecurity (1).pptx
Microsoft Unified Communications - Securing Exchange Server 2007 Messaging Wh...

Microsoft Unified Communications - Securing Exchange Server 2007 Messaging Wh...
Comprehensive Protection and Visibility into Advanced Email Attacks 

Comprehensive Protection and Visibility into Advanced Email Attacks
Microsoft Security adoptionguide for the enterprise

Microsoft Security adoptionguide for the enterprise
"Evolving Cybersecurity Strategies" - Threat protection and incident managment

"Evolving Cybersecurity Strategies" - Threat protection and incident managment
Office 365 Security - Its 2am do you know whos in your office 365

Office 365 Security - Its 2am do you know whos in your office 365
Protecting Corporete Credentials Against Threats 4 48159 wgw03071_usen

Protecting Corporete Credentials Against Threats 4 48159 wgw03071_usen
Fortifying Your Data Unveiling Enhanced Security And Privacy Features in Micr...

Fortifying Your Data Unveiling Enhanced Security And Privacy Features in Micr...
More from Principled Technologies
The 4th Generation Intel Xeon Scalable processor‑powered solution deployed in less than two hours and ran a generative AI workload effectively
Conclusion
The appeal of incorporating GenAI into your organization’s operations is likely great. Getting started with an efficient solution for your next LLM workload or application can seem daunting because of the changing hardware and software landscape, but Dell APEX Cloud Platform for Red Hat OpenShift powered by 4th Gen Intel Xeon Scalable processors could provide the solution you need. We started with a Dell Validated Design as a reference, and then went on to modify the deployment as necessary for our Llama 2 workload. The Dell APEX Cloud Platform for Red Hat OpenShift solution worked well for our LLM, and by using this deployment guide in conjunction with numerous Dell documents and some flexibility, you could be well on your way to innovating your next GenAI breakthrough.Dell APEX Cloud Platform for Red Hat OpenShift: An easily deployable and powe...

Dell APEX Cloud Platform for Red Hat OpenShift: An easily deployable and powe...Principled Technologies
Compared to a cluster of PowerEdge R750 servers running VMware Cloud Foundation (VCF)
For organizations running clusters of moderately configured, older Dell PowerEdge servers with a previous version of VCF, upgrading to better-configured modern servers can provide a significant performance boost and more.
Upgrade your cloud infrastructure with Dell PowerEdge R760 servers and VMware...

Upgrade your cloud infrastructure with Dell PowerEdge R760 servers and VMware...Principled Technologies
Compared to a cluster of PowerEdge R750 servers running VMware Cloud Foundation 4.5
If your company is struggling with underperforming infrastructure, upgrading to 16th Generation Dell PowerEdge servers running VCF 5.1 could be just what you need to handle more database throughput and reduce vSAN latencies. As an additional benefit to IT admins, we also found that the embedded VMware Aria Operation adapter provided useful infrastructure insights.
Upgrade your cloud infrastructure with Dell PowerEdge R760 servers and VMware...

Upgrade your cloud infrastructure with Dell PowerEdge R760 servers and VMware...Principled Technologies
Three AMD EPYC processor-based two-processor solutions outshined comparable Intel Xeon Scalable processor-based solutions by handling more Redis workload transactions and requests while consuming less power
Conclusion
Performance and energy efficiency are significant factors in processor selection for servers running data-intensive workloads, such as Redis. We compared the Redis performance and energy consumption of a server cluster in three AMD EPYC two-processor configurations against that of a server cluster in two Intel Xeon Scalable two-processor configurations. In each of our three test scenarios, the server cluster backed by AMD EPYC processors outperformed the server cluster backed by Intel Xeon Scalable processors. In addition, one of the AMD EPYC processor-based clusters consumed 20 percent less power than its Intel Xeon Scalable processor-based counterpart. Combining these measurements gave us power efficiency metrics that demonstrate how valuable AMD EPYC processor-based servers could be—you could see better performance per watt with these AMD EPYC processor-based server clusters and potentially get more from your Redis or other data intensive applications and workloads while reducing data center power costs.Realize 2.1X the performance with 20% less power with AMD EPYC processor-back...

Realize 2.1X the performance with 20% less power with AMD EPYC processor-back...Principled Technologies
We deployed this modern environment, then migrated database VMs from legacy servers and saw performance improvements that support consolidation
Conclusion
If your organization’s transactional databases are running on gear that is several years old, you have much to gain by upgrading to modern servers with new processors and networking components and an OpenShift environment. In our testing, a modern OpenShift environment with a cluster of three Dell PowerEdge R7615 servers with 4th Generation AMD EPYC processors and high-speed 100Gb Broadcom NICs outperformed a legacy environment with MySQL VMs running on a cluster of three Dell PowerEdge R7515 servers with 3rd Generation AMD EPYC processors and 25Gb Broadcom NICs. We also easily migrated a VM from the legacy environment to the modern environment, with only a few steps required to set up and less than ten minutes of hands-on time. The performance advantage of the modern servers would allow a company to reduce the number of servers necessary to perform a given amount of database work, thus lowering operational expenditures such as power and cooling and IT staff time for maintenance. The high-speed 100Gb Broadcom NICs in this solution also give companies better network performance and networking capacity to grow as they embrace emerging technologies such as AI that put great demands on networks.Improve performance and gain room to grow by easily migrating to a modern Ope...

Improve performance and gain room to grow by easily migrating to a modern Ope...Principled Technologies
A Principled Technologies deployment guide
Conclusion
Deploying VMware Cloud Foundation 5.1 on next gen Dell PowerEdge servers brings together critical virtualization capabilities and high-performing hardware infrastructure. Relying on our hands-on experience, this deployment guide offers a comprehensive roadmap that can guide your organization through the seamless integration of advanced VMware cloud solutions with the performance and reliability of Dell PowerEdge servers. In addition to the deployment efficiency, the Cloud Foundation 5.1 and PowerEdge solution delivered strong performance while running a MySQL database workload. By leveraging VMware Cloud Foundation 5.1 and PowerEdge servers, you could help your organization embrace cloud computing with confidence, potentially unlocking a new level of agility, scalability, and efficiency in your data center operations.Deploy with confidence: VMware Cloud Foundation 5.1 on next gen Dell PowerEdg...

Deploy with confidence: VMware Cloud Foundation 5.1 on next gen Dell PowerEdg...Principled Technologies
Compared to a cluster of PowerEdge R750 servers running VMware Cloud Foundation 4.5
Conclusion
If your company is struggling with underperforming infrastructure, upgrading to 16th Generation Dell PowerEdge servers running VCF 5.1 could be just what you need to handle more database throughput and reduce vSAN latencies. We found that a Dell PowerEdge R760 server cluster running VCF 5.1 processed over 78 percent more TPM and 79 percent more NOPM than a Dell PowerEdge R750 server cluster running VCF 4.5. It’s also worth noting that the PowerEdge R750 cluster bottlenecked on vSAN storage, with max write latency at 8.9ms. For reference, the PowerEdge R760 cluster clocked in at 3.8ms max write latency. This higher latency is due in part to the single disk group per host on the moderately configured PowerEdge R750 cluster, while the better-configured PowerEdge R760 cluster supported four disk groups per host. As an additional benefit to IT admins, we also found that the embedded VMware Aria Operation adapter provided useful infrastructure insights.Upgrade your cloud infrastructure with Dell PowerEdge R760 servers and VMware...

Upgrade your cloud infrastructure with Dell PowerEdge R760 servers and VMware...Principled Technologies
Compared to the Supermicro management portfolio
Conclusion
Choosing a vendor for server purchases is about more than just the hardware platform. Decision-makers must also consider more long-term concerns, including system/data security, energy efficiency, and ease of management. These concerns make the systems management tools a vendor offers as important as the hardware.
We investigated the features and capabilities of server management tools from Dell and Supermicro, comparing Dell iDRAC9 against Supermicro IPMI for embedded server management and Dell OpenManage Enterprise and CloudIQ against Supermicro Server Manager for one-to-many device and console management and monitoring. We found that the Dell management tools provided more comprehensive security, sustainability, and management/monitoring features and capabilities than Supermicro servers did. In addition, Dell tools automated more tasks to ease server management, resulting in significant time savings for administrators versus having to do the same tasks manually with Supermicro tools.
When making a server purchase, a vendor’s associated management products are critical to protect data, support a more sustainable environment, and to ease the maintenance of systems. Our tests and research showed that the Dell management portfolio for PowerEdge servers offered more features to help organizations meet these goals than the comparable Supermicro management products.
Increase security, sustainability, and efficiency with robust Dell server man...

Increase security, sustainability, and efficiency with robust Dell server man...Principled Technologies
Compared to the Supermicro management portfolio
Conclusion
Choosing a vendor for server purchases is about more than just the hardware platform. Decision-makers must also consider more long-term concerns, including system/data security, energy efficiency, and ease of management. These concerns make the systems management tools a vendor offers as important as the hardware.
We investigated the features and capabilities of server management tools from Dell and Supermicro, comparing Dell iDRAC9 against Supermicro IPMI for embedded server management and Dell OpenManage Enterprise and CloudIQ against Supermicro Server Manager for one-to-many device and console management and monitoring. We found that the Dell management tools provided more comprehensive security, sustainability, and management/monitoring features and capabilities than Supermicro servers did. In addition, Dell tools automated more tasks to ease server management, resulting in significant time savings for administrators versus having to do the same tasks manually with Supermicro tools.
When making a server purchase, a vendor’s associated management products are critical to protect data, support a more sustainable environment, and to ease the maintenance of systems. Our tests and research showed that the Dell management portfolio for PowerEdge servers offered more features to help organizations meet these goals than the comparable Supermicro management products.Increase security, sustainability, and efficiency with robust Dell server man...

Increase security, sustainability, and efficiency with robust Dell server man...Principled Technologies
In our tests, Dell APEX Block Storage for AWS outperformed similarly configured solutions from Vendor A, achieving more IOPS, better throughput, and more consistent performance on both NVMe-supported configurations and configurations backed by Elastic Block Store (EBS) alone.
Dell APEX Block Storage for AWS supports a full NVMe backed configuration, but Vendor A doesn’t—its solution uses EBS for storage capacity and NVMe as an extended read cache—which means APEX Block Storage for AWS can deliver faster storage performance.
Scale up your storage with higher-performing Dell APEX Block Storage for AWS ...

Scale up your storage with higher-performing Dell APEX Block Storage for AWS ...Principled Technologies
In our PostgreSQL tests, R7i instances boosted performance over R6i instances with previous-gen processors
If you use the open-source PostgreSQL database to run your critical business operations, you have many cloud options from which to choose. While many of these instances can do the job, some can deliver stronger performance, which can mean getting a greater return on your cloud investment.
We conducted hands-on testing with the HammerDB TPROC-C benchmark to see how the PostgreSQL performance of Amazon EC2 R7i instances, enabled by 4th Gen Intel Xeon Scalable processors, stacked up to that of R6i instances with previous-generation processors. We learned that small, medium-sized, and large R7i instances with the newer processors delivered better OLTP performance, with improvements as high as 13.8 percent. By choosing the R7i instances, your organization has the potential to support more users, deliver a better experience to those users, and even lower your cloud operating expenditures by requiring fewer instances to get the job done.Open up new possibilities with higher transactional database performance from...

Open up new possibilities with higher transactional database performance from...Principled Technologies
Migrating from Azure Database for MySQL – Single Server to a Flexible Server solution was quick and provided performance and cost benefits
Don’t put off migrating your databases from Azure Database for MySQL – Single Server until the last minute—which is September 2024, when the service will end. Our hands-on testing shows that moving to Azure Database for MySQL – Flexible Server is a simple process that can actually improve your overall database performance and offer better value. With as much as 117 percent better OLTP performance on sysbench and up to 266 percent better performance per dollar, migrating your database to Azure Database for MySQL – Flexible Server with AMD EPYC processors can help you serve more database users and potentially improve your operating budget compared to the expiring Single Server option.Improving database performance and value with an easy migration to Azure Data...

Improving database performance and value with an easy migration to Azure Data...Principled Technologies
With Azure Database for PostgreSQL – Single Server instances set for retirement, the time to migrate to your databases to new Azure Database for PostgreSQL – Flexible Server instances is now.
Migrating to Flexible Server and getting these benefits is easy. Follow our step-by-step guide to complete an offline migration using the Azure Migration tool.Realize better value and performance migrating from Azure Database for Postgr...

Realize better value and performance migrating from Azure Database for Postgr...Principled Technologies
It’s time to move your databases from Azure Database for PostgreSQL – Single Server instances now, before March 2025 when Microsoft Azure retires the service. Our hands-on testing shows that moving to Azure Database for PostgreSQL – Flexible Server is a simple process that can offer significantly better database performance and value. With as much as 4.71 times the NOPM on HammerDB and up to 3.88 times the performance per dollar compared to Single Server, moving to Azure Database for PostgreSQL – Flexible Sever with AMD EPYC processors can give you higher performing databases for lower relative cost.
Realize better value and performance migrating from Azure Database for Postgr...

Realize better value and performance migrating from Azure Database for Postgr...Principled Technologies
We compared system performance on four ChromeOS devices powered by increasingly powerful Intel processors
Conclusion
AI technology, on ChromeOS devices equipped with powerful Intel processors, could be the steppingstone your district needs to make learning more accessible, increase student engagement, and remove barriers to student success. In our hands-on tests, each step up in the Intel processor upgrade story resulted in quicker open app and tab recoveries after shutdown in a traditional session restore scenario and a session restore scenario featuring AI. Don’t miss this opportunity to help teachers and students reach their potential.
Set up students and teachers to excel now and in the future with Intel proces...

Set up students and teachers to excel now and in the future with Intel proces...Principled Technologies
More from Principled Technologies (20)
Dell APEX Cloud Platform for Red Hat OpenShift: An easily deployable and powe...

Dell APEX Cloud Platform for Red Hat OpenShift: An easily deployable and powe...
Upgrade your cloud infrastructure with Dell PowerEdge R760 servers and VMware...

Upgrade your cloud infrastructure with Dell PowerEdge R760 servers and VMware...
Upgrade your cloud infrastructure with Dell PowerEdge R760 servers and VMware...

Upgrade your cloud infrastructure with Dell PowerEdge R760 servers and VMware...
Realize 2.1X the performance with 20% less power with AMD EPYC processor-back...

Realize 2.1X the performance with 20% less power with AMD EPYC processor-back...
Improve performance and gain room to grow by easily migrating to a modern Ope...

Improve performance and gain room to grow by easily migrating to a modern Ope...
Boost PC performance: How more available memory can improve productivity

Boost PC performance: How more available memory can improve productivity
Deploy with confidence: VMware Cloud Foundation 5.1 on next gen Dell PowerEdg...

Deploy with confidence: VMware Cloud Foundation 5.1 on next gen Dell PowerEdg...
Upgrade your cloud infrastructure with Dell PowerEdge R760 servers and VMware...

Upgrade your cloud infrastructure with Dell PowerEdge R760 servers and VMware...
A comparison of security features in Dell, HP, and Lenovo PC systems

A comparison of security features in Dell, HP, and Lenovo PC systems
Increase security, sustainability, and efficiency with robust Dell server man...

Increase security, sustainability, and efficiency with robust Dell server man...
Increase security, sustainability, and efficiency with robust Dell server man...

Increase security, sustainability, and efficiency with robust Dell server man...
Scale up your storage with higher-performing Dell APEX Block Storage for AWS ...

Scale up your storage with higher-performing Dell APEX Block Storage for AWS ...
Scale up your storage with higher-performing Dell APEX Block Storage for AWS

Scale up your storage with higher-performing Dell APEX Block Storage for AWS
Get in and stay in the productivity zone with the HP Z2 G9 Tower Workstation

Get in and stay in the productivity zone with the HP Z2 G9 Tower Workstation
Open up new possibilities with higher transactional database performance from...

Open up new possibilities with higher transactional database performance from...
Improving database performance and value with an easy migration to Azure Data...

Improving database performance and value with an easy migration to Azure Data...
Realize better value and performance migrating from Azure Database for Postgr...

Realize better value and performance migrating from Azure Database for Postgr...
Realize better value and performance migrating from Azure Database for Postgr...

Realize better value and performance migrating from Azure Database for Postgr...
Set up students and teachers to excel now and in the future with Intel proces...

Set up students and teachers to excel now and in the future with Intel proces...
Finding the path to AI success with the Dell AI portfolio - Summary

Finding the path to AI success with the Dell AI portfolio - Summary
Recently uploaded
Enterprise Knowledge’s Urmi Majumder, Principal Data Architecture Consultant, and Fernando Aguilar Islas, Senior Data Science Consultant, presented "Driving Behavioral Change for Information Management through Data-Driven Green Strategy" on March 27, 2024 at Enterprise Data World (EDW) in Orlando, Florida.
In this presentation, Urmi and Fernando discussed a case study describing how the information management division in a large supply chain organization drove user behavior change through awareness of the carbon footprint of their duplicated and near-duplicated content, identified via advanced data analytics. Check out their presentation to gain valuable perspectives on utilizing data-driven strategies to influence positive behavioral shifts and support sustainability initiatives within your organization.
In this session, participants gained answers to the following questions:
- What is a Green Information Management (IM) Strategy, and why should you have one?
- How can Artificial Intelligence (AI) and Machine Learning (ML) support your Green IM Strategy through content deduplication?
- How can an organization use insights into their data to influence employee behavior for IM?
- How can you reap additional benefits from content reduction that go beyond Green IM?
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
Recently uploaded (20)
08448380779 Call Girls In Friends Colony Women Seeking Men

08448380779 Call Girls In Friends Colony Women Seeking Men
Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...

Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...
What Are The Drone Anti-jamming Systems Technology?

What Are The Drone Anti-jamming Systems Technology?
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
Handwritten Text Recognition for manuscripts and early printed texts

Handwritten Text Recognition for manuscripts and early printed texts
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf

The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf
ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke

ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
2024: Domino Containers - The Next Step. News from the Domino Container commu...

2024: Domino Containers - The Next Step. News from the Domino Container commu...
08448380779 Call Girls In Greater Kailash - I Women Seeking Men

08448380779 Call Girls In Greater Kailash - I Women Seeking Men
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
In hands-on tests, VMRay Email Threat Defender caught malware and phishing attacks that bypassed Microsoft 365 security
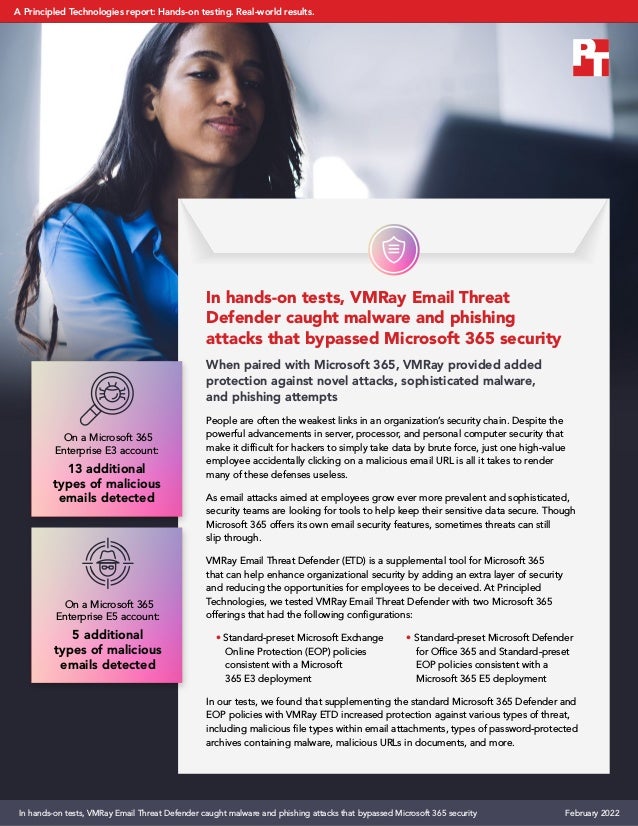
- 1. In hands-on tests, VMRay Email Threat Defender caught malware and phishing attacks that bypassed Microsoft 365 security When paired with Microsoft 365, VMRay provided added protection against novel attacks, sophisticated malware, and phishing attempts People are often the weakest links in an organization’s security chain. Despite the powerful advancements in server, processor, and personal computer security that make it difficult for hackers to simply take data by brute force, just one high-value employee accidentally clicking on a malicious email URL is all it takes to render many of these defenses useless. As email attacks aimed at employees grow ever more prevalent and sophisticated, security teams are looking for tools to help keep their sensitive data secure. Though Microsoft 365 offers its own email security features, sometimes threats can still slip through. VMRay Email Threat Defender (ETD) is a supplemental tool for Microsoft 365 that can help enhance organizational security by adding an extra layer of security and reducing the opportunities for employees to be deceived. At Principled Technologies, we tested VMRay Email Threat Defender with two Microsoft 365 offerings that had the following configurations: • Standard-preset Microsoft Exchange Online Protection (EOP) policies consistent with a Microsoft 365 E3 deployment • Standard-preset Microsoft Defender for Office 365 and Standard-preset EOP policies consistent with a Microsoft 365 E5 deployment In our tests, we found that supplementing the standard Microsoft 365 Defender and EOP policies with VMRay ETD increased protection against various types of threat, including malicious file types within email attachments, types of password-protected archives containing malware, malicious URLs in documents, and more. On a Microsoft 365 Enterprise E3 account: 13 additional types of malicious emails detected On a Microsoft 365 Enterprise E5 account: 5 additional types of malicious emails detected In hands-on tests, VMRay Email Threat Defender caught malware and phishing attacks that bypassed Microsoft 365 security February 2022 A Principled Technologies report: Hands-on testing. Real-world results.
- 2. Our results Tables 1 and 2 give a breakdown of the type and quantity of threats that VMRay Email Threat Defender identified where Microsoft policies alone did not. Though Microsoft policies caught several types of malicious emails in each account, VMRay Email Threat Defender extended this protection to cover additional types of threats. Microsoft 365 E3 with EOP offers basic protection, and Microsoft 365 E5 with EOP and Microsoft Defender offers the best recommended standard protections for a typical user without introducing a large number of false positives. Our testing shows that VMRay Email Threat Defender can supplement these robust sets of security policies for additional peace of mind. Table 2: Types of attack that VMRay Email Threat Defender identified for the E5 account that Microsoft EOP and Defender alone did not. Source: Principled Technologies. Enhanced protection for E5 Standard EOP and Standard Defender policies Quantity Type of attack 3 Malicious files in attachments 1 Password-protected archive attachments containing malware 1 Hidden, malicious macros within files Table 1: Types of attack that VMRay Email Threat Defender identified for the E3 account that Microsoft EOP alone did not. Source: Principled Technologies. Enhanced protection for E3 Standard EOP policies Quantity Type of attack 4 Malicious files in attachments 2 Password-protected archive attachments containing malware 2 Hidden, malicious macros within files 1 Malicious URL within a document 4 Obscured or shortened URLs within the email body In hands-on tests, VMRay Email Threat Defender caught malware and phishing attacks that bypassed Microsoft 365 security February 2022 | 2
- 3. How we tested We deployed two accounts within Microsoft 365 using security policies consistent with either an E3 EOP or E5 EOP and Microsoft Defender deployment. E3 and E5 are enterprise subscription plans for Microsoft 365, with E5 offering more advanced security settings than E3. The E5 plan uses the cloud-based Microsoft Defender for Office 365 in conjunction with Microsoft EOP policies. After configuring each account with VMRay Email Threat Defender, we began our tests. We sent to each account a set of email messages, each of which contained a particular type of threat (such as malicious links and attachments) to see which threats were still able to reach each account’s inbox. When an email did not arrive at the inbox, we checked the Microsoft and VMRay quarantines. We configured VMRay Email Threat Defender to process emails only after Microsoft 365 security features had a chance to respond. Therefore, any emails caught within the VMRay Email Threat Defender quarantine would not have been picked up by Microsoft 365 alone. Email Threat Defender can scan emails at earlier points, but we did not test those features. We generated each attack type in one of two ways: either by obtaining (and altering, if necessary) threat samples from third-party websites that collect samples for security professionals, or by using recent threat samples that VMRay has obtained from its customers (after scrubbing all sensitive information). Because we used live threats, our samples were limited by the number of threats available around the time of testing. Note that in this report, we have purposefully obfuscated or omitted sensitive details that could lead bad actors to identify and exploit vulnerabilities we found in our testing. For some additional details, see the science behind the report. About VMRay Email Threat Defender According to the VMRay website, Email Threat Defender fully automates inbound email scanning by analyzing attachments and links before an email can land in a user’s inbox. Rather than fully replace an email app’s existing security features, VMRay works to enhance native protection as a second layer of defense, integrating with Microsoft Defender APIs and connectors and sharing its analytics with other security tools. To learn more about Email Threat Defender, visit https://www.vmray.com/products-email-threat-defender-etd/. In hands-on tests, VMRay Email Threat Defender caught malware and phishing attacks that bypassed Microsoft 365 security February 2022 | 3
- 4. Conclusion The best data center security in the world may be unable to stop a hacker if one gains access to a high-value account via a convincing phishing email. To reduce the likelihood of a successful attack, it can help to supplement your organization’s existing email security tools for an added layer of protection. In our tests, we found that VMRay Email Threat Defender enhanced the native security of Microsoft 365 E3 and E5 accounts by protecting against more types of malicious email attacks—13 types of attacks beyond E3 protection and 5 types of attacks beyond E5 protection. Adding VMRay Email Threat Defender to your Microsoft 365 deployment could help prevent successful phishing attempts and help keep your business safe. Just one malicious email reaching the right inbox is enough opportunity to compromise critical organizational assets as well as employee and customer data. For more information, visit https://www.vmray.com/solutions/close-the-gaps-in-your-office-365-email-security/. Principled Technologies is a registered trademark of Principled Technologies, Inc. All other product names are the trademarks of their respective owners. For additional information, review the science behind this report. Principled Technologies® Facts matter.® Principled Technologies® Facts matter.® This project was commissioned by VMRay. Read the science behind this report at https://facts.pt/iHN6LLy In hands-on tests, VMRay Email Threat Defender caught malware and phishing attacks that bypassed Microsoft 365 security February 2022 | 4
