Ip
•Download as DOCX, PDF•
0 likes•9 views
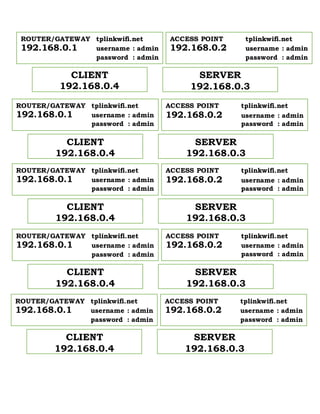
The document lists the IP addresses and login credentials for a router/gateway, client, server, and access point that are all part of a home network with IP range 192.168.0.x. The router/gateway, client, and access point can be accessed at their respective static IP addresses and have the default admin username and password.
Report
Share
Report
Share
Recommended
Recommended
More Related Content
Similar to Ip
Similar to Ip (20)
Cessation of Misconfigurations: Common Network Misconfiguration Risks & How t...

Cessation of Misconfigurations: Common Network Misconfiguration Risks & How t...
Complete squid & firewall configuration. plus easy mac binding

Complete squid & firewall configuration. plus easy mac binding
List of default router admin passwords and ip addresses

List of default router admin passwords and ip addresses
AtlasCamp 2015 Docker continuous integration training

AtlasCamp 2015 Docker continuous integration training
DeveloperWeek 2015: A Practical Introduction to Docker

DeveloperWeek 2015: A Practical Introduction to Docker
Simple Misconfiguration Equals Network Vulnerability!

Simple Misconfiguration Equals Network Vulnerability!
Nagios Conference 2013 - Leland Lammert - Nagios in a Multi-Platform Enviornment

Nagios Conference 2013 - Leland Lammert - Nagios in a Multi-Platform Enviornment
Recently uploaded
Recently uploaded (16)
Production 2024 sunderland culture final - Copy.pptx

Production 2024 sunderland culture final - Copy.pptx
Reggie miller choke t shirtsReggie miller choke t shirts

Reggie miller choke t shirtsReggie miller choke t shirts
The Use of AI in Indonesia Election 2024: A Case Study

The Use of AI in Indonesia Election 2024: A Case Study
Thank You Luv I’ll Never Walk Alone Again T shirts

Thank You Luv I’ll Never Walk Alone Again T shirts
Cyber Security Services Unveiled: Strategies to Secure Your Digital Presence

Cyber Security Services Unveiled: Strategies to Secure Your Digital Presence
Case study on merger of Vodafone and Idea (VI).pptx

Case study on merger of Vodafone and Idea (VI).pptx
Development Lifecycle.pptx for the secure development of apps

Development Lifecycle.pptx for the secure development of apps
Ip
- 1. ROUTER/GATEWAY tplinkwifi.net 192.168.0.1 username : admin password : admin CLIENT 192.168.0.4 SERVER 192.168.0.3 ACCESS POINT tplinkwifi.net 192.168.0.2 username : admin password : admin ROUTER/GATEWAY tplinkwifi.net 192.168.0.1 username : admin password : admin CLIENT 192.168.0.4 SERVER 192.168.0.3 ACCESS POINT tplinkwifi.net 192.168.0.2 username : admin password : admin ROUTER/GATEWAY tplinkwifi.net 192.168.0.1 username : admin password : admin CLIENT 192.168.0.4 SERVER 192.168.0.3 ACCESS POINT tplinkwifi.net 192.168.0.2 username : admin password : admin ROUTER/GATEWAY tplinkwifi.net 192.168.0.1 username : admin password : admin CLIENT 192.168.0.4 SERVER 192.168.0.3 ACCESS POINT tplinkwifi.net 192.168.0.2 username : admin password : admin ROUTER/GATEWAY tplinkwifi.net 192.168.0.1 username : admin password : admin CLIENT 192.168.0.4 SERVER 192.168.0.3 ACCESS POINT tplinkwifi.net 192.168.0.2 username : admin password : admin