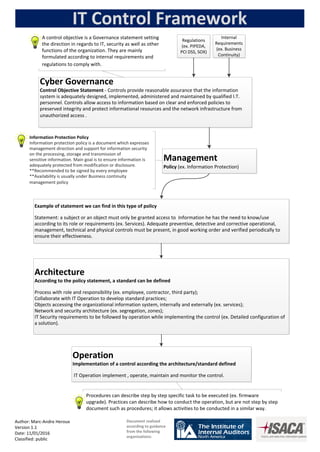
IT Control Framework
- 1. Cyber Governance Control Objective Statement - Controls provide reasonable assurance that the information system is adequately designed, implemented, administered and maintained by qualified I.T. personnel. Controls allow access to information based on clear and enforced policies to preserved integrity and protect informational resources and the network infrastructure from unauthorized access . Regulations (ex. PIPEDA, PCI DSS, SOX) Management Policy (ex. Information Protection) Example of statement we can find in this type of policy Statement: a subject or an object must only be granted access to Information he has the need to know/use according to its role or requirements (ex. Services). Adequate preventive, detective and corrective operational, management, technical and physical controls must be present, in good working order and verified periodically to ensure their effectiveness. Internal Requirements (ex. Business Continuity) Architecture According to the policy statement, a standard can be defined Process with role and responsibility (ex. employee, contractor, third party); Collaborate with IT Operation to develop standard practices; Objects accessing the organizational information system, internally and externally (ex. services); Network and security architecture (ex. segregation, zones); IT Security requirements to be followed by operation while implementing the control (ex. Detailed configuration of a solution). IT Control Framework Author: Marc-Andre Heroux Version 1.1 Date: 11/01/2016 Classified: public Document realized according to guidance from the following organizations: A control objective is a Governance statement setting the direction in regards to IT, security as well as other functions of the organization. They are mainly formulated according to internal requirements and regulations to comply with. Information Protection Policy Information protection policy is a document which expresses management direction and support for information security on the processing, storage and transmission of sensitive information. Main goal is to ensure information is adequately protected from modification or disclosure. **Recommended to be signed by every employee **Availability is usually under Business continuity management policy Procedures can describe step by step specific task to be executed (ex. firmware upgrade). Practices can describe how to conduct the operation, but are not step by step document such as procedures; it allows activities to be conducted in a similar way. Operation Implementation of a control according the architecture/standard defined IT Operation implement , operate, maintain and monitor the control.
