Eset vs Symantec
•Download as PPTX, PDF•
0 likes•86 views
This document compares the endpoint security products Eset and Symantec. Eset scored higher than Symantec in most categories on G2 including requirements, ease of use, ease of setup, ease of admin, device control, and web control. However, one user commented that Eset was not protecting against ransomware as expected. For Symantec, one user noted the transition between portals was more difficult than it should have been. A Gartner review found that Eset focuses on protection against ransomware, advanced threats, and monitoring applications while Symantec emphasizes artificial intelligence-powered security, strong antivirus, application control, and being powered by its global intelligence network.
Report
Share
Report
Share
Recommended
Recommended
"Can We Have Both Safety and Performance in AI for Autonomous Vehicles?," a P...

"Can We Have Both Safety and Performance in AI for Autonomous Vehicles?," a P...Edge AI and Vision Alliance
More Related Content
Similar to Eset vs Symantec
"Can We Have Both Safety and Performance in AI for Autonomous Vehicles?," a P...

"Can We Have Both Safety and Performance in AI for Autonomous Vehicles?," a P...Edge AI and Vision Alliance
Similar to Eset vs Symantec (20)
Presentatie McAfee: Optimale Endpoint Protection 26062015

Presentatie McAfee: Optimale Endpoint Protection 26062015
Developing functional safety systems with arm architecture solutions stroud

Developing functional safety systems with arm architecture solutions stroud
How PCI And PA DSS will change enterprise applications

How PCI And PA DSS will change enterprise applications
Proving the Security of Low-Level Software Components & TEEs

Proving the Security of Low-Level Software Components & TEEs
Snort Intrusion Detection / Prevention System on PFSense Firewall

Snort Intrusion Detection / Prevention System on PFSense Firewall
"Can We Have Both Safety and Performance in AI for Autonomous Vehicles?," a P...

"Can We Have Both Safety and Performance in AI for Autonomous Vehicles?," a P...
Anti Key Logging And Real Time Encryption Software

Anti Key Logging And Real Time Encryption Software
CYBERSECURITY PROCESSES & TECHNOLOGIES LAB #2: MANAGING HOST BASED SECURITY

CYBERSECURITY PROCESSES & TECHNOLOGIES LAB #2: MANAGING HOST BASED SECURITY
Recently uploaded
Recently uploaded (20)
Boost PC performance: How more available memory can improve productivity

Boost PC performance: How more available memory can improve productivity
Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024

Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024
Factors to Consider When Choosing Accounts Payable Services Providers.pptx

Factors to Consider When Choosing Accounts Payable Services Providers.pptx
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
Tata AIG General Insurance Company - Insurer Innovation Award 2024

Tata AIG General Insurance Company - Insurer Innovation Award 2024
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
2024: Domino Containers - The Next Step. News from the Domino Container commu...

2024: Domino Containers - The Next Step. News from the Domino Container commu...
Axa Assurance Maroc - Insurer Innovation Award 2024

Axa Assurance Maroc - Insurer Innovation Award 2024
[2024]Digital Global Overview Report 2024 Meltwater.pdf![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[2024]Digital Global Overview Report 2024 Meltwater.pdf
The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf

The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
Advantages of Hiring UIUX Design Service Providers for Your Business

Advantages of Hiring UIUX Design Service Providers for Your Business
Eset vs Symantec
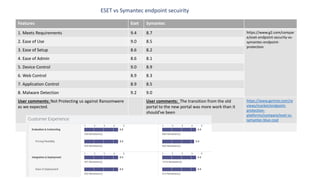
- 1. Features Eset Symantec 1. Meets Requirements 9.4 8.7 https://www.g2.com/compar e/eset-endpoint-security-vs- symantec-endpoint- protection 2. Ease of Use 9.0 8.5 3. Ease of Setup 8.6 8.2 4. Ease of Admin 8.6 8.1 5. Device Control 9.0 8.9 6. Web Control 8.9 8.3 7. Application Control 8.9 8.5 8. Malware Detection 9.2 9.0 User comments: Not Protecting us against Ransomwere as we expected. User comments: The transition from the old portal to the new portal was more work than it should've been https://www.gartner.com/re views/market/endpoint- protection- platforms/compare/eset-vs- symantec-blue-coat ESET vs Symantec endpoint secuirity
- 2. Eset Symantec Features 1. Protection against ransopmware and targeted attacks 2. Detects and remediates against advanced persistent threats 3. Randomware Sheild monitors and evaluates all applications 4. Advanced Memory scanner scans suspicious processes 5. Exploit blocker detects and blocks threats in commonly exploited applications 6. Two-way firewall prevents unauthorised access to your companies network with anti-hacker software 7. Detects malicious communication for strong botnet protection 8. Monitors system activity and uses rules to identify and stop suspicious behaviour Features: 1. Enhanced security powered by artificial intelligence techniques to prevent viruses, with strong firewall and intrusion protection 2. Strong anti-virus protection to stop malware and zero-day exploits 3. Application and device control through central management dashboard, to control device access and behaviour, with app whitelisting and blacklisting 4. AI guided security management to help IT Admins more efficiently update devices and policy 5. Powered by Symantec’s Global Intelligence Networks fed by over 175 million Endpoints 6. Add-on module for protecting laptop endpoints for users working remotely with protection from malicious Wifi networks and policy driven VPN’s to secure employee privacy 7. Application Isolation and Control to block suspicious and malicious apps from Endpoint devices 8. Threat defence for Active Directory to stop credential theft of employees 9. Powerful phishing protection with anti-virus systems and Deception module to help learn how attackers are targeting your organisation https://www.expertinsights.co m/compare/symantec- endpoint-protection-vs-eset- endpoint-security
